Privacy Enhancing Technologies PET Dr Nicholas Shaw IEEE










- Slides: 15

Privacy Enhancing Technologies (PET) Dr. Nicholas Shaw IEEE Senior Member EDS, an HP Company

Overview of Privacy-enhancing technologies (PET) are tools formed to protect the service user, rather than the service itself. PET are the means to protect the privacy of individuals. Internet/Web (social networking/e-commerce) Mobile-based (cell phones/GPS/m-commerce) Non-compute-based (Real. ID) Before discussing PET, one must have a fundamental understanding of Privacy

Overview of Privacy One definition of Privacy is the right of entities to determine by themselves when, how, and to what extent information about them (personally identifiable information or PII) is communicated to others Travelocity (airlines, hotels, rental cars, and partners of each) Information about you is valuable Companies exist to sell information about you! Behavioral Targeting/User Profiling (Google mail) Data Mining Sometimes more information protects privacy Companies walk a thin line between competitive edge and losing customers due to trust issues Employment (Facebook, My. Space, “Boseman, MT”) Insurance (example: LBS) Crime (example: LBS)

Overview of Privacy Policies Natural Language Long In Legalese Not often read Electronic Privacy Policy Lanaguage P 3 P <50% of e-commerce sites have electronic versions Don’t often match the natural language versions

Overview of Privacy How one views privacy is in the eyes of the individual: Age (generational) Grown up with computers Didn’t grow up with computers Occupation Uses computers daily in work versus those who don’t Involved in marketing versus those who aren’t Experience (those who have been burned versus those who haven’t) Location High tech area versus low tech Availability of stores (urban) versus low availability (rural)

Types of Data Breaches Internal Intentional (unhappy employees, criminal) Unintentional Accidental (system admins working on systems without enough sleep) Stupid (employees leaving laptops in car, in plain view) External (hackers trying to break into systems) Of all breaches, the most prevalent and dangerous are internal.

Types of Attacks Internet (Web) and Mobile (Location-Based Services – LBS) Behavioral Targeting (user profiling) Misuse of personal information Use for other than stated in privacy policy Sale for profit Criminal Other (use by companies in hiring/firing such as use of Facebook/Myspace data or to change rates or cancel insurance policies) E-/M-commerce (M-commerce is mobile-based commerce) Need for profit drives collection/use of personal information User Trust Need to balance the advantages of using PII with

Behavioral Targeting Example Prepare two Google gmails to yourself (without a subject): I like bananas I need an airplane, hotel, and car reservation Now, when you get the e-mails back, open them and look at the top bar and side. What you’ll see is information (using airplane, hotel, car) are advertisements from rental companies, hotels, etc. For bananas I received ads on yogurt, fruit, etc. The ads constantly change everytime you open the e-mail up. This is behavioral targeting but the interesting aspect is that your e-mail is being read by Google (automated bots).

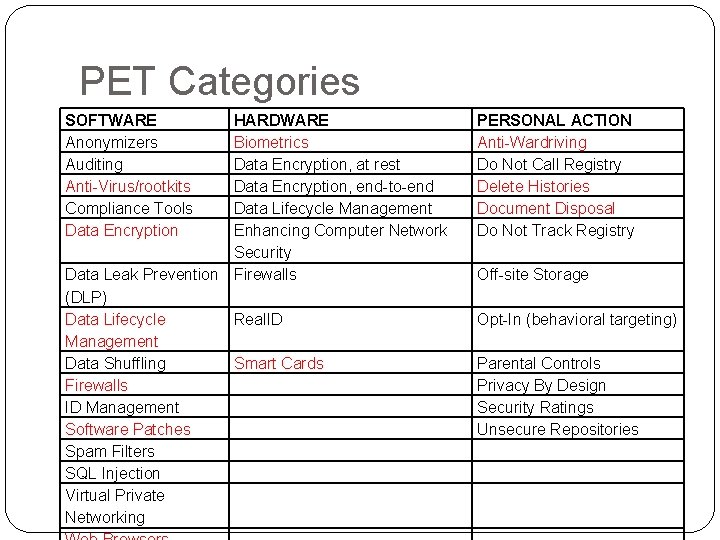
PET Categories SOFTWARE Anonymizers Auditing Anti-Virus/rootkits Compliance Tools Data Encryption HARDWARE Biometrics Data Encryption, at rest Data Encryption, end-to-end Data Lifecycle Management Enhancing Computer Network Security Data Leak Prevention Firewalls (DLP) Data Lifecycle Real. ID Management Data Shuffling Smart Cards Firewalls ID Management Software Patches Spam Filters SQL Injection Virtual Private Networking PERSONAL ACTION Anti-Wardriving Do Not Call Registry Delete Histories Document Disposal Do Not Track Registry Off-site Storage Opt-In (behavioral targeting) Parental Controls Privacy By Design Security Ratings Unsecure Repositories

Software PET Most users implement some level of PET on their systems such as encryption, anti-virus (AV) software, anonymous web browsers such as Google Chrome or Internet Explorer (IE) 8 Newer technologies such as Data Leak Prevention (DLP), also called Information Leak Prevention (ILP) deploy capabilities such as data in motion, in use, and at rest Data/Information Lifecycle Management, while understood, is still relatively new Often implemented for production servers Rarely implemented by users Questionable when it comes to PII

Hardware PET Typical hardware PET include firewalls and routers Biometric scanners (finger print) are becoming more common on laptop devices with the scanners built right in at the factory Smart cards, such as the CAC (Common Authentication Card) used by the military, are also becoming more common Whereas most encryption today is softwarebased, hardware-based encryption is gaining and prices are dropping. The advantages of hardware encryption include automatic encryption/decryption of data and no impact to performance

User Actions PET All of these PET require actions from the user such as Opt-in/Opt-out, signing up such as for Do Not Call/Track, etc. Anti-wardriving (the practice of driving around with a Wi. Fi finder) Deletion of histories is required unless the user is using a software solution such as IE 8 or Google Chrome which do not save histories or cookies when in stealth mode Off-site storage is a staple of production systems and is now being offered by the major vendors across the Internet Document disposal is actually part of DLM (see software PET) – in short, users get rid of files they don’t need

References Machanavajjhala, A. , Kifer, D. , Gehrke, J. , & Venkitasubramaniam, M. (2007). L-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data, 1(1), 3. Mont, M. C. , & Beato, F. (2007). On Parametric Obligation Policies: Enabling Privacy-Aware ILM in Enterprises. Eighth IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY'07), 51 -55. Govil, J. , Kaur, N. , Kaur, H. , & Govil, J. (2008). Data/Information Lifecycle Management: A Solution for Taming Data Beast. Fifth International Conference on Information Technology: New Generations, 1226 -1227. Bulbul, H. I. , Batmaz, I. , & Ozel, M. (2008). Wireless network security: comparison of WEP (Wired Equivalent Privacy) mechanism, WPA (Wi-Fi Protected Access) and RSN (Robust Security Network) security protocols. 1 st international conference on Forensic applications and techniques in telecommunications, information, and multimedia and workshop, Adelaide, Australia. Kang, Y. , Lee, H. , Chun, K. , Song, J. (2007). Classification of Privacy Enhancing Technologies in Life-cycle of Information. International Conference on Emerging Security Information, Systems, and Technologies (SECUREWARE '07), 66 -70. Salas, P. P. , & Krishnan, P. (2008). Testing Privacy Policies using Models. Sixth IEEE International Conference on Software Engineering and Formal Methods, 117 -126. Ofuonye, E. , Beatty, P. , Reay, I. , Dick, S. , & Miller, J. (2008). How Do We Build Trust into Ecommerce Web Sites? IEEE Software, 25(5), 7 -9. Boritz, J. E. , No, W. G. , & Sundarraj, R. P. (2008). Internet Privacy in E-Commerce: Framework, Review, and Opportunities for Future Research. 41 st Hawaii International Conference on System Sciences, 204 -214. Gupta, S. , Jain, S. , Kazi, M. , Deshpande, B. , Bedekar, M. , & Kapoor, K. (2008). Personalization of Web Search Results Based on User Profiling. First International

References Smith, R. , & Shao, J. (2007). Privacy and E-commerce: A Consumer-centric Perspective. Electronic Commerce Research, 7(2), 89 -116. Hecker, M. , Dillon, T. , & Change, E. (2008). Privacy Ontology Support for E-Commerce. IEEE Internet Computing, 54 -61. Jing, R. , Yu, J. , Jiang, Z. (2008). Exploring Influencing Factors in E-Commerce Transaction Behaviors. 2008 International Symposium on Electronic Commerce and Security. 603 -607. Robbins, J. , & Sabo, J. (2006). Managing Information Privacy: Developing a Context for Security and Privacy Standards Convergence. IEEE Security & Privacy, 4(4), 92 -95. Reay, Ian, Dick, Scott, & Miller, James (2009). A large-scale empirical study of P 3 P privacy policies: Stated actions vs. legal obligations. ACM Transactions on the Web (TWEB), 3(2), 134. Duma, Claudiu, Herzog, Almut, & Shahmehri, Nahid (2007). Privacy in the Semantic Web: What Policy Languages Have to Offer. Paper presented at the 8 th IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY '07). Hansen, Marit, Schwartz, Ari, & Cooper, Alissa (2008). Privacy and Identity Management. IEEE Security & Privacy, 6(2), 38 -45. Decker, Michael (2008). Location Privacy-An Overview. Paper presented at the 7 th International Conference on Mobile Business, 221 -230. Xu, Toby, & Cai, Ying (2007). Location Anonymity in Continuous Location-Based Services. Paper presented at the 15 th International Symposium on Advances in Geographic Information Systems (GIS '07), Seattle, WA.

References Beatty, Patricia, Reay, Ian, Dick, Scott, & Miller, James (2007). P 3 P Adoption on E- Commerce Web Sites: A Survey and Analysis. [Feature]. IEEE Internet Computing, 11(2), 65 -71. Kojima, Takao, & Itakura, Jukio (2008, October 31, 2008). Proposal of Privacy Policy Matching Engine. Paper presented at the 4 th ACM Workshop on Digital Identity Management (DIM '08), Fairfax, VA. Yan, J. , Liu, N. , Wang, G. , Zhang, W. , Jiang, Y. , & Chen, Z. (2009). How Much Can Behavioral targeting Help Online Advertising? Proceedings of the 18 th International Conference on WWW, 261 -270. Yaveroglu, I. , & Donthu, N. (2008). Advertising Repetition and Placement Issues in On-Line Environments. Journal of Advertising, 37(2), 31 -43.