Public Key Infrastructure Content Prerequisites Public key infrastructure

Public Key Infrastructure

Content • Prerequisites • Public key infrastructure • X 509 and Openssl • Domain name system • Lab materials • Issuing and Revoking Certificates • Hierarchy of Certificate Authority • Threat to Public Key Infrastructure

Public Key Infrastructure
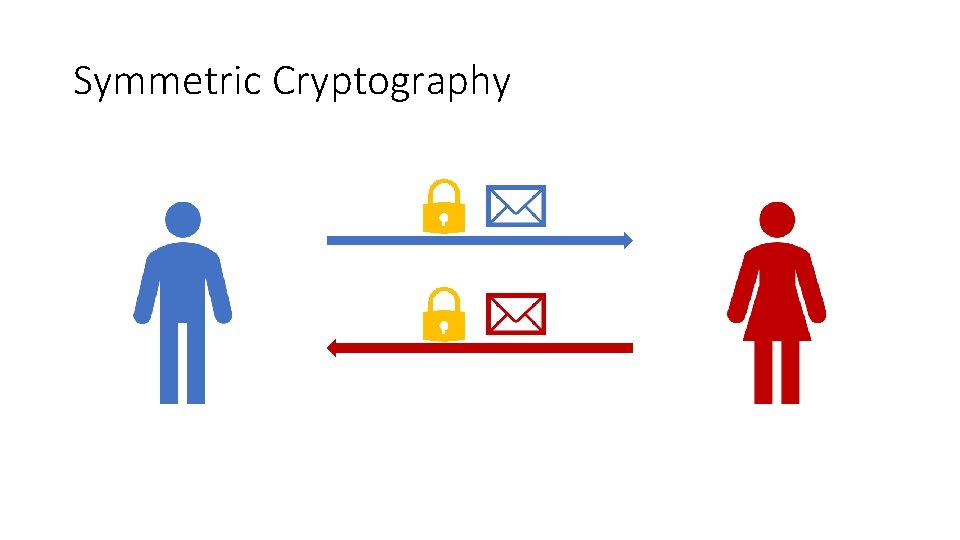
Symmetric Cryptography
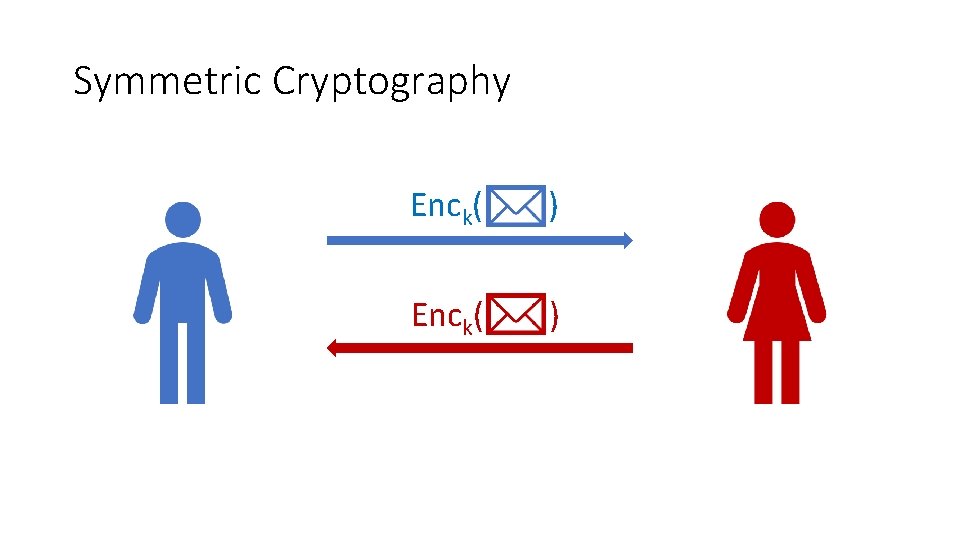
Symmetric Cryptography Enck( )
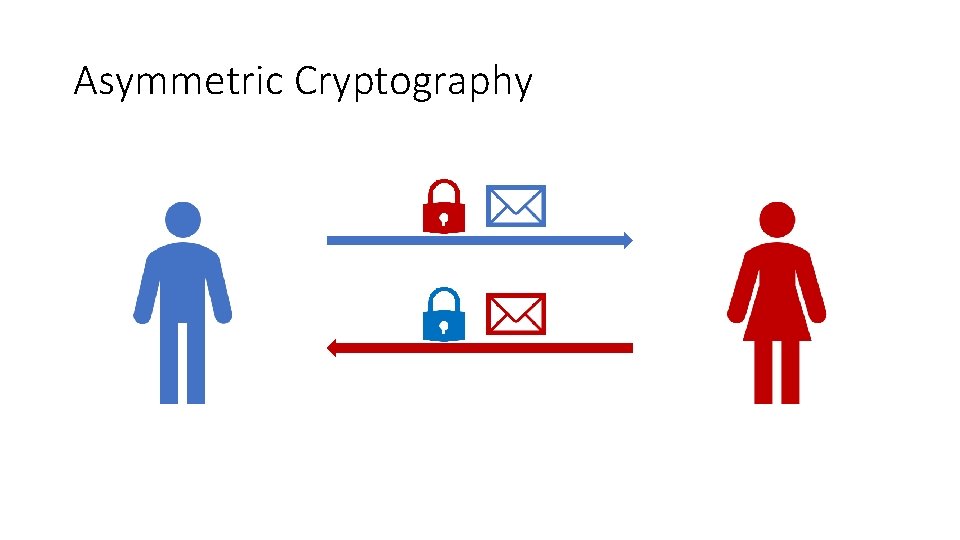
Asymmetric Cryptography
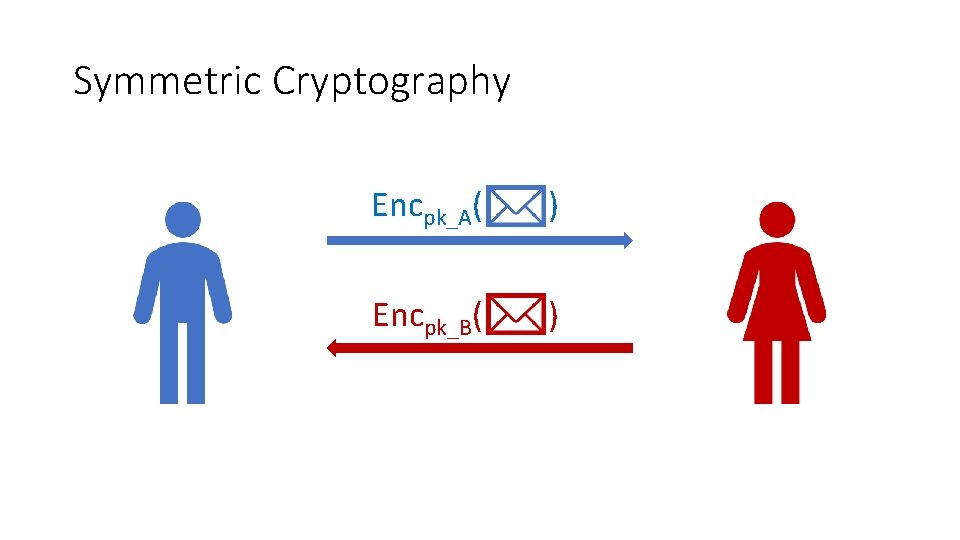
Symmetric Cryptography Encpk_A( ) Encpk_B( )
Confidentiality and Authenticity
Confidentiality and Authenticity
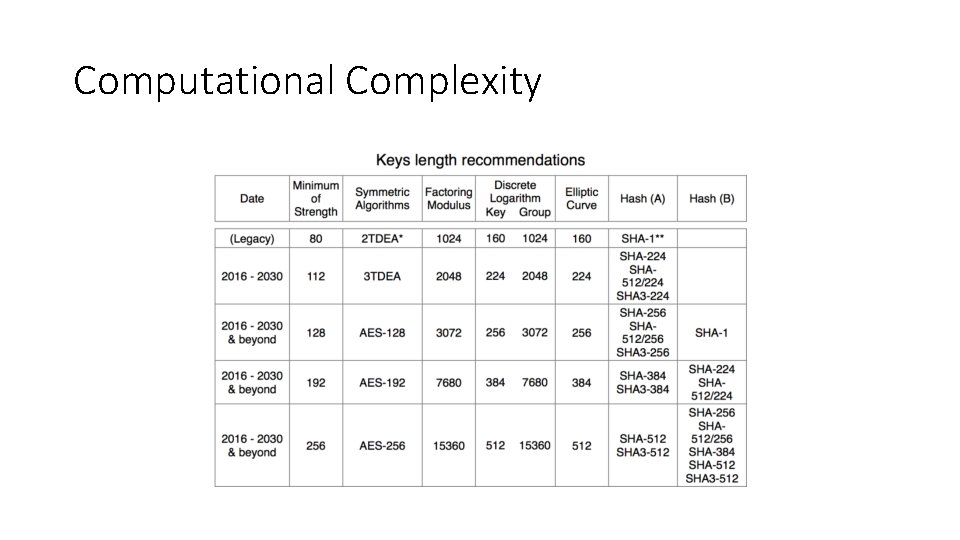
Computational Complexity
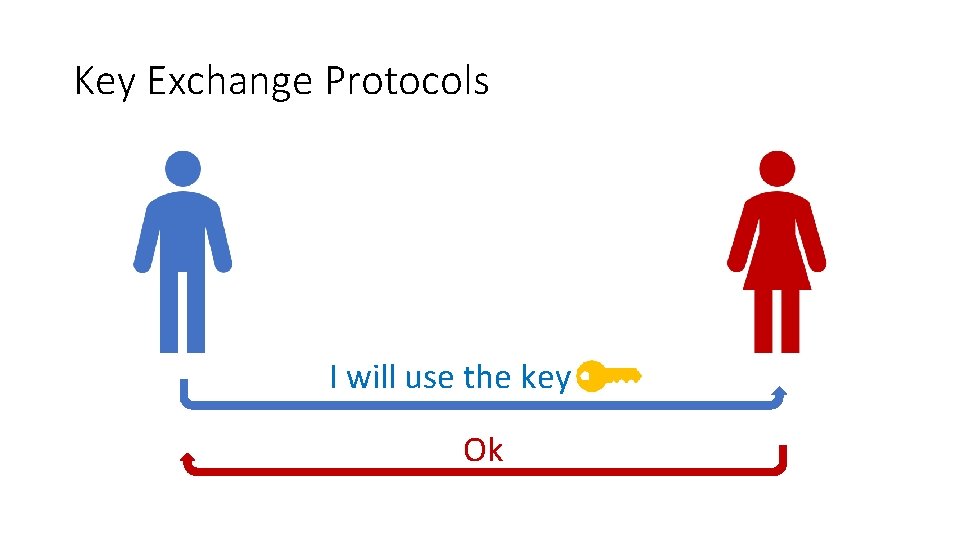
Key Exchange Protocols I will use the key Ok
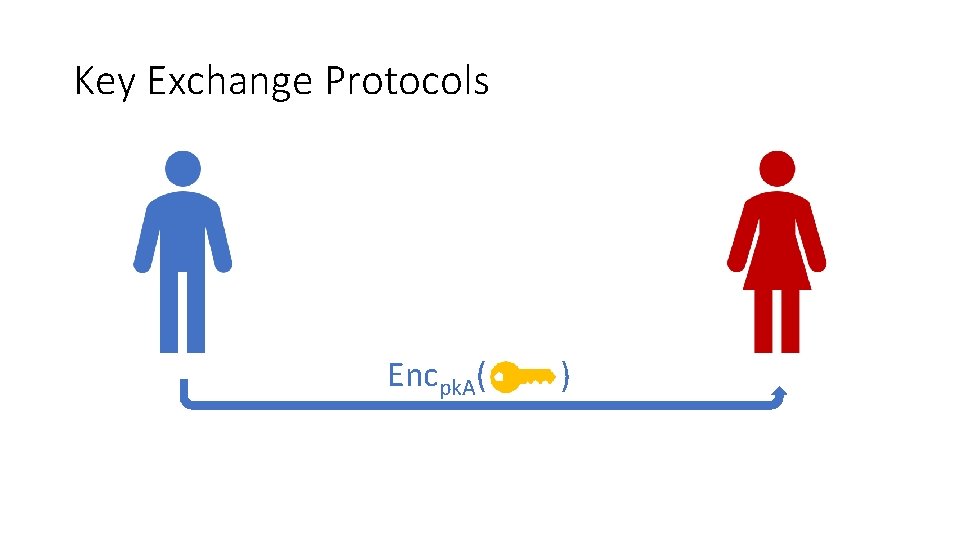
Key Exchange Protocols Encpk. A( )
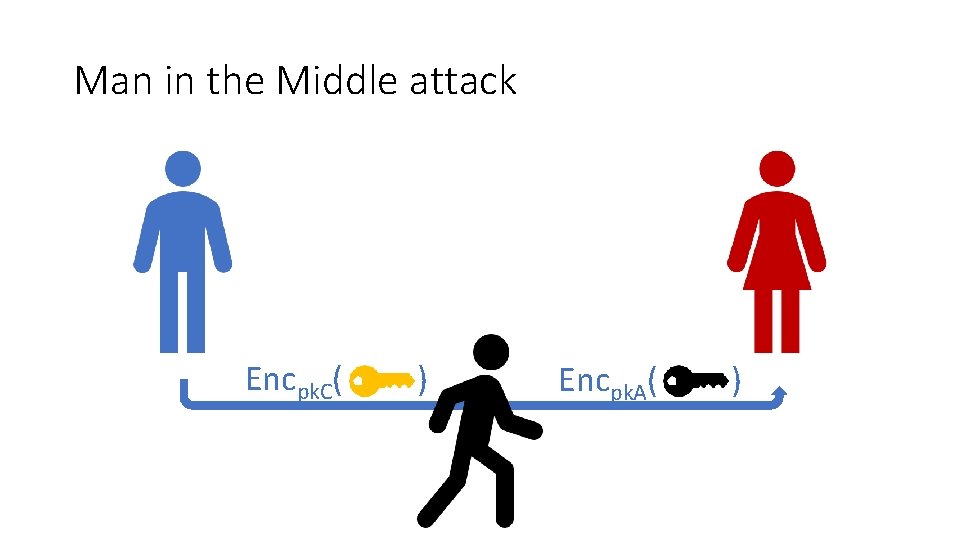
Man in the Middle attack Encpk. C( ) Encpk. A( )

Certificate Give me your Public key and certificate is the certificate and public key
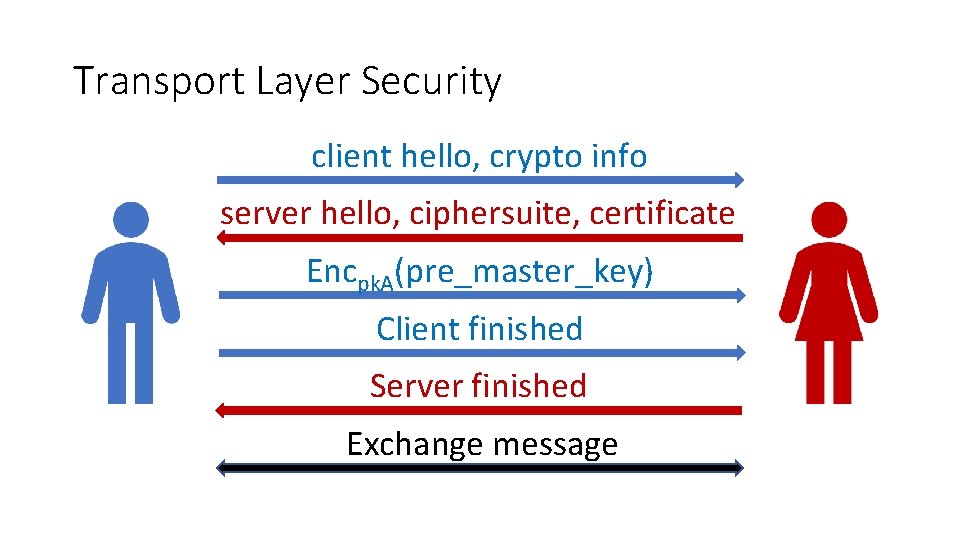
Transport Layer Security client hello, crypto info server hello, ciphersuite, certificate Encpk. A(pre_master_key) Client finished Server finished Exchange message
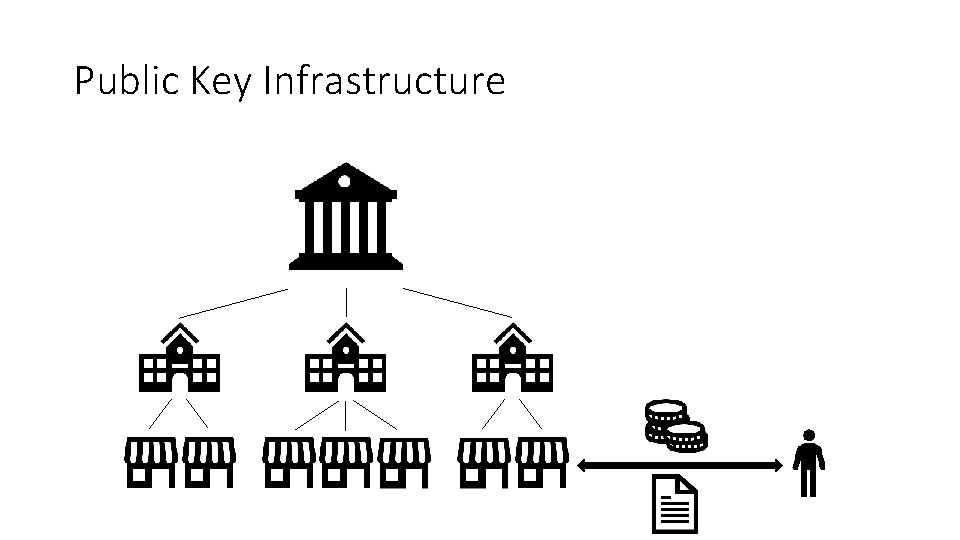
Public Key Infrastructure

x 509 and Openssl

x 509 • Standard format of public key certificates • Used in TLS/SSL, electronic signature • Self-signed or signed by certificate authority • Certificate revocation list • Path validation algorithm

Openssl CSR Entities Private keys
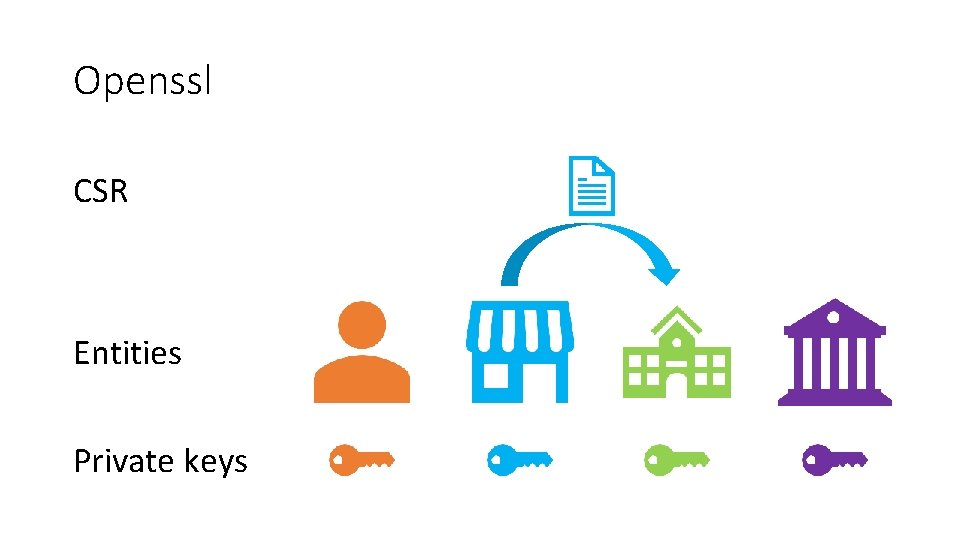
Openssl CSR Entities Private keys
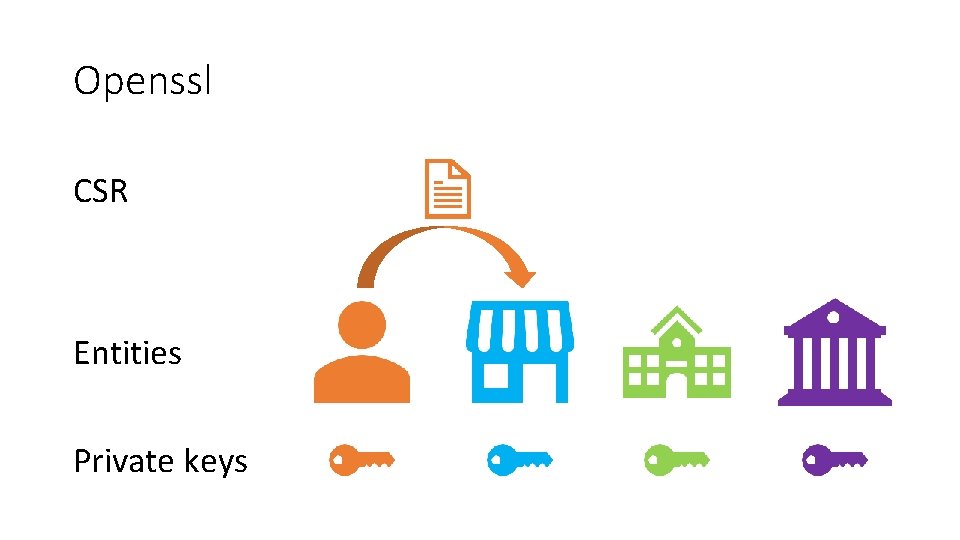
Openssl CSR Entities Private keys

Sample commands • Generate a Private Key and a CSR openssl req -newkey rsa: 2048 -nodes -keyout domain. key -out domain. csr • Generate a Self-Signed Certificate openssl req -newkey rsa: 2048 -nodes -keyout domain. key -x 509 -days 365 -out domain. crt • Sign a certificate openssl x 509 -req -days 360 -in <CSR-for-the-new-device> -CA <your-intermediate-CA-certificate> -CAkey <yourintermediate-CA-key> -out <your-new-certificate> -set_serial <a random number>

Domain Name System
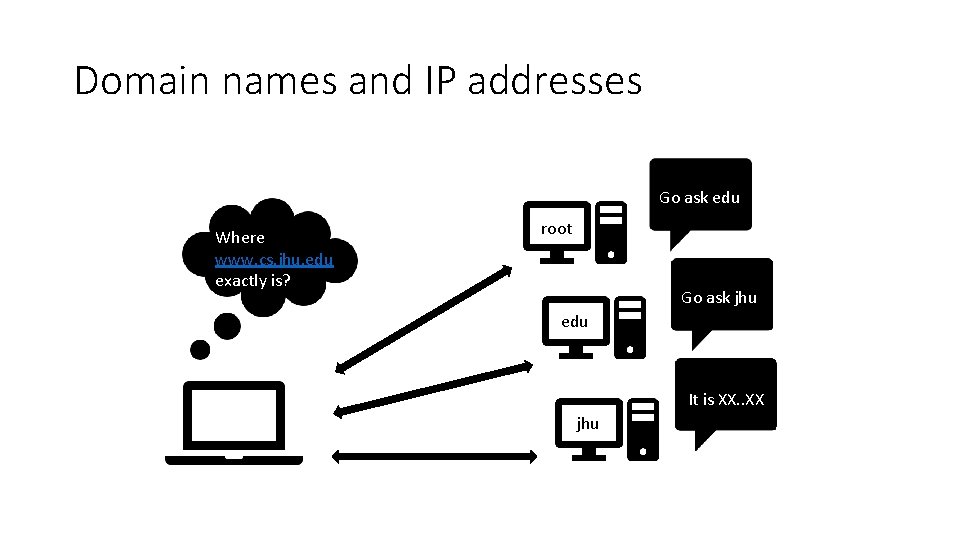
Domain names and IP addresses Go ask edu Where www. cs. jhu. edu exactly is? root Go ask jhu edu It is XX. . XX jhu
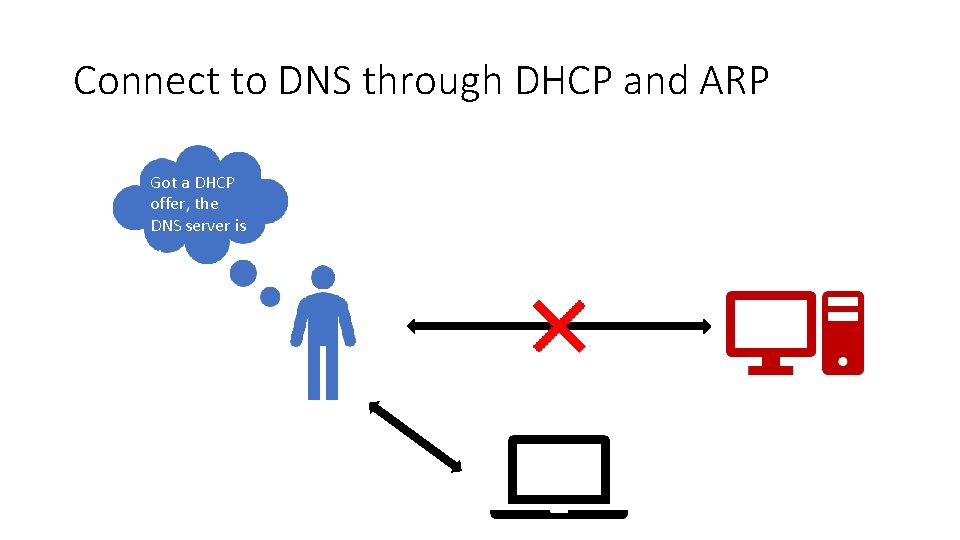
Connect to DNS through DHCP and ARP Got a DHCP offer, the DNS server is …

Lab Materials

Issuing and Revoking Certificates • Draw topology and reserve resources • Set up LAMP for web application • Set up Certificate Authority • Generate certificate and configurate it • Revoke the certificate

Hierarchy of Certificate Authority • Basically the same as the previous one • Replace a single CA with a chain of CA
Threat to Public Key Infrastructure • Setup DNS server on attacker’s node • Setup web server on server’s node • Install tool-sslsplit on attacker’s node • Connect web server from client • Check whether attacker did intercept messages
- Slides: 29