Program Analysis using Weighted Pushdown Systems Thomas Reps



![matched ( e [ e ] ] e ) [ ( e [ matched matched ( e [ e ] ] e ) [ ( e [ matched](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-9.jpg)
![Interprocedural Analysis JOVP(n) = V 0 start # f 1 p Matched. Paths. To[n] Interprocedural Analysis JOVP(n) = V 0 start # f 1 p Matched. Paths. To[n]](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-12.jpg)
![Representing Distributive Functions [RHS 95] Identity Function a b c f = λV. V Representing Distributive Functions [RHS 95] Identity Function a b c f = λV. V](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-13.jpg)
![Representing Distributive Functions [RHS 95] “Gen/Kill” Function a b c f = λV. (V Representing Distributive Functions [RHS 95] “Gen/Kill” Function a b c f = λV. (V](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-14.jpg)






![SPKI/SDSI Principals (Public Keys) KBob , KAlice Individuals KCS CS Department KOwner[R] Owner of SPKI/SDSI Principals (Public Keys) KBob , KAlice Individuals KCS CS Department KOwner[R] Owner of](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-23.jpg)
![Auth Certs A CS faculty member can use host H KOwner[H] KCS faculty Can Auth Certs A CS faculty member can use host H KOwner[H] KCS faculty Can](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-25.jpg)
![KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KCS faculty KBob my. Students KBob my. KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KCS faculty KBob my. Students KBob my.](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-26.jpg)
![KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob my. Students KAlice 30 KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob my. Students KAlice 30](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-27.jpg)
![KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KAlice my. Friends KBob my. Students Does KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KAlice my. Friends KBob my. Students Does](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-28.jpg)


![Basic Authorization-Access Query: <KOwner[H] , > Pre*({<K, □>, <K, ■>})? <KOwner[H] , > S Basic Authorization-Access Query: <KOwner[H] , > Pre*({<K, □>, <K, ■>})? <KOwner[H] , > S](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-49.jpg)
![{<KAlice, >, <KAlice, >} KOwner[H] KCS KBob { , KAlice } 61 {<KAlice, >, <KAlice, >} KOwner[H] KCS KBob { , KAlice } 61](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-53.jpg)
![Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-56.jpg)
![Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-57.jpg)
![Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-58.jpg)

![Certificate-Set-Analysis • Many more — see [JR 04] • Main message: Algorithms for model Certificate-Set-Analysis • Many more — see [JR 04] • Main message: Algorithms for model](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-61.jpg)

![Weighted Pushdown System (WPDS) [BET 03], [SJRS 03] States: { σ 1, σ 2 Weighted Pushdown System (WPDS) [BET 03], [SJRS 03] States: { σ 1, σ 2](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-63.jpg)
![Validity using a Weighted PDS Rule KOwner[D] KAlice Validity 10 20 Request Does KAlice Validity using a Weighted PDS Rule KOwner[D] KAlice Validity 10 20 Request Does KAlice](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-68.jpg)
![Validity using a Weighted PDS <KOwner[D], > 10 20 = max <KAlice, ■> max(10, Validity using a Weighted PDS <KOwner[D], > 10 20 = max <KAlice, ■> max(10,](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-69.jpg)
![“Auth Cert Reduction is Incomplete” [LM 03] Rule KOwner[D] KAlice Authorization {read} {write} Request “Auth Cert Reduction is Incomplete” [LM 03] Rule KOwner[D] KAlice Authorization {read} {write} Request](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-70.jpg)
![Authorization using a Weighted PDS <KOwner[D], > {read} Cert chain? ! {write} = <KAlice, Authorization using a Weighted PDS <KOwner[D], > {read} Cert chain? ! {write} = <KAlice,](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-71.jpg)
![Authorization using a Weighted PDS <KOwner[D], > {read} Cert tree! {write} = <KAlice, ■> Authorization using a Weighted PDS <KOwner[D], > {read} Cert tree! {write} = <KAlice, ■>](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-72.jpg)


![So What? Who Cares? [Yawn] • Check properties of programs using model checking – So What? Who Cares? [Yawn] • Check properties of programs using model checking –](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-77.jpg)






![Other Contributions • Differential propagation [SCP 05] – Weight domain + difference operator • Other Contributions • Differential propagation [SCP 05] – Weight domain + difference operator •](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-88.jpg)
- Slides: 88

Program Analysis using Weighted Pushdown Systems Thomas Reps, 1, 2 Akash Lal, 1 and Nick Kidd 1 1 Univ. of Wisconsin 2 Gramma. Tech, Inc.

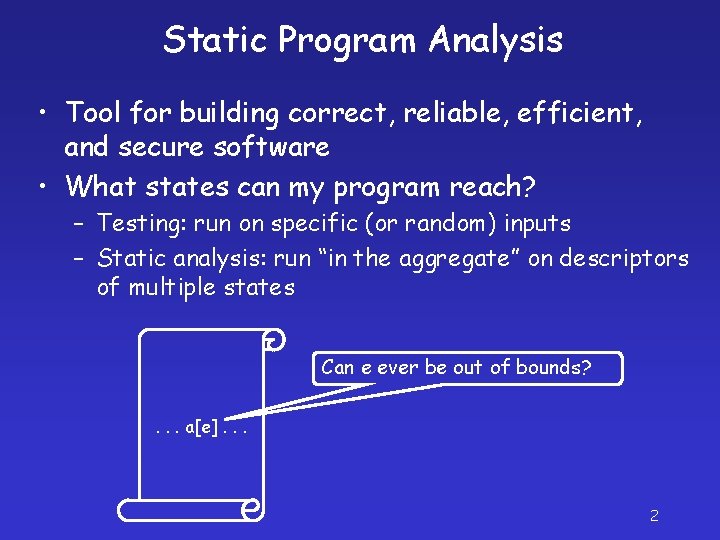
Static Program Analysis • Tool for building correct, reliable, efficient, and secure software • What states can my program reach? – Testing: run on specific (or random) inputs – Static analysis: run “in the aggregate” on descriptors of multiple states Can e ever be out of bounds? . . . a[e]. . . 2

Static Program Analysis • Tool for building correct, reliable, efficient, and secure software • What states can my program reach? – Testing: run on specific (or random) inputs – Static analysis: run “in the aggregate” on descriptors of multiple states Does the program conform to policy P? 3

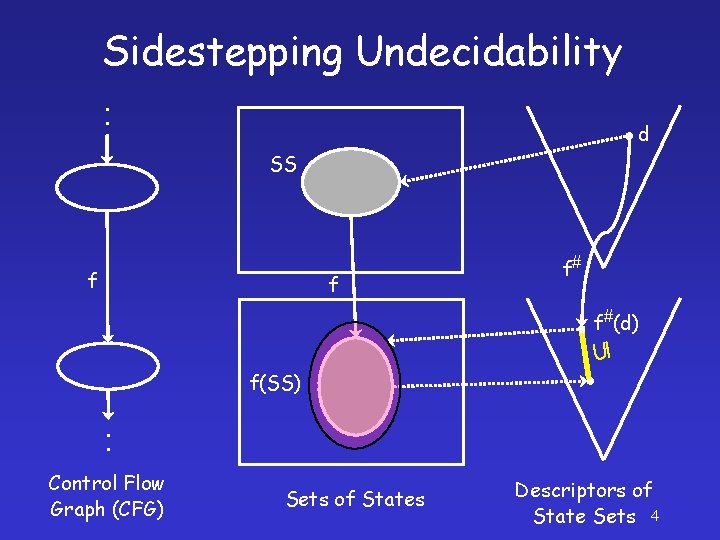
Sidestepping Undecidability ׃ d SS f f f# f#(d) f(SS) ׃ Control Flow Graph (CFG) Sets of States Descriptors of State Sets 4

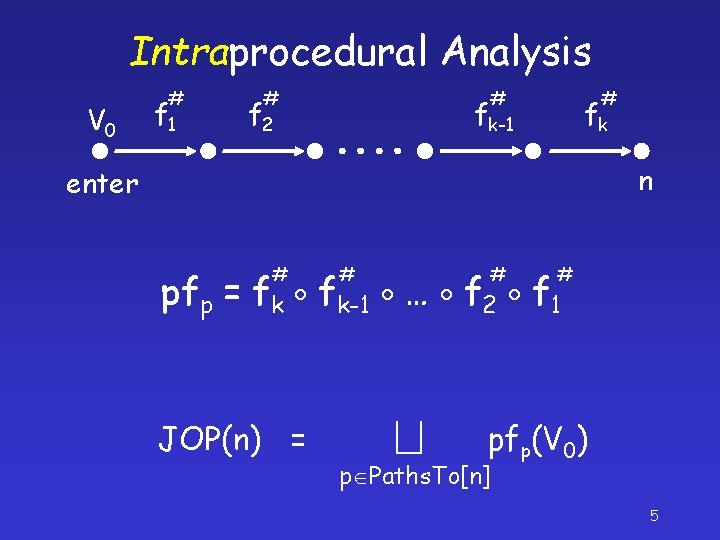
Intraprocedural Analysis V 0 # f 1 # f 2 # fk-1 # fk n enter # # pfp = fk fk-1 … f 2 f 1 JOP(n) = pfp(V 0) p Paths. To[n] 5

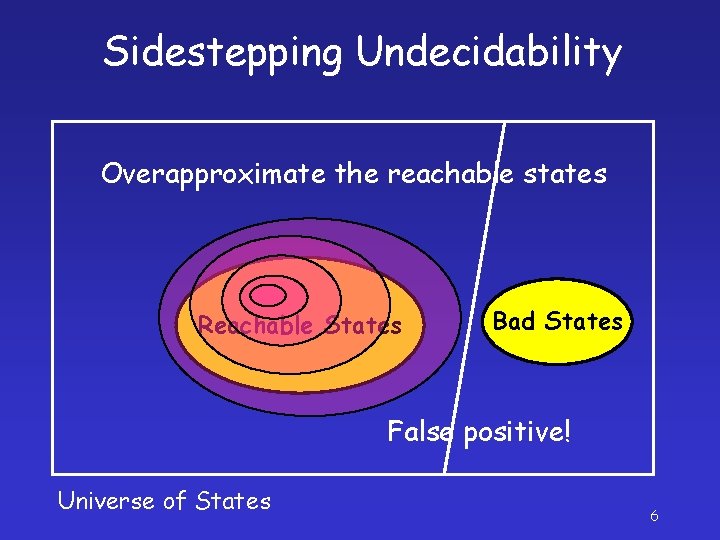
Sidestepping Undecidability Overapproximate the reachable states Reachable States Bad States False positive! Universe of States 6

Rest of the Talk: A Story From CFL-Reachability to Weighted Pushdown Systems T. Reps, S. Jha, S. Schwoon, N. Kidd, A. Lal, D. Melski, T. Touili, H. Wang, G. Balakrishnan, D. Gopan, J. Lim, S. Chaki, E. Clarke, S. Stubblebine • Prologue – Program analysis via CFL-reachability 7

• Aha! Our Story’s Theme: When the World Smiles on You – My problem P can be cast in formalism F, and I can use a known algorithm AF • Bonus – Can sometimes do more, now that you know that P is an F problem • Bummer – I want to do “something” that F doesn’t support • Ah! – Extend F to do “something” – Write new paper, which is interesting because of the connection to P – Discover that the extension has applications and/or applications in the original context (i. e. , F problems)8
![matched e e e e matched matched ( e [ e ] ] e ) [ ( e [ matched](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-9.jpg)
matched ( e [ e ] ] e ) [ ( e [ matched ] ( matched ) matched ] e s | | e e [ e ] ] e CFL-Reachability Ordinary Graph Reachability ) 9 t

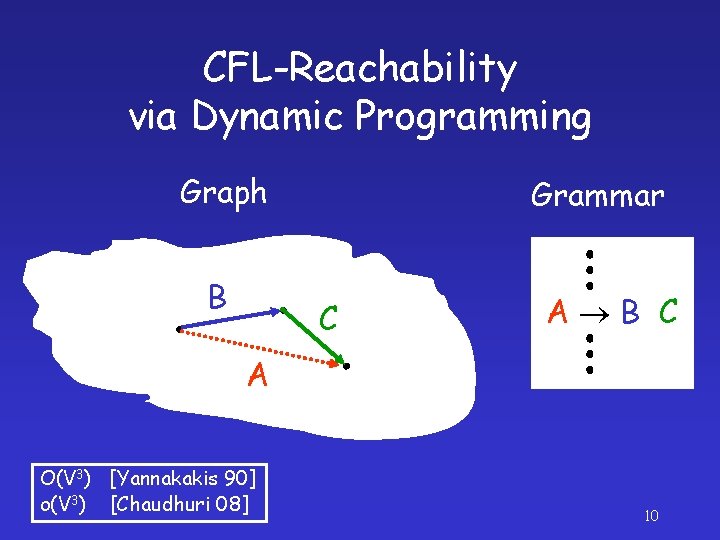
CFL-Reachability via Dynamic Programming Graph B Grammar C A B C A O(V 3) [Yannakakis 90] o(V 3) [Chaudhuri 08] 10

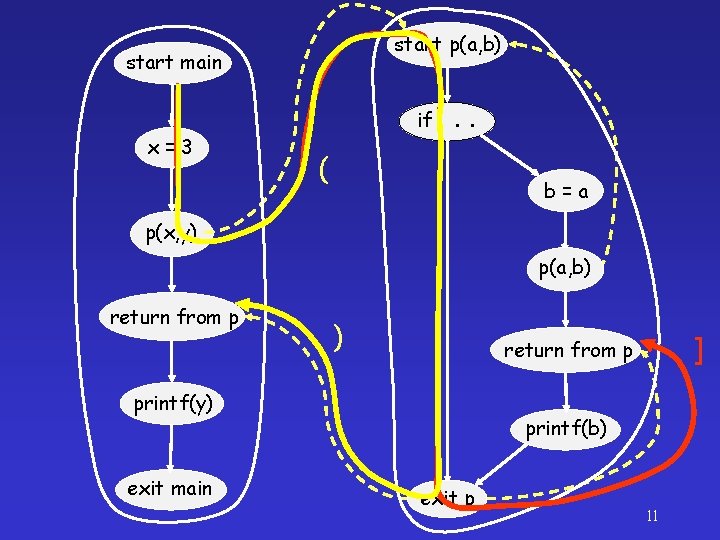
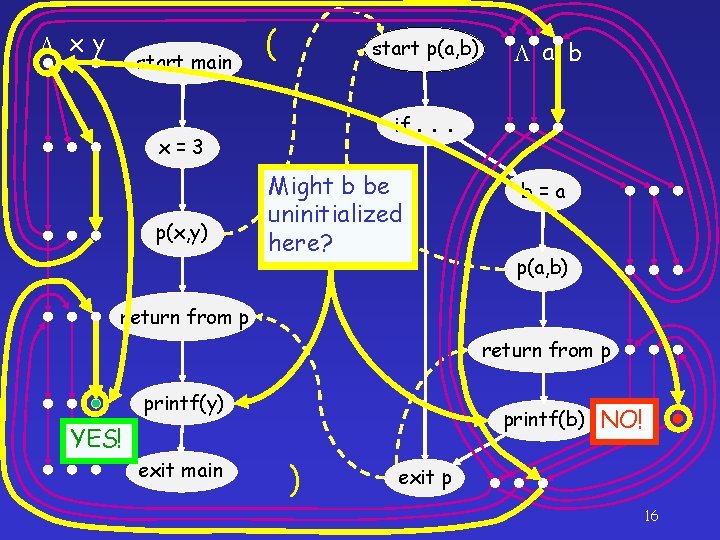
start p(a, b) start main x=3 if. . . ( b=a p(x, y) p(a, b) return from p ) printf(y) exit main ] return from p printf(b) exit p 11
![Interprocedural Analysis JOVPn V 0 start f 1 p Matched Paths Ton Interprocedural Analysis JOVP(n) = V 0 start # f 1 p Matched. Paths. To[n]](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-12.jpg)
Interprocedural Analysis JOVP(n) = V 0 start # f 1 p Matched. Paths. To[n] callq # f 2 # f 3 ( enterq ret ) pfp(V 0) # fk-1 # fk-2 # fk n exitq # f 4 # fk-3 # f 5 12
![Representing Distributive Functions RHS 95 Identity Function a b c f λV V Representing Distributive Functions [RHS 95] Identity Function a b c f = λV. V](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-13.jpg)
Representing Distributive Functions [RHS 95] Identity Function a b c f = λV. V f({a, b}) = {a, b} Constant Function f = λV. {b} f({a, b}) = {b} 13
![Representing Distributive Functions RHS 95 GenKill Function a b c f λV V Representing Distributive Functions [RHS 95] “Gen/Kill” Function a b c f = λV. (V](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-14.jpg)
Representing Distributive Functions [RHS 95] “Gen/Kill” Function a b c f = λV. (V {b}) {c} f({a, b}) = {a, c} Non-“Gen/Kill” Function f = λV. if a V then V {b} else V {b} f({a, b}) = {a, b} 14

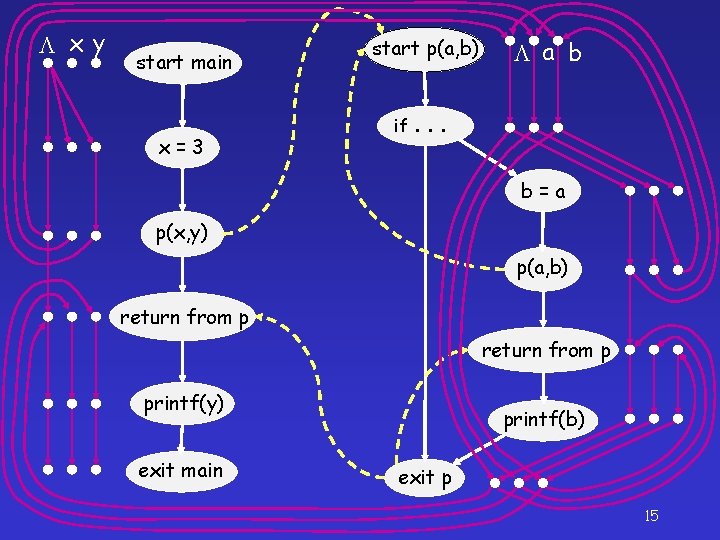
x y start main x=3 start p(a, b) if. a b . . b=a p(x, y) p(a, b) return from p printf(y) exit main printf(b) exit p 15

x y start main ( start p(a, b) if. x=3 p(x, y) a b . . Might b y be uninitialized here? b=a p(a, b) return from p printf(y) printf(b) YES! exit main ) NO! exit p 16

CFL-Reachability Advantages • Intuitive – good conceptual model for understanding many dataflow-analysis results • Linear-time algorithms for some variants 17

Rest of the Talk: A Story From CFL-Reachability to Weighted Pushdown Systems T. Reps, S. Jha, S. Schwoon, N. Kidd, A. Lal, D. Melski, T. Touili, H. Wang, G. Balakrishnan, D. Gopan, J. Lim, S. Chaki, E. Clarke, S. Stubblebine 20

Our Story • Prologue – Program analysis via CFL-reachability • Chapter 1 – Cubic-time algorithm for certificate-chain discovery in SPKI/SDSI: D. Clarke, J. -E. Elien, C. M. Ellison, M. Fredette, A. Morcos, and R. L. Rivest, Certificate chain discovery in SPKI/SDSI, JCS, 2001 21

Authorization to Use Shared Resources • Traditionally, use access control lists (ACLs) – Associate permissions with objects – E. g. , AFS permissions for directory D reps rlidwka touili rlidwk reps: students rl 22

Trust Management • Express security policy in a formal language – Digitally signed statements – Bob: Joe is my student [C 1] – Alice: All of Bob’s students can access host H [C 2] • Find a proof of authorization – “certificate-chain discovery” • Joe provides “proof of authorization” to Alice – C 1 + C 2 • Proof is checked and Joe is granted access – “compliance checking” • Examples: Keynote [Blaze et al. ], Referee [Chu et al. ], RT* [Li and Mitchell], SD 3 [Jim], Binder[De. Treville], 23 …

SPKI/SDSI • SPKI – Ellison, Frantz, Thomas, & Ylonen • SDSI – Lampson and Rivest • SPKI/SDSI – Ellison, Frantz, Lampson, Rivest, Thomas, & Ylonen – Local name spaces reps student spouse – Delegation 24
![SPKISDSI Principals Public Keys KBob KAlice Individuals KCS CS Department KOwnerR Owner of SPKI/SDSI Principals (Public Keys) KBob , KAlice Individuals KCS CS Department KOwner[R] Owner of](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-23.jpg)
SPKI/SDSI Principals (Public Keys) KBob , KAlice Individuals KCS CS Department KOwner[R] Owner of resource R Local Names KCS faculty KBob my. Students Extended Names KBob my. Students Spouse 25

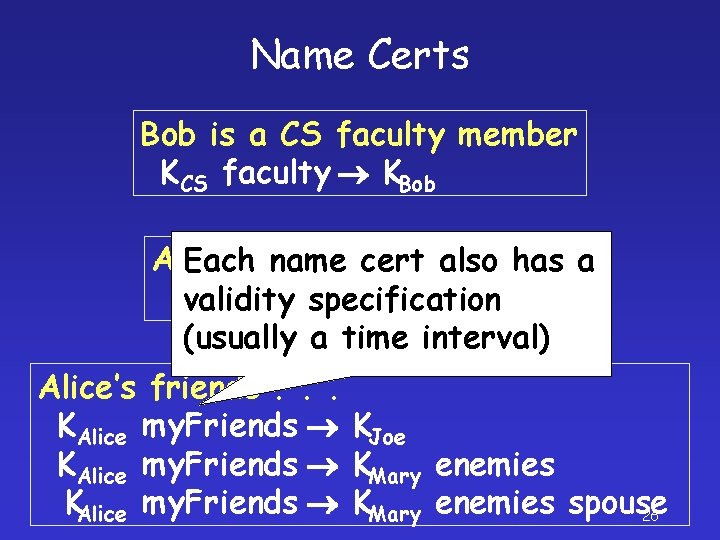
Name Certs Bob is a CS faculty member KCS faculty KBob Alice a student of Bob’s Eachis name cert also has a Kvalidity KAlice specification Bob my. Students (usually a time interval) Alice’s friends. . . KAlice my. Friends KJoe KAlice my. Friends KMary enemies spouse 26
![Auth Certs A CS faculty member can use host H KOwnerH KCS faculty Can Auth Certs A CS faculty member can use host H KOwner[H] KCS faculty Can](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-25.jpg)
Auth Certs A CS faculty member can use host H KOwner[H] KCS faculty Can delegate Bob allows access to his students KBob my. Students Cannot delegate Alice allows access to her friends KAlice my. Friends 27
![KOwnerH Certificate Chain KOwnerH KCS faculty KBob KCS faculty KBob my Students KBob my KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KCS faculty KBob my. Students KBob my.](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-26.jpg)
KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KCS faculty KBob my. Students KBob my. Students KAlice 29
![KOwnerH Certificate Chain KOwnerH KCS faculty KBob my Students KAlice 30 KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob my. Students KAlice 30](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-27.jpg)
KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob my. Students KAlice 30
![KOwnerH Certificate Chain KOwnerH KCS faculty KBob KAlice my Friends KBob my Students Does KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KAlice my. Friends KBob my. Students Does](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-28.jpg)
KOwner[H] Certificate Chain KOwner[H] KCS faculty KBob KAlice my. Friends KBob my. Students Does not apply! KBob my. Students KAlice 31

Basic Authorization-Access Query • Given a resource R and principal K, is K authorized to access R? Solved by finding a certificate chain that proves that access is permitted (certificate -chain discovery) Cubic-time algorithm: Clarke, Elien, Ellison, Fredette, Morcos, & Rivest [JCS 01] 32

Our Story • Prologue – Program analysis via CFL-reachability • Chapter 1 – Cubic-time algorithm for certificate-chain discovery in SPKI/SDSI [CEEFMR 01] • Chapter 2 (Aha!) – September 2001: Jha and Reps discuss Clarke et al. paper and see the connection between certificate-chain discovery and modelchecking pushdown systems (PDSs) – New application for PDS formalism; previously • PDSs describe the call-return structure of programs • PDS model checking: establish properties of recursive programs 33

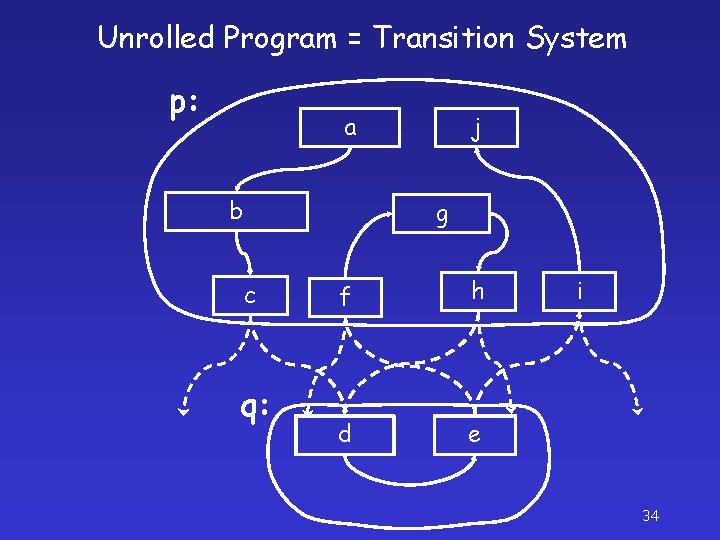
Unrolled Program = Transition System p: a b j g c q: f h d e i 34

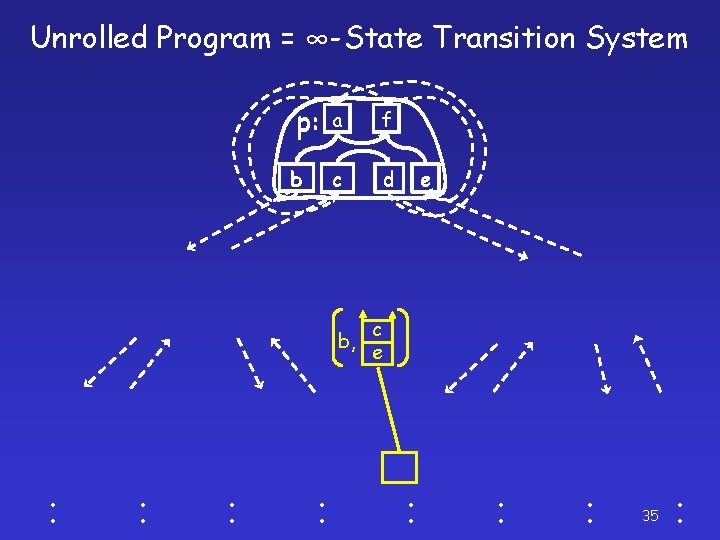
Unrolled Program = ∞-State Transition System p: a f b c d b, ׃ ׃ e c e ׃ ׃ ׃ 35 ׃

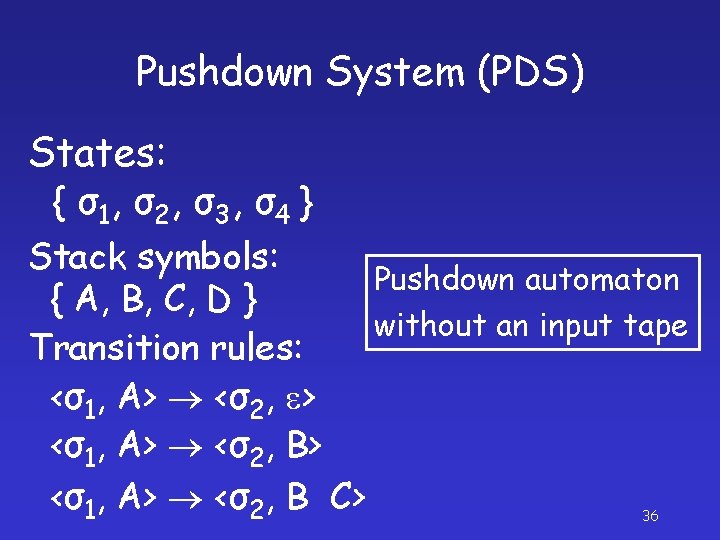
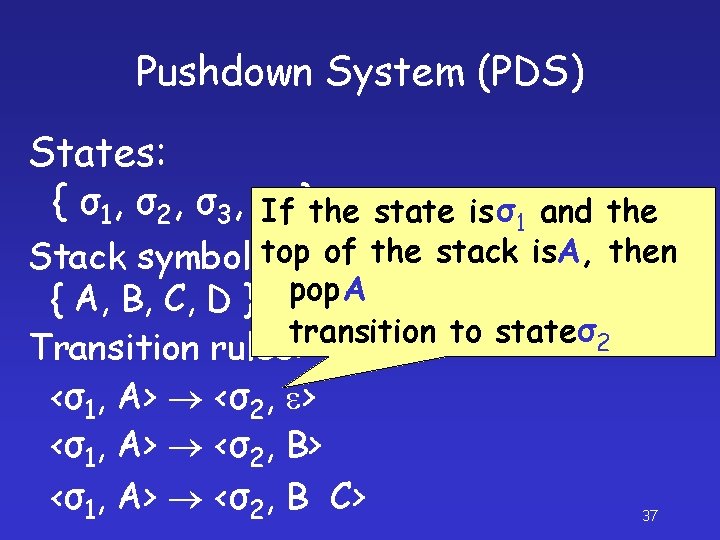
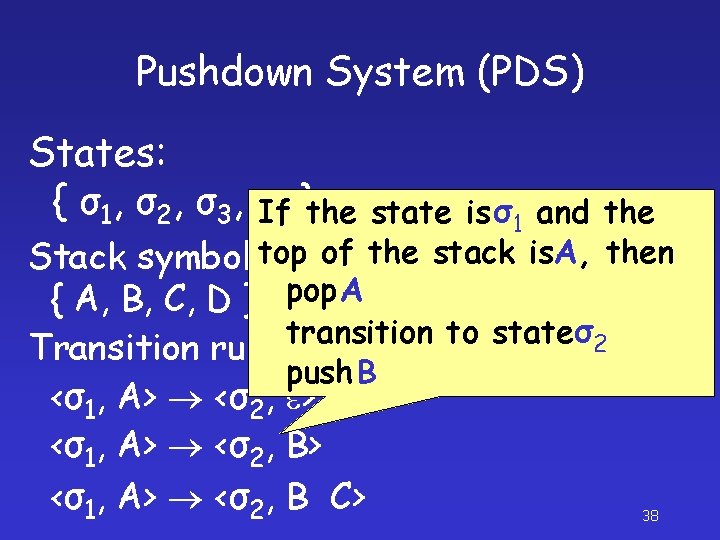
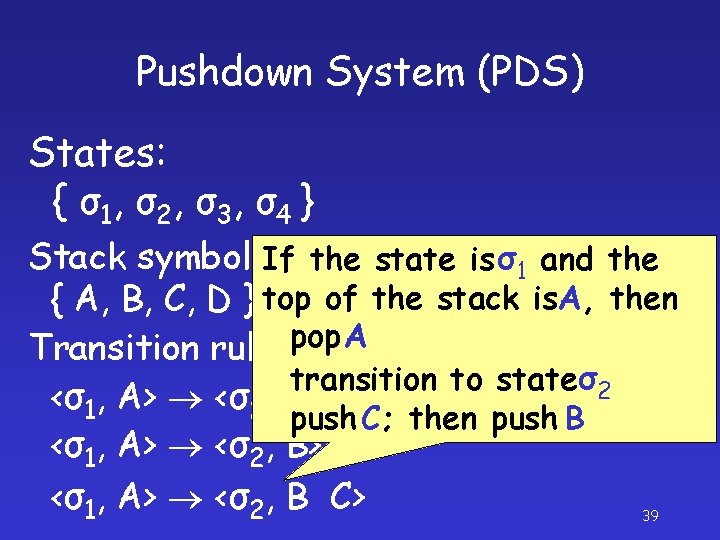
Pushdown System (PDS) States: { σ 1, σ 2 , σ 3 , σ 4 } Stack symbols: Pushdown automaton { A, B, C, D } without an input tape Transition rules: <σ1, A> <σ2, e> <σ1, A> <σ2, B C> 36

Pushdown System (PDS) States: { σ1, σ2, σ3, σIf 4 }the state is σ1 and the top of the stack is. A, then Stack symbols: Pushdown automaton pop A { A, B, C, D } without an input transition to state σ2 tape Transition rules: <σ1, A> <σ2, e> <σ1, A> <σ2, B C> 37

Pushdown System (PDS) States: { σ1, σ2, σ3, σIf 4 }the state is σ1 and the top of the stack is. A, then Stack symbols: Pushdown automaton pop A { A, B, C, D } without an input tape transition to state σ 2 Transition rules: push B <σ1, A> <σ2, e> <σ1, A> <σ2, B C> 38

Pushdown System (PDS) States: { σ 1, σ 2 , σ 3 , σ 4 } Stack symbols: If the state is σ1 and the Pushdown automaton { A, B, C, D } top of the stack is. A, then without an input tape pop A Transition rules: transition to stateσ2 <σ1, A> <σ2, e> push C; then push B <σ1, A> <σ2, B> <σ1, A> <σ2, B C> 39

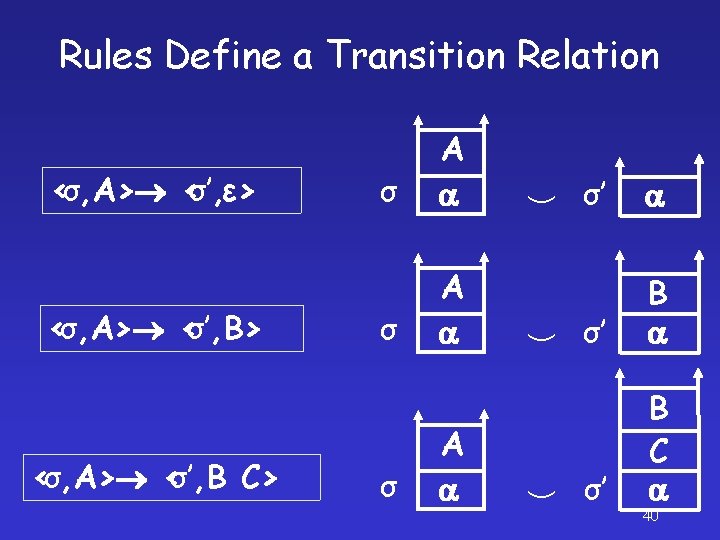
Rules Define a Transition Relation <σ, A> <σ’, ε> <σ, A> <σ’, B C> σ A σ’ σ’ B C 40

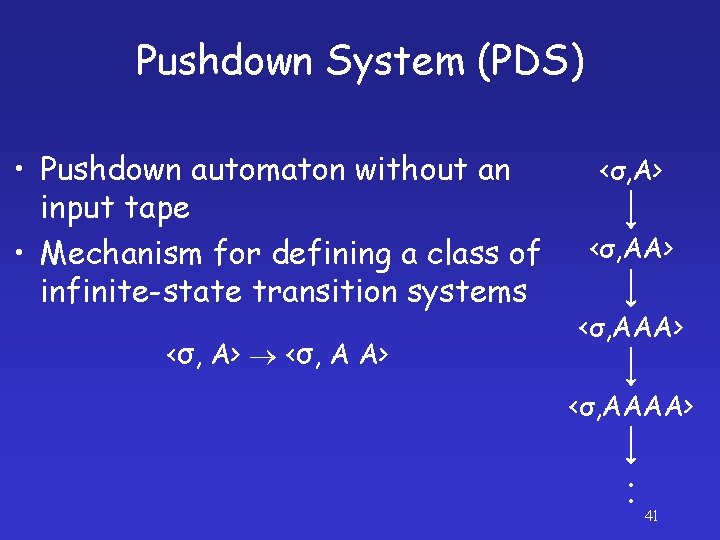
Pushdown System (PDS) • Pushdown automaton without an input tape • Mechanism for defining a class of infinite-state transition systems <σ, A> <σ, A A> <σ, AA> <σ, AAAA> ׃ 41

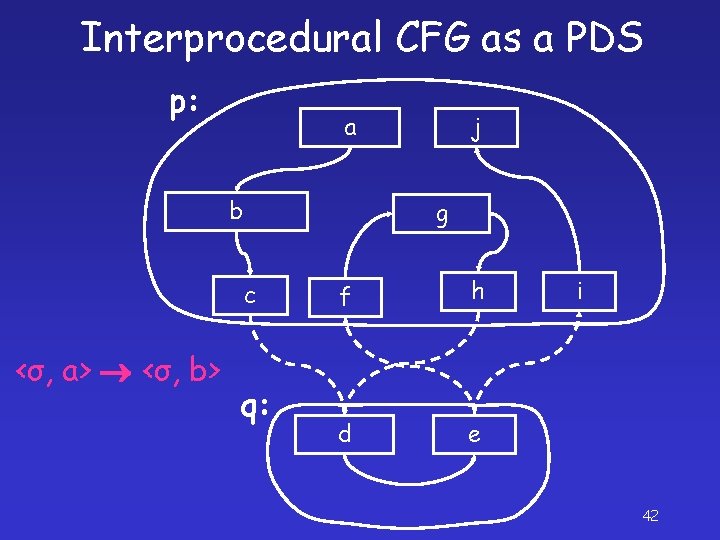
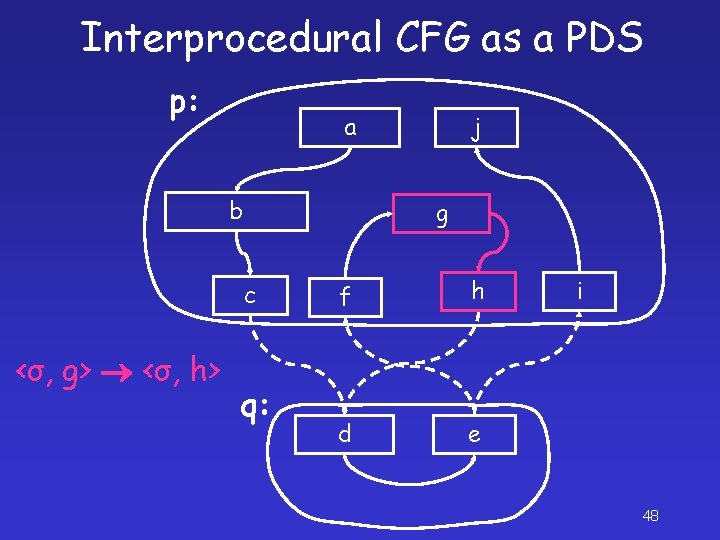
Interprocedural CFG as a PDS p: a b g c <σ, a> <σ, b> j q: f h d e i 42

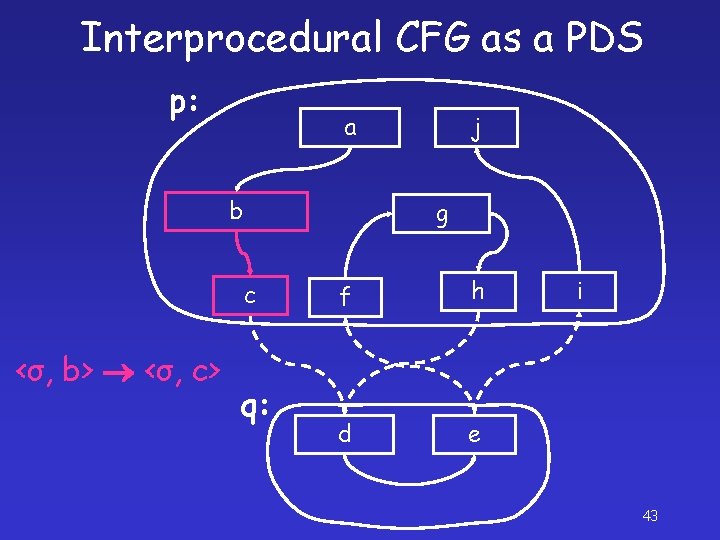
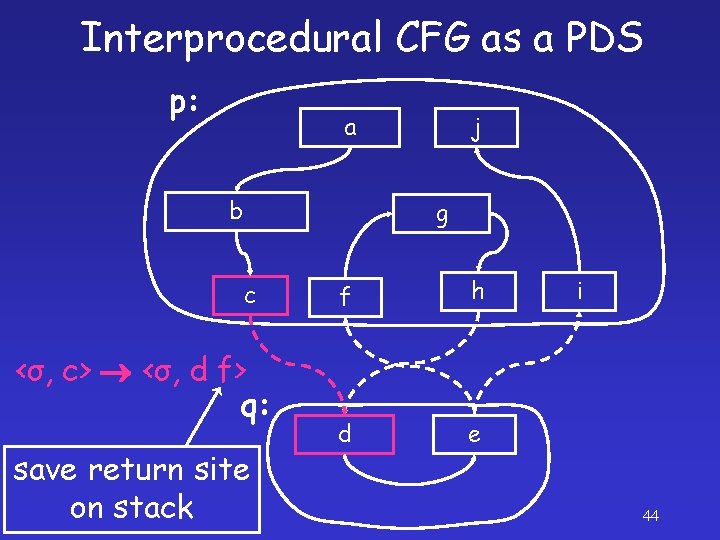
Interprocedural CFG as a PDS p: a b g c <σ, b> <σ, c> j q: f h d e i 43

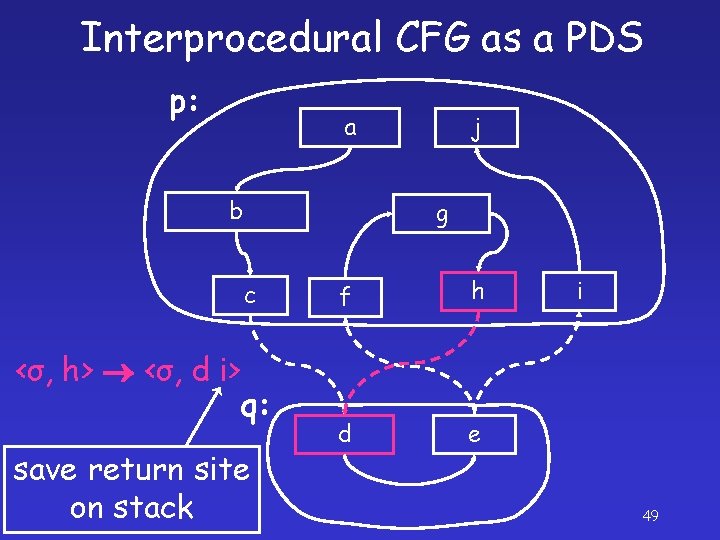
Interprocedural CFG as a PDS p: a b j g c <σ, c> <σ, d f> q: save return site on stack f h d e i 44

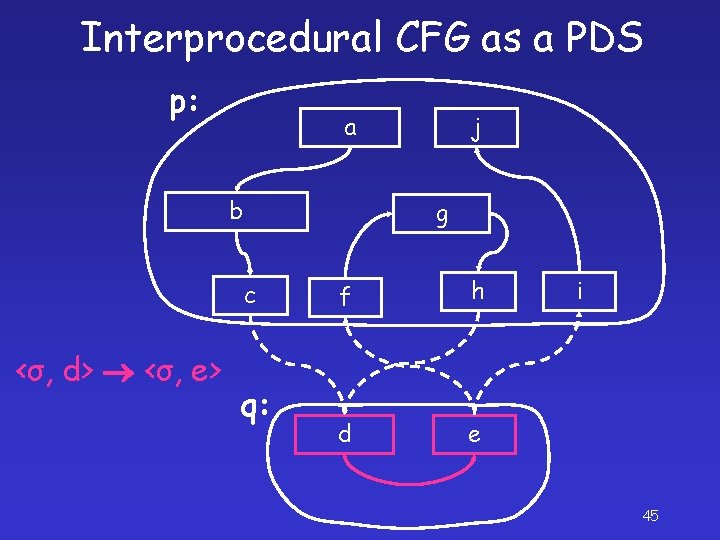
Interprocedural CFG as a PDS p: a b g c <σ, d> <σ, e> j q: f h d e i 45

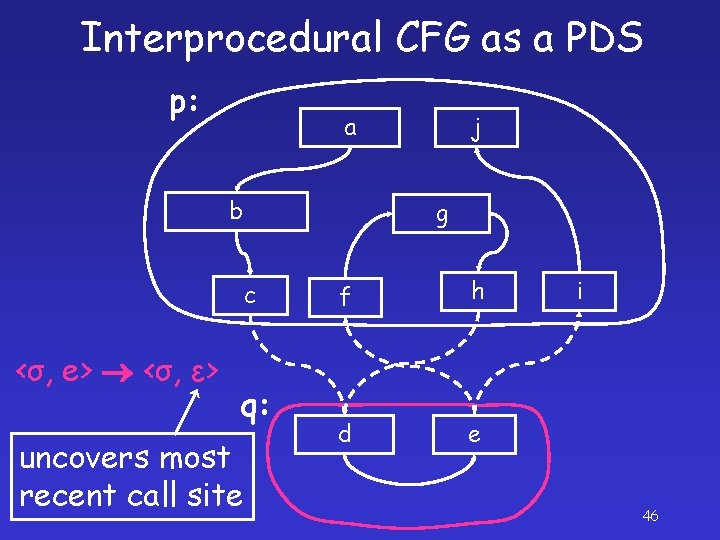
Interprocedural CFG as a PDS p: a b g c <σ, e> <σ, ε> q: uncovers most recent call site j f h d e i 46

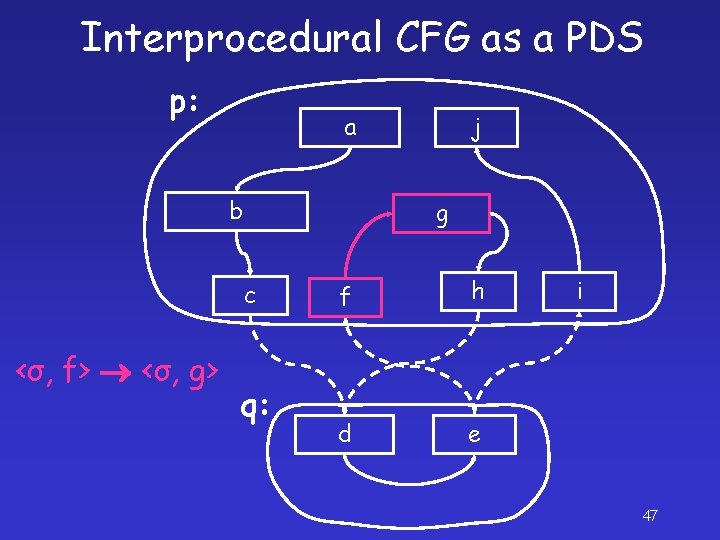
Interprocedural CFG as a PDS p: a b g c <σ, f> <σ, g> j q: f h d e i 47

Interprocedural CFG as a PDS p: a b g c <σ, g> <σ, h> j q: f h d e i 48

Interprocedural CFG as a PDS p: a b j g c <σ, h> <σ, d i> q: save return site on stack f h d e i 49

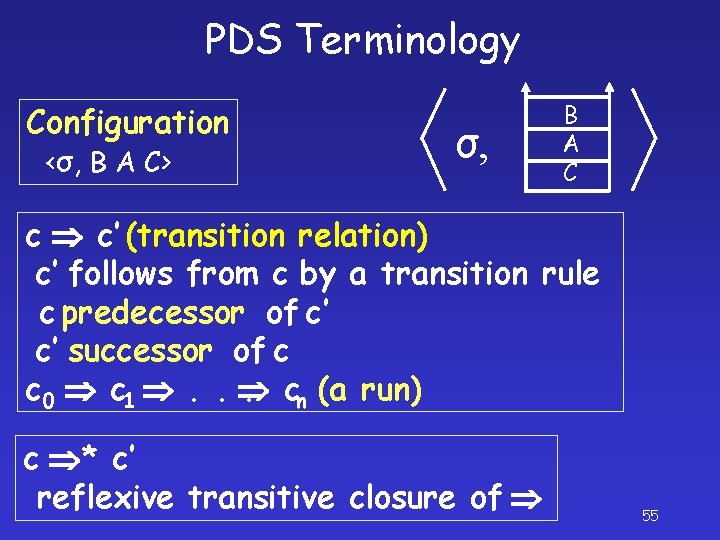
PDS Terminology Configuration <σ, B A C> σ, B A C c c’ (transition relation) c’ follows from c by a transition rule c predecessor of c’ c’ successor of c c 0 c 1 . . . cn (a run) c * c’ reflexive transitive closure of 55

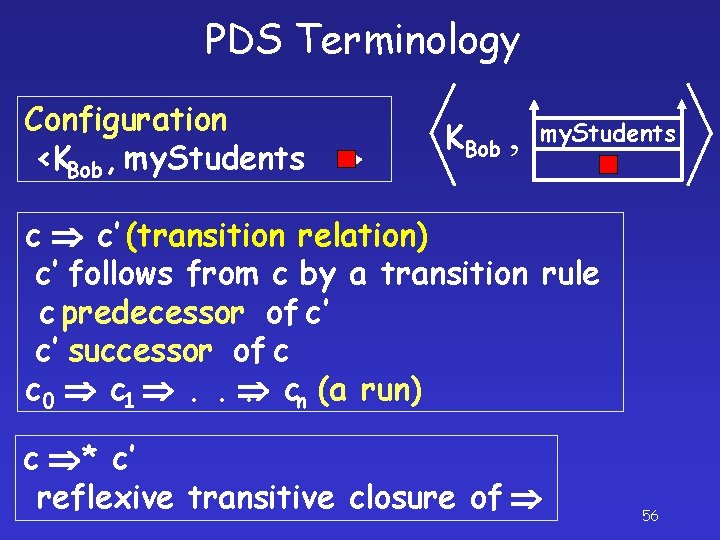
PDS Terminology Configuration <KBob , my. Students > KBob , my. Students c c’ (transition relation) c’ follows from c by a transition rule c predecessor of c’ c’ successor of c c 0 c 1 . . . cn (a run) c * c’ reflexive transitive closure of 56
![Basic AuthorizationAccess Query KOwnerH PreK K KOwnerH S Basic Authorization-Access Query: <KOwner[H] , > Pre*({<K, □>, <K, ■>})? <KOwner[H] , > S](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-49.jpg)
Basic Authorization-Access Query: <KOwner[H] , > Pre*({<K, □>, <K, ■>})? <KOwner[H] , > S = {<K, □>, <K, ■>} Pre*(S) 57

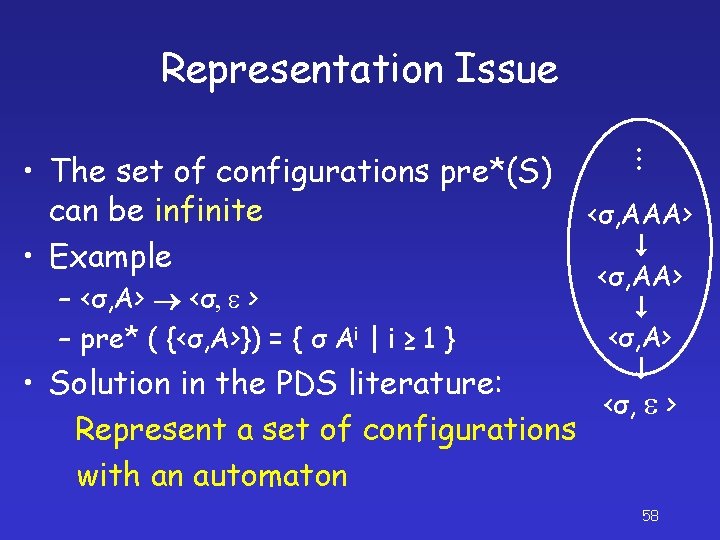
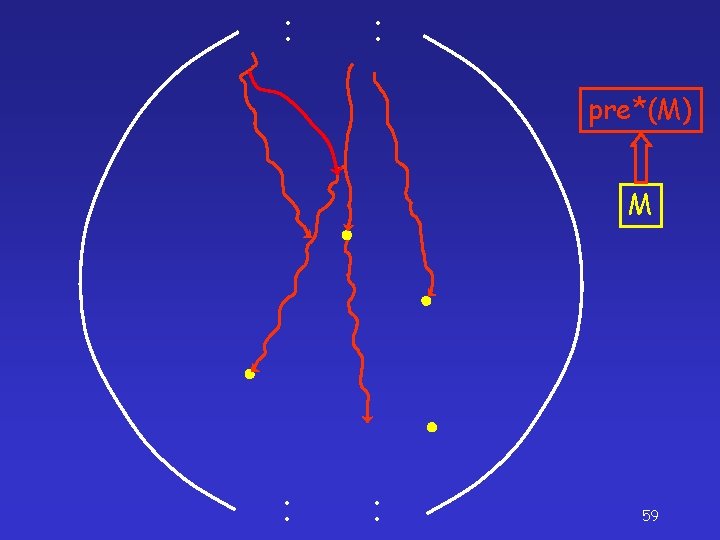
Representation Issue – <σ, A> <σ, e > – pre* ( {<σ, A>}) = { σ Ai | i ≥ 1 } . . . • The set of configurations pre*(S) can be infinite • Example <σ, AAA> <σ, A> • Solution in the PDS literature: <σ, e > Represent a set of configurations with an automaton 58


![KAlice KAlice KOwnerH KCS KBob KAlice 61 {<KAlice, >, <KAlice, >} KOwner[H] KCS KBob { , KAlice } 61](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-53.jpg)
{<KAlice, >, <KAlice, >} KOwner[H] KCS KBob { , KAlice } 61

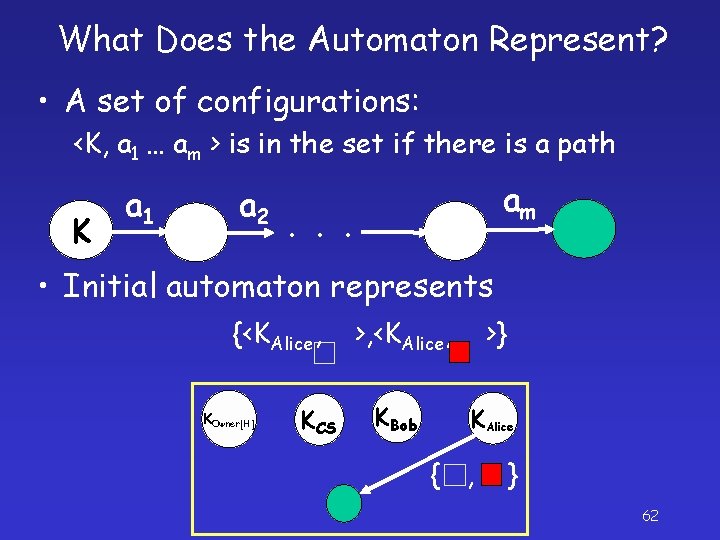
What Does the Automaton Represent? • A set of configurations: <K, a 1 … am > is in the set if there is a path K a 1 a 2 am . . . • Initial automaton represents {<KAlice, KOwner[H] KCS >, <KAlice, >} KBob KAlice { , } 62

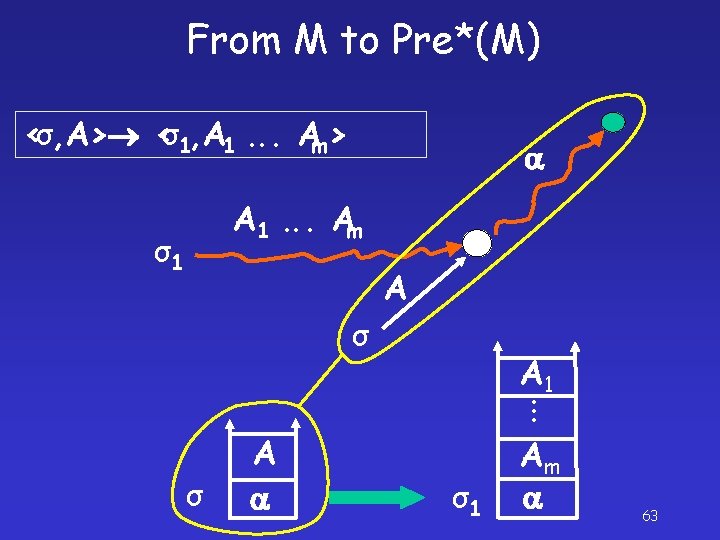
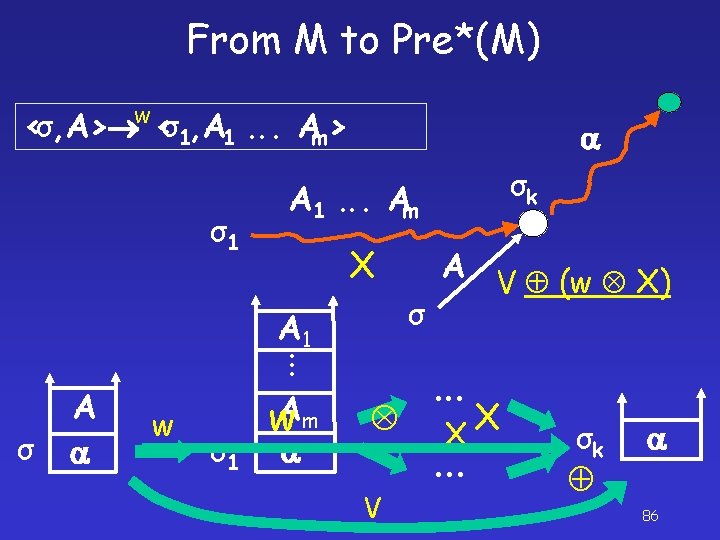
From M to Pre*(M) <σ, A> <σ1, A 1. . . Am> A 1. . . Am σ1 A σ . . . A 1 σ A σ1 Am 63
![PreKAlice KAlice my Students faculty KOwnerH KCS KBob KAlice Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-56.jpg)
Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } <KBob , my. Students > <KAlice , e> <KCS, faculty > <KBob , e> 64
![PreKAlice KAlice my Students faculty KOwnerH KCS KBob KAlice Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-57.jpg)
Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } <KBob , > <KBob , my. Students ■> <KOwner[H] , > <KCS, faculty > 65
![PreKAlice KAlice my Students faculty KOwnerH KCS KBob KAlice Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice }](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-58.jpg)
Pre*({<KAlice, >, <KAlice, >}) my. Students faculty KOwner[H] KCS KBob { , KAlice } <KOwner[H] , > Pre*({<KAlice, □>, <KAlice, ■>}) 66

Our Story • Chapter 3 (Bonus) – Applying model-checking techniques lets you answer other questions about SPKI/SDSI certificate sets [JR 02, JR 04] • What are the properties of this security policy? • What would happen if the policy were changed? 68

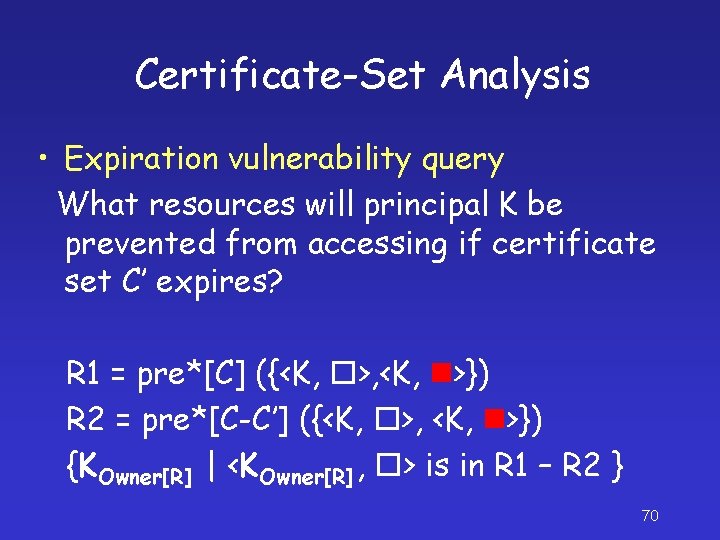
Certificate-Set Analysis • Expiration vulnerability query What resources will principal K be prevented from accessing if certificate set C’ expires? R 1 = pre*[C] ({<K, >, <K, >}) R 2 = pre*[C-C’] ({<K, >, <K, >}) {KOwner[R] | <KOwner[R] , > is in R 1 – R 2 } 70
![CertificateSetAnalysis Many more see JR 04 Main message Algorithms for model Certificate-Set-Analysis • Many more — see [JR 04] • Main message: Algorithms for model](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-61.jpg)
Certificate-Set-Analysis • Many more — see [JR 04] • Main message: Algorithms for model checking pushdown systems can be exploited to solve several certificate-set-analysis problems 71

Our Story • Chapter 3 (Bonus) – Applying model-checking techniques lets you answer other questions about SPKI/SDSI certificate sets [JR 02, JR 04] • Chapter 4 (Bummer) – Actually, SPKI/SDSI PDS • What about issues such as recency, trust, and expiration? – From PDSs to weighted PDSs [SJRS 03] 72
![Weighted Pushdown System WPDS BET 03 SJRS 03 States σ 1 σ 2 Weighted Pushdown System (WPDS) [BET 03], [SJRS 03] States: { σ 1, σ 2](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-63.jpg)
Weighted Pushdown System (WPDS) [BET 03], [SJRS 03] States: { σ 1, σ 2 , σ 3 , σ 4 } Stack symbols: { A, B, C, D } Transition rules: w 1 <σ1, A> <σ2, e> w 2 <σ1, A> <σ2, B> w 3 <σ1, A> <σ2, B C> 73

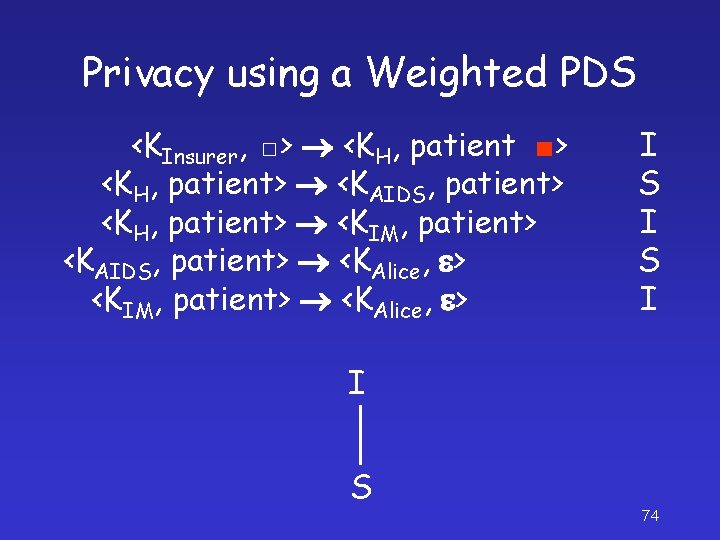
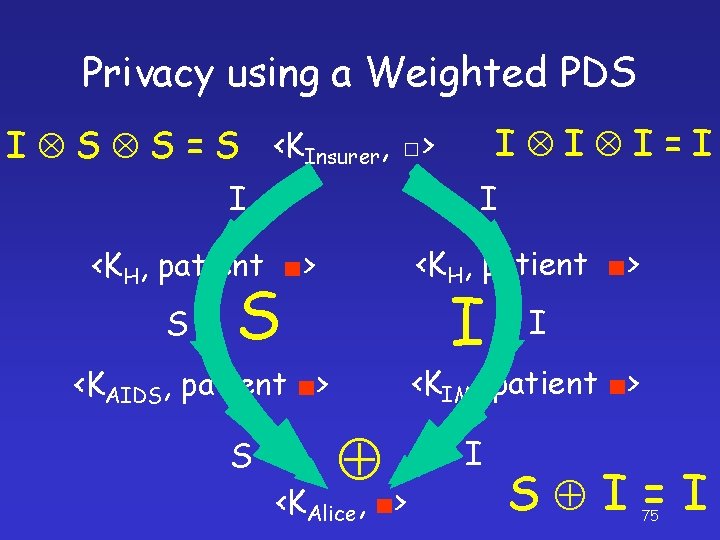
Privacy using a Weighted PDS <KInsurer, □> <KH, patient ■> <KH, patient> <KAIDS, patient> <KH, patient> <KIM, patient> <KAIDS, patient> <KAlice, e> <KIM, patient> <KAlice, e> I S I I S 74

Privacy using a Weighted PDS I I I=I I S S = S <KInsurer, □> I I <KH, patient ■> S S I <KIM, patient ■> <KAIDS, patient ■> S I <KAlice, ■> I S I=I 75

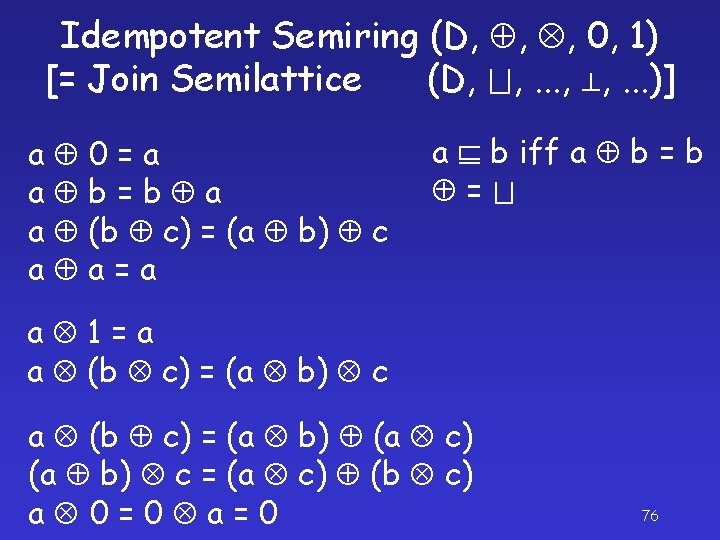
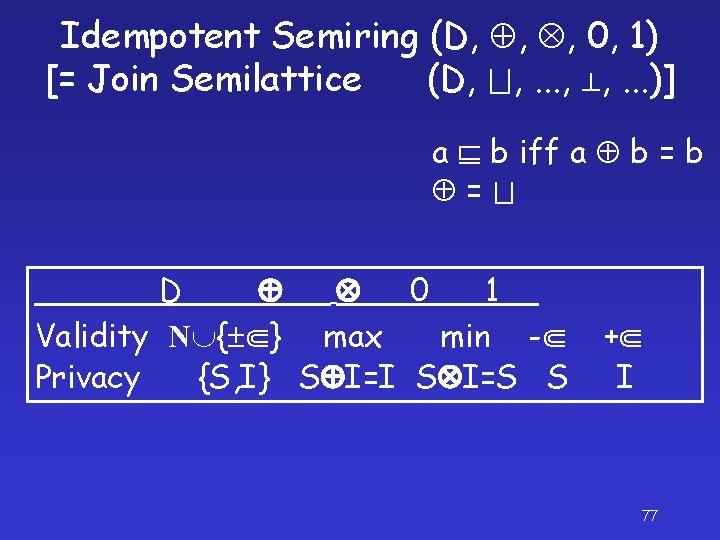
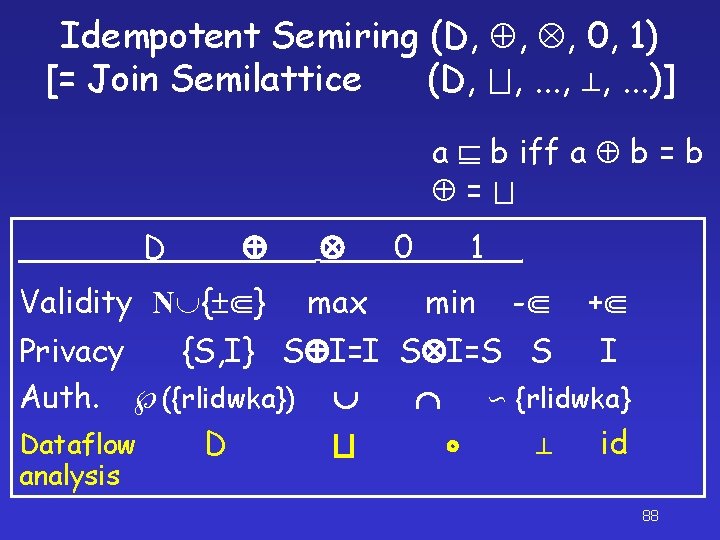
Idempotent Semiring (D, , , 0, 1) [= Join Semilattice (D, , . . . )] a 0=a a b=b a a (b c) = (a b) c a a=a a b iff a b = a 1=a a (b c) = (a b) c a (b c) = (a b) (a c) (a b) c = (a c) (b c) a 0=0 a=0 76

Idempotent Semiring (D, , , 0, 1) [= Join Semilattice (D, , . . . )] a b iff a b = D 0 1 Validity N { } max min - Privacy {S, I} S I=I S I=S S + I 77
![Validity using a Weighted PDS Rule KOwnerD KAlice Validity 10 20 Request Does KAlice Validity using a Weighted PDS Rule KOwner[D] KAlice Validity 10 20 Request Does KAlice](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-68.jpg)
Validity using a Weighted PDS Rule KOwner[D] KAlice Validity 10 20 Request Does KAlice have the right to access D? If so, what is the cert chain with the largest validity value? 78
![Validity using a Weighted PDS KOwnerD 10 20 max KAlice max10 Validity using a Weighted PDS <KOwner[D], > 10 20 = max <KAlice, ■> max(10,](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-69.jpg)
Validity using a Weighted PDS <KOwner[D], > 10 20 = max <KAlice, ■> max(10, 20) = 20 79
![Auth Cert Reduction is Incomplete LM 03 Rule KOwnerD KAlice Authorization read write Request “Auth Cert Reduction is Incomplete” [LM 03] Rule KOwner[D] KAlice Authorization {read} {write} Request](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-70.jpg)
“Auth Cert Reduction is Incomplete” [LM 03] Rule KOwner[D] KAlice Authorization {read} {write} Request Does KAlice have {read, write} access to D? No RFC 2693: “Remove all certificates whose authorization is not {read, write}” 80
![Authorization using a Weighted PDS KOwnerD read Cert chain write KAlice Authorization using a Weighted PDS <KOwner[D], > {read} Cert chain? ! {write} = <KAlice,](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-71.jpg)
Authorization using a Weighted PDS <KOwner[D], > {read} Cert chain? ! {write} = <KAlice, ■> {read} {write} = {read, write} 81
![Authorization using a Weighted PDS KOwnerD read Cert tree write KAlice Authorization using a Weighted PDS <KOwner[D], > {read} Cert tree! {write} = <KAlice, ■>](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-72.jpg)
Authorization using a Weighted PDS <KOwner[D], > {read} Cert tree! {write} = <KAlice, ■> {read} {write} = {read, write} 82

From M to Pre*(M) w <σ, A> <σ1, A 1. . . Am> σ1 A 1. . . Am X. . . σ w σ1 w. Am A σ A 1 A σk V V (w X) . . . X X . . . σk 86

Our Story • Chapter 3 (Bonus) – Applying model-checking techniques lets you answer other questions about SPKI/SDSI certificate sets [JR 02, JR 04] • Chapter 4 (Bummer) – Actually, SPKI/SDSI PDS • What about issues such as recency, trust, and expiration? – From PDSs to weighted PDSs [SJRS 03] • Chapter 5 (Ah!) – WPDSs provide a new framework for static program analysis that is strictly richer than 35 years worth of previous approaches [RSJ 03, RSJM 05] 87

Idempotent Semiring (D, , , 0, 1) [= Join Semilattice (D, , . . . )] a b iff a b = D Validity N { } max 0 1 min - + Privacy {S, I} S I=I S I=S S I Auth. ({rlidwka}) {rlidwka} Dataflow D id analysis 88

WPDSs: A More Powerful Program-Analysis Framework • Example: better debugging primitive – at a breakpoint at n, retrieve the stack (say S) – stack-constrained slicing: “What are the program elements that could have affected the values used at n, given that we reached n with stack S? ” 89
![So What Who Cares Yawn Check properties of programs using model checking So What? Who Cares? [Yawn] • Check properties of programs using model checking –](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-77.jpg)
So What? Who Cares? [Yawn] • Check properties of programs using model checking – SLAM [Ball & Rajamani 00] – MOPS [Chen & Wagner 02] – “Metacompliation” [Engler et al. ] In essence, all are using PDSs • PDS WPDS – More powerful formalism for modeling program behaviors: How does the program transform the data? 96

Our Story Continues. . . • Traditional trust-management models provide centralized solutions – require certificates to be sent to a central site for certificate-chain discovery • not acceptable in practice – solution: distributed WPDS solver [JSWR 06, Kidd unpublished] • useful in program analysis, too • Polyhedral analysis? – “widening weights” [Gopan thesis] • Concurrent PDS model checker [CCKRT 06] – Analysis engine for model checking concurrent programs – Undecidable in general; uses semi-decision procedure [BET 03] • Context-bounded model checking – Analyze a concurrent program for a bounded number of context switches [QR 05], [LTKR 08] 102

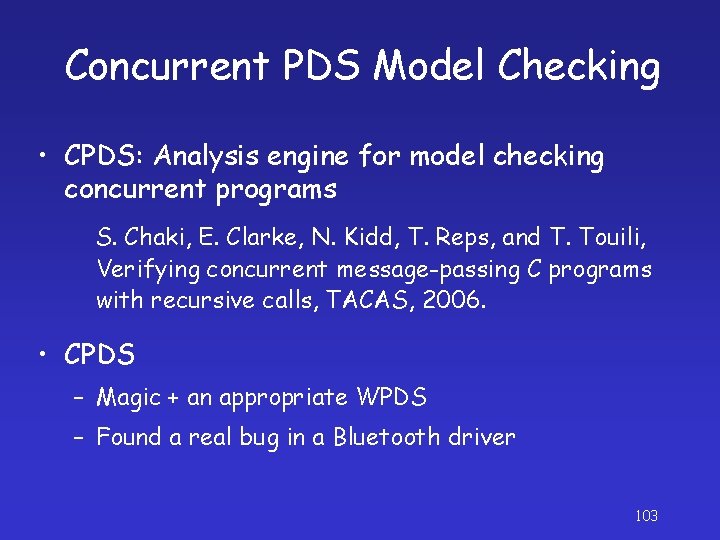
Concurrent PDS Model Checking • CPDS: Analysis engine for model checking concurrent programs S. Chaki, E. Clarke, N. Kidd, T. Reps, and T. Touili, Verifying concurrent message-passing C programs with recursive calls, TACAS, 2006. • CPDS – Magic + an appropriate WPDS – Found a real bug in a Bluetooth driver 103

CPDS Analysis of Bluetooth Driver (I) • Model of Bluetooth driver from Windows NT – Reentrant multi-threaded library • Has known bug, found by KISS [QW 04] – 2 handler processes • each receives one request ― A: RUN; B: STOP – 2 context switches: A B A • Modeled with a CPDS – Buggy run performs 8 actions – Found in 5 seconds, using 334 MB 104

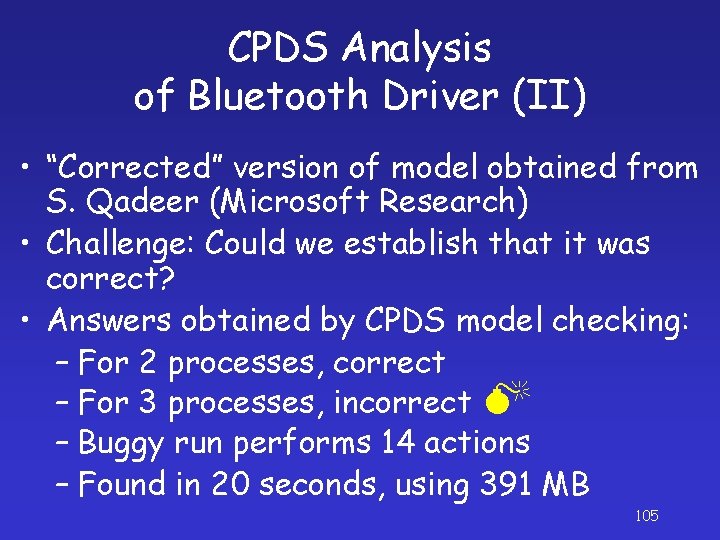
CPDS Analysis of Bluetooth Driver (II) • “Corrected” version of model obtained from S. Qadeer (Microsoft Research) • Challenge: Could we establish that it was correct? • Answers obtained by CPDS model checking: – For 2 processes, correct – For 3 processes, incorrect – Buggy run performs 14 actions – Found in 20 seconds, using 391 MB 105

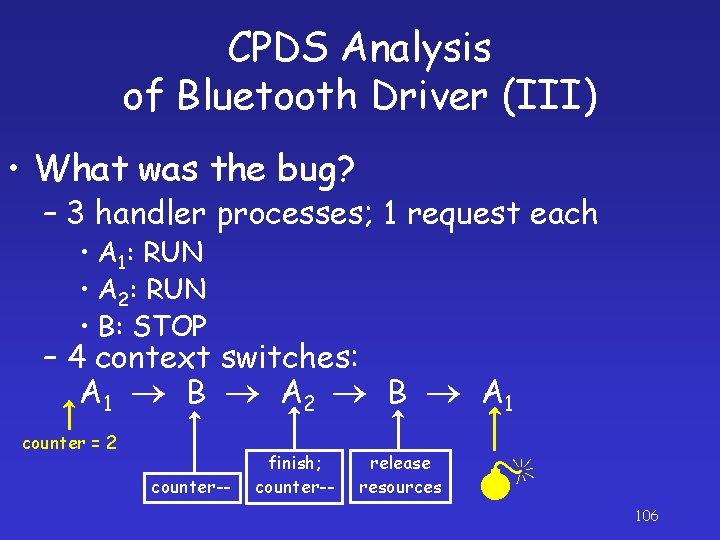
CPDS Analysis of Bluetooth Driver (III) • What was the bug? – 3 handler processes; 1 request each • A 1: RUN • A 2: RUN • B: STOP – 4 context switches: A 1 B A 2 B A 1 counter = 2 counter-- finish; counter-- release resources 106

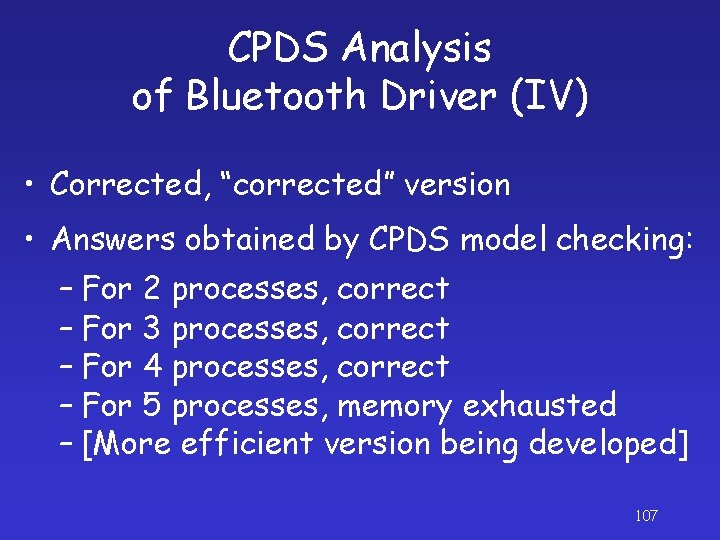
CPDS Analysis of Bluetooth Driver (IV) • Corrected, “corrected” version • Answers obtained by CPDS model checking: – For 2 processes, correct – For 3 processes, correct – For 4 processes, correct – For 5 processes, memory exhausted – [More efficient version being developed] 107

Conclusion • Built a bridge between authorization problems for distributed systems and static program analysis – Message: use model-checking techniques for the reachability problems that arise in authorization • Similar to what happened 25 years ago for HW verification – Showed how to fix a flaw in SPKI/SDSI • cert chain cert tree • Beneficial side effect: improved program-analysis methods – we use WPDSs extensively in our tools to analyze stripped x 86 executables [LRB 05, B 07] • Cross-fertilization from working on both problems together • Try them youself: Google for “WPDS++” or “WALi” 109

Questions? 110

111

Related Work • SPKI/SDSI – Clarke, Elien, Ellison, Fredette, Morcos, & Rivest [J. Comp. Sec. 01] • Pushdown systems – – Bouajjani, Esparza, & Maler [Concur 97] Finkel, Willems, & Wolper [ENTCS 97] Esparza, Hansel, Rossmanith, & Schwoon [CAV 00] Bouajjani, Esparza, & Touili [POPL 03] • Weighted-hypergraph problems – – Knuth [IPL 77] Grammar flow analysis: Möncke & Wilhelm [WAGA 91] Ramalingam thesis [LNCS #1089] Ramalingam & Reps [J. Alg 96] • Interprocedural dataflow analysis – [Cousot & Cousot 78], [Sharir & Pnueli 81], Knoop & Steffen 92] 112 – IDE framework: Sagiv, Reps, & Horwitz [TCS 96]
![Other Contributions Differential propagation SCP 05 Weight domain difference operator Other Contributions • Differential propagation [SCP 05] – Weight domain + difference operator •](https://slidetodoc.com/presentation_image/3e3ecbb1ce164b36cde1c6f5ff35a20b/image-88.jpg)
Other Contributions • Differential propagation [SCP 05] – Weight domain + difference operator • Simultaneous forward & backward analysis – Error projection [SAS 07] • Extended WPDS [CAV 05] – Extension for handling local variables • • Non-saturation-based pre*/post* algs. [CAV 06] Distributed algorithms for WPDS problems Implemented systems (WPDS++, WALi) Non-trivial applications in a tool for analyzing stripped executables 114