procurement fraud and the EFT fraud threat government
















- Slides: 22

procurement fraud and the EFT fraud threat government supply chain and procurement summit 2008 advocate steven powell 13 – 14 October 2008, Gallagher Estate Midrand

objectives? § to highlight the procurement fraud risk § eft abuse explained § eft fraud modus operandi § cases explained § vulnerable areas § precautions that should be taken

electronic funds transfer fraud two methods • creation of alternative vendor profile which is then selected to perform illicit transactions • substitution of employee account and deletion – in the 1 st scenario the risk of being caught is higher as the employee info remains on the vendor profile and should be detected through proper checks

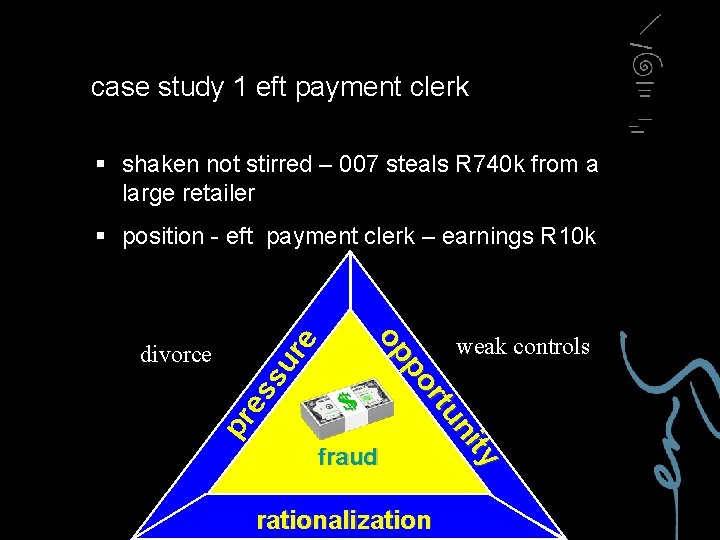
case study 1 eft payment clerk § shaken not stirred – 007 steals R 740 k from a large retailer su es pr weak controls ty ni rtu po op divorce re § position - eft payment clerk – earnings R 10 k fraud rationalization

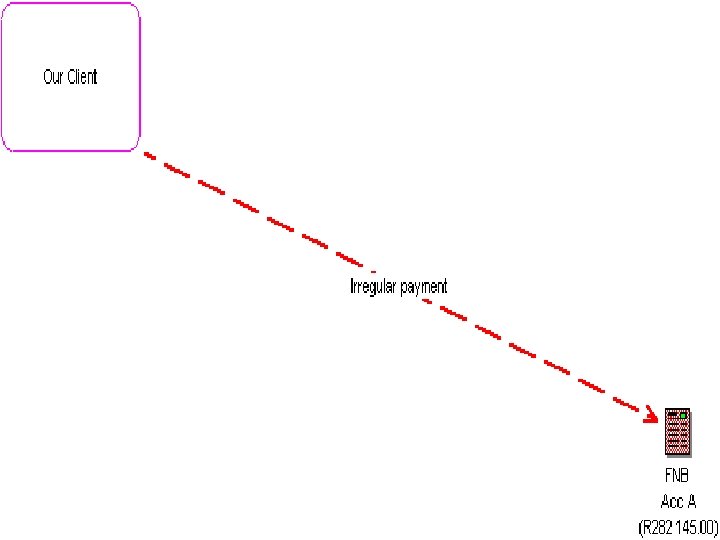
the black hole • lost payment – software programmers showed our suspect how to manually override the system to ensure that payments reach the intended destination • every time our suspect made a legitimate payment he knew he could steal by changing a text file on his c drive “I could not resist the temptation, the controls were so weak they deserved it • testing thresholds

key controls – vet vendors properly (address, history, bank account, expertise & infrastructure) – enforce tight control over changes to suppliers bank accounts – add management authorisation – audit changes to supplier banking info over the past year – interrogate the changes – verify with suppliers and banking institution

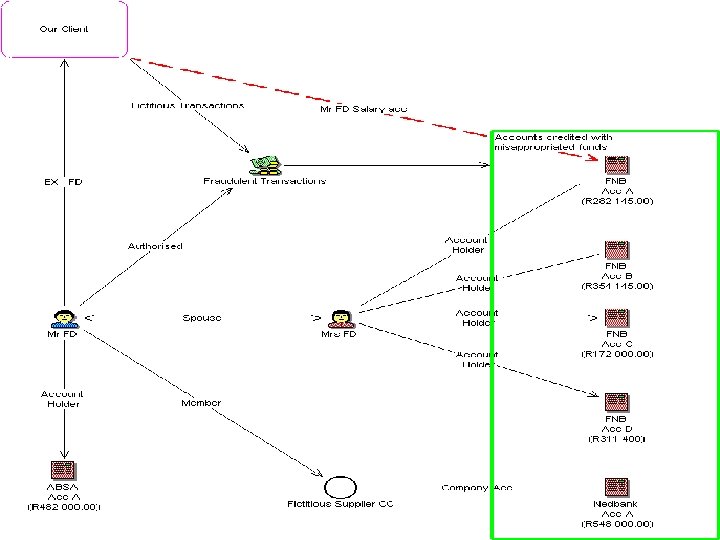
case study 2 – chief accountant • R 2 million in one year • modus operandi – amendment of vendor banking account detail on vendor master file • substituted account not own account (DRC) • once illicit transaction concluded – amended vendor profile deleted and vendor banking info restored to original • when routine audits are performed – all appears as it should • where did the money go? – the local casino received R 1, 95 million out of the R 2 million stolen

case study 3 - FD at packaging company • R 4. 2 mil misappropriated • R 1, 7 in one morning substitution and deletion • vehicles, houses, timeshare (house search), gambling, overseas travel, holidays, private schooling, heart operation, • property for family, vehicles for close friends • safety deposit boxes? • 3 million rand recovery via full co-operation which translated into mitigation for an effective 5 year jail term




what should the company have picked up? • eft clerk – the payments to a particular supplier whose profile was exploited was far over budget – routine audits testing payroll against the vendor master files would have identified the illicit profile • chief accountant – password control was abused – cfo signed off batches of eft’s – if he just counted the transactions he would have noticed that there were more payments in the batch than the paperwork reflected – supplier payments were duplicate- a proper recon of each supplier against approved budget would have identified the overspend

procurement fraud - the importance of screening employees and suppliers too many of our clients employ individuals with criminal records – you can ask about and check prior criminal history when you appoint to positions of trust declaration of interests coupled to regular screening is vital to identify § moonlighting § related party transactions (hidden) § ghost suppliers

examples of corrupt schemes ghost suppliers § this is a letterhead and a bank account § the corrupt employee signs off or requisitions payments for a company which does not exist § payments are made to this entity and usually find the way to the employee or his spouses accounts § no services or supplies are rendered

ghost supplies/fictitious invoices § genuine supplier § fictitious invoices are submitted by a collusive supplier § corrupt employee approves invoice and submits through normal channels § when supplier receives payment, a kickback is channelled to the employee/corruptee (usually cash) § almost impossible to ID the false invoices § undelivered goods are allocated to negligent departments

the symptoms of fraudulent behavior the red flags or warning signals in respect of the corrupt employee are always present make sure that you detect the obvious

procurement red flags § excessive lifestyle § gambling alcohol or drug problems § staff who constantly claim underpaid § close relationships with suppliers § sole suppliers - not shopping around § poor credit rating § poor communication and reports § indulging in affairs § not taking leave § refusal of promotion § excessive & unexplained overtime § criminal record

divisional red flags § too much trust placed in key employees limited segregation of duty § no independent checks on reconciliation and payments § no clear lines of authority or responsibility § proper authorization procedures not enforced § inadequate documentation & records § infrequent independent reviews § inadequate disclosure of interests & investments (not just directors) § management override of the controls § operating on a crisis basis § inadequate attention to detail

the tools to combat fraud § the fraud hotline § data mining § FRM - fraud risk management strategies § code of ethics/conduct § fraud awareness training § fraud risk measurement (focused approach) § fraud prevention and response plans § gift policies § proper enforcement of existing policies § zero tolerance policy

conclusion § staff who control eft payments literally have an open door to your bank account § make sure that access to changing vendor master file info is tightly controlled § regularly review changes to vendor banking details § regularly run checks testing for links between employees and vendors – supplier data vs staff data § know who you are paying and why § CALL ENS © 2008 S Powell

Questions

thank you tel +2721 410 2553 cell 082 820 1036 spowell@ens. co. za w w w. ens. c o. z a