Processing Integrity and Availability Controls Chapter 10 Copyright

Processing Integrity and Availability Controls Chapter 10 Copyright © 2015 Pearson Education, Inc. 10 -1

Learning Objectives • Identify and explain controls designed to ensure processing integrity. • Identify and explain controls designed to ensure systems availability. Copyright © 2015 Pearson Education, Inc. 10 -2
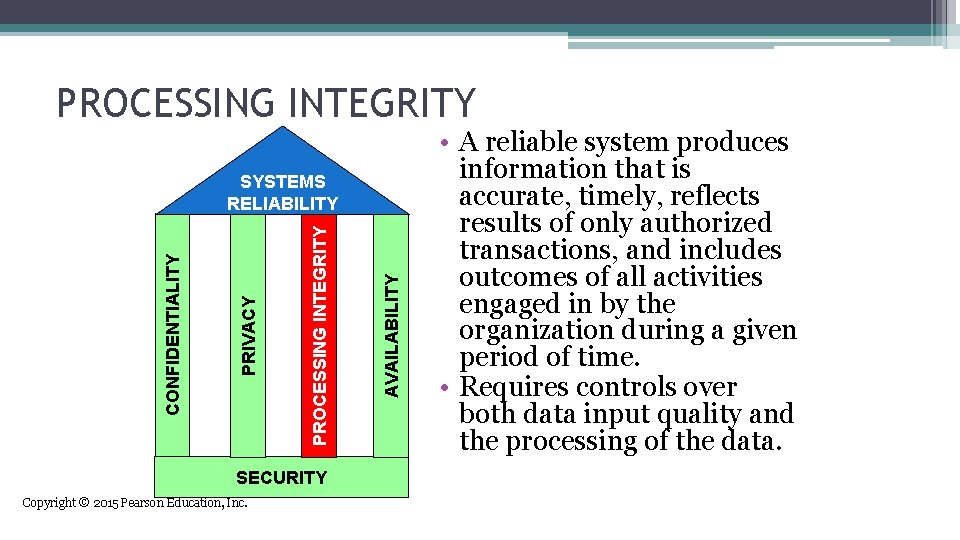
PROCESSING INTEGRITY SECURITY Copyright © 2015 Pearson Education, Inc. AVAILABILITY PROCESSING INTEGRITY PRIVACY CONFIDENTIALITY SYSTEMS RELIABILITY • A reliable system produces information that is accurate, timely, reflects results of only authorized transactions, and includes outcomes of all activities engaged in by the organization during a given period of time. • Requires controls over both data input quality and the processing of the data.

Processing Integrity Controls • Input ▫ Forms design �Sequentially prenumbered/sequence test ▫ Turnaround documents ▫ Cancellation & storage of documents ▫ Visual Scanning Copyright © 2015 Pearson Education, Inc. 10 -4
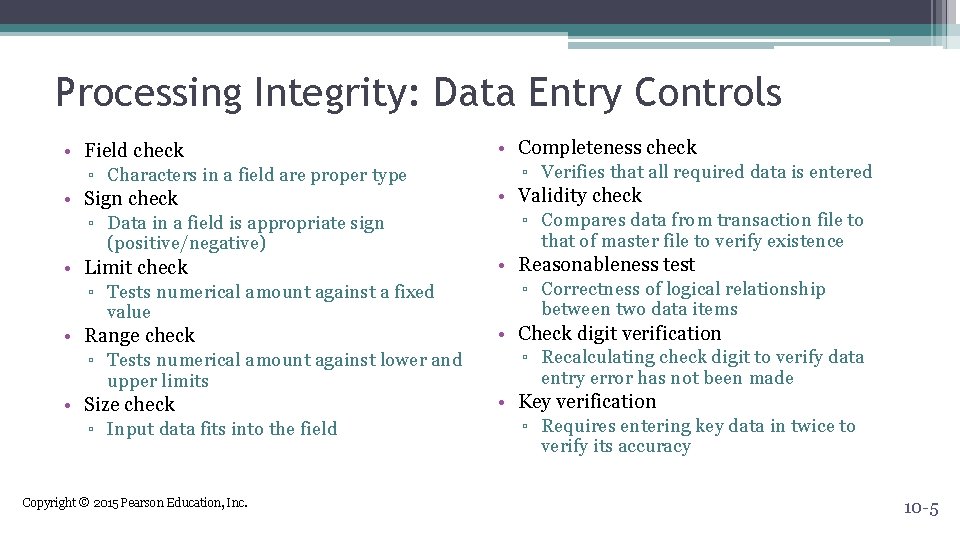
Processing Integrity: Data Entry Controls • Field check ▫ Characters in a field are proper type • Sign check ▫ Data in a field is appropriate sign • Completeness check ▫ Verifies that all required data is entered • Validity check ▫ Compares data from transaction file to • Limit check ▫ Tests numerical amount against a fixed • Reasonableness test ▫ Correctness of logical relationship • Range check ▫ Tests numerical amount against lower and • Check digit verification ▫ Recalculating check digit to verify data • Size check ▫ Input data fits into the field • Key verification ▫ Requires entering key data in twice to (positive/negative) value upper limits Copyright © 2015 Pearson Education, Inc. that of master file to verify existence between two data items entry error has not been made verify its accuracy 10 -5

Input Controls • The preceding tests are used for batch processing and online real-time processing. • Both processing approaches also have some additional controls that are unique to each approach. Copyright © 2015 Pearson Education, Inc.
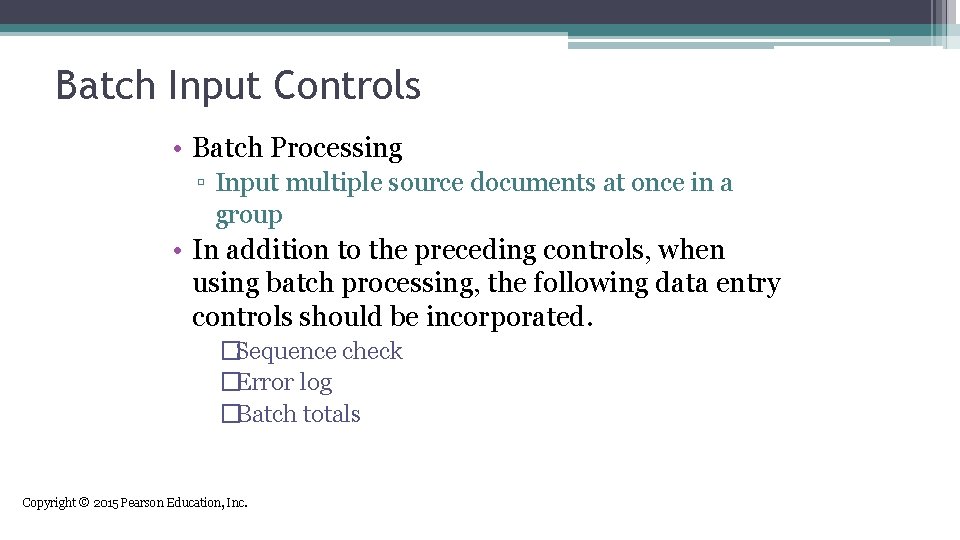
Batch Input Controls • Batch Processing ▫ Input multiple source documents at once in a group • In addition to the preceding controls, when using batch processing, the following data entry controls should be incorporated. �Sequence check �Error log �Batch totals Copyright © 2015 Pearson Education, Inc.

Batch Input Controls • Batch Totals ▫ Compare input totals to output totals �Financial �Sums a field that contains monetary values �Hash �Sums a nonfinancial numeric field �Record count �The number of records in a batch Copyright © 2015 Pearson Education, Inc.
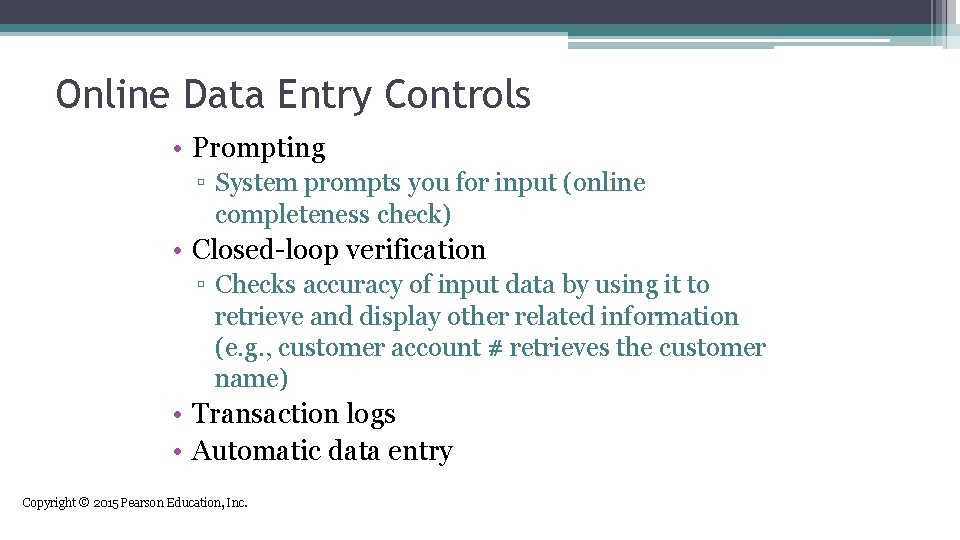
Online Data Entry Controls • Prompting ▫ System prompts you for input (online completeness check) • Closed-loop verification ▫ Checks accuracy of input data by using it to retrieve and display other related information (e. g. , customer account # retrieves the customer name) • Transaction logs • Automatic data entry Copyright © 2015 Pearson Education, Inc.
Processing Controls • Data matching ▫ Two or more items must be matched before an action takes place • File labels ▫ Ensures correct and most updated file is used • Recalculation of batch totals • Cross-footing ▫ Verifies accuracy by comparing two alternative ways of calculating the same total • Zero-balance tests ▫ For control accounts (e. g. , payroll clearing) • Write-protection mechanisms ▫ Protect against overwriting or erasing data • Concurrent update controls ▫ Prevent error of two or more users updating the same record at the same time Copyright © 2015 Pearson Education, Inc. 10 -10
Output Controls • User review of output • Reconciliation ▫ Procedures to reconcile to control reports (e. g. , general ledger A/R account reconciled to Accounts Receivable Subsidiary Ledger) ▫ External data reconciliation • Data transmission controls 1. Checksums – hash of file transmitted, comparison made of hash before and after transmission 2. Parity checking Copyright © 2015 Pearson Education, Inc. 10 -11
AVAILABILITY SECURITY Copyright © 2015 Pearson Education, Inc. AVAILABILITY PROCESSING INTEGRITY PRIVACY CONFIDENTIALITY SYSTEMS RELIABILITY • Reliable systems are available for use whenever needed. • Threats to system availability originate from many sources, including: ▫ ▫ ▫ Hardware and software failures Natural and man-made disasters Human error Worms and viruses Denial-of-service attacks and other sabotage
Availability Controls • Preventive maintenance • Fault tolerance ▫ Use of redundant components • Data center location and design ▫ Raised floor ▫ Fire suppression ▫ Air conditioning ▫ Uninterruptible power supply (UPS) ▫ Surge protection • Training • Patch management and antivirus software Copyright © 2015 Pearson Education, Inc. • Backup procedures ▫ Incremental �Copies only items that have changed since last partial backup ▫ Differential backup �Copies all changes made since last full backup • Disaster recovery plan (DRP) ▫ Procedures to restore organization’s IT function • Business continuity plan (BCP) ▫ How to resume all operations, not just IT 10 -13

AVAILABILITY • Disaster Recovery and Business Continuity Planning Objectives: ▫ Minimize the extent of the disruption, damage, and loss ▫ Temporarily establish an alternative means of processing information ▫ Resume normal operations as soon as possible ▫ Train and familiarize personnel with emergency operations • Recovery point objective (RPO) • Recovery time objective (RTO) Copyright © 2015 Pearson Education, Inc.

AVAILABILITY • Organizational options for replacing computer and networking equipment. ▫ Reciprocal agreements ▫ Cold sites ▫ Hot sites ▫ Real-time mirroring Copyright © 2015 Pearson Education, Inc.

AVAILABILITY • Documentation ▫ An important and often overlooked component. Should include: �The disaster recovery plan itself, including instructions for notifying appropriate staff and the steps to resume operation, needs to be well documented. �Assignment of responsibility for the various activities. �Vendor documentation of hardware and software. �Documentation of modifications made to the default configuration (so replacement will have the same functionality). �Detailed operating instructions. ▫ Copies of all documentation should be stored both onsite and off-site. Copyright © 2015 Pearson Education, Inc.

AVAILABILITY • Testing ▫ Periodic testing and revision is probably the most important component of effective disaster recovery and business continuity plans. �Most plans fail their initial test, because it’s impossible to anticipate everything that could go wrong. �The time to discover these problems is before the actual emergency and in a setting where the weaknesses can be carefully analyzed and appropriate changes made. Copyright © 2015 Pearson Education, Inc.
- Slides: 17