PrivacyPreserving Linear Programming UCSD Center for Computational Mathematics












- Slides: 26

Privacy-Preserving Linear Programming UCSD – Center for Computational Mathematics Seminar January 11, 2011 Olvi Mangasarian UW Madison & UCSD La Jolla

Problem Statement • Entities with related data wish to solve a linear program based on all the data • The entities are unwilling to reveal their data to each other – If each entity holds a different set of variables for all constraints, then the data is said to be vertically partitioned – If each entity holds a different set of constraints with all variables, then the data is said to be horizontally partitioned • Our approach: privacy-preserving linear programming (PPLP) using random matrix transformations – Provides exact solution to the total linear program – Does not reveal any private information

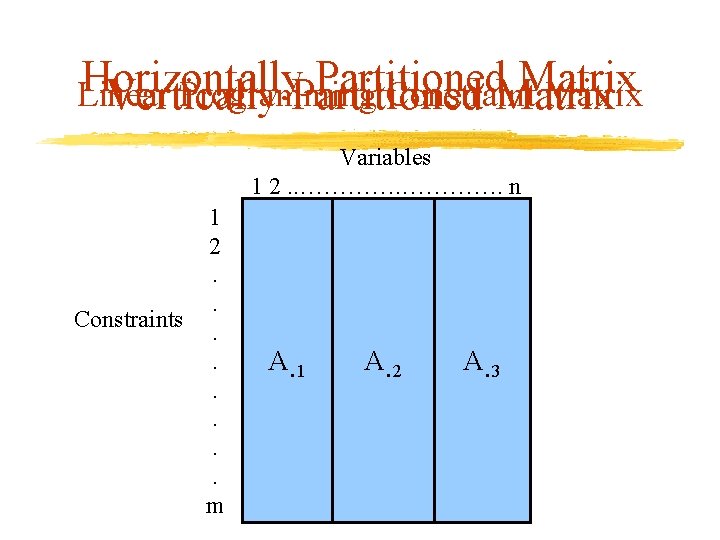
Horizontally Partitioned Matrix Linear Programming Constraint Matrix Vertically Partitioned Matrix Variables 1 2. . …………. n 1 2. . Constraints. . . m A 1 A¢ 2 AA A 3 A¢ 3

Outline • Vertically (horizontally) partitioned linear program • Secure transformation via a random matrix • Privacy-preserving linear program solution • Computational results • Summary

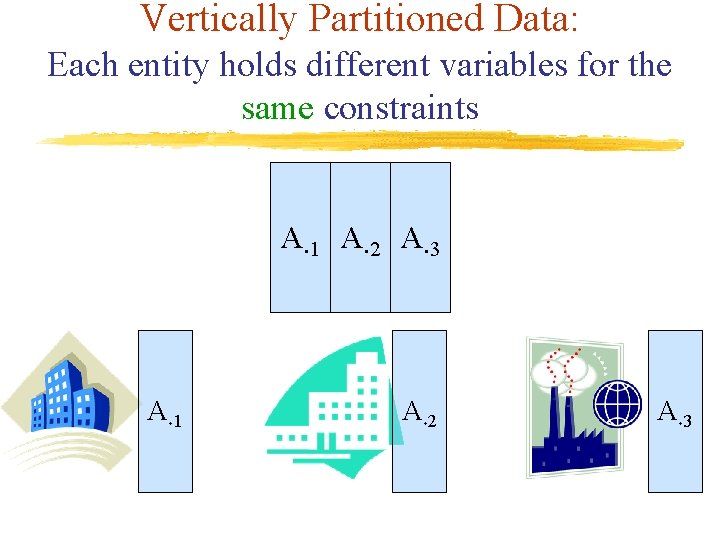
Vertically Partitioned Data: Each entity holds different variables for the same constraints A¢ 1 A¢ 2 A¢ 3

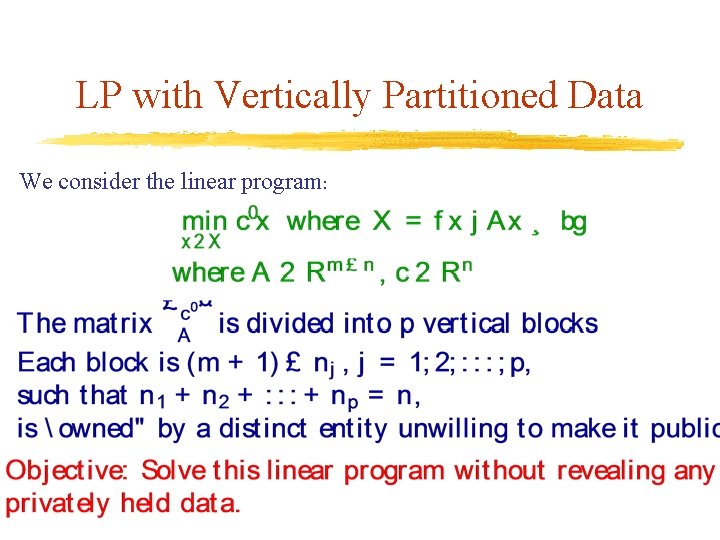
LP with Vertically Partitioned Data We consider the linear program:

Secure Linear Program Generation

Why Secure Linear Program?

Original & Secure LPs Are Equivalent

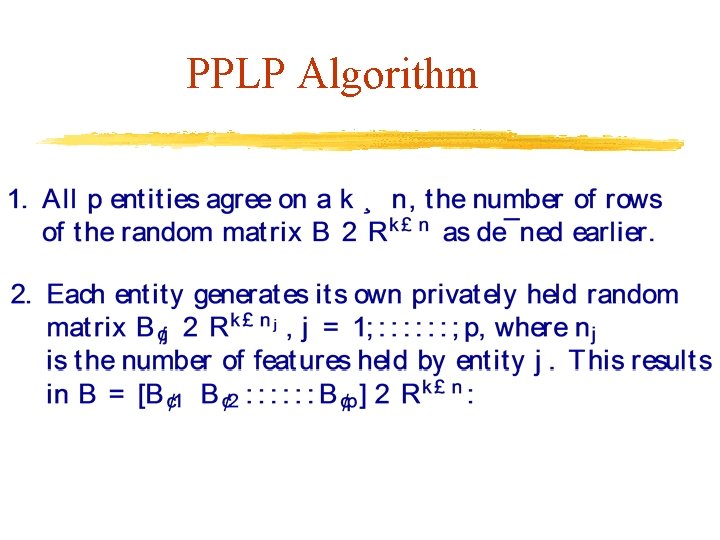
PPLP Algorithm

PPLP Algorithm (Continued)

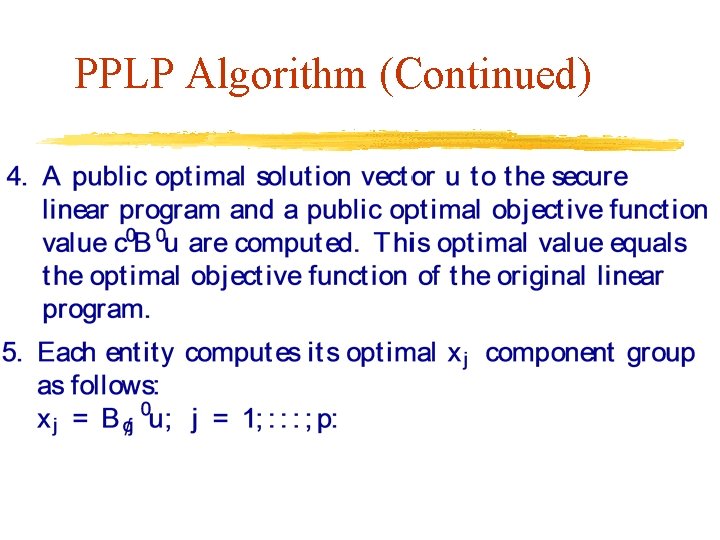
PPLP Algorithm (Continued)

PPLP Algorithm (Continued)

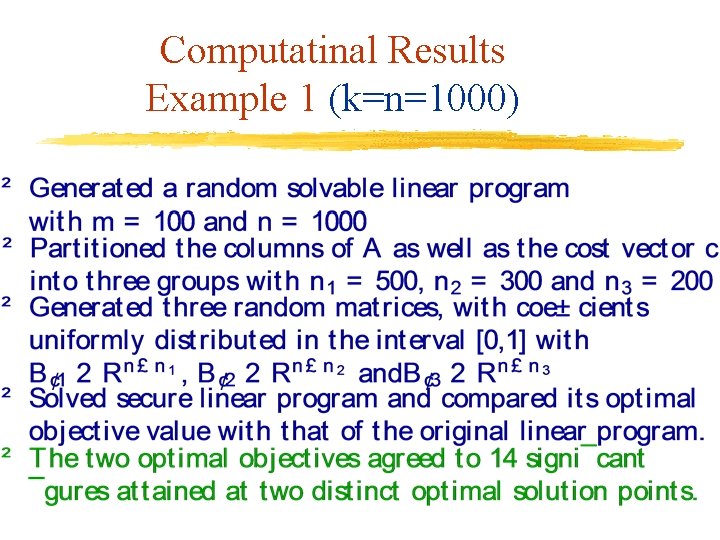
Computatinal Results Example 1 (k=n=1000)

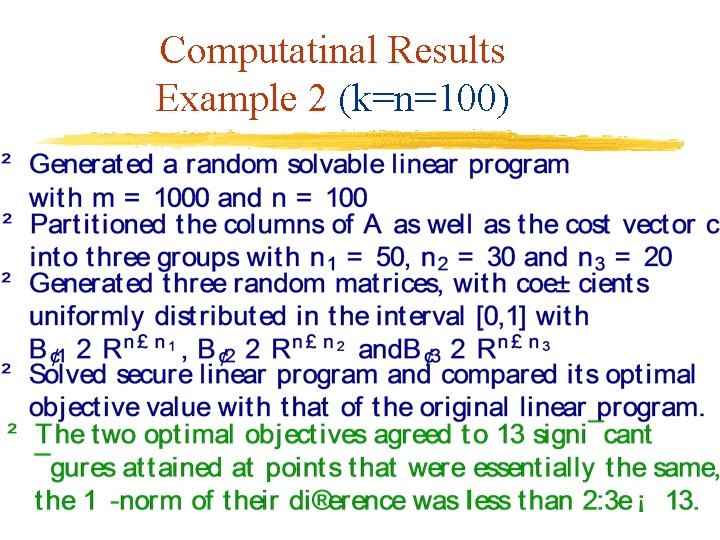
Computatinal Results Example 2 (k=n=100)

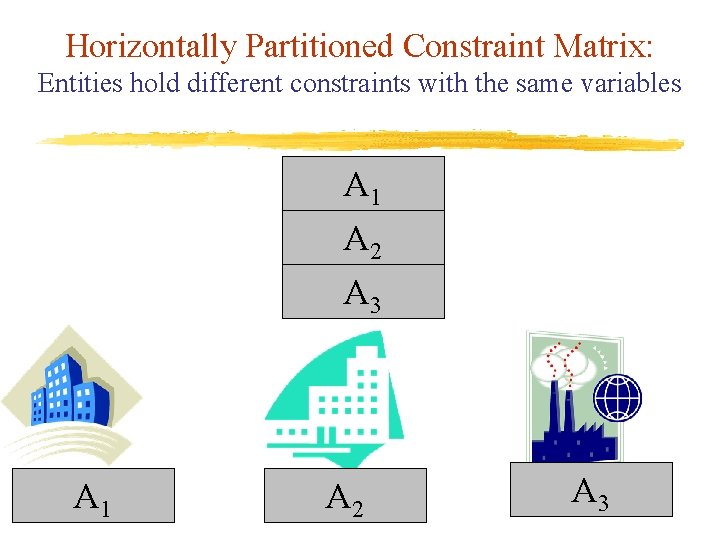
Horizontally Partitioned Constraint Matrix: Entities hold different constraints with the same variables A 1 A 2 A 3

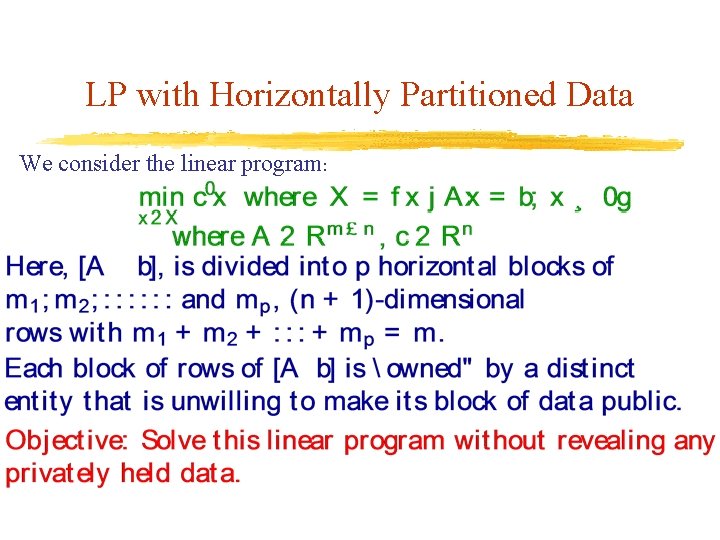
LP with Horizontally Partitioned Data We consider the linear program:

Secure Linear Program Generation

Why Secure Linear Program?

Original & Secure LPs Are Equivalent

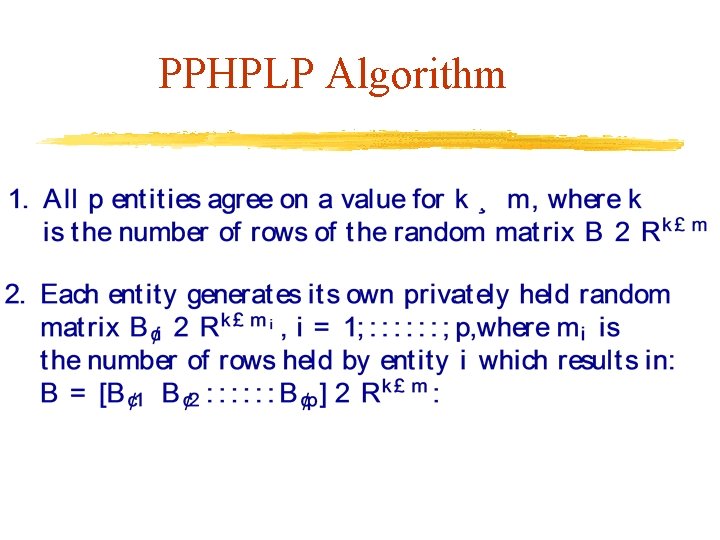
PPHPLP Algorithm

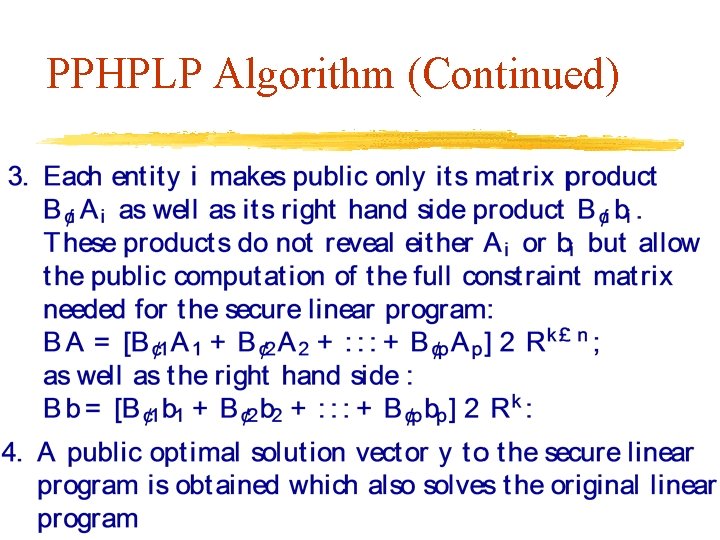
PPHPLP Algorithm (Continued)

Computatinal Results Example 1 (k=1000)

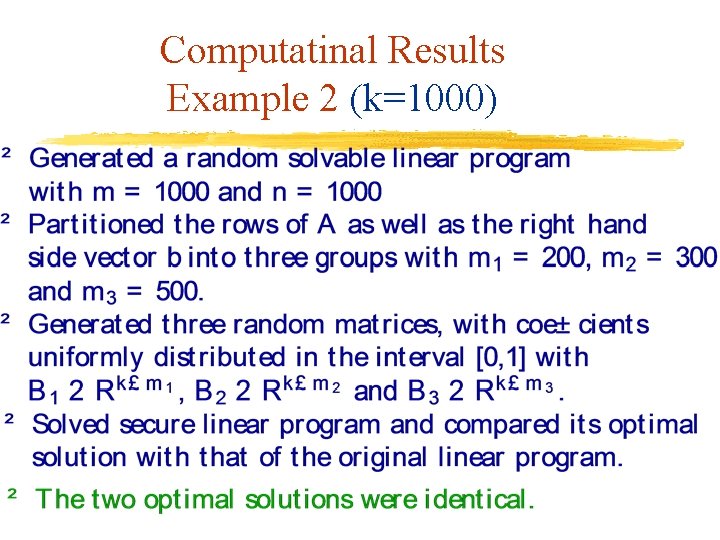
Computatinal Results Example 2 (k=1000)

Summary & Outlook Privacy preserving linear programming for vertically or horizontally partitioned data – Based on a transformation using a random matrix B – Get exact solution to the original linear program without revealing privately held data Possible extensions to: horizontally partitioned inequality constraints, complementarity problems and nonlinear programs

References ftp: //ftp. cs. wisc. edu/pub/dmi/tech-reports/10 -01. pdf ftp: //ftp. cs. wisc. edu/pub/dmi/tech-reports/10 -02. pdf Optimization Letters, to appear