Privacy Security and Trust Issues arising from Cloud
















- Slides: 19

Privacy, Security and Trust Issues arising from Cloud Computing Siani Pearson and Azzedine Benameur International Conference of Cloud Computing Technology and Science, 2010 Presented by Shameek Bhattacharjee Fall 2011, Oct 25 th

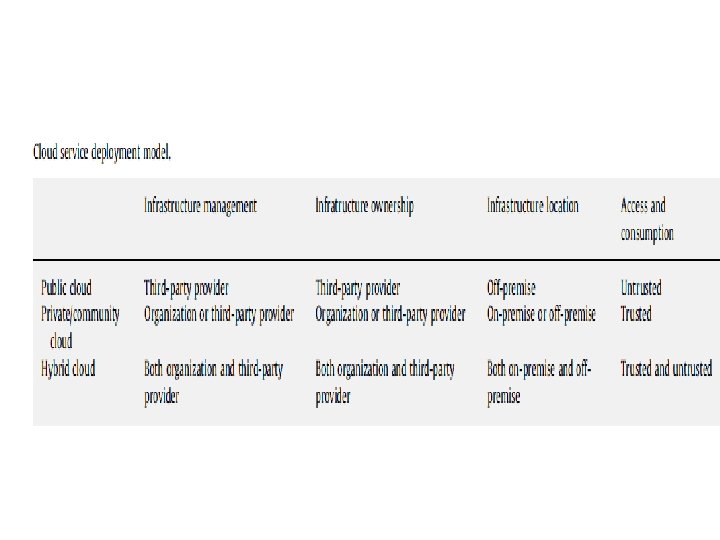
Background • Cloud Computing is a new paradigm that offers a number of new features. • Any new paradigm has weaknesses characteristic to its very design. Difference between Vulnerability and Security Threat The inherent design of a new paradigm that provides new features also creates new avenues that may be potentially harnessed by malicious entities. These issues are a part of vulnerability assessment. A vulnerability in a system causes a security threat. Security and privacy threats are often contextual and depends on a number of parameters, deployment (Private, Public, Hybrid etc. ) and service delivery model ( Saa. S, Paa. S, Iaa. S).

Challenges in Cloud Computing • Elasticity : Allows dynamic expansion and shrinkage of resources makes it difficult to monitor what resources are used and in which country. • Geographical: The cross section of the variety of resources used spans different countries and continents and hence makes compliance with regulations related to data handling difficult. • Volatility of Resources: exacerbates the process of auditing. • Multi-tenancy/Virtualization: Customers are users of multitenant apps in Saa. S. The partition used to separate data of each client may be broken. Use of virtualization may introduce new threats like cross VM side channel attacks. It is possible to break the partition created by use of VMs. • • Outsourcing Nature: creates a challenge on data privacy as data is present in another machine owned & operated by another organization.

Vulnerabilities and Threats related to Privacy • Lack of User centric control over data - Service provider becomes responsible for storage of data in Saa. S environment. - How to provide adequate trust for consumers to switch cloud services? - Causes vendor lock in. Threats o Secondary usage of customer data by CSP. E. g. a CSP may sell a consumer’s business sales data to its competitors for money. o In an event of vendor demise, bankruptcy, or a vendor being acquired by another CSP, there may be concerns on the data already being held.

Vulnerabilities and Threats related to Privacy contd. . • Availability, Data Proliferation, Self healing - To provide availability the CSP’s replicate data on multiple data centers. Back up is critical for providing resilience. Cloud provider’s may depend on seamless backups for infrastructure resilience. - There is data flow across legal jurisdictions Threats o It is difficult to ensure that if a deletion request is made all the copies of such data will be deleted. o Issues of jurisdiction may be really complicated and questions may raise on what law applies and legal remedy applicable due to heterogeneity of laws across zones.

• Dynamic Nature of Cloud Computing o It is difficult to pin point which specific server or storage device will be used and this worsens the issue of transborder data flow. o It’s not clear how to assign liability to a security breach or violation of law. o Difficult to decide which parties responsible for what aspects of security. o There is no trust boundary due to fuzzy boundaries as to where data is stored and processed. Private clouds may be solution, but the cost is really high.

Vulnerabilities and threats in cloud • Self Optimization – feature allows automatic adaptation of services to meet changing requirements; provides elasticity, scalability, intelligence. This Hampers the ability to maintain consistent security standards. • Lack of Standardization- makes it difficult to establish security frameworks for heterogeneous environments. • Use of virtualization: Virtualization is used to maximize resource utilization which is an USP of cloud computing. Although VM’s are meant for isolation, it is possible to break the isolation through cross VM side channel attacks to obtain data from a target VM on the same machine.

A few hurdles • Increase of IT management overhead with multiple Saa. S products, because the model needs to mimic organizational boundary within the cloud , as multiple SMBs will be deploying their business processes on a single cloud environment. • • Same data in more than one legal location with different legal consequences. Efficient processing of encrypted data at rest in cloud is difficult till date.

Vulnerabilities in S. a. a. S delivery model Co-Located Customers • The customers are co-located on the same provider’s infrastructure and provider must keep each customer from seeing each other’s data. • A malicious entity may also enter as a customer and then access other customer’s information. • You can hack through loopholes in the application or inject client code into Saas System. The above vulnerability is a threat to proper data segregation and privacy. Checks for SQL injection flaws may be a way to check. Locality of data not known • In this scenario the customer is not sure where the data is stored. There is always a question of whose jurisdiction the data falls under and what are the consequences. It acts as a deterrent to use Saa. S. Difficulty to achieve data integrity • Integrity in stand alone systems with a single DB is achieved easily by ensuring the preservation of database constraints and transactional properties ( ACID properties). But in cloud the Saa. S are multi-tenant applications hosted by a third party.

A few hurdles • • Saa. S apps. expose their functionality through XML based APIs. At protocol level, does not support transaction or guaranteed delivery, so the only option is to implement them at the API level. The standards available for ensuring data integrity is not yet mature (e. g. WS Transaction). So most Saa. S vendors expose their web services API without transaction support. Each Saa. S app. may have different levels of availability and SLA that makes it difficult to ensure data integrity properties across multiple Saa. S applications. The above vulnerabilities are a threat to data integrity. Difficulties in web application security • • Saa. S has to be managed over the web. The challenge with Saa. S security is almost similar to any web application technology but the problem is that traditional security solutions like network firewall, intrusion detection do not adequately address the problem. The open web application Project has identified top ten threats

Vulnerabilities contd. . Cloud becomes a High Value Target Since data from various users and organizations are under the same umbrella breaking into cloud will attack a broad spectrum of users. Hence it becomes a lucrative target from malicious entities’ point of view. • Virtualization Vulnerabilities Many bugs have been found in all popular VMM’s that allow escapes from VM, possible to bypass certain restrictions. e. g. 1. The vulnerability of Microsoft Virtual PC and Microsoft Virtual Server could allow a guest OS user to run code on host or other guest OS. 2. The vulnerability in Xen due to input validation error. Exploited by root user of a guest domain to execute arbitrary commands in domain 0 via crafted entries in grub. conf.

Vulnerabilities in Paa. S • • • Any security below the application layer is under the jurisdiction of the provider who has to provide a strong assurance of data security and privacy. More extensible as compared to Saa. S , so there is more provision for customer to layer on additional security according to requirement. Vulnerabilities of cloud are not only associated with web apps but also machine to machine SOA (service oriented architecture) applications.

Vulnerabilities in Iaa. S • • • Consumer is responsible for the security controls that related IT systems, like OS, apps, data. The vulnerabilities are contextual based on deployment model. Public clouds at greater risk. The path of data transmitted from source to destination through a large number of third party infrastructure devices. There’s a possibility that one of them belongs to intruder’s infrastructure. Space is virtually allocated, and users do not know One or VMs may be used for programs to run, but when the task is finished and resources are released, the media may not be wiped, and the next user it is possible to recover previous user’s data. This is due to the feature that control over data life cycle is short lived.


Trust Issues in Cloud computing • • Since users have lack of control over resources they have to rely on trust mechanisms and contracts in conjunction with mechanisms that provide a compensation. But trust is a very fuzzy concept very difficult to calculate in a heterogeneous environment that is assessed by human or social trust. A Combination of social and technological trust. It can be done through vouching mechanism. Entities that are trusted vouch for the method of providing information. Weak Links in a Trust Chain – - contractors may be sub contracting without your knowledge. - contract requirements may not be propagated down the chain. In order to provide extra capacity at short notice or real time, new providers are hastily added without adequate background research or the knowledge of customer. Lack of public relations. Legislation has to be updated before to address the challenges.

Some Remedies • Contractual issues in Data Handling mechanism : - Clarifying in what geographical regions data is located and notify if there’s a change. - what happens when agreement ends. • Data Security mechanism: - For some critical data, a trade-off between efficiency of data processing and security (encrypted) may be made. Obfuscate some data before transferring to the cloud. • Standardization - Important to track what a CSP is doing and how data is stored, accessed controlled etc. ; only then can there be assessment. • Accountability - What is worse than violation is no clear entity to blame. Create laws for accountability profile

• - Increase trust Attaching individual privacy rights directly to identity data. Personal devices under our physical control to act on our behalf. Intelligent software agents in the personal device or with the cloud that automates scanning, negotiating, reveal identity information.

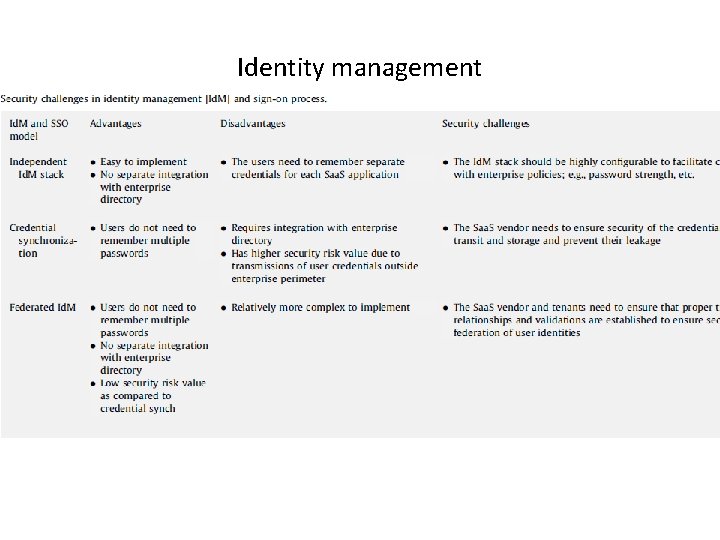
Identity management

References Primary References • Siani Pearson and Azzedine Benameur , `` Privacy, Security and Trust Issues Arising from Cloud Computing”, In Proc. of 2 nd IEEE International Conference on Cloud Computing Technology and Science, 2010. • S. Subashini and V. Kavitha, ``A survey on security issues in service delivery models of cloud computing”, In Elsevier Journal of Network and Computer Applications , July 2010. Auxiliary References • X. Zhang, N. Wuwong, H. Li and X. Zhang, ``Information security risk management framework for cloud computing environment”, In Proc. of IEEE International Conference on Computer and Information Technology, 2010. • A few white papers.