PublicKey Encryption Introduction to Number Theory A prime
Public-Key Encryption Introduction to Number Theory • A prime number is an integer that can only be divided without remainder by positive and negative values of itself and 1. Prime numbers play a critical role both in number theory and in cryptography. • Two theorems that play important roles in public-key cryptography are Fermat's theorem and Euler's theorem. • An important requirement in a number of cryptographic algorithms is the ability to choose a large prime number. An area of ongoing research is the development of efficient algorithms for determining if a randomly chosen large integer is a prime number. 1

Fermat's Theorem Fermat's theorem states the following: If p is prime and a is a positive integer not divisible by p, then An alternative form of Fermat's theorem is also useful: If p is prime and a is a positive integer, then • • p = 5, a = 3 ap = 35 = 243 3(mod 5) = a(mod p) p = 5, a = 10 ap = 105 = 100000 10(mod 5) = a(mod p) 2

Euler Totient Function ø(n) • to compute ø(n) need to count number of residues to be excluded • in general need prime factorization, but – for p (p prime) – for p. q (p, q prime) ø(pq) = p-1 =(p-1)x(q-1) • eg. ø(37) = 36 ø(21) = (3– 1)x(7– 1) = 2 x 6 = 12 3

Public-Key Cryptography • public-key/two-key/asymmetric cryptography involves the use of two keys: – a public-key, which may be known by anybody, and can be used to encrypt messages, and verify signatures – a private-key, known only to the recipient, used to decrypt messages, and sign (create) signatures • is asymmetric because – those who encrypt messages or verify signatures cannot decrypt messages or create signatures 4

Why Public-Key Cryptography? • developed to address two key issues: – key distribution – how to have secure communications in general without having to trust a KDC with your key – digital signatures – how to verify a message comes intact from the claimed sender • public invention due to Whitfield Diffie & Martin Hellman at Stanford Uni in 1976 – known earlier in classified community 5

Public-Key Applications • can classify uses into 3 categories: – encryption/decryption (provide secrecy) – digital signatures (provide authentication) – key exchange (of session keys) • some algorithms are suitable for all uses, others are specific to one 6

RSA • by Rivest, Shamir & Adleman of MIT in 1977 • best known & widely used public-key scheme • uses large integers (eg. 1024 bits) • security due to cost of factoring large numbers 7

RSA ingredients We are now ready to state the RSA scheme. The : ingredients are the following We are now ready to state the RSA scheme. The ingredients are the following: p, q, two prime numbers (private, chosen) n = pq (public, calculated) e, with gcd(f(n), e) = 1; 1 < e < f(n) (public, chosen) d e 1(mod f(n)) (private, calculated) 8

RSA Algorithm 9
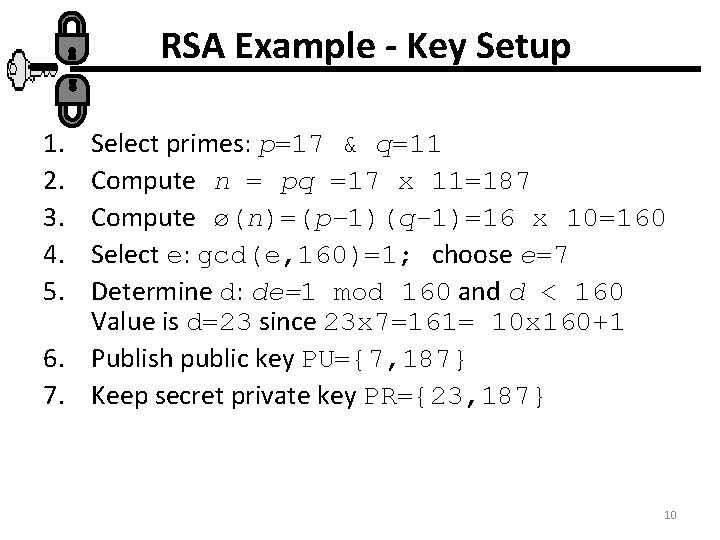
RSA Example - Key Setup 1. 2. 3. 4. 5. Select primes: p=17 & q=11 Compute n = pq =17 x 11=187 Compute ø(n)=(p– 1)(q-1)=16 x 10=160 Select e: gcd(e, 160)=1; choose e=7 Determine d: de=1 mod 160 and d < 160 Value is d=23 since 23 x 7=161= 10 x 160+1 6. Publish public key PU={7, 187} 7. Keep secret private key PR={23, 187} 10

11

Clarification • we need to calculate C = 887 mod 187. Exploiting the properties of modular arithmetic, we can do this as follows: 887 mod 187 = [(884 mod 187) x (882 mod 187) x (881 mod 187)] mod 187 881 mod 187 = 88 882 mod 187 = 7744 mod 187 = 77 884 mod 187 = 59, 969, 536 mod 187 = 132 887 mod 187 = (88 x 77 x 132) mod 187 = 894, 432 mod 187 = 11 12

Security of RSA Four possible approaches to attacking the RSA: Brute force: This involves trying all possible private keys. Mathematical attacks: There are several approaches, all equivalent in effort to factoring the product of two primes. Timing attacks: These depend on the running time of the decryption algorithm. Chosen cipher text attacks: This type of attack exploits properties of the RSA algorithm. 13
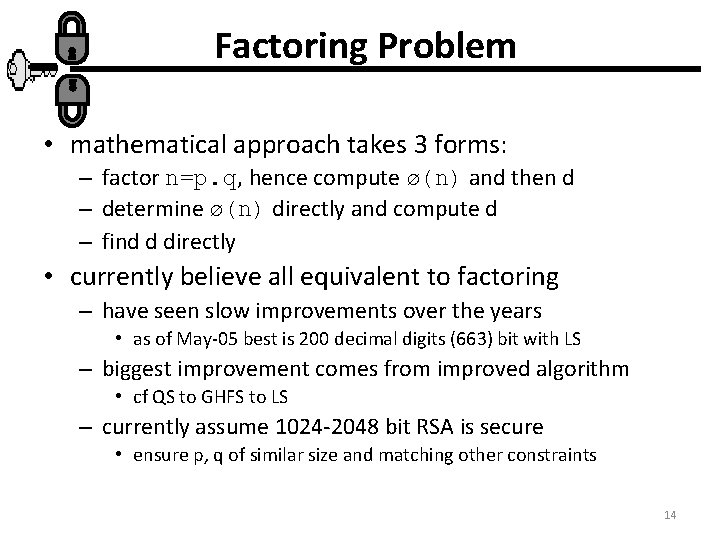
Factoring Problem • mathematical approach takes 3 forms: – factor n=p. q, hence compute ø(n) and then d – determine ø(n) directly and compute d – find d directly • currently believe all equivalent to factoring – have seen slow improvements over the years • as of May-05 best is 200 decimal digits (663) bit with LS – biggest improvement comes from improved algorithm • cf QS to GHFS to LS – currently assume 1024 -2048 bit RSA is secure • ensure p, q of similar size and matching other constraints 14

Timing Attacks • developed by Paul Kocher in mid-1990’s • exploit timing variations in operations – eg. multiplying by small vs large number – or IF's varying which instructions executed • infer operand size based on time taken • RSA exploits time taken in exponentiation • countermeasures – use constant exponentiation time – add random delays – blind values used in calculations 15

Chosen Cipher text Attacks • RSA is vulnerable to a Chosen Ciphertext Attack (CCA) • attackers chooses ciphertexts & gets decrypted plaintext back • choose ciphertext to exploit properties of RSA to provide info to help cryptanalysis • can counter with random pad of plaintext • or use Optimal Asymmetric Encryption Padding (OASP) 16

Examples on RSA • Perform encryption and decryption using the RSA algorithm, for the following: 1. p = 5; q = 11, e = 3; M = 9 2. p = 7; q = 11, e = 17; M = 8 3. p = 11; q = 13, e = 11; M = 7 4. p = 3; q = 11, e = 7; M = 5 17
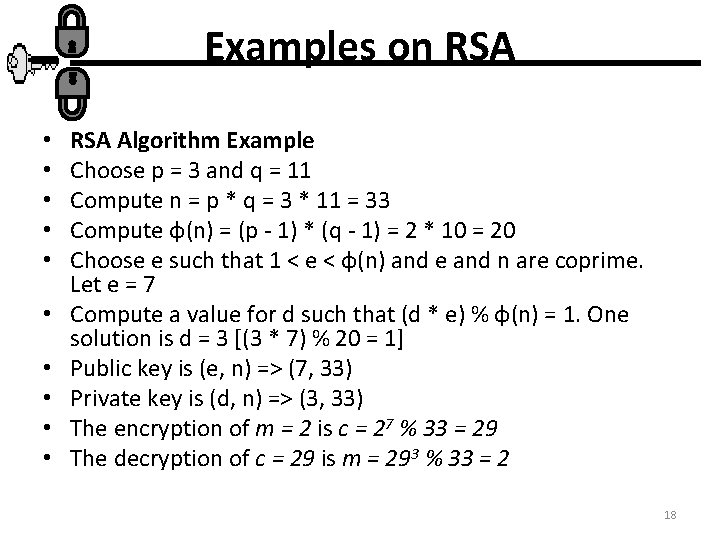
Examples on RSA • • • RSA Algorithm Example Choose p = 3 and q = 11 Compute n = p * q = 3 * 11 = 33 Compute φ(n) = (p - 1) * (q - 1) = 2 * 10 = 20 Choose e such that 1 < e < φ(n) and e and n are coprime. Let e = 7 Compute a value for d such that (d * e) % φ(n) = 1. One solution is d = 3 [(3 * 7) % 20 = 1] Public key is (e, n) => (7, 33) Private key is (d, n) => (3, 33) The encryption of m = 2 is c = 27 % 33 = 29 The decryption of c = 29 is m = 293 % 33 = 2 18
End of Sections Creative Minds never gives up Thank you 19
- Slides: 19