Protocol Basics IPSec Provides two modes of protection

Protocol Basics

IPSec • Provides two modes of protection – Tunnel Mode – Transport Mode • Authentication and Integrity • Confidentiality • Replay Protection

Tunnel Mode • Encapsulates the entire IP packet within IPSec protection • Tunnels can be created between several different node types – Gateway to gateway – Host to host
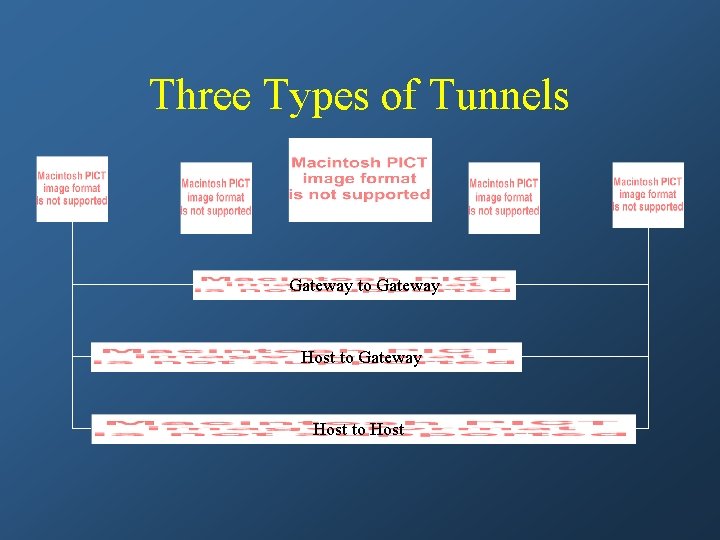
Three Types of Tunnels Gateway to Gateway Host to Host
Transport Mode • Encapsulates only the transport layer information within IPSec protection • Can only be created between host nodes

Authentication and Integrity • Verification of the origin of data • Assurance that data sent is the data received • Assurance that the network headers have not changed since the data was sent

Confidentiality • Encrypts data to protect against eavesdropping • Can hide data source when encryption is used over a tunnel

Replay Prevention • Causes retransmitted packets to be dropped.

IPSec Protection Protocols • Authentication Header – Authenticates payload data – Authenticates network header – Gives anti-replay protection • Encapsulated Security Payload – Encrypts payload data – Authenticates payload data – Gives anti-replay protection
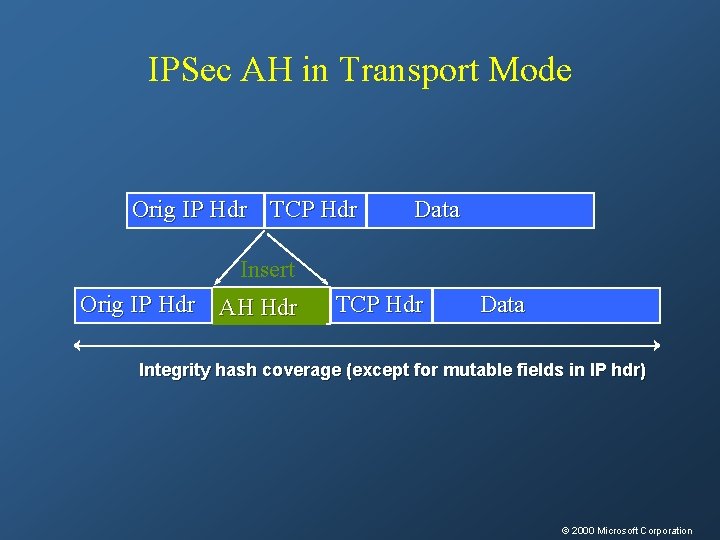
IPSec AH in Transport Mode Orig IP Hdr TCP Hdr Data Insert Orig IP Hdr AH Hdr TCP Hdr Data Integrity hash coverage (except for mutable fields in IP hdr) © 2000 Microsoft Corporation
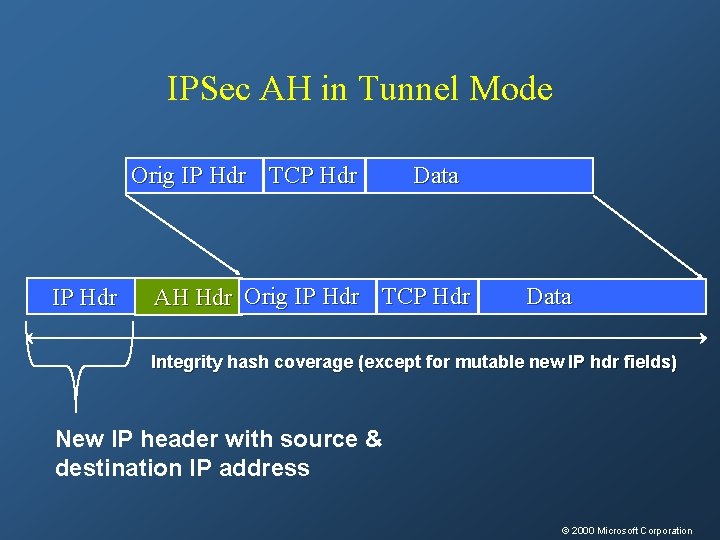
IPSec AH in Tunnel Mode Orig IP Hdr TCP Hdr IP Hdr Data AH Hdr Orig IP Hdr TCP Hdr Data Integrity hash coverage (except for mutable new IP hdr fields) New IP header with source & destination IP address © 2000 Microsoft Corporation
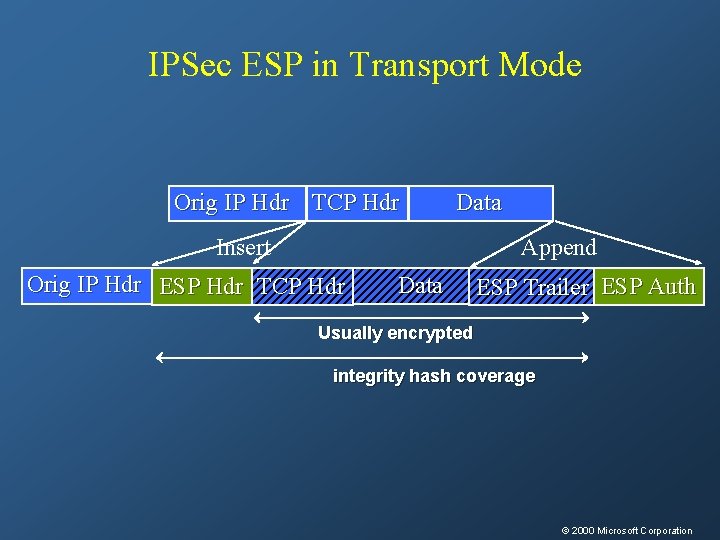
IPSec ESP in Transport Mode Orig IP Hdr TCP Hdr Data Insert Append Orig IP Hdr ESP Hdr TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage © 2000 Microsoft Corporation
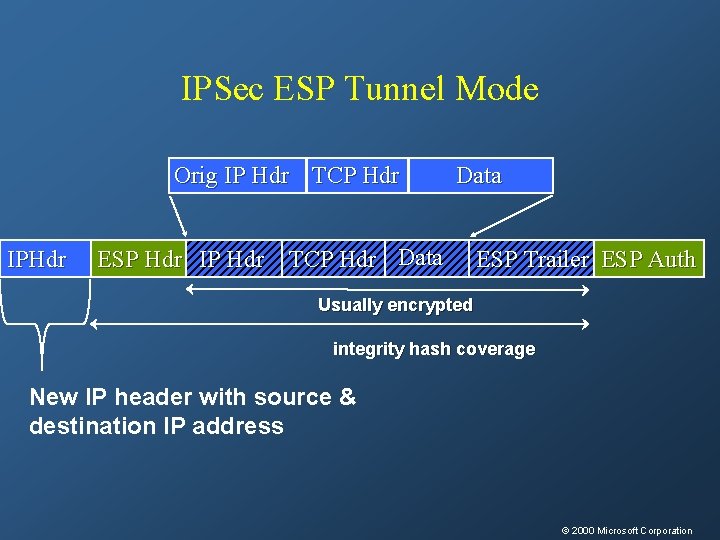
IPSec ESP Tunnel Mode Orig IP Hdr TCP Hdr IPHdr ESP Hdr IP Hdr Data TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage New IP header with source & destination IP address © 2000 Microsoft Corporation

IPSec Basic Architecture • IPSec Driver • Policy Agent • Internet Key Exchange (IKE) TCP/IP Driver Policy Agent IKE IPSec Driver

IPSec Driver • Monitors and Secures IP traffic – Encryption and Authentication of outbound packets – Decryption and Authentication of inbound packets – Prompts IKE to negotiate secure channels as needed • Maintains secure channel state information

Policy Agent • Maintains IPSec policy and state information • Distributes filter rule sets to the IPSec Driver • Distributes authentication and security settings to IKE

IKE • Negotiates secure channels based on settings received from the Policy Agent • Distributes secure channel information to the IPSec driver
How It All Fits Together Tunnel Transport
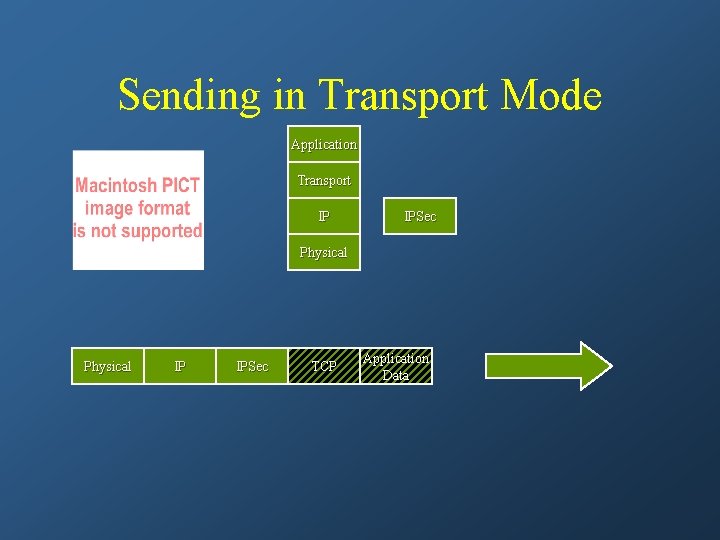
Sending in Transport Mode Application Transport IP IPSec Physical IP IPSec TCP Application Data
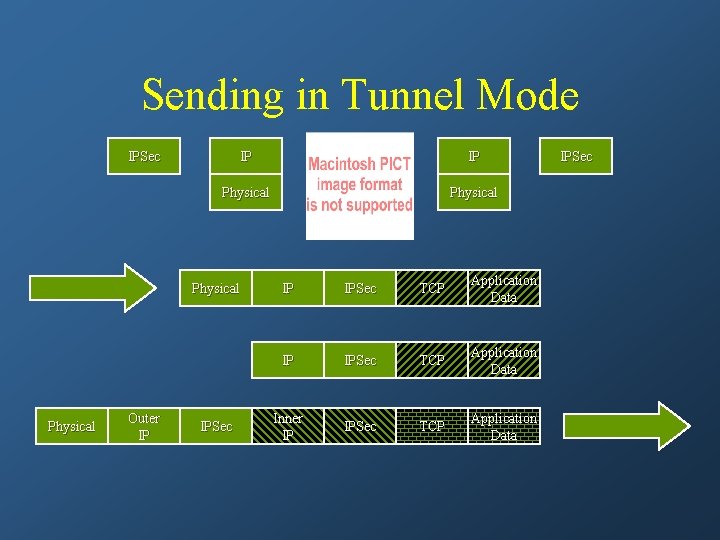
Sending in Tunnel Mode IPSec IP IP Physical Outer IP IPSec TCP Application Data Inner IP IPSec TCP Application Data IPSec
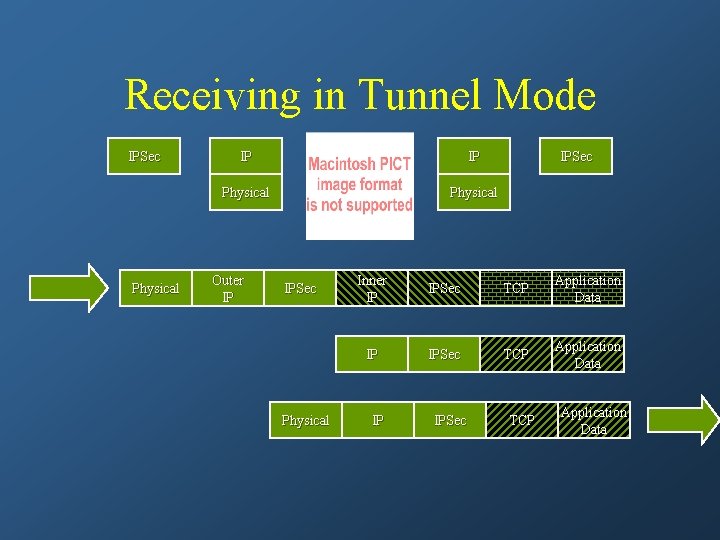
Receiving in Tunnel Mode IPSec Physical IP IP Physical Outer IP IPSec Physical IPSec Inner IP IPSec TCP Application Data

Receiving in Transport Mode Application Transport IPSec IP Physical IP IPSec TCP Application Data

Layer Two Tunneling Protocol (L 2 TP) • Provides – Provides PPP encapsulation over IP – VPN services • Doesn’t Provide – A method of encryption for it’s traffic – Protection against injection of packets into an open L 2 TP session
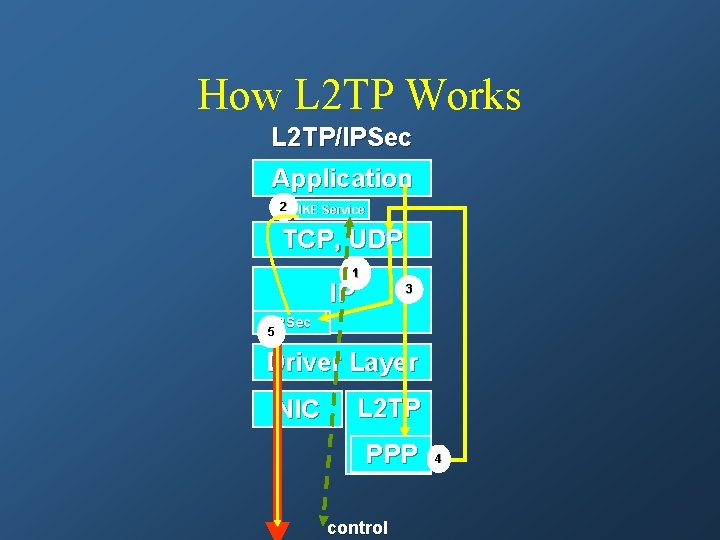
How L 2 TP Works L 2 TP/IPSec Application 2 IKE Service TCP, UDP 1 IP 3 IPSec 5 Driver Layer NIC L 2 TP PPP control 4

Kerberos • Provides authentication of network server and client

What Kerberos Provides • Mutual authentication of parties
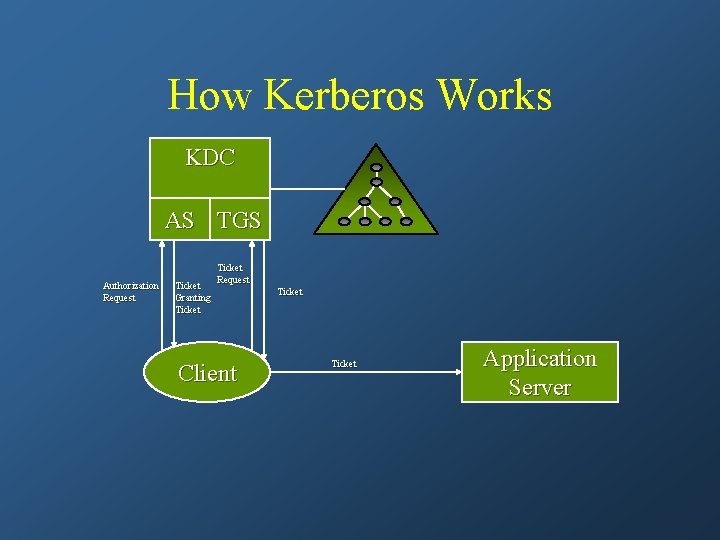
How Kerberos Works KDC AS TGS Authorization Request Ticket Granting Ticket Request Client Ticket Application Server

Public Key Infrastructure Basics

How Public Keys Are Used for Authentication

What’s In a Certificate?

How PKI Works
- Slides: 31