Public Key Encryption and the RSA Algorithm Computer

Public Key Encryption and the RSA Algorithm Computer Networking- A top-Down Approach Featuring the Internet James F Kurose and Keith W Ross, Second Edition, Pearson Publication Chapter 7 - page 642 – 647

Goal • To understand what public key encryption is doing to achieve security. • To focus on the working principle of public key encryption using RSA algorithm

Objective • The student will be able to apply the technique followed in public key encryption method

Private-Key Cryptography • traditional private/secret/single key cryptography uses only one key. • Key is shared by both sender and receiver and needs to be known in advance. • if the key is disclosed communications are compromised. • This is also referred to as symmetric key approach.

Possibility of secret key in advance • In internet communicating parties never meet or converse except over the network. • Is it possible for communication to take place without having secret key in advance? – Answer is YES.

Public-Key Cryptography • uses two keys – a public key and a private key • asymmetric since sender do not know private key of receiver • uses clever application of number theory concepts to function • complements rather than replaces private key cryptography
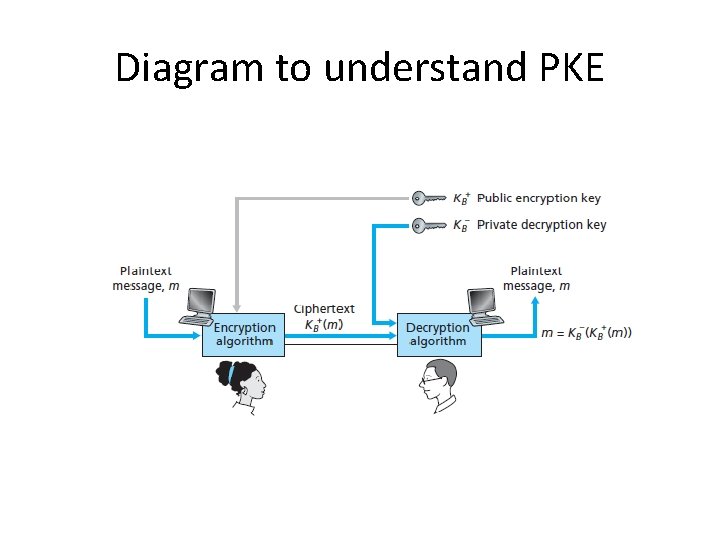
Diagram to understand PKE

Public Key Encryption • public-key/two-key/asymmetric cryptography involves the use of two keys: – a public-key, which may be known by anybody, and can be used to encrypt messages – a private-key, known only to the recipient, used to decrypt messages • is asymmetric because – those who encrypt messages cannot decrypt messages
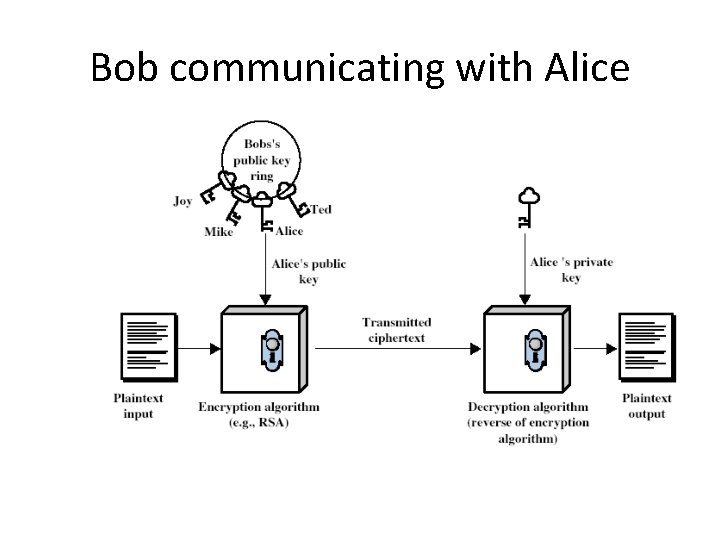
Bob communicating with Alice

Why PK Cryptography? • developed to address two key issues: – key distribution – how to have secure communications in general without having to trust a KDC with your key – digital signatures – how to verify a message comes intact from the claimed sender • public key invention is due to Whitfield Diffie & Martin Hellman at Stanford U. in 1976

Applications • can classify uses into 3 categories: – encryption/decryption (provide secrecy) – digital signatures (provide authentication) – key exchange (of session keys)

RSA • Ron Rivest, Adi Shamir & Leonard Adleman of MIT in 1977. • best known & widely used public-key scheme

Two interrelated components of RSA • The choice of the public key and the private key • The encryption and decryption algorithm
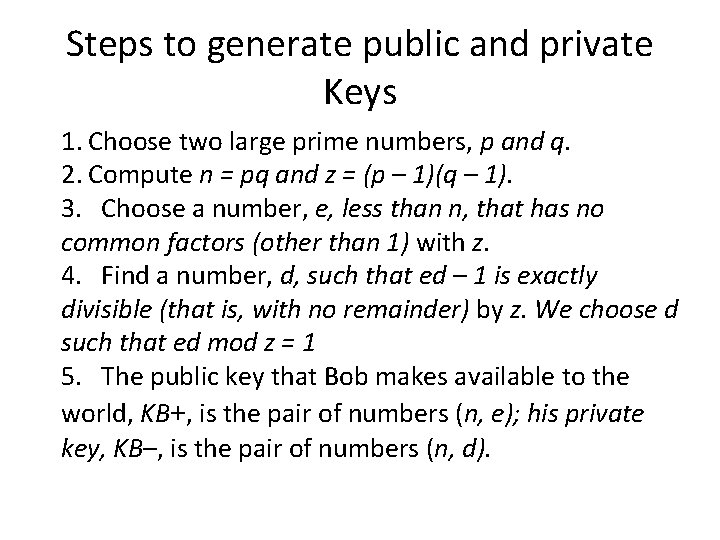
Steps to generate public and private Keys 1. Choose two large prime numbers, p and q. 2. Compute n = pq and z = (p – 1)(q – 1). 3. Choose a number, e, less than n, that has no common factors (other than 1) with z. 4. Find a number, d, such that ed – 1 is exactly divisible (that is, with no remainder) by z. We choose d such that ed mod z = 1 5. The public key that Bob makes available to the world, KB+, is the pair of numbers (n, e); his private key, KB–, is the pair of numbers (n, d).

Encryption and Decryption steps

Pros and Cons of RSA • The security of RSA relies on the fact that there are no known algorithms for – quickly factoring a number, in this case the public value n, into the primes p and q. • It is not known whether or not there exist fast algorithms for factoring a number, hence the security of RSA is not guaranteed. • If one knew p and q, then given the public value e, one could easily compute the secret key, d.

Things to ponder • • The application of PKC Limitation of Public key cryptography KDC Digital signature Example to solve with integer numbers Example to solve with text Alert points

General Instruction for evaluation • Students will follow the team members formed for problem solving • Each team will be assigned a task on the spot in the classroom based on this ppt.

End of RSA FLIPPED CLASSROOM SESSION Click here to view the movie
- Slides: 19