Protocol carrying Authentication for Network Access PANA Subir

Protocol carrying Authentication for Network Access (PANA) Subir Das/Basavaraj Patil Telcordia Technologies Inc. /Nokia 12/14/2001

Motivations • Currently, the authentication process depends upon the type of network that a user is attaching to and it is very much tied to an access technology • Since existing solutions are specific to access technologies, we need either a new mechanism or an extension to existing mechanism to authenticate users each time a new access technology is being standardized • A common protocol for performing user authentication at the network layer (IP) or above could avoid the proliferation of such access specific solutions
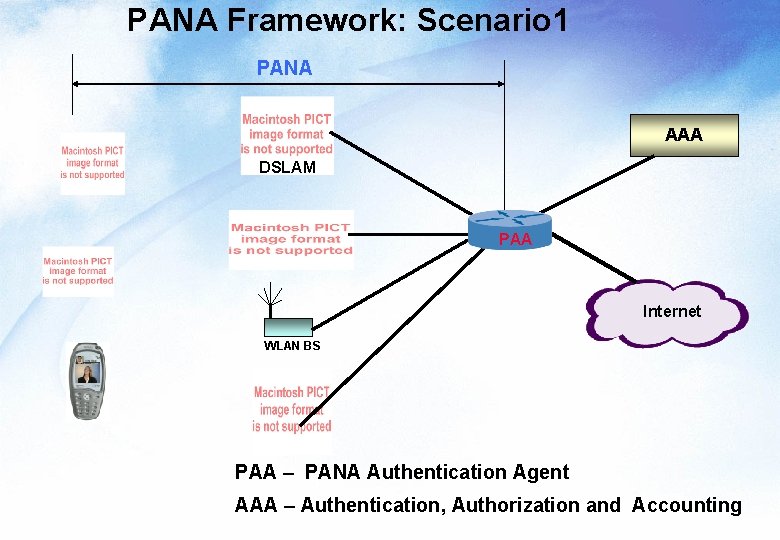
PANA Framework: Scenario 1 PANA AAA DSLAM PAA Internet WLAN BS PAA – PANA Authentication Agent AAA – Authentication, Authorization and Accounting
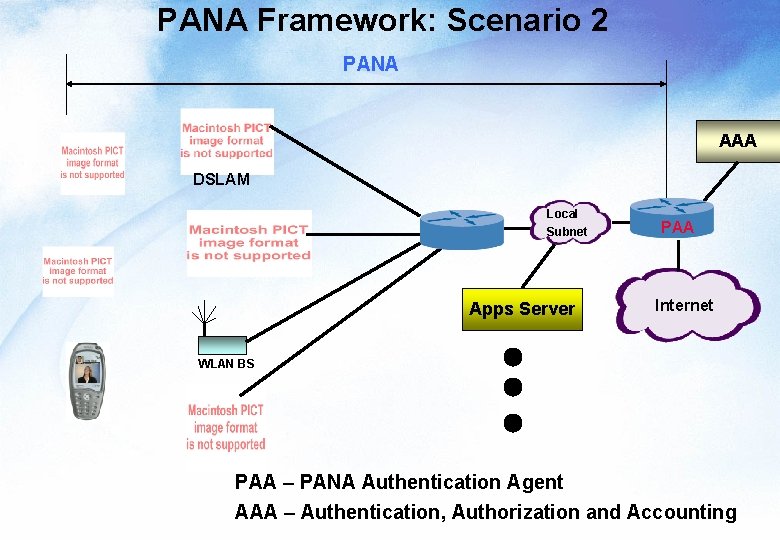
PANA Framework: Scenario 2 PANA AAA DSLAM Local Subnet Apps Server PAA Internet WLAN BS PAA – PANA Authentication Agent AAA – Authentication, Authorization and Accounting

Objective/Goals • The working group's primary task is to define a protocol between a user's device and a node in the network that allows: -- A device (on behalf of a user) to authenticate to an agent in the local network. The agent is called PANA Authentication Agent (PAA) in this charter -- The device to discover the IP address of the PAA -- The PAA to use either local mechanisms/knowledge, or the AAA infrastructure i. e. , being a client of the AAA, to authenticate the device • The WG’s secondary task is to create a Local Security Association (LSA) between the device and PAA after successful initial authentication

Mailing list Information • To subscribe: pana-request@research. telcordia. com In Body : (un) subscribe • General Discussion pana@research. telcordia. com • Archive ftp: //ftp. research. telcordia. com/pub/Group. archive/pana/archive
- Slides: 6