Privacy information access and security the perils of











































































- Slides: 118

Privacy, information access, and security – the perils of online searching in a panopticon society donna Bair-Mundy

Intercepting topics Security Libraries Privacy Surveillance

Topics What is privacy? Why do we need it? Why do we need surveillance? Creating a Surveillance Society: Building the Panopticon What does this have to do with online searching? Privacy in Libraries

Discussion questions: What is privacy? Why do we need it?

Informational privacy - Westin's definition - part 1 Privacy is the claim of individuals, groups, or institutions to determine for themselves when, how, and to what extent information about them is communicated to others. Control Westin, Alan F. 1970. Privacy and freedom. London: Bodley Head.

Informational privacy - Westin's definition - part 2 Viewed in terms of the relation of the individual to social participation, Choice privacy is the voluntary and temporary withdrawal of a person from the Temporal general society through physical or psychological means, either in a state of solitude or, when among larger groups, in a condition of anonymity or reserve. Varied means


Informational privacy - Westin's definition - part 3 The individual's desire for privacy is never absolute, since participation in society is an equally powerful desire. Ongoing dialectic

Informational privacy - Westin's definition - part 4 Thus each individual is continually engaged in a personal adjustment process in which he balances the desire for privacy with the desire for disclosure and communication of himself to others, in light of the environmental conditions and social norms set by the society in which he lives. Social norms


Informational privacy - Westin's definition - part 5 The individual balances the desire for privacy with the desire for disclosure and communication of himself to others] in the face of pressures from the curiosity of others and from the processes of surveillance that every society sets in order to enforce its social norms. Privacy v. Surveillance

Release from tensions of life in society requires release from pressure of playing social roles Westin's privacy theory: 4 Power to define functions of privacy the boundaries of the “core self” Personal autonomy Emotional release Self-evaluation Limited & protected communication Need to integrate experiences into Share confidences and meaningful pattern; Westin, Alan F. 1970. Privacy and freedom. London: intimacies only with those one essential for creativity trusts Bodley Head.

Individual privacy versus individual secrecy Privacy Allowed and in some cases required for socially-sanctioned acts. Stress reducing. Secrecy Involves socially proscribed acts. Stress inducing. Margulis, Stephen T. 1977. Conceptions of privacy: current status and next steps. Journal of social issues 33(3): 5 -21, p. 10. Margulis, Stephen T. 2003. Privacy as a social issue and behavioral concept. Journal of social issues 59(2): 243 -261.

Election day Us Us Them Us

On the network news: Ayman al-Zawahiri

So you do a search. . .

A few days later. . . How do you feel?

Discussion question: Why do we need surveillance?

Need for surveillance (1)

Need for surveillance (2)

Need for surveillance (2)

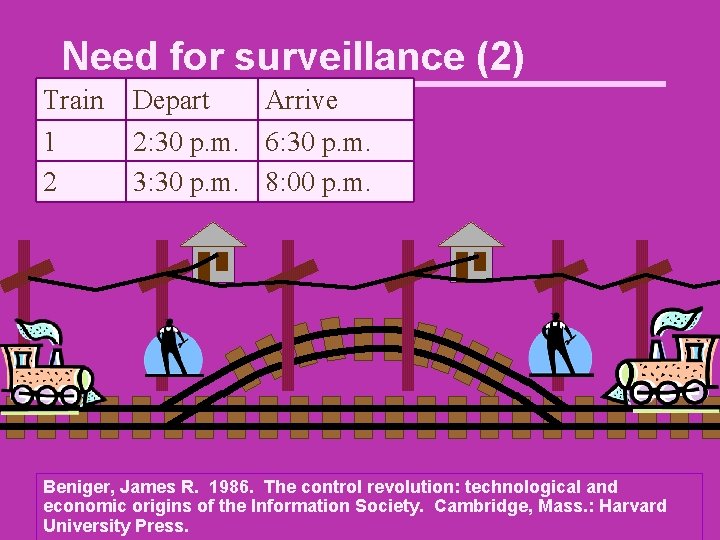
Need for surveillance (2) Train 1 2 Depart Arrive 2: 30 p. m. 6: 30 p. m. 3: 30 p. m. 8: 00 p. m. Beniger, James R. 1986. The control revolution: technological and economic origins of the Information Society. Cambridge, Mass. : Harvard University Press.

Surveillance in a transforming society Zuboff, Shoshana. 1988. In the age of the smart machine: the future of work and power. New York: Basic Books.

Roles of Surveillance (1) Used to catch the criminals Used as means to control workers Necessitated by technology Facilitated by technology

Roles of surveillance (2) Provision of services (Social Security) Allows participation (Voter registration) Protection against threat Means of social control • Discover and rout deviance • Threat of surveillance used to promote compliance with the law

Routing out “deviants” Round-up of Pennsylvania Quakers (1777) Sedition Act of 1798 Espionage Act of 1917 – 1918 amend. Internment of persons of Japanese ancestry—WW II Used against Hungarians, Czechs, Slovaks, Croats, Poles, Jews, Russians, Lithuanians, Finns, Irish, Catholics, Amish, Mennonites, Jehovah’s Witnesses (then called Russelites), Roma (then called gypsies), African Americans.

Dealing with dissidents President Franklin Roosevelt had FBI spy on New Deal opponents President Johnson had FBI spy on opponents of his Vietnam War policy President Nixon had FBI, CIA, NSA, IRS, and Army Intelligence spy on and harass his perceived enemies United States. Congress. Senate. The Select Committee to Study Governmental Operations with Respect to Intelligence Activities. 1976. Final report.

“COINTELPRO New Left” FBI program to “expose, disrupt, and otherwise neutralize” activities groups and individuals affiliated with the “New Left” Extensive and mostly illegal surveillance United States. Congress. Senate. The Select Committee to Study Governmental Operations with Respect to Intelligence Activities. 1976. Final report.

“COINTELPRO New Left” Had members arrested on marijuana charges Sent anonymous letters about a student’s activities to parents, neighbors, and the parents’ employers Sent anonymous letters about New Left faculty members (signed “A Concerned Alumni” or “A Concerned Taxpayer”) to university officials, legislators, Board of Regents, and the press United States. Congress. Senate. The Select Committee to Study Governmental Operations with Respect to Intelligence Activities. 1976. Final report.

Creating a Surveillance Society: Building the Panopticon

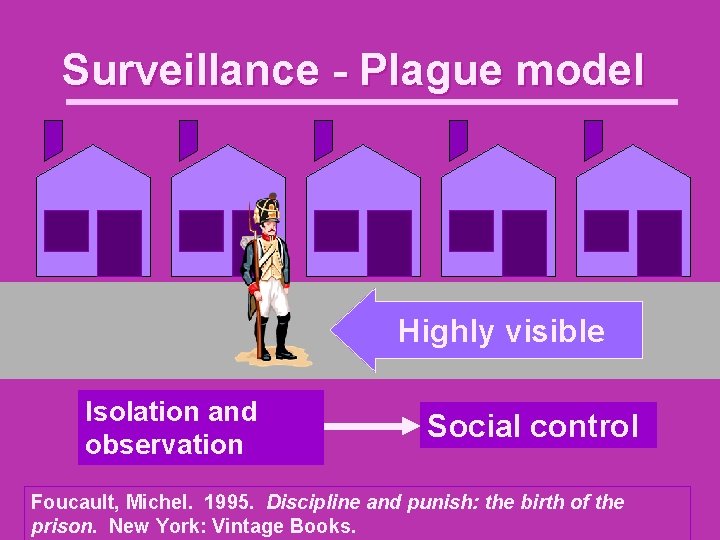
Surveillance - Plague model Highly visible Isolation and observation Social control Foucault, Michel. 1995. Discipline and punish: the birth of the prison. New York: Vintage Books.

Surveillance—Panopticon model Jeremy Bentham • • Legal theorist Rationalism Utilitarianism Eccentric

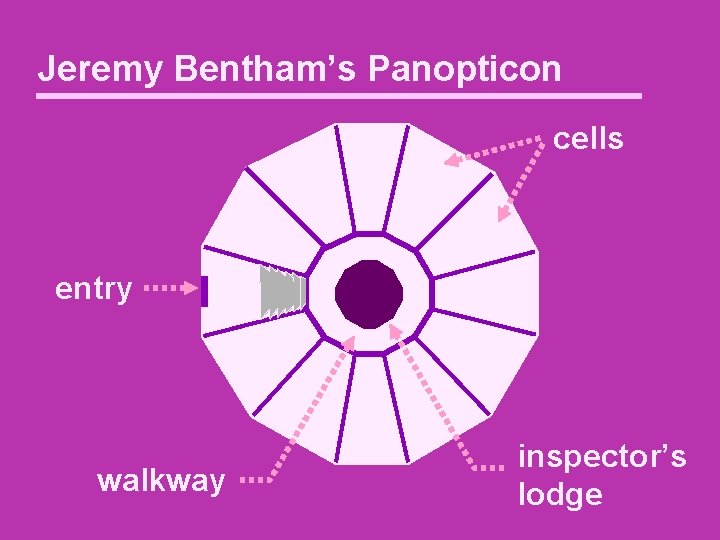
Jeremy Bentham’s Panopticon cells entry walkway inspector’s lodge

Panopticon society

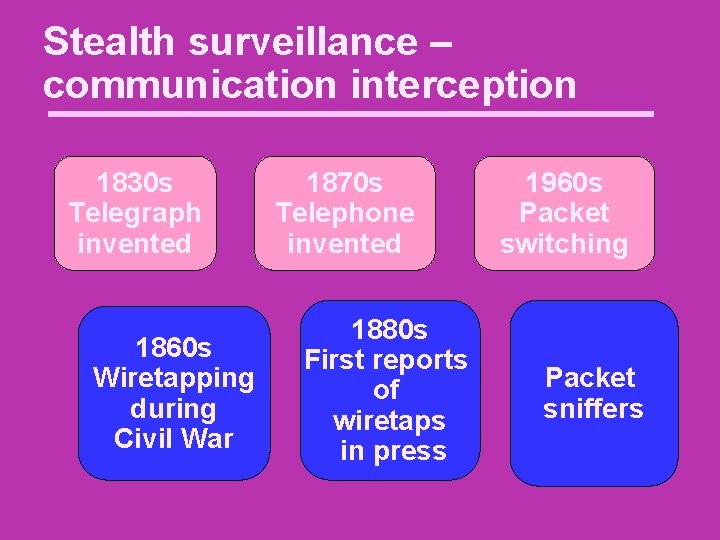
Stealth surveillance – communication interception 1830 s Telegraph invented 1860 s Wiretapping during Civil War 1870 s Telephone invented 1880 s First reports of wiretaps in press 1960 s Packet switching Packet sniffers

What does this have to do with online searching?

Online searching – Google jacso “as we may search” One of Google’s servers

Sending your search request (1) search 1 2 3

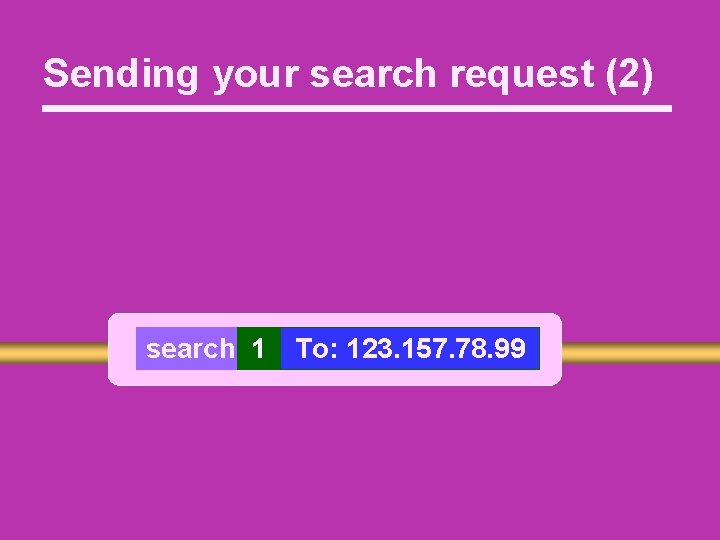
Sending your search request (2) search 1 To: 123. 157. 78. 99

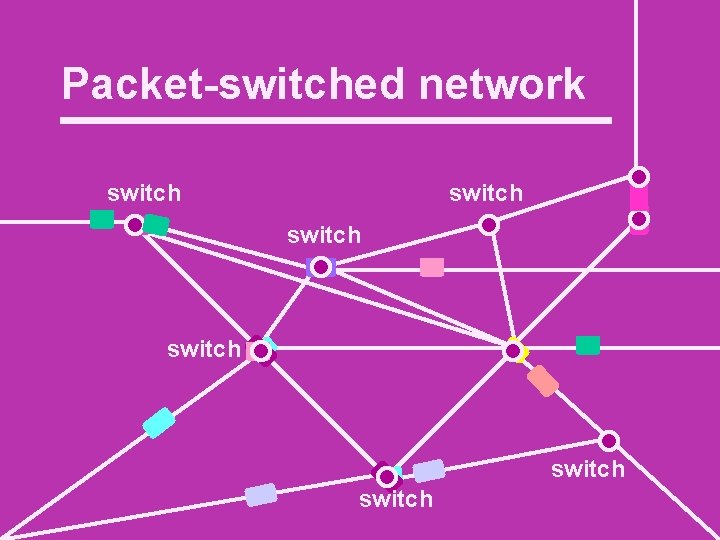
Packet-switched network switch switch

Online searching Server where the database resides

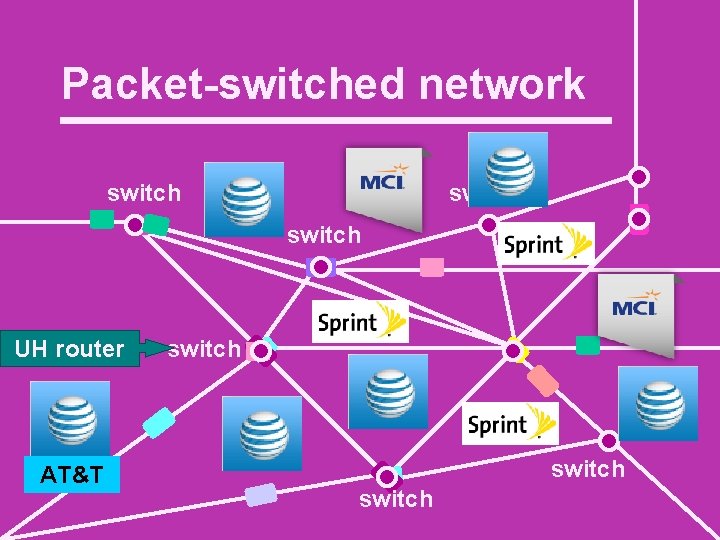
Packet-switched network switch UH router AT&T switch

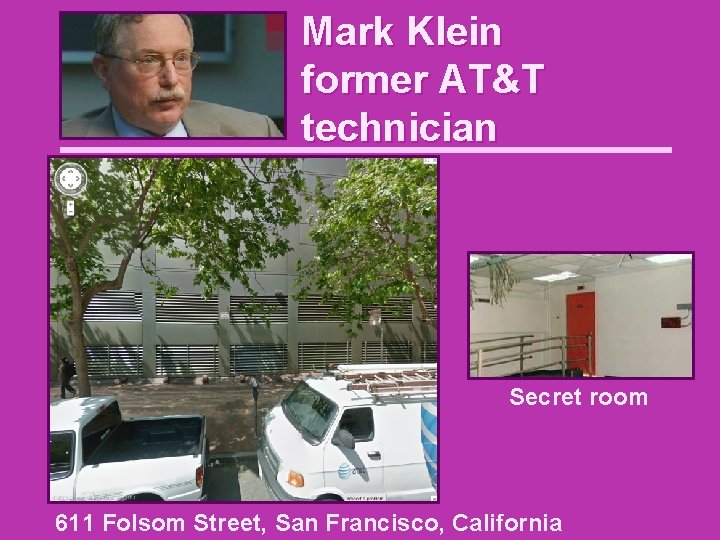
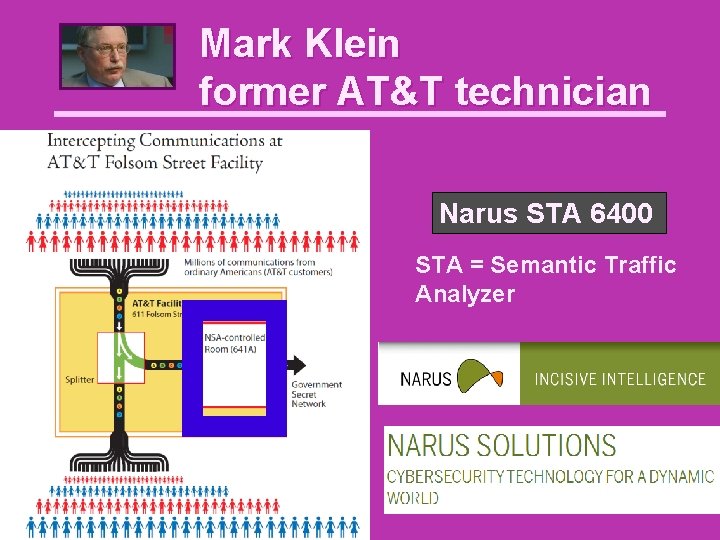
Mark Klein former AT&T technician Secret room 611 Folsom Street, San Francisco, California

Mark Klein former AT&T technician Narus STA 6400 STA = Semantic Traffic Analyzer

William Binney former intelligence official with the NSA Saw that the NSA was spying on domestic communications Quit the NSA in 2001 Became a whistle-blower Estimated that he NSA had intercepted trillions of communications "transactions" of Americans such as phone calls, emails, and other forms of data (but not including financial data)

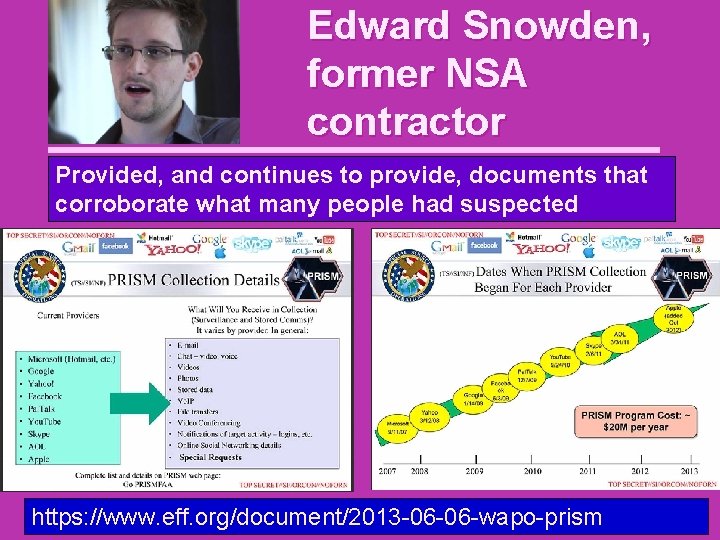
Edward Snowden, former NSA contractor Provided, and continues to provide, documents that corroborate what many people had suspected https: //www. eff. org/document/2013 -06 -06 -wapo-prism

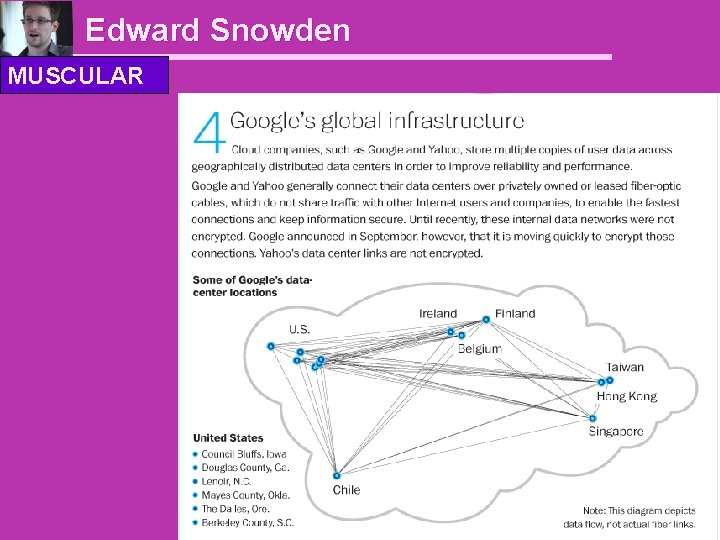
Edward Snowden MUSCULAR – NSA and GCHQ secretly raided data from Google and Yahoo

Edward Snowden MUSCULAR

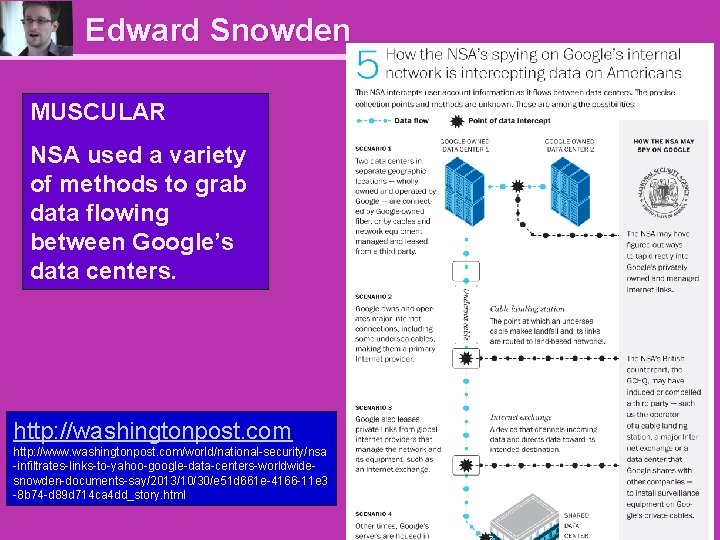
Edward Snowden MUSCULAR NSA used a variety of methods to grab data flowing between Google’s data centers. http: //washingtonpost. com http: //www. washingtonpost. com/world/national-security/nsa -infiltrates-links-to-yahoo-google-data-centers-worldwidesnowden-documents-say/2013/10/30/e 51 d 661 e-4166 -11 e 3 -8 b 74 -d 89 d 714 ca 4 dd_story. html

Spy programs that we know of PRISM accessing Internet data of 9 major Internet companies in the U. S. MUSCULAR Secretly broke into main communication links that connect Yahoo and Google data centers around the world UPSTREAM cable-tapping of fiber cables and infrastructure, giving direct access to fiber-optic cables that carry Internet and telephone traffic via AT&T, Verizon, Sprint

Spy programs that we know of SHELLTRUMPET metadata program targeting international communications BULLRUN program “to defeat encryption used in specific network communication technologies”

Google fighting back https: //www. google. com/

Privacy in Libraries

ALA on Confidentiality • The First Amendment’s guarantee of freedom of speech and of the press requires that the corresponding rights to hear what is spoken and read what is written be preserved, free from fear of government intrusion, intimidation, or reprisal. • In seeking access or in the pursuit of information, confidentiality is the primary means of providing the privacy that will free the individual from fear or intimidation or retaliation.

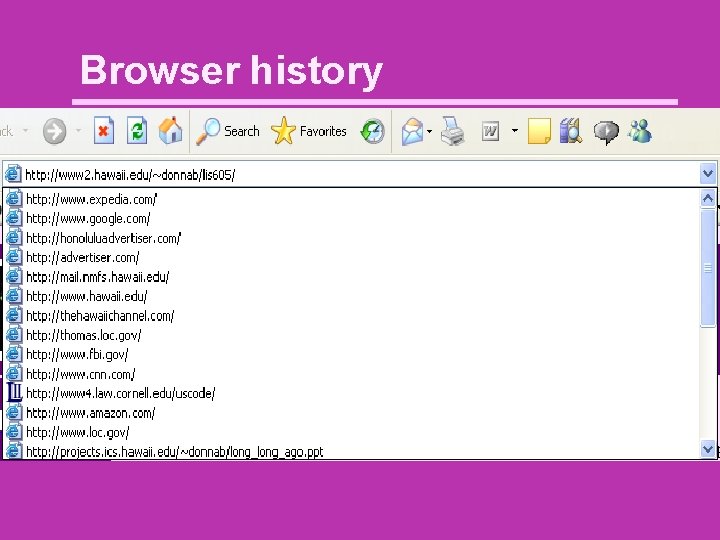
Browser history

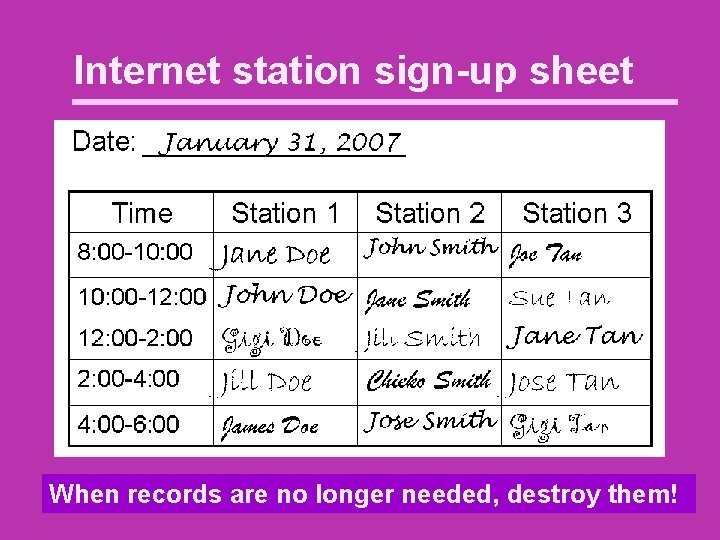
Internet station sign-up sheet When records are no longer needed, destroy them!

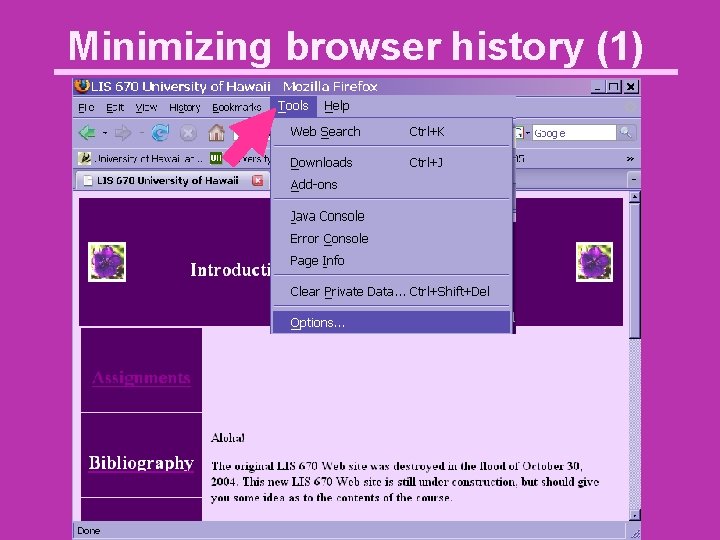
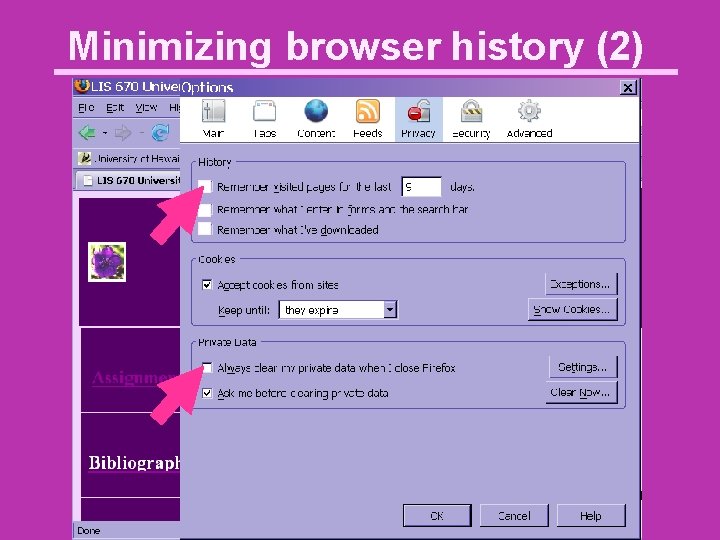
Minimizing browser history (1)

Minimizing browser history (2)

Web Server Log

Web Server Statistics Who: Countries . . . Full list . . . Regions . . . Cities Hosts . . . Full list . . . Last visit Authenticated users . . . Full list . . . Last visit Navigation: Visits duration Viewed Operating Systems Browsers Referrers: Origin . . . Referring search engines . . . Referring sites Search . . . Search Keyphrases . . . Search Keywords

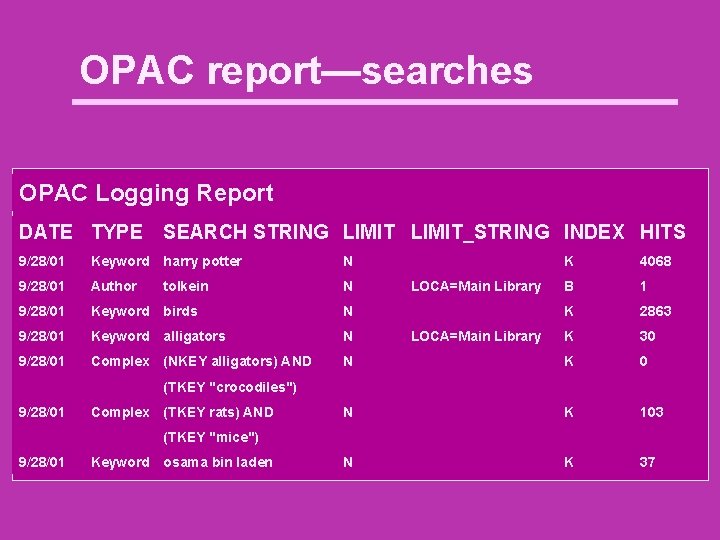
OPAC report—searches OPAC Logging Report DATE TYPE SEARCH STRING LIMIT_STRING INDEX HITS 9/28/01 Keyword harry potter N 9/28/01 Author N 9/28/01 Keyword birds N 9/28/01 Keyword alligators N 9/28/01 Complex (NKEY alligators) AND tolkein K 4068 B 1 K 2863 K 30 N K 103 N K 37 LOCA=Main Library (TKEY "crocodiles") 9/28/01 Complex (TKEY rats) AND (TKEY "mice") 9/28/01 Keyword osama bin laden

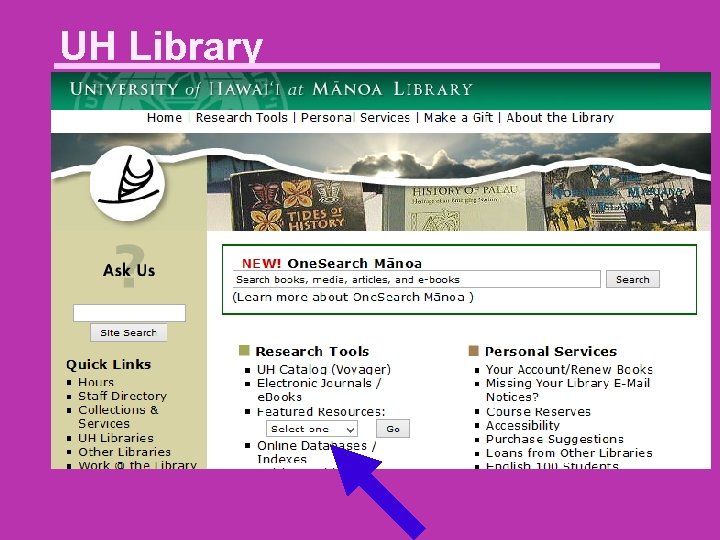
UH Library

Log in screen

What can we do? (ALA tips) • Conduct privacy audits • Identify the type and nature of all records and files that contain library patron and user personally identifiable information • Establish a schedule for the retention of records and files containing library patron and user personally identifiable information Detail the specific steps staff should follow in responding to investigatory requests for patron and user personally identifiable information from governmental agencies

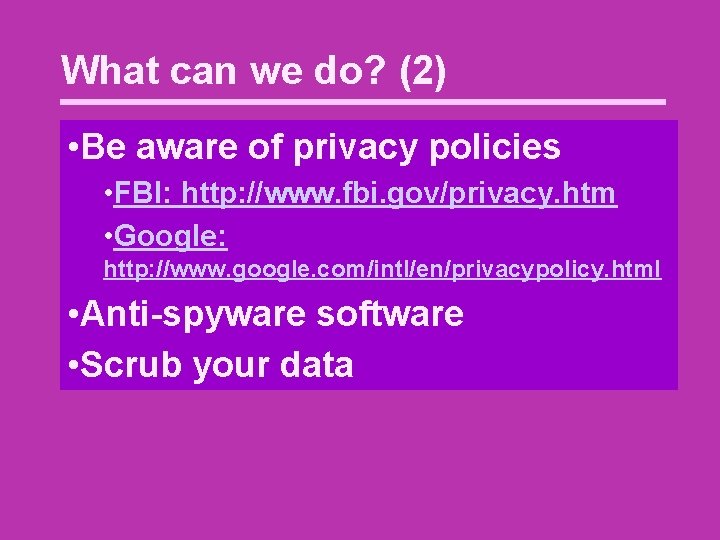
What can we do? (2) • Be aware of privacy policies • FBI: http: //www. fbi. gov/privacy. htm • Google: http: //www. google. com/intl/en/privacypolicy. html • Anti-spyware software • Scrub your data

Questions ?

Mahalo

USA PATRIOT Act & Libraries (1) • June 8, 2004 – FBI demands list from Deming branch of Whatcom Country Library System of everyone who had borrowed a biography of Osama bin Laden since November 2001. • Library refused. • 15 days later, FBI withdrew its request.

USA PATRIOT Act & Libraries (1) • 2005– FBI presents National Security letter and demands “any and all subscriber information, billing information, and access logs of any person or entity” associated with a specified IP address during a specified period • Librarians fought gag order in court • Librarians speak out

Library Awareness Program • Begun during Cold War* • Desire to restrict access to unclassified scientific information by foreign nationals • Desire to recruit librarians to report on “foreigners” • Agent told librarians to report name and reading habits of anyone with a foreign sounding name or foreign sounding accent • Librarians who criticized program were investigated *Curt Gentry gives onset year as 1962: Gentry, Curt. 1991. J. Edgar Hoover: the man and the secrets. New York: Norton. , pp. 759 -760.

Online searching in the library

Do we have legal protections? Privacy and the Law

Do we have legal protections? Privacy and the Law

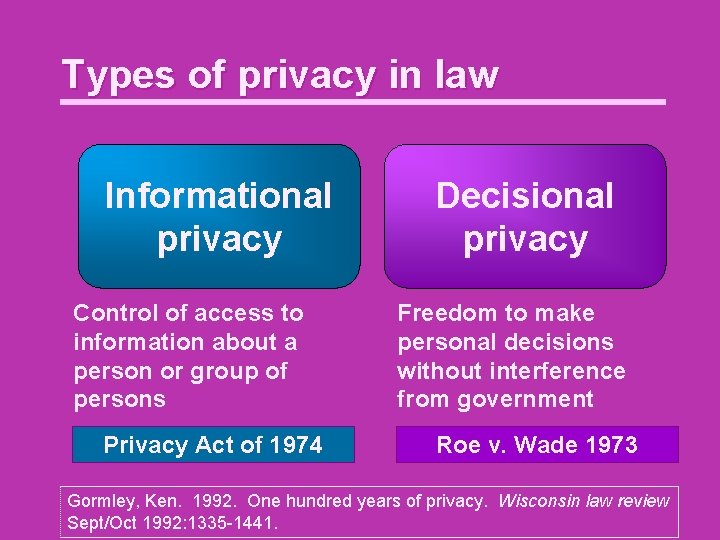
Types of privacy in law Informational privacy Control of access to information about a person or group of persons Privacy Act of 1974 Decisional privacy Freedom to make personal decisions without interference from government Roe v. Wade 1973 Gormley, Ken. 1992. One hundred years of privacy. Wisconsin law review Sept/Oct 1992: 1335 -1441.

American Constitution • Heavily influenced by natural rights philosophy (John Locke) • After extensive argument decided to include a Bill of Rights

Bill of Rights debate: Mason, Jefferson, et al. When assigning powers to the government must also limit those powers General warrants and writs of assistance

Objections to Bill of Rights is stipulation a king gives to his subjects, granting a few exceptions to rights of the monarch Bill of Rights dangerous—implies government has powers not Could later be misconstrued as allinclusive not granted (Alexander Hamilton, Federalist paper no. 84, etc. )

The compromise Amendment IX The enumeration in the Constitution of certain rights shall not be construed to deny or disparage others retained by the people.

Fourth Amendment The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.

Privacy an old concern Halakhah (Jewish law) Proscriptions on: Physical intrusion Visual surveillance Aural surveillance Talmud Walls between houses to be a certain height Creditor may not enter person’s house Ancient Roman law (Justinian’s Pandects) Prohibition against going into a home and dragging out the person Hippocratic oath No disclosure of what in practice seen or heard that “ought never be published abroad”

General warrants (1) • • No specific individual No specific crime No specific place to be searched No specific items to be sought • Illegal according to Sir Edward Coke’s Institutes of the Lawes of England (first published 1642 and 1644) • Illegality confirmed by Sir Matthew Hale • Illegality confirmed by Sir William Blackstone

General warrants (2) • Suspicion of crime related to government revenue • Used against anyone who dared to challenge or limit the authority of Parliament or the crown • John Wilkes (member of Parliament) • Anonymously wrote critical essay published in North Briton • General warrant leads to massive arrests, Wilkes ► Tower of London

Writs of assistance • Any customs official could enter “any House, shop, Cellar, Warehouse or Room or other Place. . . ” • Seize unaccustomed goods • Lasted for the life of the sovereign under which it was issued plus six months • According to John Adams, major factor in seeking American Independence

Fifth Amendment No person shall be held to answer for a capital, or otherwise infamous crime, unless on a presentment or indictment of a Grand Jury. . . ; nor shall any person be subject for the same offence to be twice put in jeopardy of life or limb; nor shall be compelled in any criminal case to be a witness against himself, nor be deprived of life, liberty, or property, without due process of law. . .

First Amendment Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances. Freedom of 1 st Amendment gives right to associate without surveillance (Lieber 1859)

Ex parte Jackson “The constitutional guaranty of the right of the people to be secure in their papers against unreasonable searches and seizures extends to their papers, thus closed against inspection, wherever they may be. Whilst in the mail, they can only be opened and examined under like warrant, issued upon similar oath or affirmation, particularly describing the thing to be seized. . . ” Justice Field 96 U. S. 727, 732

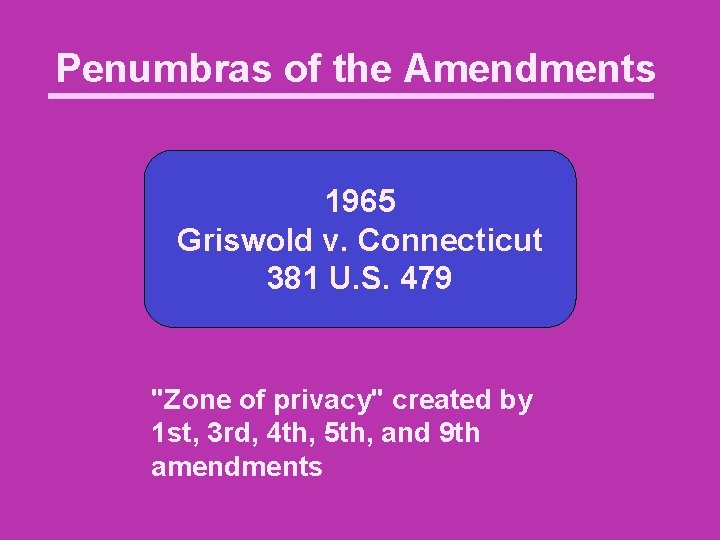
Penumbras of the Amendments 1965 Griswold v. Connecticut 381 U. S. 479 "Zone of privacy" created by 1 st, 3 rd, 4 th, 5 th, and 9 th amendments

Re-thinking constitutional privacy 1964 U. S. Senate Long Subcommittee Hearings on surveillance activities by federal agencies; first looked at IRS

No warrantless wiretapping in criminal cases 1967 Katz v. United States 389 U. S. 347

Congress Acts 1968 The Omnibus Crime Control and Safe Streets Act of 1968 (“Federal Wiretapping Act“), 18 USC Section 2510 et seq. Wiretapping illegal but when crime has been or is being committed law enforcement can, with a warrant, engage in wiretapping for limited periods. Provides judicial oversight for law enforcement wiretapping.

National security wiretapping 1972 U. S. v. U. S. District Court for the Eastern District of Michigan “Keith” “the customary Fourth Amendment requirement of judicial approval before initiation of a search applies in domestic security cases”

FISA 1978 Foreign Intelligence Surveillance Act U. S. Code 50 USC Sections 1801 -1863

Electronic mail 1993 ECPA Electronic Communications Privacy Act Addressed the need to protect e-mail.

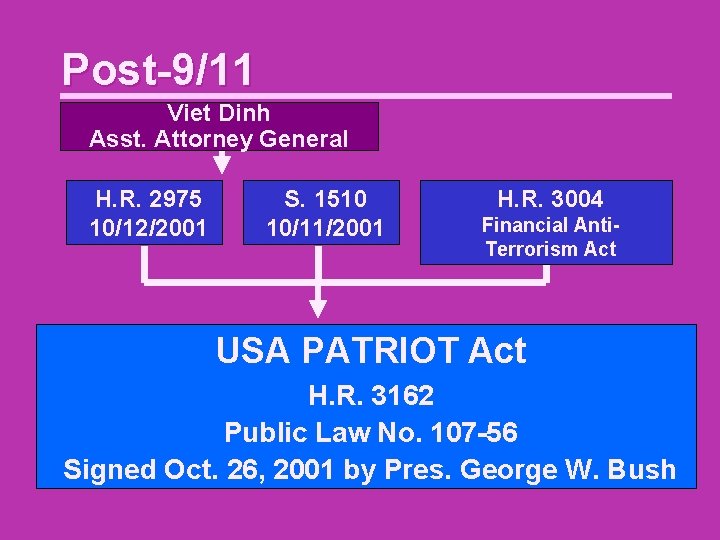
Post-9/11 Viet Dinh Asst. Attorney General H. R. 2975 10/12/2001 S. 1510 10/11/2001 H. R. 3004 Financial Anti. Terrorism Act USA PATRIOT Act H. R. 3162 Public Law No. 107 -56 Signed Oct. 26, 2001 by Pres. George W. Bush

The USA PATRIOT Act H. R. 3162 The Acronym Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism

The USA PATRIOT Act H. R. 3162 The Purpose To deter and punish terrorist acts in the United States and around the world, to enhance law enforcement investigatory tools, and for other purposes.

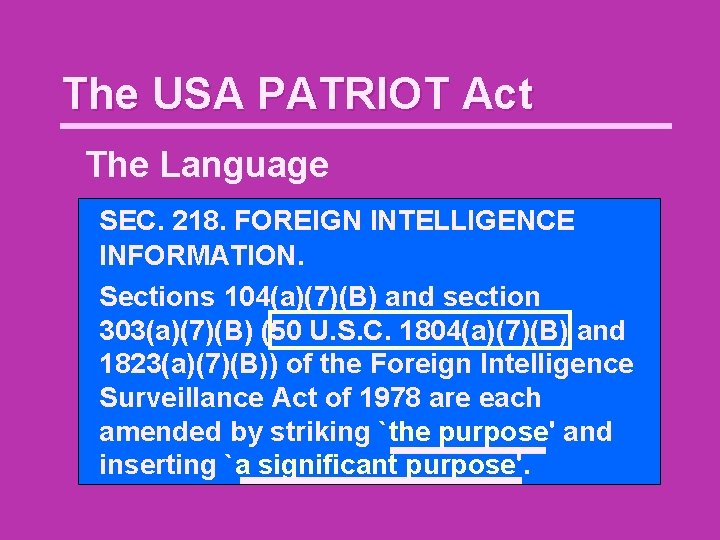
The USA PATRIOT Act The Language SEC. 218. FOREIGN INTELLIGENCE INFORMATION. Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'.

The U. S. Code Sections 104(a)(7)(B) and section 303(a)(7)(B) (50 U. S. C. 1804(a)(7)(B) and 1823(a)(7)(B)) of the Foreign Intelligence Surveillance Act of 1978 are each amended by striking `the purpose' and inserting `a significant purpose'. TITLE 50 > CHAPTER 36 > SUBCHAPTER I > § 1804. Applications for court orders (7) a certification … (B) that the purpose of the surveillance is to (B) that a significant purpose of the obtain foreign intelligence information; surveillance is to obtain foreign intelligence information;

Federal Wiretapping Act 1968 The Omnibus Crime Control and Safe Streets Act of 1968 (“Federal Wiretapping Act”) U. S. Code 18 USC Section 2510 et seq. Federal Rules of Criminal Procedure Rule 41 Search and Seizure

FISA 1978 Foreign Intelligence Surveillance Act U. S. Code 50 USC Sections 1801 -1863

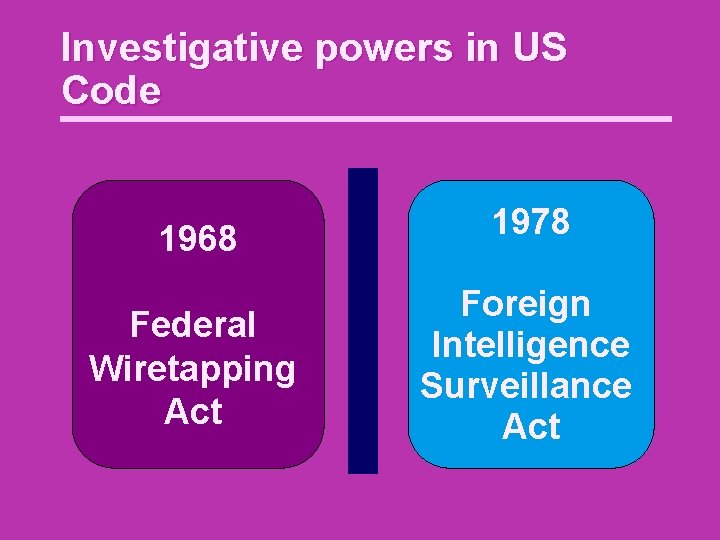
Investigative powers in US Code 1968 1978 Federal Wiretapping Act Foreign Intelligence Surveillance Act

The USA PATRIOT Act The Complaints— Records vulnerable Section 215—Amending FISA 501(a) The Director of the [FBI] or a designee of the Director. . . may make an application for an order requiring the production of any tangible things (including books, records, papers, documents, and other items) for an investigation to protect against international terrorism or clandestine intelligence activities, provided that such investigation of a United States person is not conducted solely upon the basis of activities protected by the first amendment to the Constitution.

The USA PATRIOT Act The Complaints—Freedom of Speech Section 215—Amending FISA 501(d) No person shall disclose to any other person (other than those persons necessary to produce the tangible things under this section) that the Federal Bureau of Investigation has sought or obtained tangible things under this section.

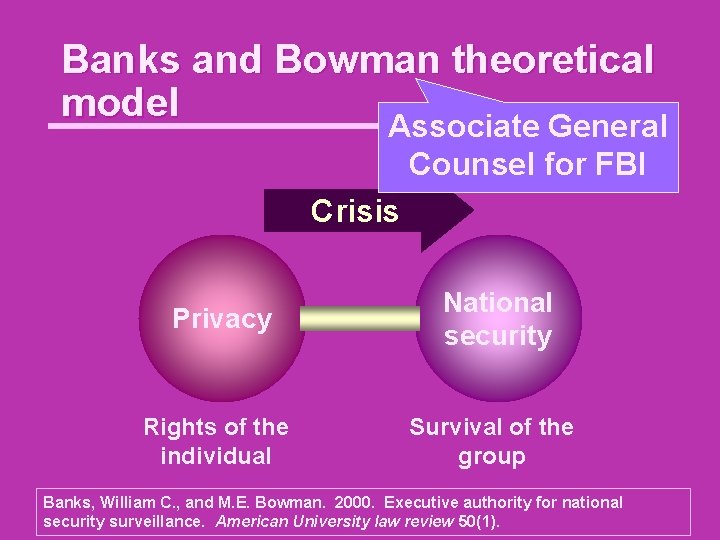
Banks and Bowman theoretical model Associate General Counsel for FBI Crisis Privacy National security Rights of the individual Survival of the group Banks, William C. , and M. E. Bowman. 2000. Executive authority for national security surveillance. American University law review 50(1).

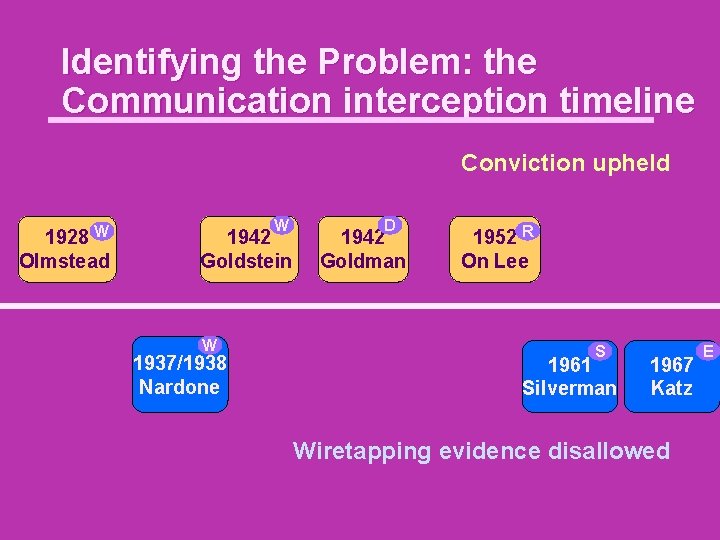
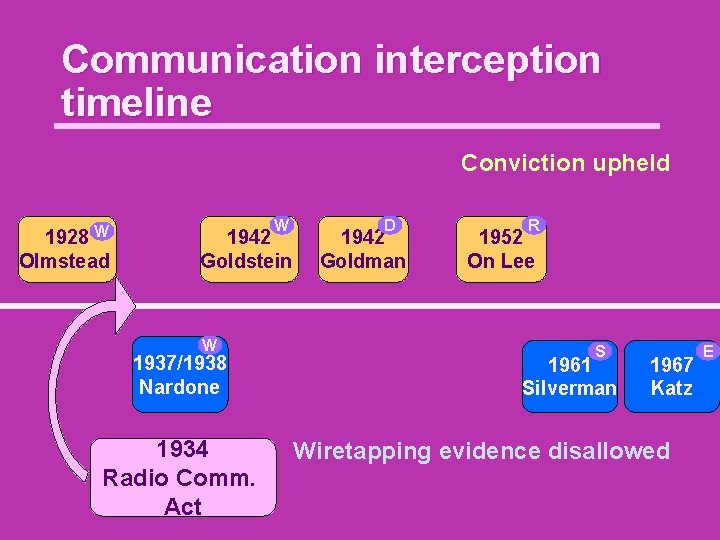
Identifying the Problem: the Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone D 1942 Goldman 1952 R On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E

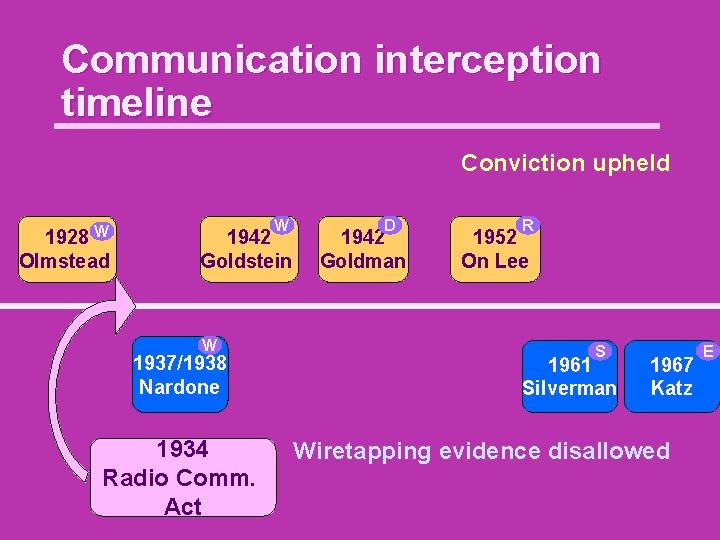
Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E

Federal Communications Act 1934 Section 605 No person not being authorized by the sender shall intercept any radio communication and divulge or publish the existence, contents, substance, purport, effect, or meaning of such intercepted communication to any person.

Nardone “…the plain words of § 605 forbid anyone, unless authorized by the sender, to intercept a telephone message, and direct in equally clear language that “no person” shall divulge or publish the message or its substance to “any person. ” To recite the contents of the message in testimony before a court is to divulge the message. The conclusion that the act forbids such testimony seems to us unshaken by the government’s arguments. ” Justice Roberts

Communication interception timeline Conviction upheld W 1928 Olmstead W 1942 Goldstein W 1937/1938 Nardone 1934 Radio Comm. Act D 1942 Goldman R 1952 On Lee S 1961 Silverman 1967 Katz Wiretapping evidence disallowed E

Olmstead v. United States (1928) The evidence in the records discloses a conspiracy of amazing magnitude…. It involved the employment of not less than fifty persons, of two seagoing vessels for the transportation of liquor to British Columbia, of smaller vessels for coastwise transportation to the State of Washington. … In a bad month sales amounted to $176, 000; the aggregate for a year must have exceeded two millions of dollars. Mr. Chief Justice Taft

Magna Carta 1215 cap. 39 Nullus liber homo capiatur vel imprisonetur, aut disseisiatur, aut utlagetur, aut exuletur, aut aliquo modo destruatur, nec super eum ibimus, nec super eum mittemus, nisi per legale judicium parium suorum vel per legem terrae. Magna Carta

Magna Carta 1215 cap. 39 Magna Carta No free man shall be seized or imprisoned, or stripped of his rights or possessions, or outlawed or exiled, or deprived of his standing in any other way, nor will we proceed with force against him, or send others to do so, except by the lawful judgment of his equals or by the law of the land.

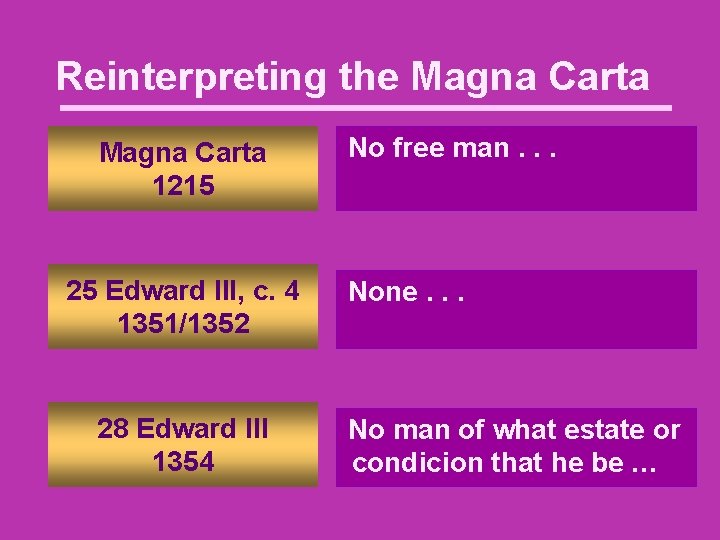
Reinterpreting the Magna Carta 1215 25 Edward III, c. 4 1351/1352 28 Edward III 1354 No free man. . . None. . . No man of what estate or condicion that he be …

Reinterpreting the Magna Carta Sir Edward Coke 1642 “…for Justices of Peace to make warrants upon surmises, for breaking the houses of any subjects to search for felons, or stoln [sic] goods, is against Magna Carta. ” Coke, Edward. 1642. The fourth part of the institutes of the laws of England. London: M. Flesher.

Reinterpreting the Magna Carta William Pitt 1763 “The poorest man may, in his cottage, bid defiance to all the forces of the Crown. It may be frail; its roof may shake; the wind may blow through it; the storm may enter; the rain may enter; but the King of England may not enter; all his force dares not cross the threshold of the ruined tenement. ”

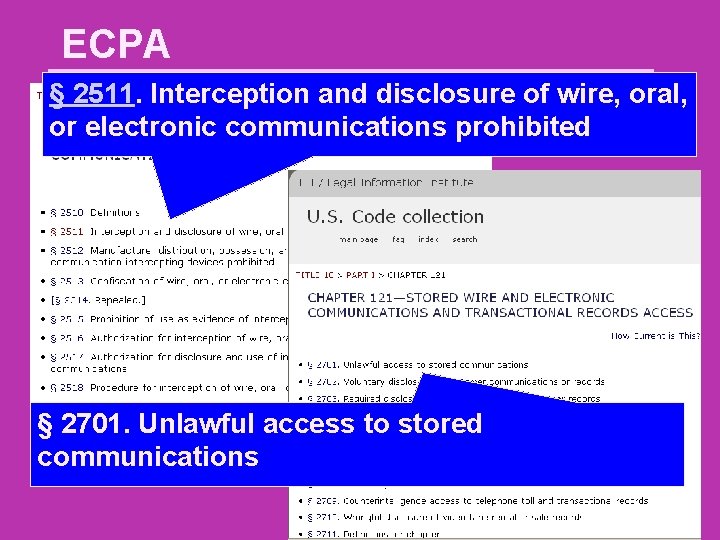
ECPA § 2511. Interception and disclosure of wire, oral, or electronic communications prohibited § 2701. Unlawful access to stored communications

ECPA § 2701. Unlawful access to stored communications (a) Offense. — Except as provided in subsection (c) of this section whoever— (1) intentionally accesses without authorization a facility through which an electronic communication service is provided; or (2) intentionally exceeds an authorization to access that facility; and thereby obtains, alters, or prevents authorized access to a wire or electronic communication while it is in electronic storage in such system shall be punished as provided in subsection (b) of this section.

ECPA (c) Exceptions. — Subsection (a) of this section does not apply with respect to conduct authorized — (1) by the person or entity providing a wire or electronic communications service; (2) by a user of that service with respect to a communication of or intended for that user; or (3) in section 2703, 2704 or 2518 of this title.