PROOFPOINT MAIL SECURITY 1 2018 Proofpoint Inc Proofpoint











- Slides: 31

PROOFPOINT MAIL SECURITY 1 © 2018 Proofpoint, Inc.

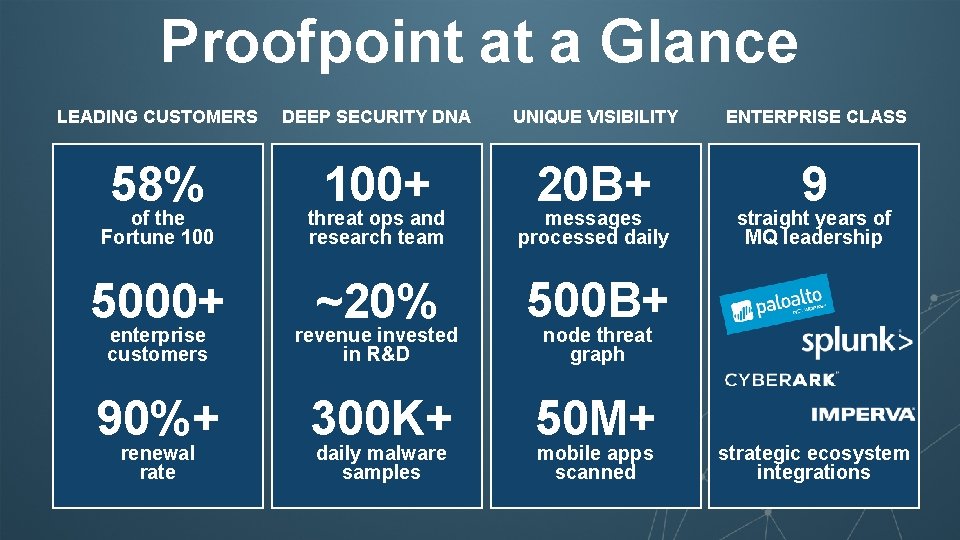
Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY ENTERPRISE CLASS 58% 100+ 20 B+ 9 of the Fortune 100 threat ops and research team messages processed daily 5000+ enterprise customers ~20% revenue invested in R&D 500 B+ 90%+ 300 K+ 50 M+ renewal rate daily malware samples straight years of MQ leadership node threat graph mobile apps scanned strategic ecosystem integrations 2 © 2018 Proofpoint, Inc.

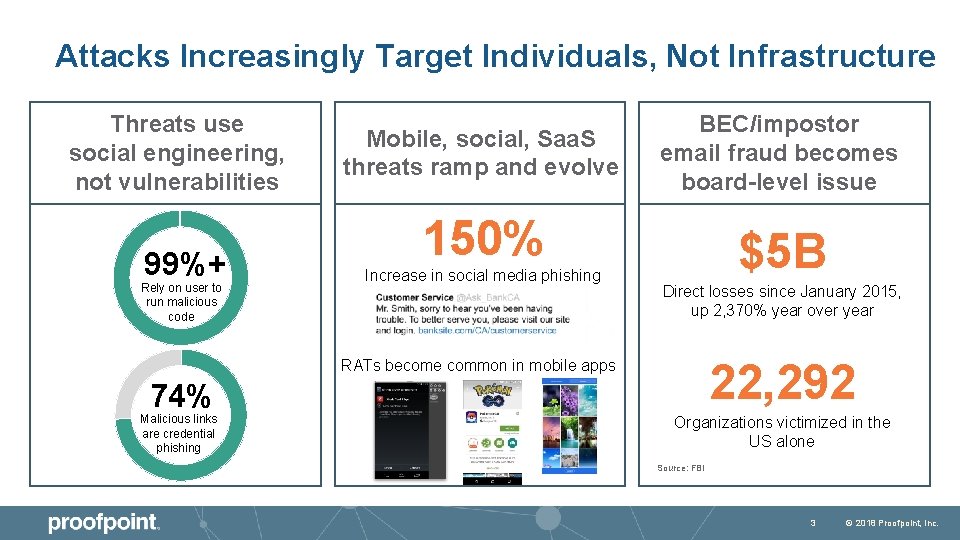
Attacks Increasingly Target Individuals, Not Infrastructure Threats use social engineering, not vulnerabilities 99%+ Rely on user to run malicious code Mobile, social, Saa. S threats ramp and evolve BEC/impostor email fraud becomes board-level issue 150% Increase in social media phishing $5 B Direct losses since January 2015, up 2, 370% year over year 22, 292 RATs become common in mobile apps 74% Malicious links are credential phishing Organizations victimized in the US alone Source: FBI 3 © 2018 Proofpoint, Inc.

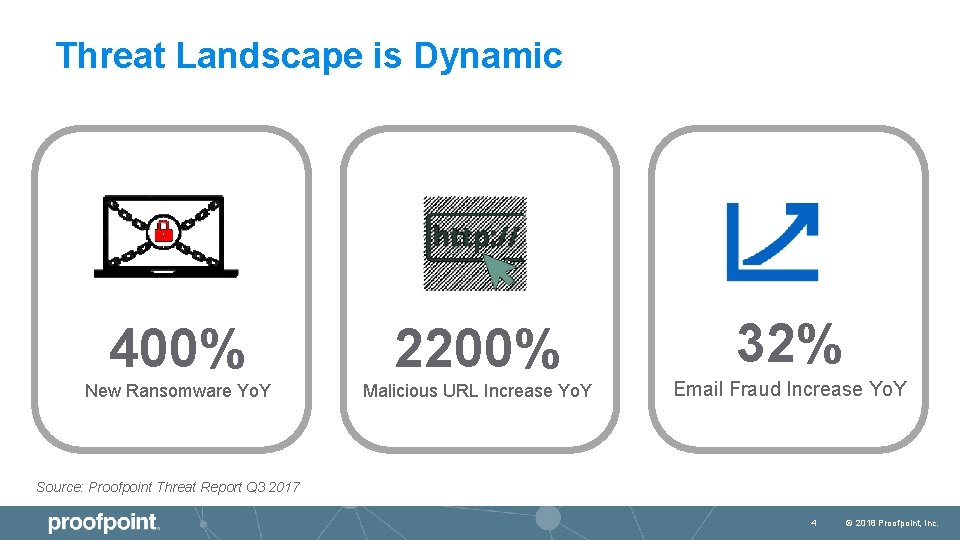
Threat Landscape is Dynamic 400% 2200% New Ransomware Yo. Y Malicious URL Increase Yo. Y 32% Email Fraud Increase Yo. Y Source: Proofpoint Threat Report Q 3 2017 Source: 3 Q 17 Proofpoint Threat Report 4 © 2018 Proofpoint, Inc.

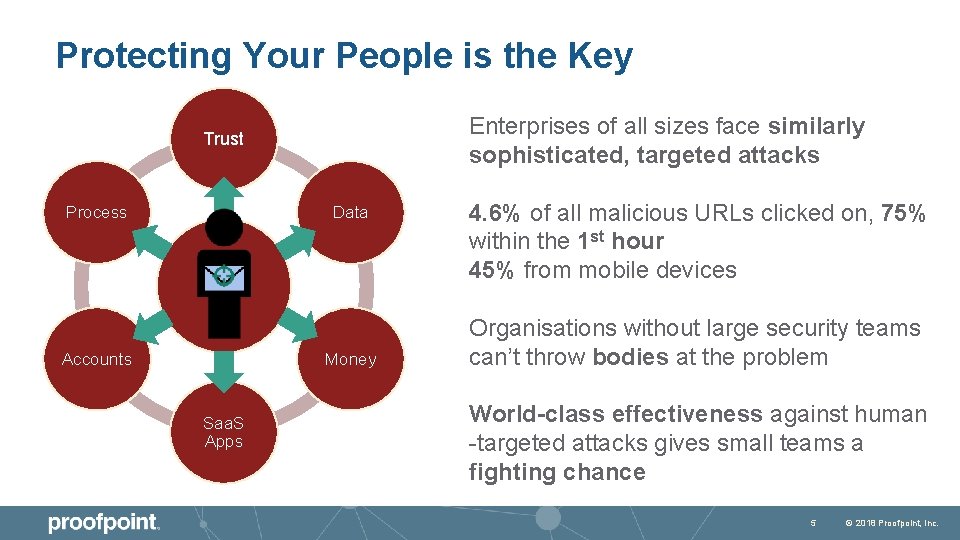
Protecting Your People is the Key Enterprises of all sizes face similarly sophisticated, targeted attacks Trust Process Data Accounts Money Saa. S Apps 4. 6% of all malicious URLs clicked on, 75% within the 1 st hour 45% from mobile devices Organisations without large security teams can’t throw bodies at the problem World-class effectiveness against human -targeted attacks gives small teams a fighting chance 5 © 2018 Proofpoint, Inc.

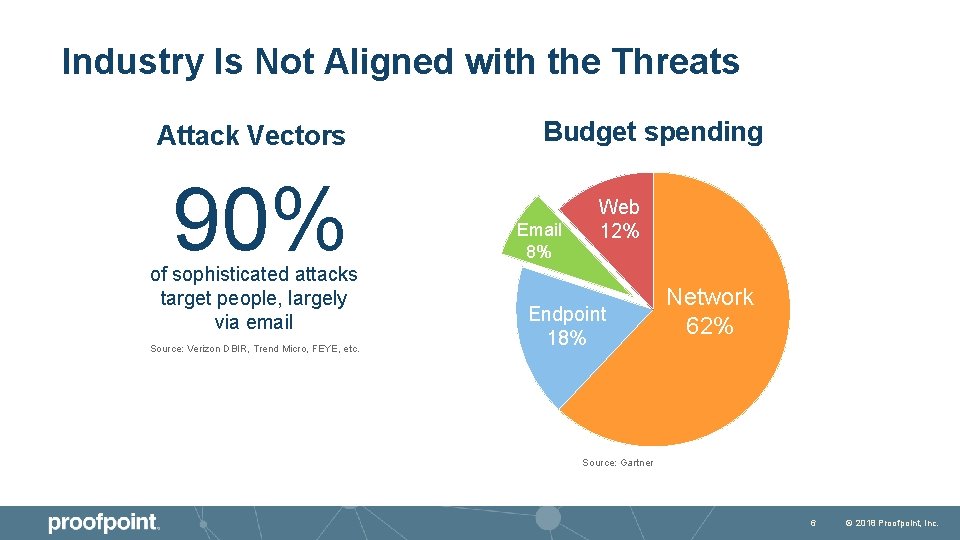
Industry Is Not Aligned with the Threats Attack Vectors 90% of sophisticated attacks target people, largely via email Source: Verizon DBIR, Trend Micro, FEYE, etc. Budget spending Email 8% Web 12% Endpoint 18% Network 62% Source: Gartner 6 © 2018 Proofpoint, Inc.

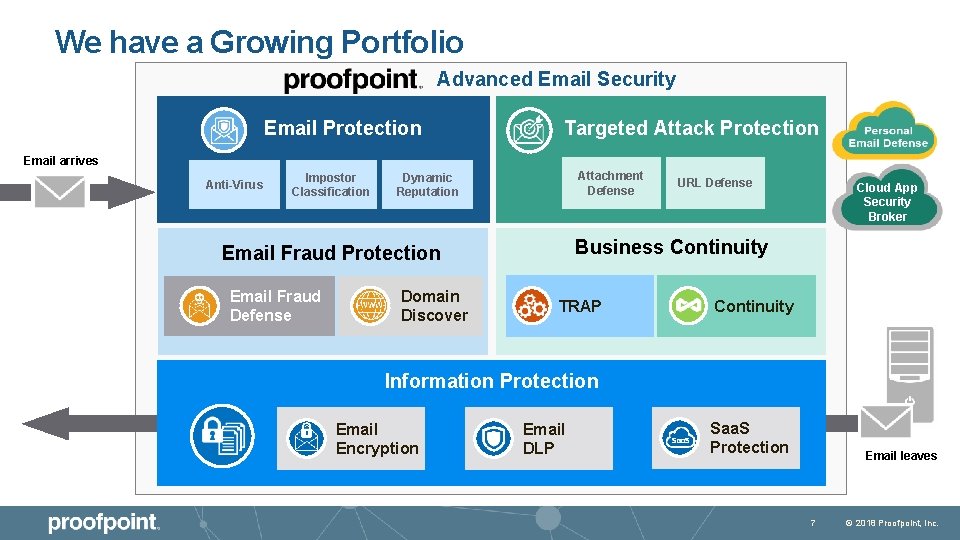
We have a Growing Portfolio Advanced Email Security Email Protection Targeted Attack Protection Email Security Email arrives Anti-Virus SPAM Virus Email Fraud Executive Impersonation Attachments Cloud App Security Broker URLs Business Continuity Protection Supply-chain Phishing Email Fraud Domain Email Fraud (BEC) Defense Discover Consumer Phishing Advanced Threats Attachment Advanced URLThreats Defense Malicious Impostor Dynamic Classification Reputation Malware DDOS Phishing Look Alike Business TRAP Response Continuity Remediation Continuity Information Protection Exfiltration Email. Protecting Insider Threats Regulatory Compliance Sensitive Saa. S Email Information Encryption DLP Protection Email leaves 7 © 2018 Proofpoint, Inc.

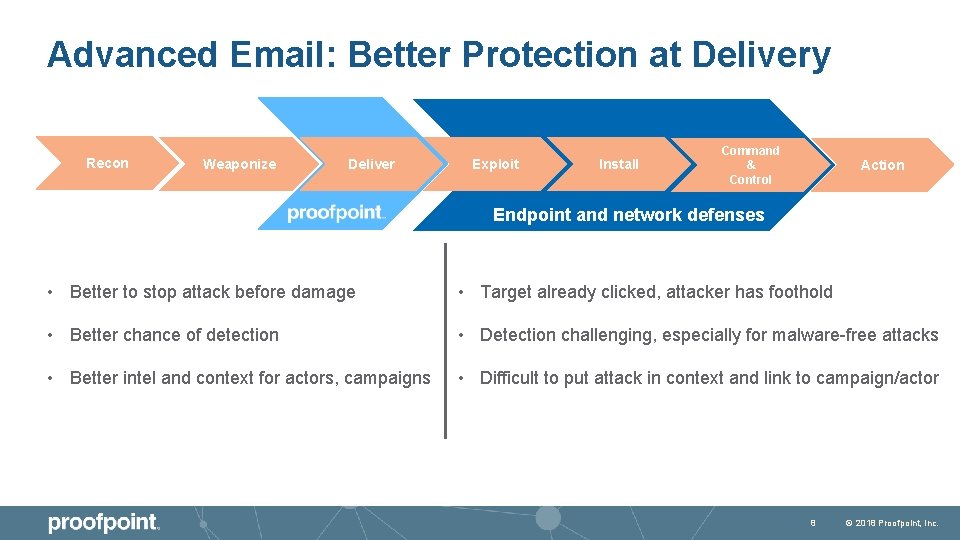
Advanced Email: Better Protection at Delivery Recon Weaponize Deliver Exploit Install Command & Control Action Endpoint and network defenses • Better to stop attack before damage • Target already clicked, attacker has foothold • Better chance of detection • Detection challenging, especially for malware-free attacks • Better intel and context for actors, campaigns • Difficult to put attack in context and link to campaign/actor 8 © 2018 Proofpoint, Inc.

Blocking Malware & Security Intelligence 9 © 2018 Proofpoint, Inc.

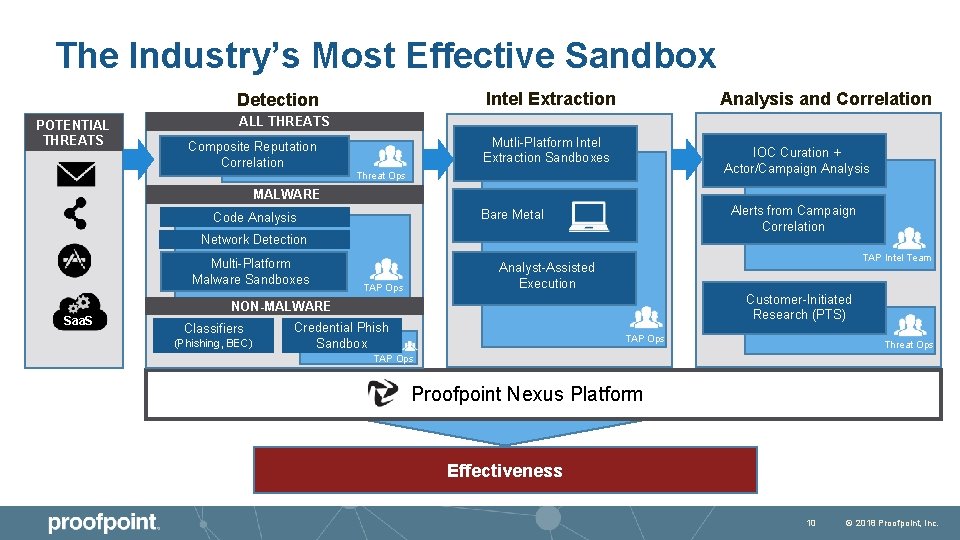
The Industry’s Most Effective Sandbox Intel Extraction Detection POTENTIAL THREATS Analysis and Correlation ALL THREATS Mutli-Platform Intel Extraction Sandboxes Composite Reputation Correlation IOC Curation + Actor/Campaign Analysis Threat Ops MALWARE Alerts from Campaign Correlation Bare Metal Code Analysis Network Detection Multi-Platform Malware Sandboxes TAP Intel Team Analyst-Assisted Execution TAP Ops Customer-Initiated Research (PTS) NON-MALWARE Saa. S Classifiers (Phishing, BEC) Credential Phish Sandbox TAP Ops Threat Ops TAP Ops Proofpoint Nexus Platform Effectiveness 10 © 2018 Proofpoint, Inc.

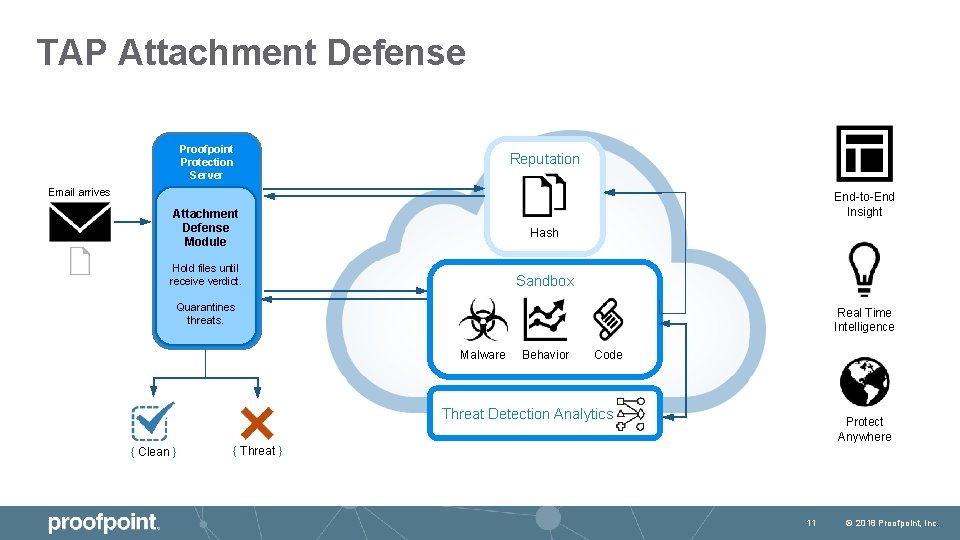
TAP Attachment Defense Proofpoint Protection Server Reputation Email arrives End-to-End Insight Attachment Defense Module Hash Hold files until receive verdict. Sandbox Quarantines threats. Real Time Intelligence Malware Behavior Code Threat Detection Analytics { Clean } Protect Anywhere { Threat } 11 © 2018 Proofpoint, Inc.

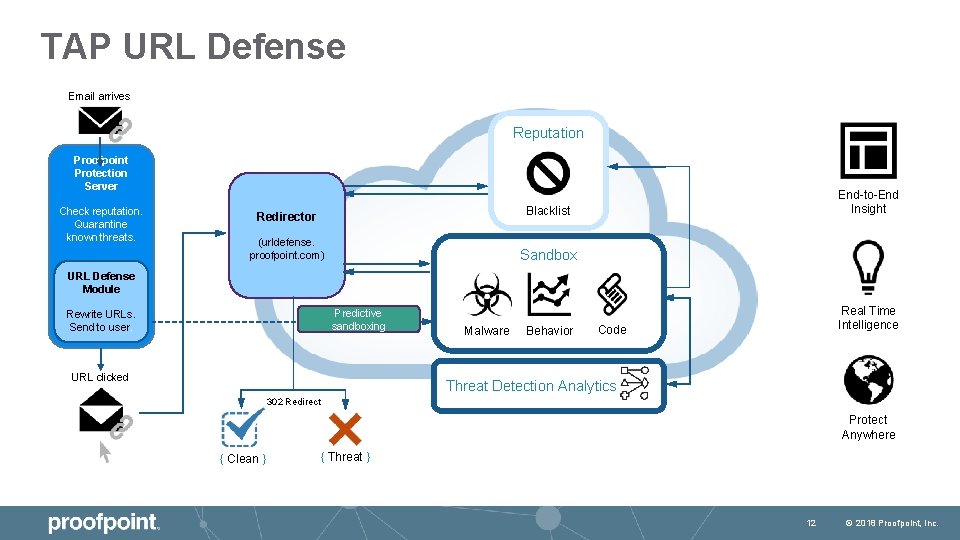
TAP URL Defense Email arrives Reputation Proofpoint Protection Server Check reputation. Quarantine known threats. End-to-End Insight Blacklist Redirector (urldefense. proofpoint. com) Sandbox URL Defense Module Predictive sandboxing Rewrite URLs. Send to user. URL clicked Malware Behavior Real Time Intelligence Code Threat Detection Analytics 302 Redirect Protect Anywhere { Clean } { Threat } 12 © 2018 Proofpoint, Inc.

Overview Essentials 13 © 2018 Proofpoint, Inc.

Proofpoint Essentials: 36, 000 CUSTOMERS 1. 6 M+ USERS Europe BEST SME SECURITY SOLUTION – June 2017 #1 in 3 rd PARTY TESTS SE LABS - AUGUST 2017 150% 18, 000 Yo. Y INCREASE IN CUSTOMERS Office 365 CUSTOMERS 14 © 2018 Proofpoint, Inc.

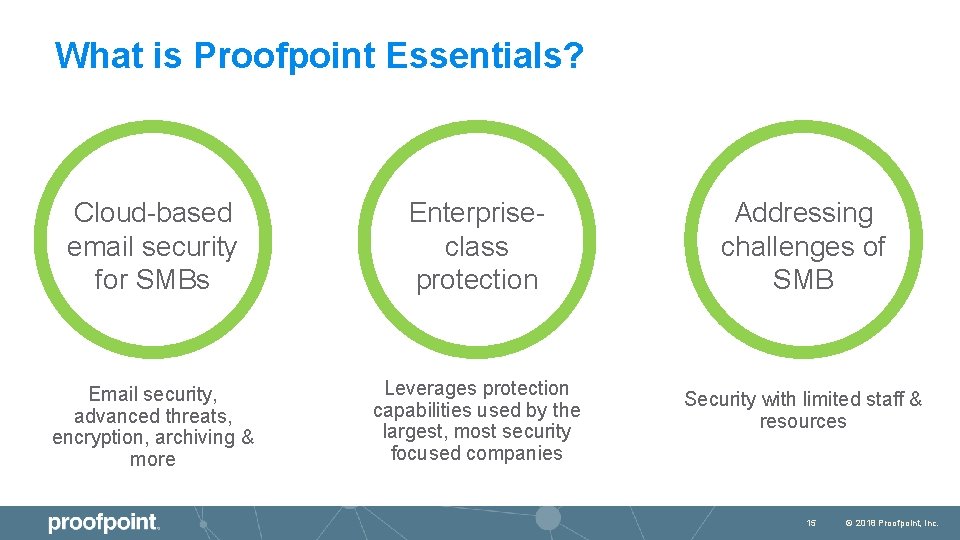
What is Proofpoint Essentials? Cloud-based email security for SMBs Enterpriseclass protection Email security, advanced threats, encryption, archiving & more Leverages protection capabilities used by the largest, most security focused companies Addressing challenges of SMB Security with limited staff & resources 15 © 2018 Proofpoint, Inc.

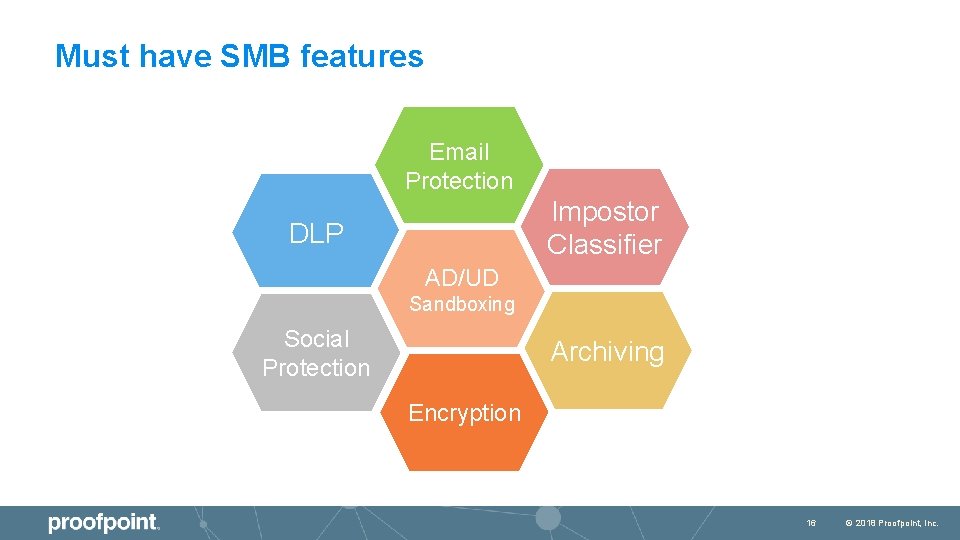
Must have SMB features Email Protection Impostor Classifier DLP AD/UD Sandboxing Social Protection Archiving Encryption 16 © 2018 Proofpoint, Inc.

Email Protection Deep Content Analysis Enterprise-class Protection Flexible Controls • • • Advanced anti-spam, phishing & email fraud Inbound & outbound content filtering • Dynamic reputation service leverages Global IP and URL Reputation Behavioral based zero-hour protection Easy to define controls Configurable by user, group and company-wide 17 © 2018 Proofpoint, Inc.

Advanced Threat Protection WWW. URL Defense Attachment Defense • • • Next Generation URL Sandboxing Follow-Me Protection (URL Rewrite) • Next Generation Attachment Sandboxing Utilizes visibility across all ADS customers Social Media Protection • • Protect up to 3 company social media accounts Automated removal of spam, malicious links or inappropriate content Protection and correlation across all major vectors – Proofpoint Nexus Threat Graph 18 © 2018 Proofpoint, Inc.

Information Protection: Email Encryption & Data Loss Prevention Smart Identifiers Defined dictionaries Analyze Email Content • • Detects content such as driving license numbers, credit cards or social security numbers Over 100 defined by default • Detects specific terms within content such as PHI, Source Code, Trading Over 20 defined dictionaries Includes message, attachments, email attributes Detect, block, and alert if confidential information is entering or leaving organization. 19 © 2018 Proofpoint, Inc.

Email Archiving Unlimited Storage Retention and Legal Hold Powerful Discovery Tools • • Fixed cost per user per year Up to 10 year retention Company and user-based legal hold • Company or individual user search Export archived email Easily capture and search email communications across the company in minutes. 20 © 2018 Proofpoint, Inc.

Disaster Recovery / Message Continuity Spooling & Failover Emergency Inbox Instant Replay • • Instant and automatic activation Always-on SMTP Deferral, Failover & Queue protection “Webmail” interface to send & receive email during server outages Redeliver inbound emails lost or deleted from your email server Maintain business during planned or unplanned email outage and downtime 21 © 2018 Proofpoint, Inc.

Easy to setup and management Simple setup • • • “Best practice” policies are enabled by default Embedded documentation and videos Setup assistance provided Multiple ways to import and manage users • • Auto-discovery users Sync users with AD Sync, Azure AD Unified experience • Single UI for admins, users; managing all components (email security, encryption, archiving) 22 © 2018 Proofpoint, Inc.

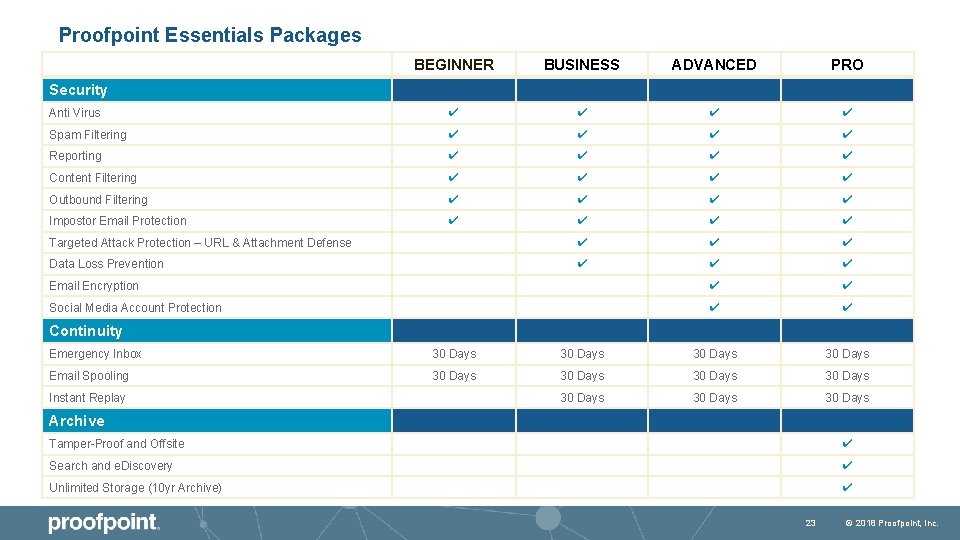
Proofpoint Essentials Packages BEGINNER BUSINESS ADVANCED PRO Anti Virus ✔ ✔ Spam Filtering ✔ ✔ Reporting ✔ ✔ Content Filtering ✔ ✔ Outbound Filtering ✔ ✔ Impostor Email Protection ✔ ✔ Targeted Attack Protection – URL & Attachment Defense ✔ ✔ ✔ Data Loss Prevention ✔ ✔ ✔ Email Encryption ✔ ✔ Social Media Account Protection ✔ ✔ Security Continuity Emergency Inbox 30 Days Email Spooling 30 Days 30 Days Instant Replay Archive Tamper-Proof and Offsite ✔ Search and e. Discovery ✔ Unlimited Storage (10 yr Archive) ✔ 23 © 2018 Proofpoint, Inc.

Proofpoint Essentials - Best Overall Value Superior Protection More Effective in all 3 rd party tests* Competitive Pricing Competitively priced across all packages Rapid On-boarding <60 minutes to full protection Easy Management Default policies, minimum configuration Fully Integrated Solution Integrated: security, privacy, continuity and archiving *See appendix 24 © 2018 Proofpoint, Inc.

Demonstration 25 © 2018 Proofpoint, Inc.

Discovering Threats Pre-POC 26 © 2018 Proofpoint, Inc.

POC Challenges § I’m Sure I’m Already Protected! § I’m Generally Happy With my Solution! § Incumbent Solution Embedded in Network Infrastructure! § Lengthy Change Control / Need a Compelling Reason to Move! 27 © 2018 Proofpoint, Inc.

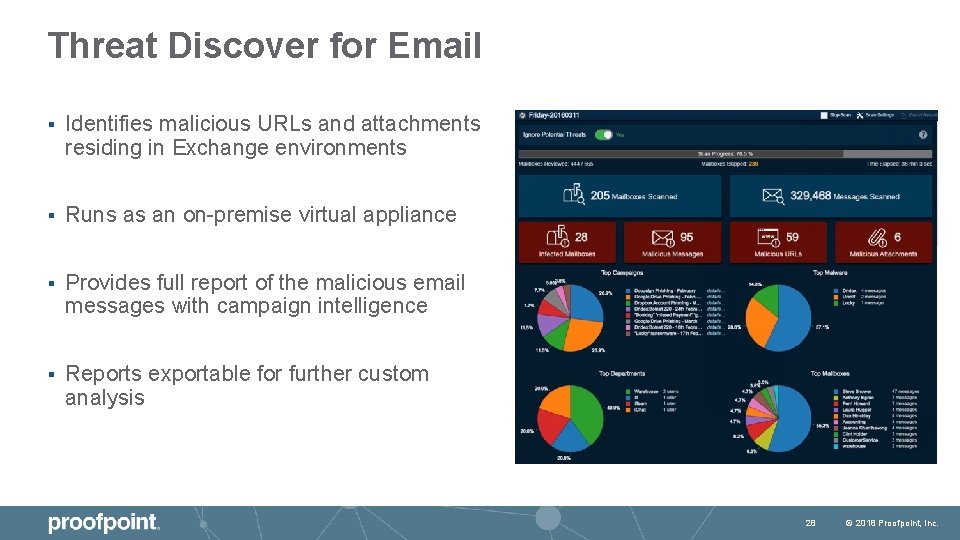
Threat Discover for Email § Identifies malicious URLs and attachments residing in Exchange environments § Runs as an on-premise virtual appliance § Provides full report of the malicious email messages with campaign intelligence § Reports exportable for further custom analysis 28 © 2018 Proofpoint, Inc.

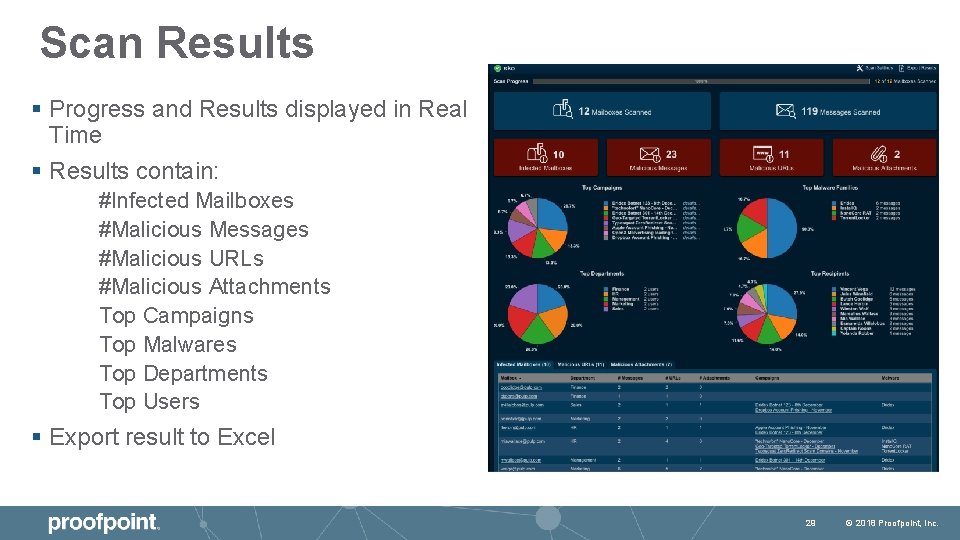
Scan Results § Progress and Results displayed in Real Time § Results contain: #Infected Mailboxes #Malicious Messages #Malicious URLs #Malicious Attachments Top Campaigns Top Malwares Top Departments Top Users § Export result to Excel 29 © 2018 Proofpoint, Inc.

Q&A 30 © 2018 Proofpoint, Inc.

31 © 2018 Proofpoint, Inc.