PROTECTING BAREMETAL EMBEDDED SYSTEMS WITH PRIVILEGE OVERLAYS Abraham

PROTECTING BARE-METAL EMBEDDED SYSTEMS WITH PRIVILEGE OVERLAYS Abraham A. Clements, Naif Saleh Almakhdhub, Khaled S. Saab, Prashast Srivastava, Jinkyu Koo, Saurabh Bagchi, and Mathias Payer / 18

BARE-METAL SYSTEMS Systems without an OS Examples Constraints Amazon’s Dash button Small memory sizes Smart door locks 1 MB Flash, 128 KB’s of RAM Tight run-time constraints Engine controllers Low power requirements SD card controllers Single Application Wi. Fi So. C’s No kernel/user space seperation Security left out 2 / 18
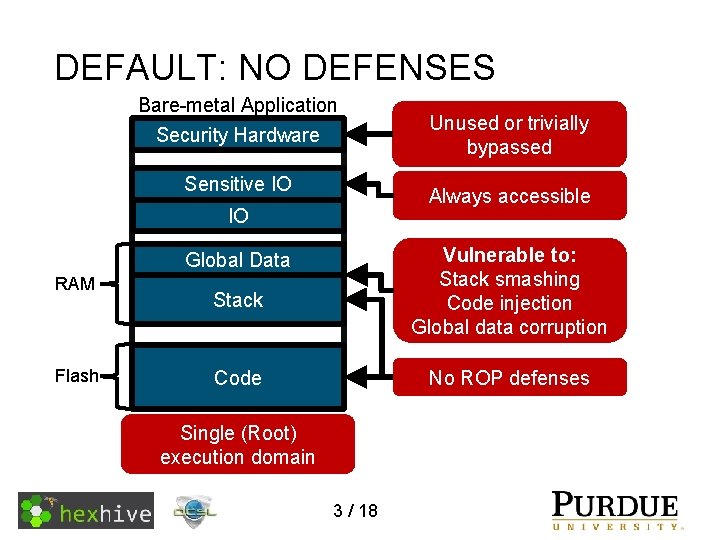
DEFAULT: NO DEFENSES Bare-metal Application Security Hardware Sensitive IO Always accessible IO Stack Vulnerable to: Stack smashing Code injection Global data corruption Code No ROP defenses Global Data RAM Flash Unused or trivially bypassed Single (Root) execution domain 3 / 18

DEFENSE CHALLENGES Single application No separation privilege levels (e. g. kernel, user) Systems lack a MMU Defenses are limited to physical memory space Small memory sizes Tight run-time constraints 4 / 18
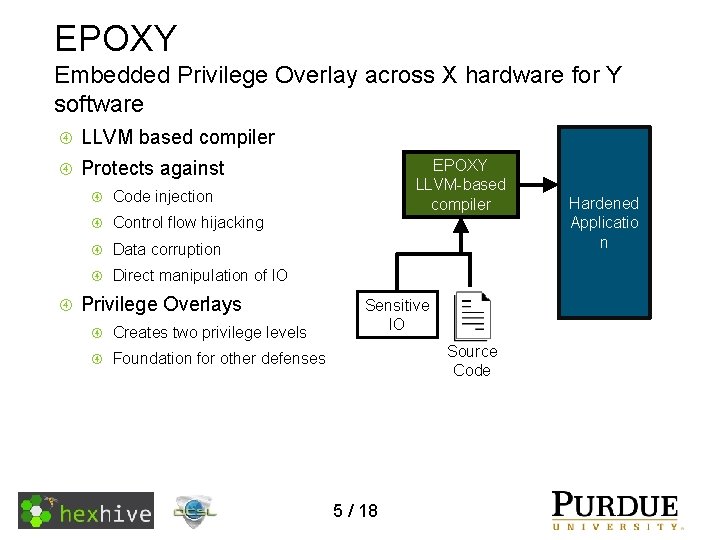
EPOXY Embedded Privilege Overlay across X hardware for Y software LLVM based compiler EPOXY LLVM-based compiler Protects against Code injection Control flow hijacking Data corruption Direct manipulation of IO Privilege Overlays Creates two privilege levels Sensitive IO Source Code Foundation for other defenses 5 / 18 Hardened Applicatio n
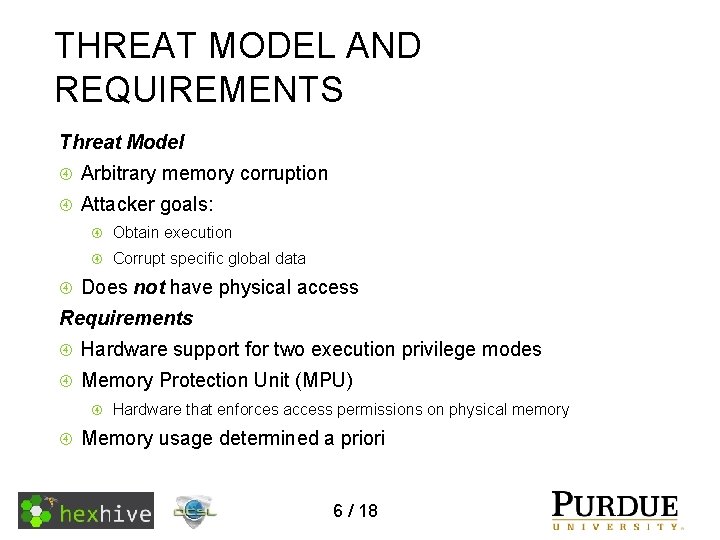
THREAT MODEL AND REQUIREMENTS Threat Model Arbitrary memory corruption Attacker goals: Obtain execution Corrupt specific global data Does not have physical access Requirements Hardware support for two execution privilege modes Memory Protection Unit (MPU) Hardware that enforces access permissions on physical memory Memory usage determined a priori 6 / 18
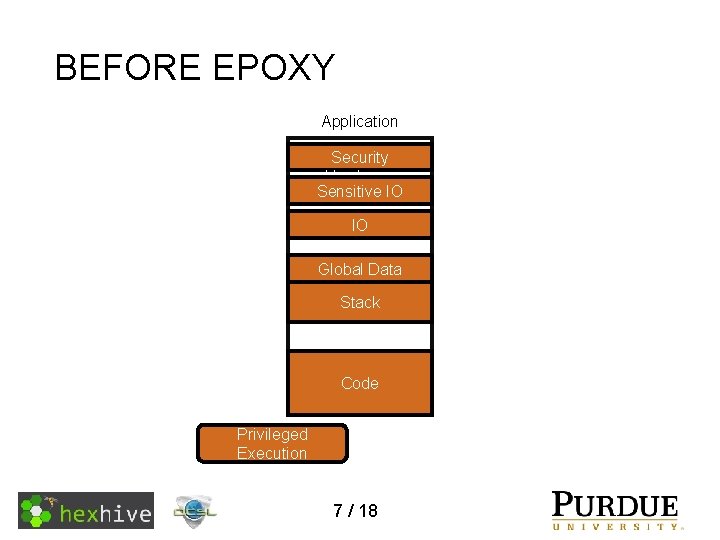
BEFORE EPOXY Application Security Hardware Sensitive IO IO Global Data Stack Code Privileged Execution 7 / 18

PRIVILEGE OVERLAY Creates multiple privilege levels Enables developer to assume access to everything Restricts privileged operations at run-time Static analysis identifies privileged operations Specific instructions defined by the ISA that require privileges Sensitive memory mapped registers (e. g. , MPU configuration , sensitive IO) Created by injecting code to: Configure MPU – Enforce DEP and restrict access to sensitive registers Reduce privileges of entire application Request privileges for restricted operations Handle privilege requests 8 / 18
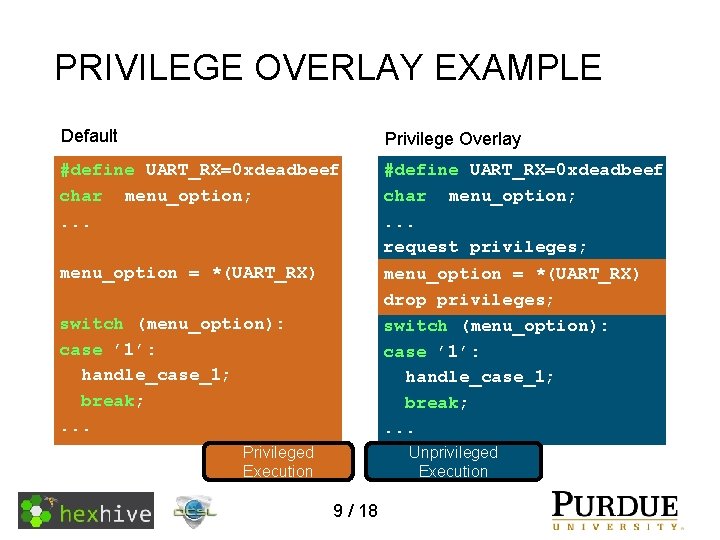
PRIVILEGE OVERLAY EXAMPLE Default Privilege Overlay #define UART_RX=0 xdeadbeef char menu_option; . . . request privileges; menu_option = *(UART_RX) drop privileges; switch (menu_option): case ’ 1’: handle_case_1; break; . . . menu_option = *(UART_RX) switch (menu_option): case ’ 1’: handle_case_1; break; . . . Unprivileged Execution Privileged Execution 9 / 18
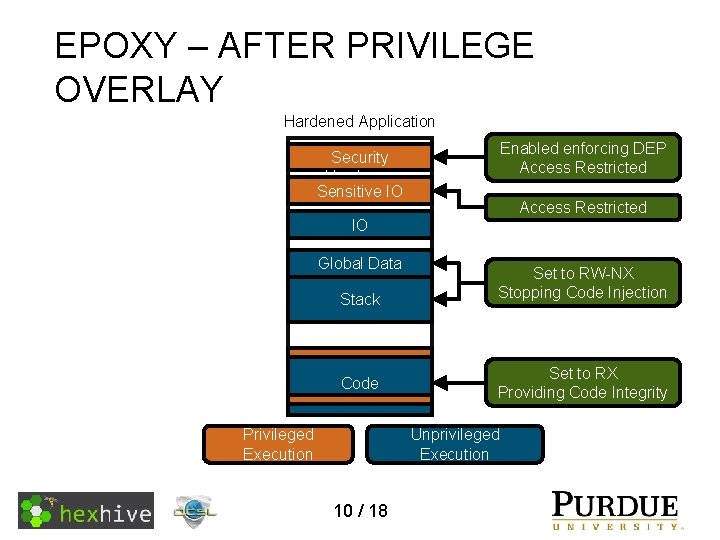
EPOXY – AFTER PRIVILEGE OVERLAY Hardened Application Enabled enforcing DEP Access Restricted Security Hardware Sensitive IO Access Restricted IO Global Data Stack Code Privileged Execution Set to RW-NX Stopping Code Injection Set to RX Providing Code Integrity Unprivileged Execution 10 / 18
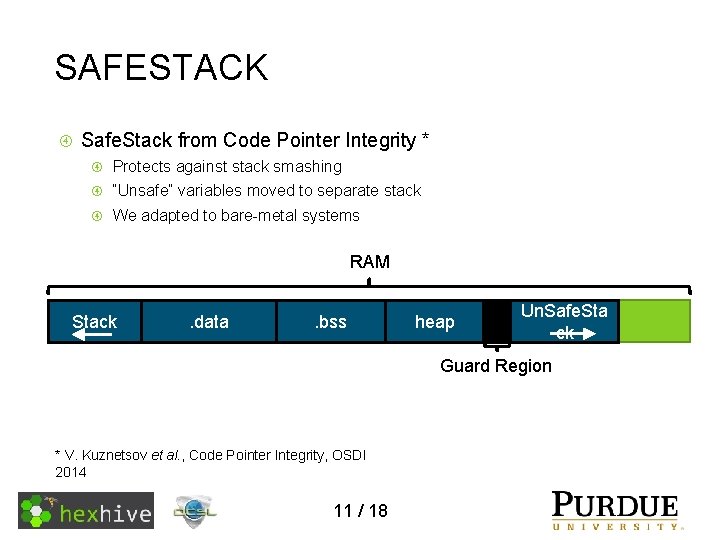
SAFESTACK Safe. Stack from Code Pointer Integrity * Protects against stack smashing “Unsafe” variables moved to separate stack We adapted to bare-metal systems RAM Un. Safe. Stack. data ck . bss. data heap. bss Un. Safe. Sta heap ck Guard Region * V. Kuznetsov et al. , Code Pointer Integrity, OSDI 2014 11 / 18
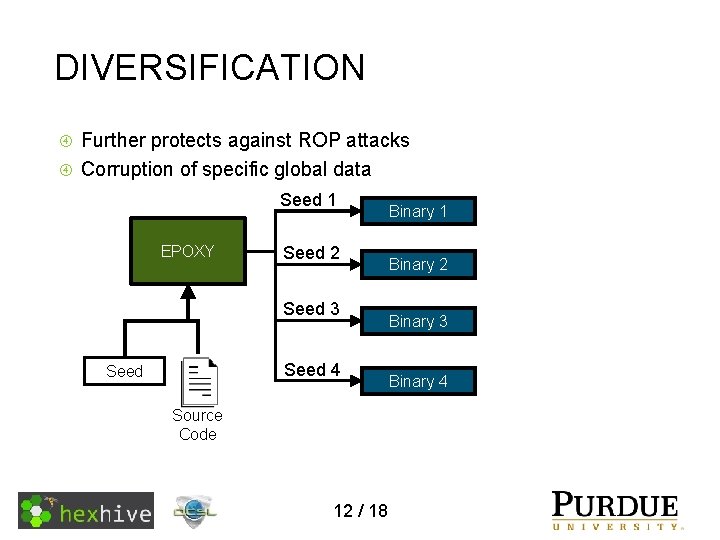
DIVERSIFICATION Further protects against ROP attacks Corruption of specific global data Seed 1 EPOXY Seed 2 Seed 3 Seed 4 Seed Source Code 12 / 18 Binary 1 Binary 2 Binary 3 Binary 4
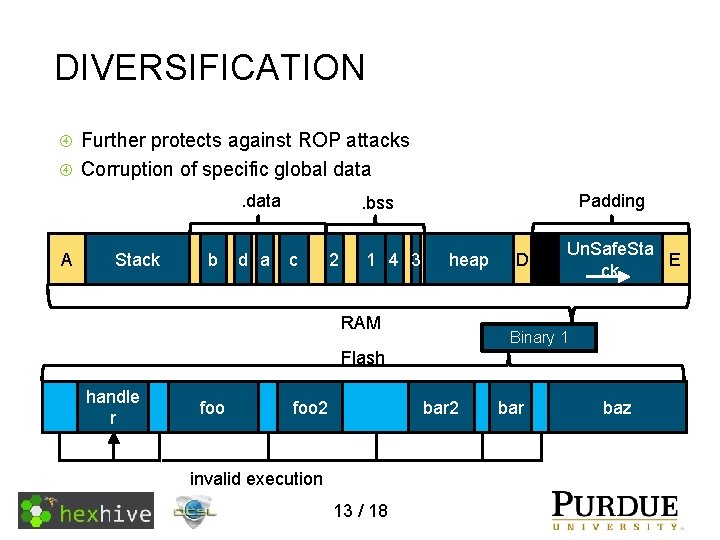
DIVERSIFICATION Further protects against ROP attacks Corruption of specific global data Padding . bss b da. bss ab c d 2 C A Stack. data. B heap 1 4 3 RAM Un. Safe. Sta heap D A B C D E ck ck Binary 1 Flash handle foo bar r foo baz foo 2 bar 2 invalid execution 13 / 18 handler foo 2 bar 2 bar Jumps tobaz r
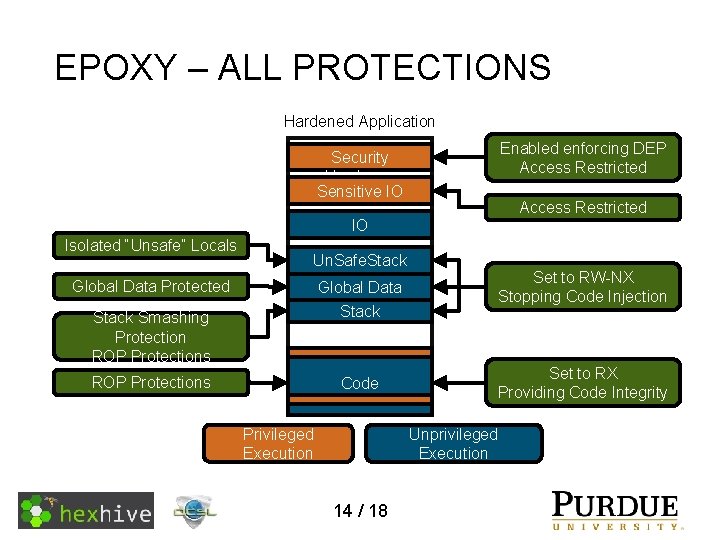
EPOXY – ALL PROTECTIONS Hardened Application Enabled enforcing DEP Access Restricted Security Hardware Sensitive IO Access Restricted IO Isolated “Unsafe” Locals Un. Safe. Stack Global Data Protected Global Data Stack Smashing Protection ROP Protections Stack ROP Protections Code Set to RW-NX Stopping Code Injection Set to RX Providing Code Integrity Unprivileged Execution Privileged Execution 14 / 18
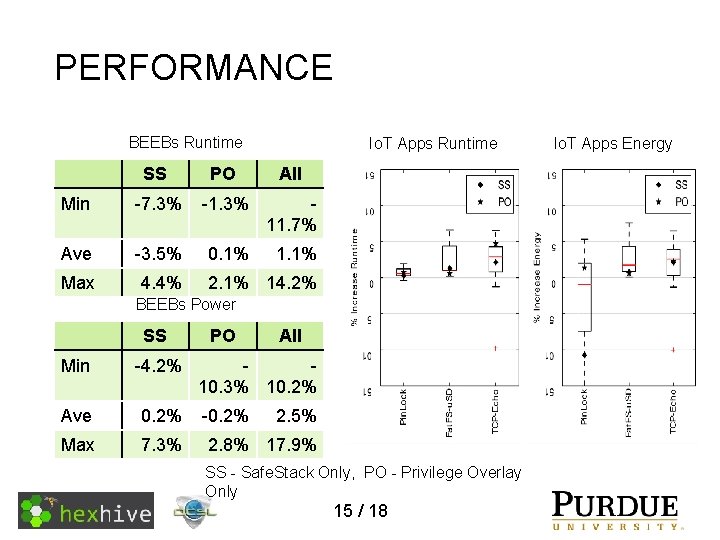
PERFORMANCE BEEBs Runtime Io. T Apps Runtime SS PO All Min -7. 3% -1. 3% 11. 7% Ave -3. 5% 0. 1% 1. 1% Max 4. 4% 2. 1% 14. 2% BEEBs Power SS Min -4. 2% Ave 0. 2% Max 7. 3% PO All 10. 3% 10. 2% -0. 2% 2. 5% 2. 8% 17. 9% SS - Safe. Stack Only, PO - Privilege Overlay Only 15 / 18 Io. T Apps Energy
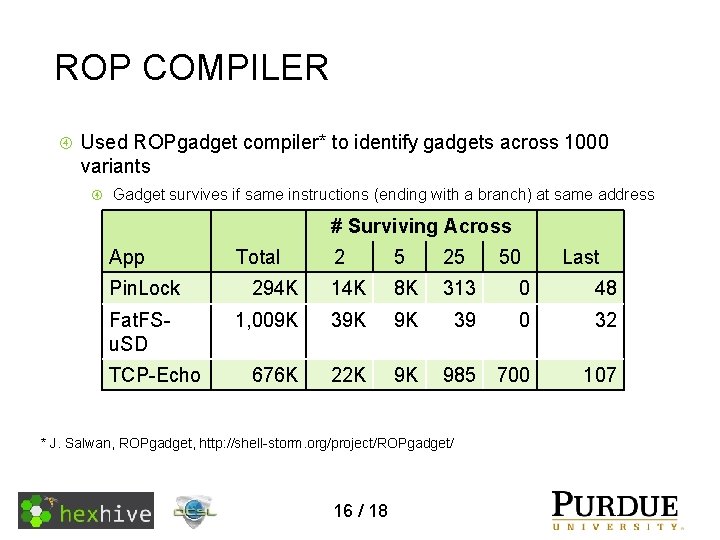
ROP COMPILER Used ROPgadget compiler* to identify gadgets across 1000 variants Gadget survives if same instructions (ending with a branch) at same address # Surviving Across App Pin. Lock Fat. FSu. SD TCP-Echo Total 2 5 25 294 K 14 K 8 K 313 0 48 1, 009 K 39 K 9 K 39 0 32 676 K 22 K 9 K 985 700 107 * J. Salwan, ROPgadget, http: //shell-storm. org/project/ROPgadget/ 16 / 18 50 Last
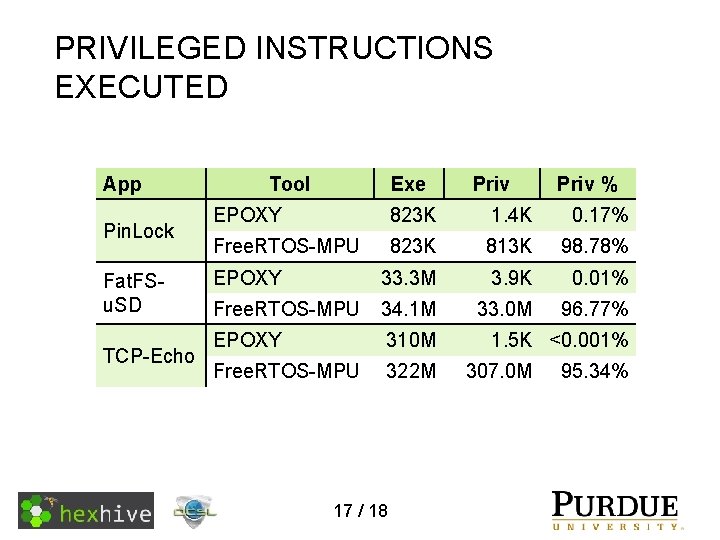
PRIVILEGED INSTRUCTIONS EXECUTED App Pin. Lock Fat. FSu. SD TCP-Echo Tool Exe Priv % EPOXY 823 K 1. 4 K 0. 17% Free. RTOS-MPU 823 K 813 K 98. 78% EPOXY 33. 3 M 3. 9 K 0. 01% Free. RTOS-MPU 34. 1 M 33. 0 M 96. 77% EPOXY 310 M Free. RTOS-MPU 322 M 17 / 18 1. 5 K <0. 001% 307. 0 M 95. 34%

CONCLUSION Fast forwards bare-metal security three decades Provides state-of-the-art protection for bare-metal systems Does not require rewriting application Provides strong stack protections, via an adapted Safe. Stack Minimizes number of privileged instructions executed Diversifies all memory Meets requirements for run-time, memory, and energy Open Sourced: https: //github. com/Hex. Hive/EPOXY 18 / 18
- Slides: 18