PRIVACY Supplement to CSH 5 Chapter 69 Security


















































- Slides: 56

PRIVACY Supplement to CSH 5 Chapter 69 “Security Audits, Standards and Inspections” Notes by M. E. Kabay, Ph. D, CISSP-ISSMP Assoc Prof Information Assurance School of Business & Management Norwich University 1 Copyright © 2011 M. E. Kabay. All rights reserved.

NOTE Ø This lecture is a supplement to the material in CSH 5 chapter 69, “Privacy in Cyberspace. ” Ø Theses slides do not follow the structure of the chapter; they also include additional material. -- M. E. Kabay, Ph. D, CISSP-ISSMP 2 Copyright © 2011 M. E. Kabay. All rights reserved.

Topics Ø Introduction: A Future Pizza Order Ø Privacy in US Jurisprudence Ø Effects of Information Technology on Privacy Ø Fourth Amendment Issues Ø Key US Laws Protecting Privacy Ø Defending Privacy in Cyberspace Ø Reading about Privacy 3 Copyright © 2011 M. E. Kabay. All rights reserved.

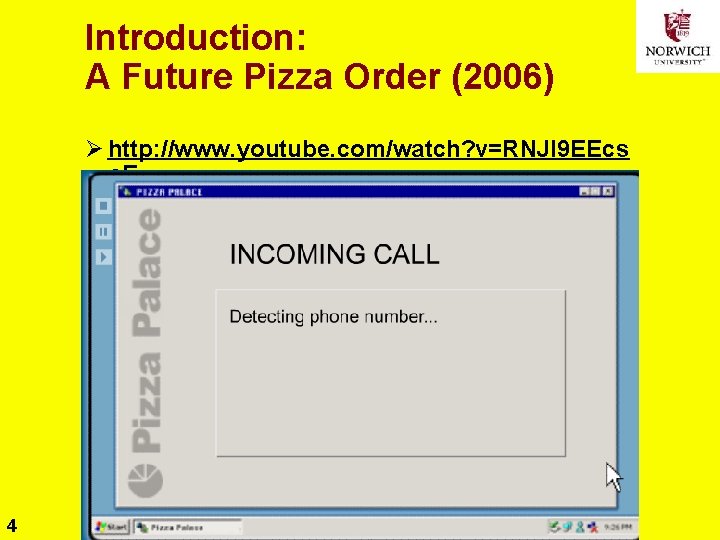
Introduction: A Future Pizza Order (2006) Ø http: //www. youtube. com/watch? v=RNJl 9 EEcs o. E 4 Copyright © 2011 M. E. Kabay. All rights reserved.

Privacy in US Jurisprudence Ø Privacy: q. Power to control truths about you that other people know q. Power to hide parts of the truth üFrom Cyberspace Law for Non-Lawyers http: //www. ssrn. com/update/lsn/cyberspace/csl_lessons. html 5 Copyright © 2011 M. E. Kabay. All rights reserved.

Common Law Privacy Ø The makers of our Constitution. . . Sought to protect Americans in their beliefs, their thoughts, their emotions and their sensations. They conferred as against the Government, the right to be let alone – the most comprehensive of the rights of man and the right most valued by civilized men. ” Justice Louis D. Brandeis Dissenting in the Olmstead decision 6 Copyright © 2011 M. E. Kabay. All rights reserved.

Common Law Privacy Invasion of privacy under common law: Ø Intrusion upon seclusion Ø Appropriation of name or likeness Ø Publicity given to private life Ø Publicity placing person in false light Ø US Constitution does not specifically mention privacy q. But 4 th amendment usually applied when discussing government intrusion 7 Copyright © 2011 M. E. Kabay. All rights reserved.

Types of Privacy Ø Informational privacy: Truths you have revealed to others but still want to control q. Public records q. Medical records q. But public behavior is not protected Ø Truths you have kept private q. Books you read q. What you say in private letters or e-mail q. Used to protected by laws of trespass 8 Copyright © 2011 M. E. Kabay. All rights reserved.

Effects of Information Technology on Privacy Ø Radical change in ease of acquiring data about individuals q. Electronic purchase records q. Telephone and e-mail records q. Surveillance technology redefines public space q. Identification technology reduces the anonymity of the crowd q. Public records online Ø Radical change in ease of acquiring aggregate data about groups 9 Copyright © 2011 M. E. Kabay. All rights reserved.

Informational Privacy Ø US law traditionally did not limit uses of observations about consumers q. What you buy / read / view / eat q. Data shared among credit agencies q. Names, addresses, preferences sold to advertisers q. Even medical data were not much protected Ø European Privacy Directive much more stringent q. Caused problems for US firms – barred from doing business because of lax laws 10 Copyright © 2011 M. E. Kabay. All rights reserved.

Informational Privacy and the Internet Ø Google bought Deja. News q. Archive of all USENET discussions q. Spans ~15 years q. Can provide interesting information about previous levels of professionalism Ø Google caches Web pages q. Owner can remove an embarrassing page from Web site q. But cached copy persists for months 11 Copyright © 2011 M. E. Kabay. All rights reserved.

Controlling Electronic Information is Difficult Ø E-mail messages often circulated without permission q. Theoretical violation of copyright q. In practice, impossible to stop once it starts Ø Private message group discussions are often made public q. Can be embarrassing q. Has led to lawsuits 12 Copyright © 2011 M. E. Kabay. All rights reserved.

Data Collection on the Web Ø Cookies store information about where you have been on a specific Web site q. E. g. , AMAZON uses cookies to track your identity and your book preferences q. Unless badly formed, cookies are not supposed to be shared among Web sites Ø Web bugs q 1 -pixel images (invisible) that return information to specific advertisers q. Allow tracking of how many people visit a Web page vs how many click on ads 13 Copyright © 2011 M. E. Kabay. All rights reserved.

Data Collection – cont’d Spyware Ø Software that covertly communicates with a Web address (phones home) Ø Caught by firewalls Ø Present in Comet Cursor – cartoon cursors favored by children Ø Sends information about exactly what Web pages kids are looking at Ø Covert market research Ø Some spyware does not remove itself via its uninstall function 14 Copyright © 2011 M. E. Kabay. All rights reserved.

Spyware ØWhat is spyware? ØHow does spyware enter a system? ØExamples of spyware ØRemoving spyware ØBlocking spyware 15 Copyright © 2011 M. E. Kabay. All rights reserved.

What Is Spyware? Ø Spyware: any technology that covertly gathers information q. About person q. About organization q. About system q. Without knowledge of victim Ø Any software which q. Employs user's Internet connection q. In background ("backchannel") q. Without their knowledge or explicit permission 16 Copyright © 2011 M. E. Kabay. All rights reserved.

How does Spyware Enter a System? Ø Install freeware, shareware q. Often those that are ad-supported Ø Some browser plugins q. Offer new functions, q. New file format compatibility Ø Viruses & worms q. E-mail attachments 17 Copyright © 2011 M. E. Kabay. All rights reserved.

Early Examples of Spyware Ø Aureate / Radiate Ø Conducent / Timesink Ø Comet Cursor Ø Creative Labs Ø Go. Hip Ø Web 3000 18 Copyright © 2011 M. E. Kabay. All rights reserved.

Aureate / Radiate Ø Toolkit for information gathering q. Used by programmers of other programs q. Installed in > 30, 000 computers Ø Functions of toolkit q. Send advertising to computers where Radiate code was installed q. Exchange information between client and host computers q. Collect nonspecific data about usage q. Ask for answers to survey of preferences relating to products & services 19 Copyright © 2011 M. E. Kabay. All rights reserved.

Aureate / Radiate Problems Ø Did not tell developers to include warning to users (end-user license agreement, EULA) Ø Allowed programmers to defer or eliminate demographics survey Ø Can download arbitrary code from any server q. Uses browser process & permissions q. Therefore passes firewalls qupdate-dll. exe already found in 3 different versions in the wild Ø Demonstrated to cause browser & Windows crashes q. Common knowledge in tech support: remove advert. dll to stop (main component of A/R) 20 Copyright © 2011 M. E. Kabay. All rights reserved.

Conducent / Timesink Ø Software Developers Kit q. Soft. Click Optimization Engine q. Timesink = TSadbot. exe Ø Delivers advertising to client computer q. Retrieves user / campaign activity information q. Maintains comprehensive system for campaign management & reporting Ø Users include q. CD-ROM distributors qe. Games (large game publisher) 21 Copyright © 2011 M. E. Kabay. All rights reserved.

Comet Cursor Ø Changes cursor to animated cartoon when visiting Comet Cursor enabled Web sites q. Installed by > 90, 000 users Ø Installations (except of Real. Player) install GUID (Globally Unique Identifier) Ø Automatically updates code Ø Counts how many times user changes cursor q. Provides aggregated anonymous information to clients q. Records URL where cursor changed q. URL of next page viewed 22 Copyright © 2011 M. E. Kabay. All rights reserved.

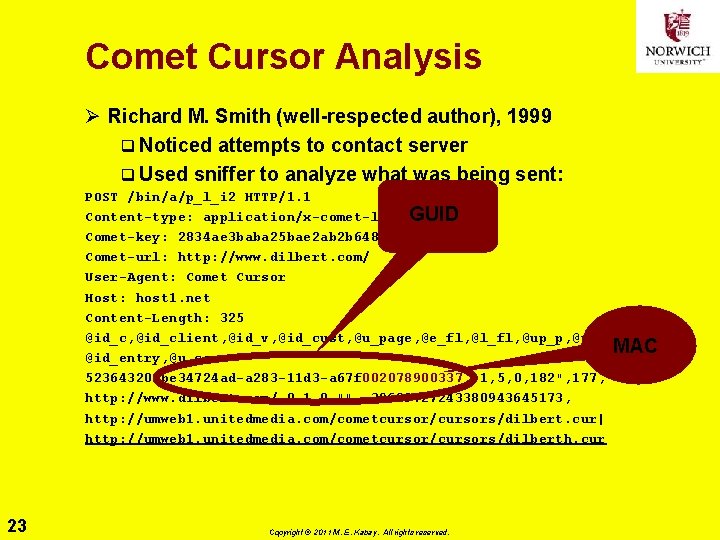
Comet Cursor Analysis Ø Richard M. Smith (well-respected author), 1999 q Noticed attempts to contact server q Used sniffer to analyze what was being sent: POST /bin/a/p_l_i 2 HTTP/1. 1 Content-type: application/x-comet-log GUID Comet-key: 2834 ae 3 baba 25 bae 2 ab 2 b 648492 e 221 f Comet-url: http: //www. dilbert. com/ User-Agent: Comet Cursor Host: host 1. net Content-Length: 325 @id_c, @id_client, @id_v, @id_cust, @u_page, @e_fl, @l_fl, @up_p, @up_v, MAC @id_entry, @u_cc 52364320, be 34724 ad-a 283 -11 d 3 -a 67 f 002078900337, "1, 5, 0, 182", 177, http: //www. dilbert. com/, 0, 1, 0, "", -39609727243380943645173, http: //umweb 1. unitedmedia. com/cometcursor/cursors/dilbert. cur| http: //umweb 1. unitedmedia. com/cometcursor/cursors/dilberth. cur 23 Copyright © 2011 M. E. Kabay. All rights reserved.

Creative Labs Ø Makers of popular sound cards, music players Ø Include newsupd. exe file in installations q. Automatically checks for driver updates q. But also sends information about user program usage to Creative Labs server Ø Problems q. Not documented q. No way of turning off in early versions Ø Outcry has resulted in improvements 24 Copyright © 2011 M. E. Kabay. All rights reserved.

Go. Hip Ø Describes itself as “metasearch engine” Ø Accused of covert installations q. Installs “Windows Startup” program into Start Menu q. Reconfigures browser to visit Go. Hip site every time browser is launched q. Redefines search default to Go. Hip q. Changes autosignature files to attach advertisement to every e-mail message recommending visit to Go. Hip Ø Privacy policy now details all of this information 25 Copyright © 2011 M. E. Kabay. All rights reserved.

Web 3000 Ø Web 3000 Ad Network Ø Toolkit for software developers Ø Automatically supplies q. Browser headlines q. Splash screens q. Status-bar messages q. Opt-in e-mail newsletters q. Installation offers Ø Automatically tries to connect to its server even when user is not using browser 26 Copyright © 2011 M. E. Kabay. All rights reserved.

Removing Spyware Ø Problems with uninstalling spyware q. Some products do not (or did not) include uninstall function q. Uninstall function failed in several cases q. Some products reinstall themselves Ø Tools available for removal; e. g. , q. Ad. Aware http: //www. lavasoftusa. com/ q. Aureate/Radiate DLL remover http: //www. spychecker. com/radiateremover. html q. Pest. Patrol http: //www. pestpatrol. com/ 27 Copyright © 2011 M. E. Kabay. All rights reserved.

Blocking Spyware Ø Can prevent messages from reaching “mother ship” Ø Silencer http: //www. spychecker. com/silencer. html q. Points all connections to adware sites to null address (127. 0. 0. 1) in Windows hosts file Ø Personal firewalls; e. g. , q. Black. Ice http: //www. blackice. com q. Norton Personal Firewall 2002 http: //www. symantec. com/sabu/nis/npf/ q. Zone. Alarm http: //www. zonelabs. com 28 Copyright © 2011 M. E. Kabay. All rights reserved.

Preventing Spyware Infestations Ø Read the fine print before installing software q. Especially adware = freeware supported by advertising Ø Run appropriate scanners (removal tools) periodically Ø Firewalls help identify infestations as well as blocking transmissions q. Choose firewall capable of trapping unexpected outbound connections q. Set parameters to alert user to unauthorized connections 29 Copyright © 2011 M. E. Kabay. All rights reserved.

Arguments Defending Data Collection Ø Doesn’t hurt anyone Ø No names collected Ø Helps to improve effectiveness of advertising Ø Improves market mechanisms by providing statistical information about consumer preferences 30 Copyright © 2011 M. E. Kabay. All rights reserved.

Attacks on Data Collection Ø Issue is control Ø Covert data collection is unacceptable Ø Data subject must be informed q. Who is collecting what info q. For what purpose q. How to stop collection q. Who has used information 31 Copyright © 2011 M. E. Kabay. All rights reserved.

Fourth Amendment Issues Ø Fourth Amendment to the US Constitution passed in 1791 q. Forbids unreasonable search and seizure by government and law enforcement agents Ø Did not apply to new technological means of information gathering q 1928 SCOTUS decision excluded telephone wiretaps from 4 th Amendment protection q. Brandeis dissented, arguing that interpretation must be updated to include new technologies 32 Copyright © 2011 M. E. Kabay. All rights reserved.

New Interpretations of 4 th Amendment Ø 1968 Katz vs US q. Constitution protects “people, not places” q. Invasion of property not the issue q. Key is whether person has “reasonable expectation of privacy” 33 Copyright © 2011 M. E. Kabay. All rights reserved.

Later Judgements Would you expect privacy in Ø Bank records (no: US vs Miller) Ø Car travel tracked by Lo. Jack (no: US vs Knotts) Ø Material stored in open field (no: Oliver vs US) Ø Garbage on curbside (no: CA vs Greenwood) Ø Material visible from plane (no: Dow Chemical v US) Ø Marijuana farming Gro-Lights seen via Infrared cameras (yes: US vs Robinson) 34 Copyright © 2011 M. E. Kabay. All rights reserved.

Key US Laws Protecting Privacy Ø Fair Credit Reporting Act of 1970 Ø Privacy Act of 1974 Ø Right to Financial Privacy Act of 1978 Ø Privacy Protection Act (PPA), 1980 Ø Electronic Communications Privacy Act (ECPA), 1986 Ø Telephone Consumer Protection Act, 1991 Ø Health Insurance Portability and Accountability Act (HIPAA), 1996 Ø Gramm-Leach-Bliley Act (GLB), 1999 35 Copyright © 2011 M. E. Kabay. All rights reserved.

Fair Credit Reporting Act of 1970 Ø Credit reports limited to q. Credit application q. Insurance q. Employment q. Government benefits q. Business transactions justifying such reports Ø Credit bureaus are data sinks q. Share information via clients (banks etc. ) q. Refusals can be mislabeled, sent on q. Wrong data can circulate endlessly q. FCRA requires due care to remove / correct bad info Ø See http: //www. ftc. gov/os/statutes/fcra. htm 36 Copyright © 2011 M. E. Kabay. All rights reserved.

Privacy Act of 1974 5 USC § 552 a Ø Government agencies may not conceal data gathering about individuals and data repositories Ø Also restrictions on distribution Ø Publish notice giving details including q. Name, location q. Types of people covered q. Purposes of routine uses of the data q. Responsible persons q. Means for data subjects to check correctness of record about themselves http: //www 4. law. cornell. edu/uscode/5/552 a. html http: //www. usdoj. gov/04 foia/privstat. htm 37 Copyright © 2011 M. E. Kabay. All rights reserved.

Right to Financial Privacy Act of 1978 (amended 1987) Ø Limits government access to financial records Ø Allows reports to government agencies for q. Establishing collateral or security for loan q. Bankruptcy proceedings q. Application for government loans Ø Banks (etc. ) may notify government agencies of suspected wrongdoing Ø Customers may authorize any disclosure q. Permission extends max. 3 months q. Permission can be revoked any time http: //www. dol. gov/dol/allcfr/SOL/Title_29/Part_19/toc. htm 38 Copyright © 2011 M. E. Kabay. All rights reserved.

Privacy Protection Act (PPA) of 1980 42 USC § 2000 aa Ø Protects journalists’ and writers’ materials and sources Ø Require probable cause for search or seizure q. Except if crime is in process or has already occurred q. To prevent immediate injury to a victim Ø Steve Jackson Games case q. Secret Service raided game company q. Seized computers, refused to return them q. See http: //www. eff. org/Legal/Cases/SJG/ http: //www 4. law. cornell. edu/uscode/42/2000 aa. html 39 Copyright © 2011 M. E. Kabay. All rights reserved.

Steve Jackson Games vs Secret Service Ø March 1, 1990 q Chris Goggans “Erik Bloodaxe” arrested, computer gear confiscated q JG small Sci. Fi computer-game maker in Austin TX q LEO raided HQ, confiscated computers q Seized gaming manual called G. U. R. P. S. Cyberpunk thinking it was a terrorism manual Ø Police misinterpreted Cyberpunk game q Loyd Blankenship – SJG employee q Simulated cyberspace conflicts Ø Operation Sundevil – May 8, 1990 q Crackdown on phone fraud and credit-card fraud bulletin boards around USA 40 Copyright © 2011 M. E. Kabay. All rights reserved.

Electronic Communications Privacy Act (ECPA), 1986 Ø 17 USC § 1367 et al. Ø Governs interception and disclosure of electronic communications q. Telephone q. E-mail q. Fax q. Pager Ø Employers are not subject to ECPA restrictions on their own employees’ communications q. Except if they have allowed a reasonable expectation of privacy to develop http: //www. cpsr. org/cpsr/privacy/wiretap/ecpa 86. html 41 Copyright © 2011 M. E. Kabay. All rights reserved.

Telephone Consumer Protection Act, 1991 Ø 47 USC § 227 Ø Bars automated calling systems that charge consumers Ø Makes unsolicited commercial fax illegal q. Need pre-existing business relation or q. Agreement of recipient Ø Some attempts to extend this law to junk email q. UCE = unsolicited commercial e-mail qaka SPAM Ø http: //www. fcc. gov/ccb/consumer_news/tcpa. html 42 Copyright © 2011 M. E. Kabay. All rights reserved.

Health Insurance Portability and Accountability Act (HIPAA), 1996 Ø 42 USC 1297 ii Ø Protects employees who change jobs but want to keep their health insurance Ø Mandates administrative simplification Ø Privacy provisions affect everyone who collects, keeps and transmits medical information Ø Patients must have full access to their medical files Ø Standards for protecting individually identifiable health information Ø http: //www 4. law. cornell. edu/cgibin/htm_hl? DB=uscode&STEMMER=en&WORDS=hipaa+&COLOUR=Red&STY LE=s&URL=/uscode/42/1397 ii. html Ø Also overview at http: //www. hcfa. gov/hipaahm. htm 43 Copyright © 2011 M. E. Kabay. All rights reserved.

Gramm-Leach-Bliley Act (GLB), 1999 Ø Financial Services Modernization Act Ø Many sections dealing with structure of banks, securities firm Ø Title V – Privacy q. Clear disclosure of privacy policies q. Notice to consumers q. Opt-out of sharing consumer info q. Enforced by FTC, federal banking agencies, SEC, National Credit Union Administration Ø http: //www. senate. gov/~banking/conf/grmleach. htm 44 Copyright © 2011 M. E. Kabay. All rights reserved.

Recent US Laws Affecting Privacy Ø U. S. A. P. A. T. R. I. O. T. Act q. Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act q. Called the “US Patriot Act” to sway public opinion in its favor q. Passed by a Congress whose members did not read the text of the Act Ø TIA System q. Total Information Awareness 45 Copyright © 2011 M. E. Kabay. All rights reserved.

U. S. A. P. A. T. R. I. O. T. Act Ø http: //w 2. eff. org/patriot/ Ø Signed 2001 -10 -26 Ø Based on premise that civil liberties prevented discovery of 9/11 plot 46 Copyright © 2011 M. E. Kabay. All rights reserved.

U. S. A. P. A. T. R. I. O. T. Act Ø Warrant can be obtained without providing evidence to justify request q. Inform any judge that surveillance is “relevant” to an investigation q. Target need not be subject of investigation q. No requirement to report findings to judge or to subject q. Judge has only 2 choices under Act: üGrant permission üAccuse law enforcement of lying Ø Easier surveillance in cases of suspected computer crime – some without court order 47 Copyright © 2011 M. E. Kabay. All rights reserved.

U. S. A. P. A. T. R. I. O. T. Act (cont’d) Ø Extension of Foreign Intelligence Surveillance Act (FISA) q. Allows surveillance of US citizens and residents by CIA & NSA Ø Information sharing between intelligence agencies and law enforcement q. Had been separated after abuses in 1950 s & 1960 s Ø Increased authority to Attorney General to circumvent restrictions on domestic surveillance limitations 48 Copyright © 2011 M. E. Kabay. All rights reserved.

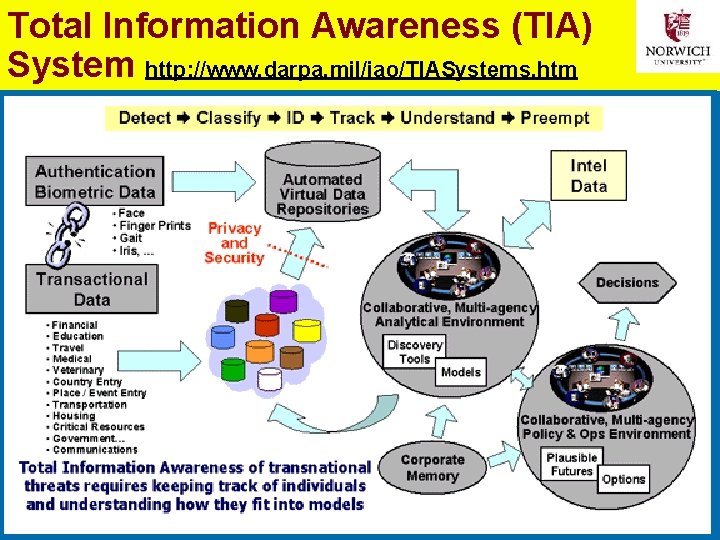
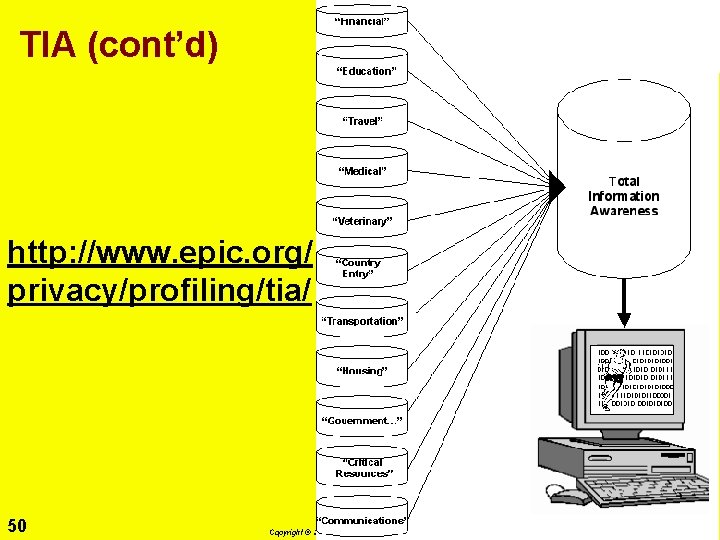
Total Information Awareness (TIA) System http: //www. darpa. mil/iao/TIASystems. htm 49 Copyright © 2011 M. E. Kabay. All rights reserved.

TIA (cont’d) http: //www. epic. org/ privacy/profiling/tia/ 50 Copyright © 2011 M. E. Kabay. All rights reserved.

TIA (cont’d) Ø Project funding shut down by Congress in September 2003 Ø Closed Pentagon’s Information Awareness Office Ø Student profiling continues under other programs q. See http: //www. epic. org/privacy/student/ 51 Copyright © 2011 M. E. Kabay. All rights reserved.

Defending Privacy in Cyberspace Ø Technology q. Encryption q. Steganography q. Anonymizers Ø Organizations q. Privacy International http: //www. privacyinternational. org q. Electronic Privacy Information Center (EPIC) http: //www. epic. org q. Center for Democracy and Technology http: //www. cdt. org q. Electronic Frontier Foundation http: //www. eff. org 52 Copyright © 2011 M. E. Kabay. All rights reserved.

Reading about Privacy Ø Diffie, W. & S. Landau (1998). Privacy on the Line - The Politics of Wiretapping and Encryption. MIT Press (Cambridge, MA). ISBN 0 -262 -04167 -7. 342 pp. Ø Garfinkel, S. (2000). Database Nation: The Death of Privacy in the 21 st Century. O’Reilly (Sebastopol, CA). ISBN 1 -565 -92653 -6. vii + 312. Index. Ø Nissenbaum, H. F. (2009). Privacy in Context: Technology, Policy, and the Integrity of Social Life. Stanford Law Books (Stanford, CA). ISBN 0 -804 -75237 -0. 304 pp. 53 Copyright © 2011 M. E. Kabay. All rights reserved.

Review Questions (1) 1. Define different kinds of privacy (4) 2. What did Justice Louis Brandeis famously say about privacy? (1) 3. Does the US Constitution explicitly use the word “privacy”? (1) 4. Does the US Constitution protect privacy rights? Where? (4) 5. Explain how modern information technology has encroached upon privacy (10) 6. Contrast the US and European legal constraints on information about consumer behavior (4) 54 Copyright © 2011 M. E. Kabay. All rights reserved.

Review Questions (2) 7. What is a “Web bug” and how does it affect privacy? (4) 8. What is “spyware? ” Why do many people object to spyware? (4) 9. How has the U. S. A. P. A. T. R. I. O. T. Act changed US law concerning privacy rights? (10) 10. What is a “cookie” in information technology? Do cookies necessarily infringe privacy? Explain. (5) 11. Be prepared to give the names of key US laws protecting privacy given a brief description of the laws. 55 Copyright © 2011 M. E. Kabay. All rights reserved.

DISCUSSION 56 Copyright © 2011 M. E. Kabay. All rights reserved.