Protection Against Rootkits Defense In Depth The Symantec




![Intrusion Prevention System rule tcp, tcp_flag&ack, daddr=$LOCALHOST, msg="[182. 1] RPC DCOM buffer overflow attempt Intrusion Prevention System rule tcp, tcp_flag&ack, daddr=$LOCALHOST, msg="[182. 1] RPC DCOM buffer overflow attempt](https://slidetodoc.com/presentation_image/9d80d86b7e5c5aaf26ed938b18fd036c/image-5.jpg)


- Slides: 11

Protection Against Rootkits “Defense In Depth”

• The Symantec technology portfolio offers a multi-layered defense including Network Filtering, Behavior Blocking and Storage Filtering layers. All of these layers encompass a wide variety of protection technologies which interact and integrate together to provide a defense in-depth protection.

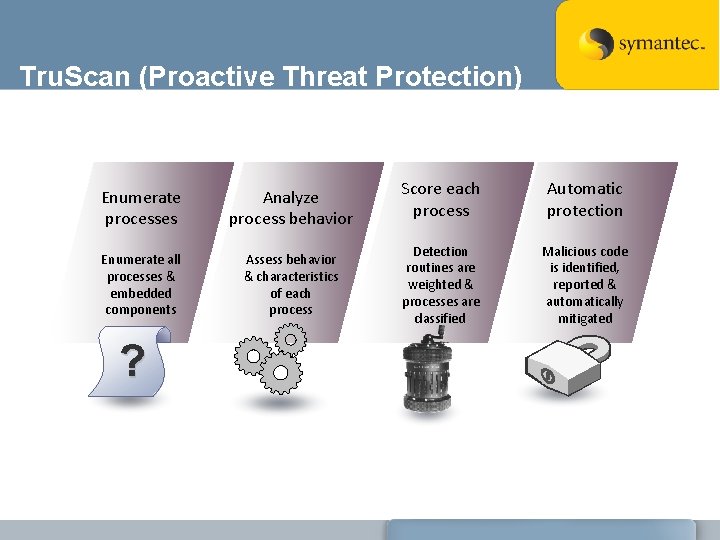
Rootkit Protection Highlights • Network Filtering • Vulnerability signatures allow protection prior to exploit knowledge • Addresses changing paradigm, and shortening window between vulnerability announcement and exploit discovery • Provides protection from diskless threats and fast-moving network worms • Dramatically reduces “time-to-protection” for customers, minimizing disruption • Behavior Blocking technology • Enumerate processes • Analyze process behavior • Score each process • Automatic protection • Storage Filtering Layer • Direct Volume Scanning (Vx. MS) allows our engine to bypass the Windows File System APIs and directly access the raw NTFS volume

Network Filtering • The Network Filtering, is the first line of defense against attacks. This layer examines incoming traffic and can stop threats before they have an impact on the PC. Network filtering layer includes the Network Intrusion Prevention System , and the desktop Firewall security technologies. • Many of today’s threats including rootkits attempt to exploit known OS and application vulnerabilities to execute their code on the PC. The Network IPS engine (using it’s Generic Exploit Blocking capabilities) can filter out attempts to exploit these vulnerabilities, thus keeping malware from executing.
![Intrusion Prevention System rule tcp tcpflagack daddrLOCALHOST msg182 1 RPC DCOM buffer overflow attempt Intrusion Prevention System rule tcp, tcp_flag&ack, daddr=$LOCALHOST, msg="[182. 1] RPC DCOM buffer overflow attempt](https://slidetodoc.com/presentation_image/9d80d86b7e5c5aaf26ed938b18fd036c/image-5.jpg)
Intrusion Prevention System rule tcp, tcp_flag&ack, daddr=$LOCALHOST, msg="[182. 1] RPC DCOM buffer overflow attempt detected", content="x 05x 00x 03x 10x 00x 00"(0, 8) SSH HTTP FTP IM Custom Sig Engine GEB SMTP Signature IDS RCP Intrusion Prevention Features • Deep packet inspection • IDS engine allows admins to create their own signatures • Uses signature format similar to SNORT™ • Regex support • Signatures applied only to vulnerable applications • Resistant to common and advanced evasion techniques SMTP SSH RCP HTTP FTP IM

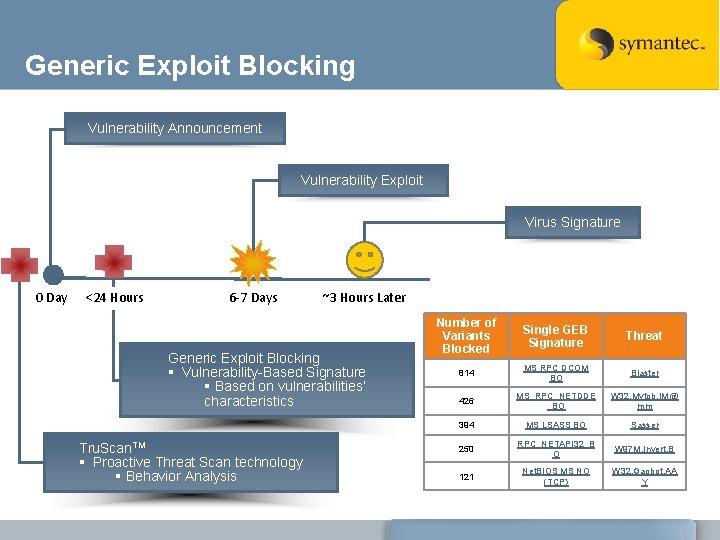
Generic Exploit Blocking Vulnerability Announcement Vulnerability Exploit Virus Signature 0 Day <24 Hours 6 -7 Days ~3 Hours Later Generic Exploit Blocking § Vulnerability-Based Signature § Based on vulnerabilities’ characteristics Tru. Scan. TM § Proactive Threat Scan technology § Behavior Analysis Number of Variants Blocked Single GEB Signature Threat 814 MS RPC DCOM BO Blaster 426 MS_RPC_NETDDE _BO W 32. Mytob. IM@ mm 394 MS LSASS BO Sasser 250 RPC_NETAPI 32_B O W 97 M. Invert. B 121 Net. BIOS MS NO (TCP) W 32. Gaobot. AA Y

Behavior Blocking technology • The second layer of our multilayered protection is the Behavior Blocking technology. This technology monitors the execution activity of code on the PC and attempts to prevent the code from completing its malicious activities. At this layer there are two main proactive technologies : • Tru. Scan • Outbound Email Heuristic (OEH). • All of these technologies have the capability of detecting threats (including rootkits) executing on the PC and can automatically take action on these threats. This protection layer does not rely on specific detection signatures thus providing zero day protection against new threats release in the wild.

Tru. Scan (Proactive Threat Protection) Enumerate processes Analyze process behavior Enumerate all processes & embedded components Assess behavior & characteristics of each process ? Score each process Automatic protection Detection routines are weighted & processes are classified Malicious code is identified, reported & automatically mitigated

Storage Filtering Layer • This layer is adds: • AV engine, threat remediation engine ERASER (Extendable, Replaceable, Advanced Side-Effects Repair), • Direct Volume Scanning (Vx. MS) • Auto. Protect features. • These are traditional signature-based technologies. These technologies continue to demonstrate their efficacy as the baseline of defense. Signature-base technology has a very low false positive rate, and is very efficient in detecting and removing known threats on the PC

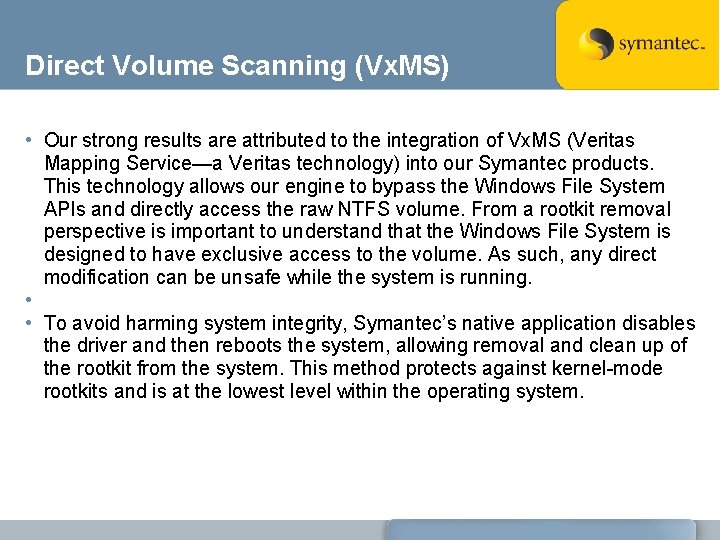
Direct Volume Scanning (Vx. MS) • Our strong results are attributed to the integration of Vx. MS (Veritas Mapping Service—a Veritas technology) into our Symantec products. This technology allows our engine to bypass the Windows File System APIs and directly access the raw NTFS volume. From a rootkit removal perspective is important to understand that the Windows File System is designed to have exclusive access to the volume. As such, any direct modification can be unsafe while the system is running. • • To avoid harming system integrity, Symantec’s native application disables the driver and then reboots the system, allowing removal and clean up of the rootkit from the system. This method protects against kernel-mode rootkits and is at the lowest level within the operating system.

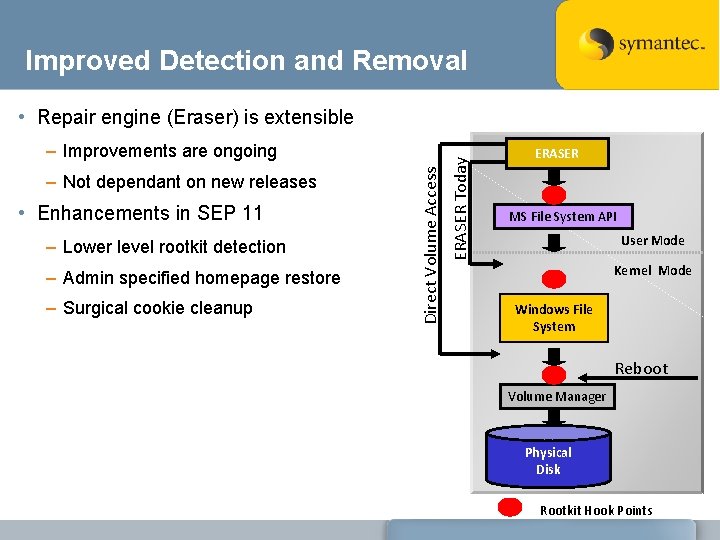
Improved Detection and Removal – Not dependant on new releases • Enhancements in SEP 11 – Lower level rootkit detection – Admin specified homepage restore – Surgical cookie cleanup Direct Volume Access – Improvements are ongoing ERASER Today • Repair engine (Eraser) is extensible ERASER MS File System API User Mode Kernel Mode Windows File System Reboot Volume Manager Physical Disk Rootkit Hook Points