Proposed Cyber Security Framework for Tanzania Presenter Prof

Proposed Cyber Security Framework for Tanzania Presenter: Prof. Leonard J. Mselle The University of Dodoma (UDOM)

Preable 2 Cybersecurity posture: an approach or attitude towards cyber attack. It addresses questions such as; how are we prepared as a community if a cyber attack of national magnitude takes place? What will we do? How shall we do it? Who is going to do what? etc.

Preamble 3 So far in Tanzania we cannot, with absolute certainty, say we have a national cybersecurity posture commensurate to the magnitude of the problem. However some initiatives have been taken to move the nation towards an adequate posture.

A preamble 4 The discussion we are about to engage is part of the study that was sponsored by TCRA. It commenced in 2013 and ended in 2017. Among the outcomes of this work include;
A preamble 5 1. Design and implementation of 4 cybersecurity programs at UDOM Msc in network security Msc in digital forensics Bsc in cybersecurity and digital forensics Certificate in cybersecurity in collaboration with EC-Council

A preamble 6 2. Implementation of a cybersecurity LAB at UDOM, fully equipped with hardware, software and skilled LOCAL personnel 3. Formation of UDOM CERT which is manned by local cybersecurity professionals

Introduction 7 In this research we have proposed two fronts concerning national cyber security posture namely; 1. Military front 2. Civilian front In all cases these two fronts have been proposed to work closely together complementing each other.
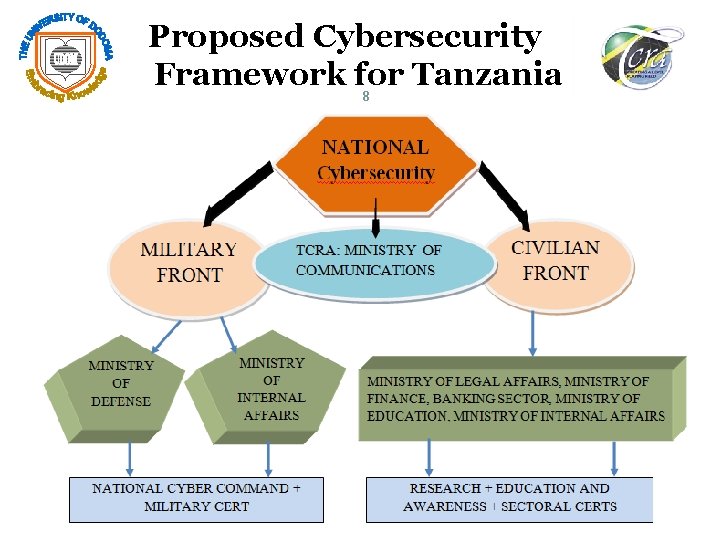
Proposed Cybersecurity Framework for Tanzania 8

The Military front 9 Several countries are aggressively taking serious steps in establishing a robust military cybesecurity posture due to the fact that for such countries wars in cyberspace are now a common phenomenon just like wars in air, land water. For the purpose of illustration, we shall employ the US approach on cybesecurity in the military front

The Military front 10 US cybesecurity in the military front ü For the US Army, cyber has an inherently military operational aspect, and the service is shaping its dedicated workforce to be 80% uniformed and 20% civilian employees and contractors. ü As an example, in 2013 US Navy cyber command recruited 800 cyber service members online to form a series of dedicated teams for Cybercom, and in the subsequent three years, the Navy cyber organization will bring on nearly 1, 000 more.

US cybesecurity in the military front 11 ü “Fully trained cyber warriors to U. S. Cyber Command, are required for operational focus areas: 1. Defending the nation, 2. Supporting the combatant commands 3. Defending the DOD information networks. ” Eric Rosenbach (commander in US cyber command)

US cybesecurity in the military front 12 The service teams are described as the command’s cyber mission forces, organized into: 1. National mission teams 2. Combat mission teams 3. Cyber protection teams.

The Military Front for Tanzania 13 ü USA is not alone in creating cyber battalions, China, Israel, Russia, Syria, North Korea and Iran are some examples that have seriously taken huge steps towards building cyber armies. ü Tanzania cannot wait for an invasion in its cyberspace to start organizing a cyber force. ü There are possibilities of building such a force if the decision is made.

The Civilian Front 14 As life in cyberspace is becoming more and more ubiquitous, collective defenses have become an imperative. The proposed model for cybersecurity in the civilian front, is Public Health Model adopted from Microsoft (2013).

The Civilian Front 15 The model contends that, as cyber security has matured over the past fifteen years, as individual defenses in cyberspace, such as firewalls, antivirus, and automatic updates, have become more commonly available and more commonly

The Civilian Front 16 while advances in technology and deployment have helped to mitigate risk in government and enterprise networks, it has proven insufficient for consumers, big and small businesses.

The Civilian Front 17 For various reasons, the awareness and availability of security products does not always result in their deployment and maintenance and, ultimately, results in inadequate risk management.

The Civilian Front 18 As a result, society needs to explore ways to implement collective defences to help protect consumers who may be unaware that their computers/smartphones have been compromised, and to reduce the risk that these comprised devices present to the ecosystem as a whole.

The Civilian Front 19 There are numerous international, and private sector efforts to promote or use collective defence that have had varying degrees of effectiveness Some examples include: 1. The International Telecommunications Union’s (ITU) 2. Japan’s Cyber Clean Center (CCC) 3. Signal Spam 4. The Finnish national Computer Emergency Response Team, CERT-FI 5. Project MARS (Microsoft Active Response for Security)

The Civilian Front 20 All of these efforts share a common commitment to help protect consumers and improve Internet health using individual and collective defenses. While each contributes to improving cyber security, these efforts have natural limitations.

Public Health Model 21 We propose to explore this model extensively to identify how it can be adopted in Tanzania in a more effective way.

Public Health Model 22 Some of the basic assumptions underpinning the PH model include; ü A single cyber attack, like a breakout of a pandemic (i. e. Avian flue), is contagious to the entire community. ü For this matter, any breakout is a concern for all society and it should not be left to the afflicted to decide what to do with the incident.

Public Health Model 23 It is the right of the public to be notified of the incident and to collectively take protective or curative measures. Most countries, in varying degrees, have put in place some arrangements to deal with education, detection, prevention and treatment in case of a health hazard (i. e. HIV aids, cholera, avian flue, Ebola, etc). üThe same arrangement is expected in case of cyber attack.

Public Health Model 24 Public health clinics are physical places known by the public as centres for reporting and receiving treatment for a given malady. Currently, as it appears, cybersecurity clinics mainly operate in the cyber space. This implies that the cybersecurity readiness can be detected through digital presence and its detectable digital capabilities.

Public Health Model 25 1. Challenge Questions: Can we, as a nation, comfortably contend that in case of a cyber threat/attack, such threat/attack can be reported, analyzed and collective measures can be taken to avert or mitigate the contagious effect of such threat/attack?

Public Health Model 26 2. Challenge Questions: Can we, as a nation, comfortably contend that we have arrangement that allows us to educate, detect, prevent our entities and the nation as a whole from possible unwanted cyber incidents?

Public Health Model 27 3. Challenge Questions: Can we, as a nation, comfortably contend that we have cybersecurity clinics that can be used by our public to report and get treatment in case of possible cyber attacks?

Public Health Model 28 An honest answer is NO. While we somehow can imagine what we will do as a nation if there is an Ebola outbreak, hardly we can provide one answer for the case of a cyber attack of national proportion.

Conclusion 29 In Tanzania, we already have a national cyber security awareness. However we cannot claim that we have achieved a credible national cybersecurity posture. So far the TCRA National CERT, is just a starting point. This was supposed to be supported by sectoral CERTs. So far, except for the one at UDOM, Sectoral CERTs are in our mind set.

Recommendations 30 What is needed now is to devise a national cybersecurity plan/initiative and turn this security initiative into action regardless of budget or time frame. There is a potential to build from the national CERT and SECTORAL CERTS (UDOM’s) and quickly improve our cybersecurity posture to a level commensurate to the threats we face.

THANK YOU END OF PRESENTATION Tuesday, April 01, 2014 31
- Slides: 31