PrivacyPreserving Approximation Center for Computational Mathematics Seminar UCSD




- Slides: 21

Privacy-Preserving Approximation Center for Computational Mathematics Seminar UCSD January 24, 2012 Olvi Mangasarian UW Madison & UCSD La Jolla Glenn Fung Siemens Medical Solutions, Malvern, PA

Problem Statement • Entities with related data points wish to obtain a function approximation based on all the data points • The entities are unwilling to reveal their data to each other • Each entity holds a different set of data points for all variables. Thus, the data is said to be horizontally partitioned • Our approach: privacy-preserving approximation (PPA) using random matrix transformations • PPA provides exact solution based on the total data • PPA does not reveal any private information

Outline • Horizontally partitioned approximation problem • Secure transformation via a random matrix • Method of solution: Privacy-preserving linear programming • Computational results • Summary

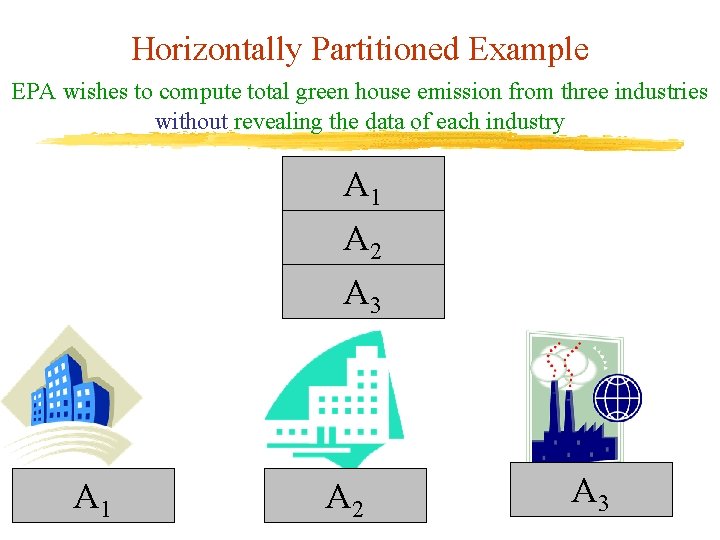
Horizontally Partitioned Example EPA wishes to compute total green house emission from three industries without revealing the data of each industry A 1 A 2 A 3

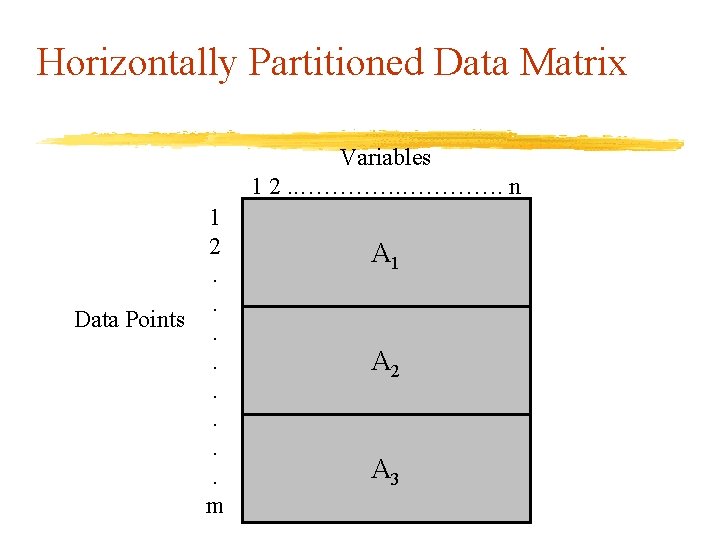
Horizontally Partitioned Data Matrix Variables 1 2. . …………. n 1 2. . Data Points. . . m A 1 A 2 A A 3

Secure Linear Approximation

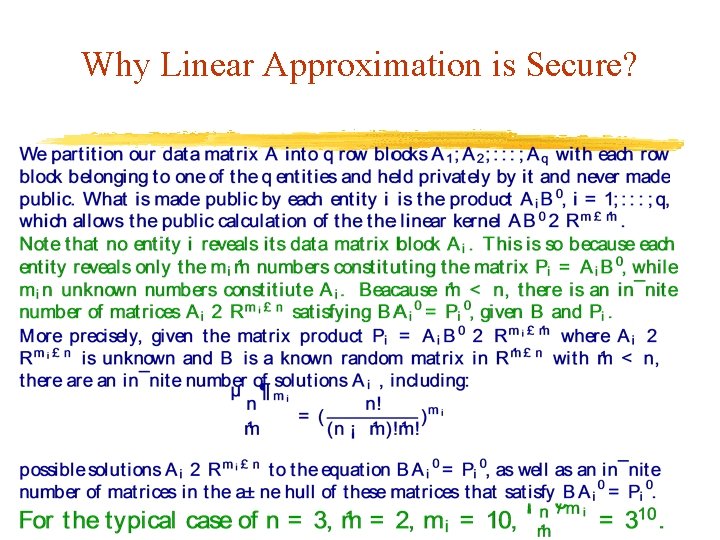
Why Linear Approximation is Secure?

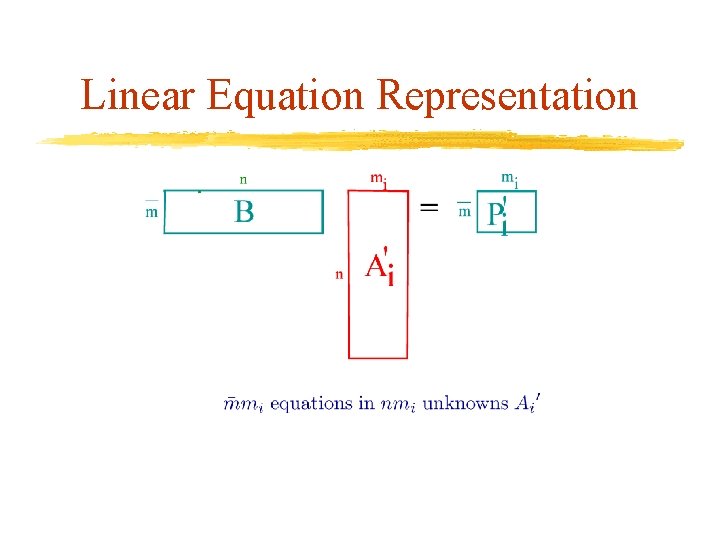
Linear Equation Representation

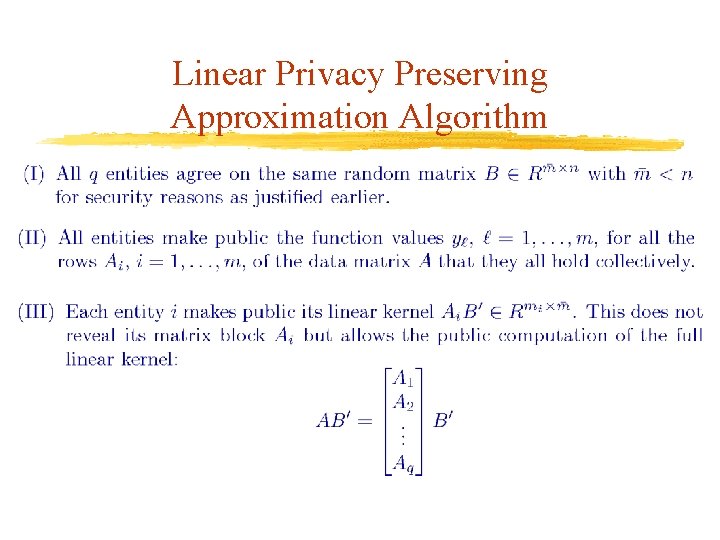
Linear Privacy Preserving Approximation Algorithm

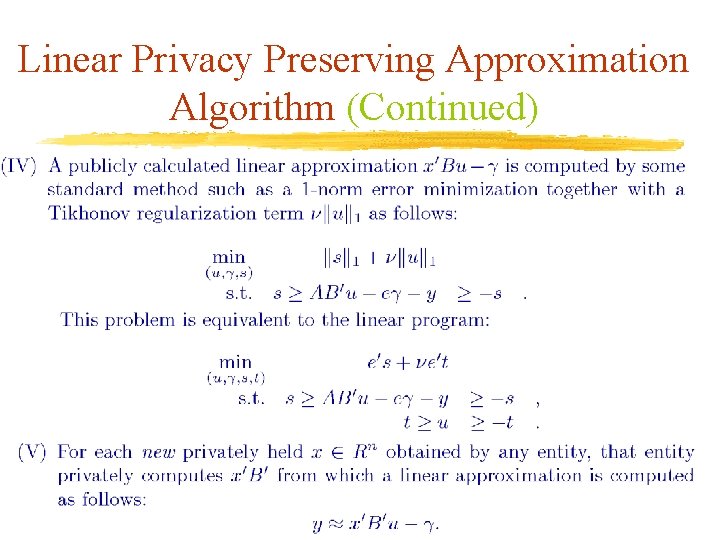
Linear Privacy Preserving Approximation Algorithm (Continued)

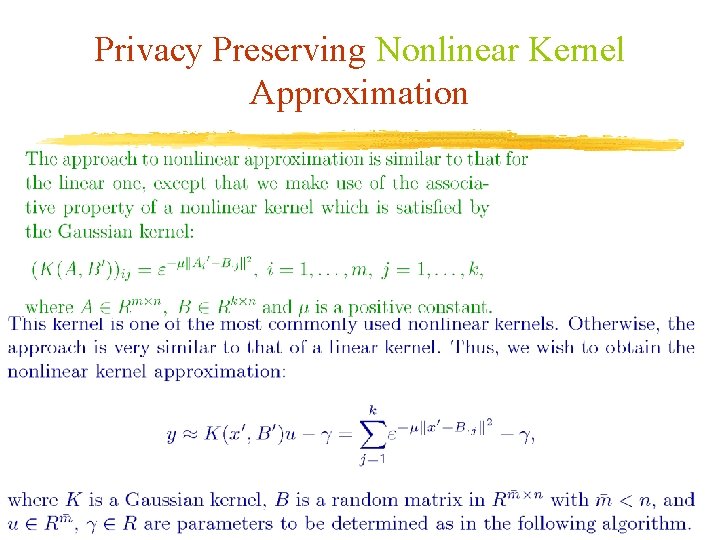
Privacy Preserving Nonlinear Kernel Approximation

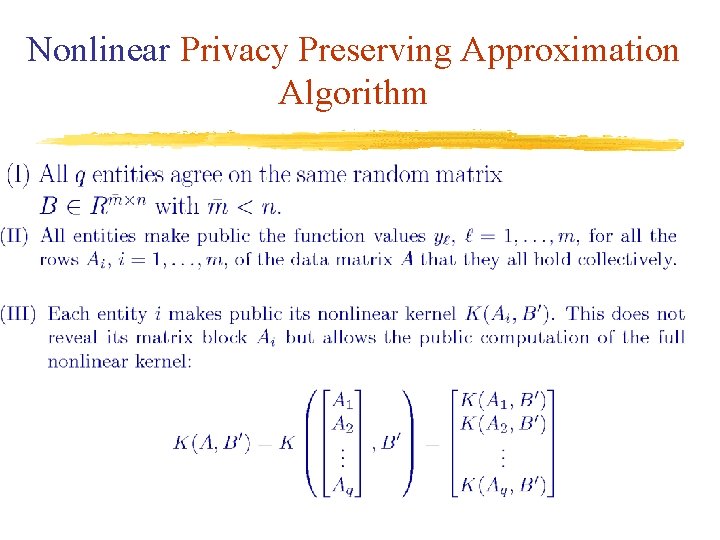
Nonlinear Privacy Preserving Approximation Algorithm

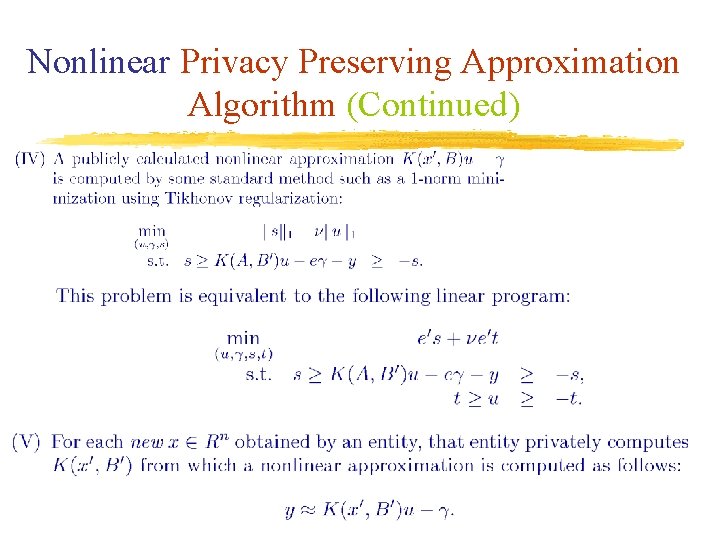
Nonlinear Privacy Preserving Approximation Algorithm (Continued)

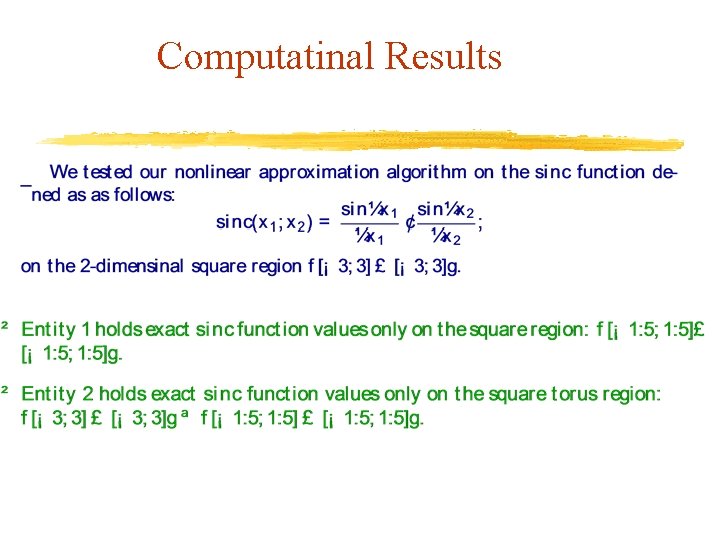
Computatinal Results

Entities’ Regions

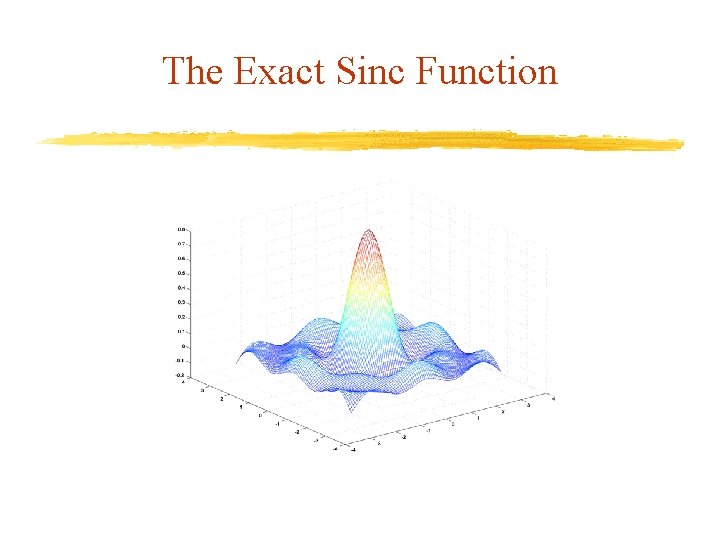
The Exact Sinc Function

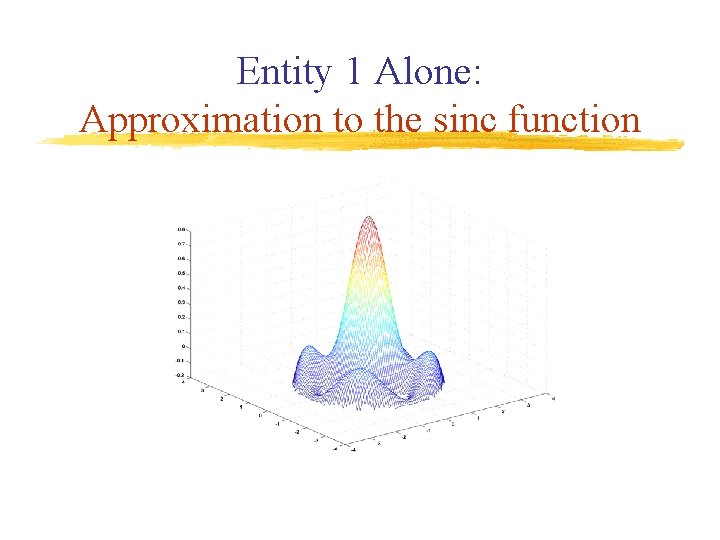
Entity 1 Alone: Approximation to the sinc function

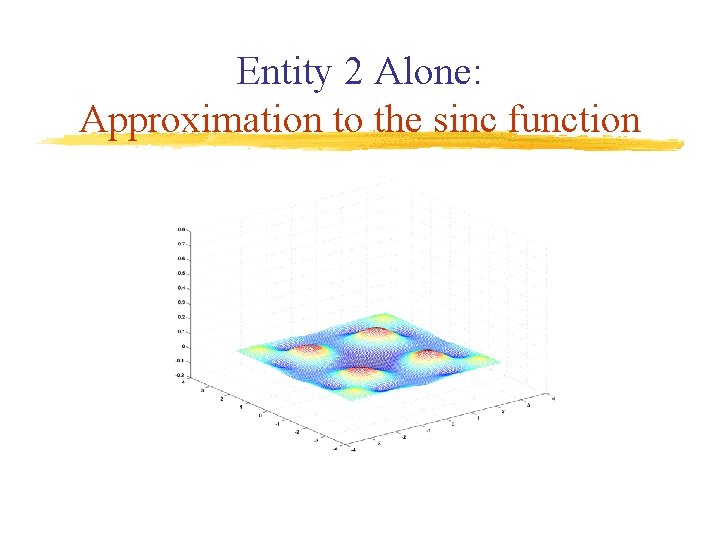
Entity 2 Alone: Approximation to the sinc function

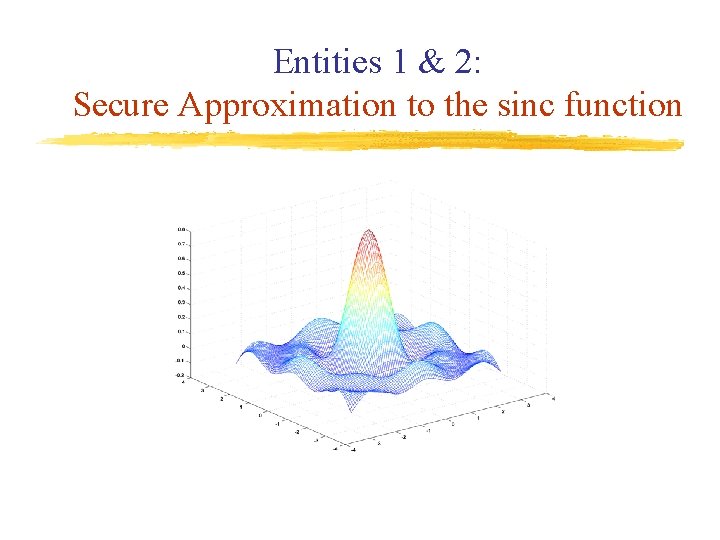
Entities 1 & 2: Secure Approximation to the sinc function

Summary & Outlook Privacy preserving approximation of functions using privately held data: – Based on a transformation using a random matrix B – Get essentially exact approximation to the original function without revealing privately held data Possible extensions to problems with privately held constraints

References ftp: //ftp. cs. wisc. edu/pub/dmi/tech-reports/11 -04. pdf ftp: //ftp. cs. wisc. edu/pub/dmi/tech-reports/07 -03. pdf