Privacy Confidentiality and Security M 8120 Fall 2001




















- Slides: 30

Privacy, Confidentiality, and Security M 8120 Fall 2001

Scope and Standards of Informatics Practice l The informatics nurse develops policies, procedures, and guidelines based on research and analytical findings, which may include: – – – l Ensuring the validity and integrity of data Ensuring the ethical use of informatics solution Ensuring the confidentiality and security of data and privacy for individuals Ensures that the informatics solution is in compliance with recognized standards from accrediting and regulatory agencies

Informatics Competencies l Beginning nurse – – l Seeks available resources to help formulate ethical decisions in computing Describes patients’ rights as they pertain to computerized information management Experienced nurse – – Interprets copyright issues in computing Discusses features, capabilities and scope of user passwords Devises strategies to protect confidentiality of computerized information Differentiates issues surrounding confidentiality in computerized information management Staggers, Gassert, & Curran, 2001

Informatics Competencies l Informatics specialist knowledge – – l Interprets copyright issues in computing Discusses features, capabilities and scope of user passwords Devises strategies to protect confidentiality of computerized information Differentiates issues surrounding confidentiality in computerized information management Informatics specialist skills – – – Develops policies related to privacy, confidentiality, and security of patient and client data Recommends procedures for achieving data integrity and security Analyzes the capability of information technology to support programs of data integrity and security Staggers, Gassert, & Curran, 2001

Definitions l Privacy - the right of individuals to be left alone and to be protected against physical or psychological invasion or the misuse of their property. It includes freedom from intrusion or invasion into one’s private affairs, the right to maintain control over certain personal information, and the freedom to act without outside interference. (ASTM E-31, 1997)

A Balance l l Privacy rights Access needs – – – Treatment Public health National security

Definitions l Confidentiality – the status accorded to data or information indicating that it is sensitive for some reason and therefore it needs to be protected against theft, disclosure or improper use, or both, and must be disseminated only to authorized individuals or organizations with a need to know. (ASTM E-31, 1997)

What are some examples of confidential data?

Breaches of Confidentiality l l l Accidental disclosures – inadvertent actions, unintensional mistakes Insider curiosity – insider’s accessing celebrities’ or friends’ information Insider subordination – insider revenge Uncontrolled secondary usage – for purposes other than intended without patient authorization Unauthorized access – hacking or use of another’s password

Definitions l Security – the means to control access and protect information from accidental or intentional disclosure to unauthorized persons and from alteration, destruction or loss (CPRI)

Definitions l Data security – the result of effective protection measures; the sum of measures that safeguard data and computer programs from undesired occurrences and exposure to: – – accidental or intentional disclosure to unauthorized persons accidental or malicious alteration, unauthorized copying, loss by theft or destruction by hardware failures, software deficiencies, operating mistakes, or physical damage by fire, water, smoke, excessive temperature, electrical failure, or sabotage or combination thereof. ASTM-E 31, 1997

Definitions l System security – the result of all safeguards including hardware, personnel policies, information practice policies, disaster preparedness, and oversight of these components. Security protects both the system and the information contained within from authorized access from without and misuse from within. ASTM E-31, 1997

Health Insurance Portability and Accountability Act of 1996 (HIPAA) l l AKA – Administrative Simplification, Kennedy. Kasselbaum, K-2 Purposes – – Improved efficiency in healthcare delivery by standardizing electronic data exchange Protection of confidentiality and security of health data through setting and enforcing standards

Health Insurance Portability and Accountability Act of 1996 (HIPAA) l Includes: – – – Standardization of electronic patient health, administrative, and financial data Unique health identifiers for individuals, employers, health plans, and health care providers Security standards protecting the confidentiality and integrity of “individually identifiable health information”, past, present, or future

Health Insurance Portability and Accountability Act of 1996 (HIPAA) l l Electronic health transactions standards Unique identifiers Security and electronic signature standards Privacy and confidentiality standards

Definitions l Individually identifiable health information – information that is a subset of health information, including demographic information collected from an individual, and that: – – Is created by or received from a health care provider, health plan, employer, or health care clearing house Relates to the past, present, or future physical or d health or condition of an individual, the provision of health care to an individual, or the past, present, or future payment for the provision of health care to an individual, and which identifies the individual or with respect to which there is a reasonable basis to believe that the information can be used to identify the individual

Definitions l Protected health information – individually identifiable health information that is: – – – Transmitted by electronic media Maintained in electronic media Transmitted or maintained in any other form or medium

Definitions l De-identified information – information that is not individually identifiable

HIPAA Privacy and Confidentiality Standards l l l Limit the non-consensual use and release of personal health information Give patients new rights to access their medical records and to know who else has accessed them Restrict most disclosure of health information to the minimum needed for the intended purpose Establish new criminal and civil sanctions for improper use or disclosure Establish new requirements for access to records by researchers and others

HIPAA Privacy and Confidentiality Standards: 5 Principles l l l Consumer control – the regulation provides consumers with critical new rights to control their medical information Boundaries – with few exceptions, an individual’s health care information should be used for health purposes only, including treatment and payment Accountability – specific penalties if right to privacy is violated Public responsibility – balance privacy with national priorities such as public health protection, medical research, improving quality of care, and fight health care fraud and abuse Security – organizational responsibility

HIPAA Security Standards l l Information systems security requiring the protection of all affected computers and data from compromise or loss Physical security requiring the protection of all buildings, facilities, and assets from compromise or threat Audit trails of access to patient-identifiable information Digital signature/data encryption requiring transmissions to be authenticated and protected from observation or change

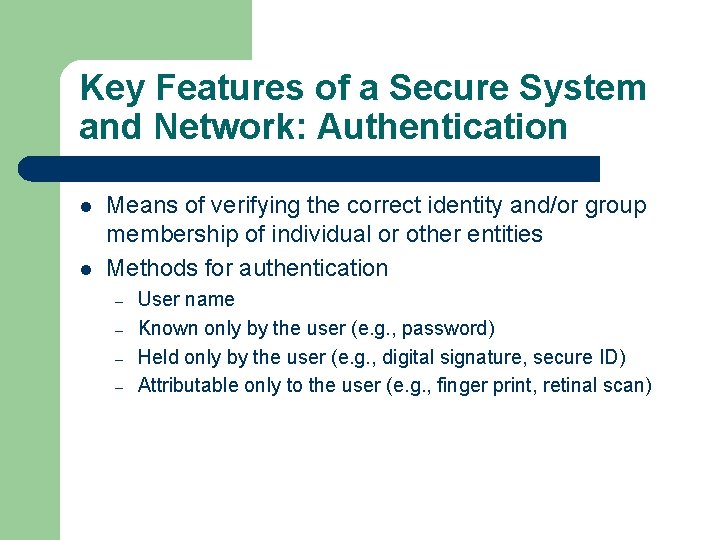
Key Features of a Secure System and Network l l l l Authentication Authorization and access control Data integrity Accountability Availability Data storage Data transmission

Key Features of a Secure System and Network: Authentication l l Means of verifying the correct identity and/or group membership of individual or other entities Methods for authentication – – User name Known only by the user (e. g. , password) Held only by the user (e. g. , digital signature, secure ID) Attributable only to the user (e. g. , finger print, retinal scan)

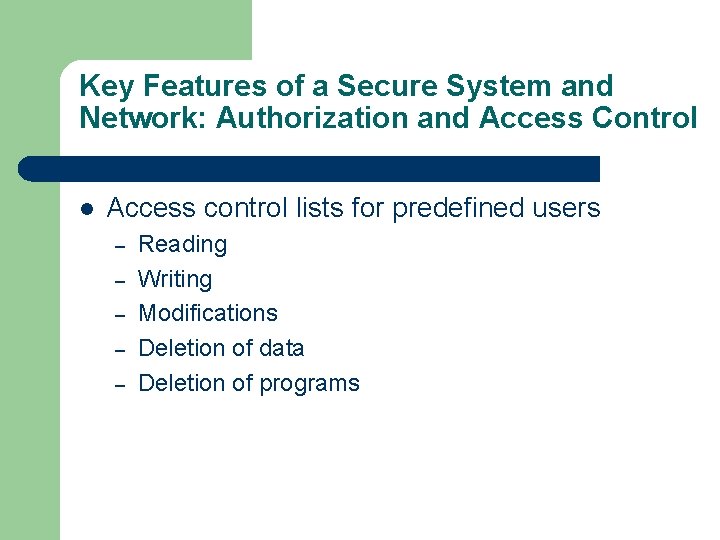
Key Features of a Secure System and Network: Authorization and Access Control l Access control lists for predefined users – – – Reading Writing Modifications Deletion of data Deletion of programs

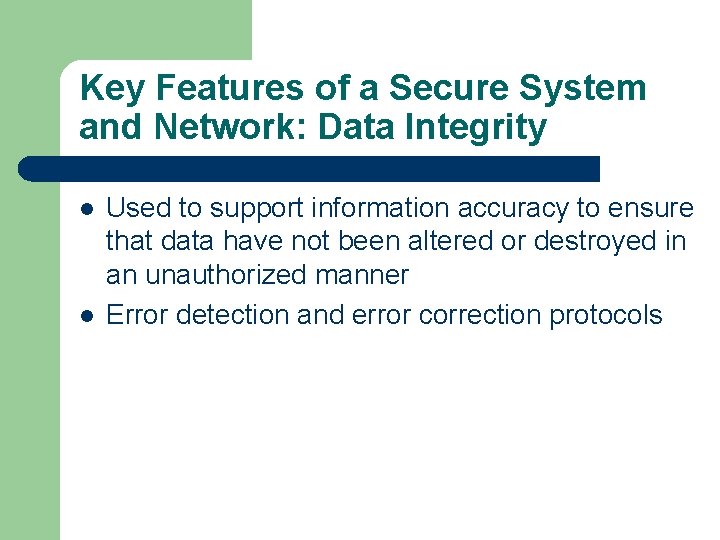
Key Features of a Secure System and Network: Data Integrity l l Used to support information accuracy to ensure that data have not been altered or destroyed in an unauthorized manner Error detection and error correction protocols

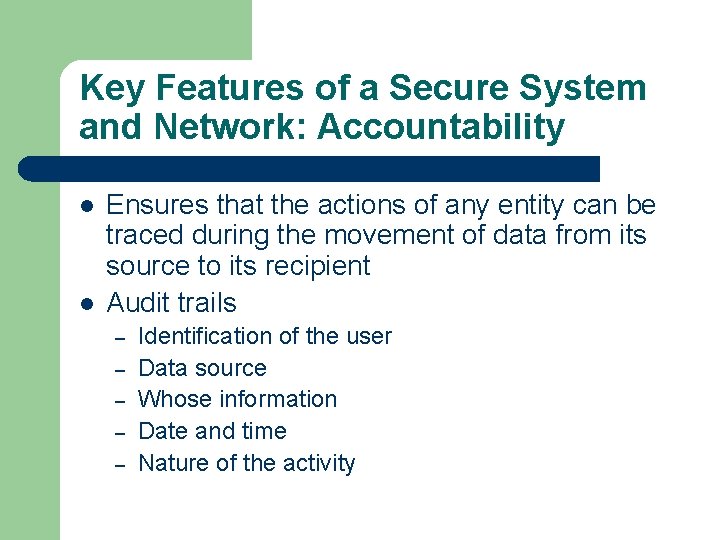
Key Features of a Secure System and Network: Accountability l l Ensures that the actions of any entity can be traced during the movement of data from its source to its recipient Audit trails – – – Identification of the user Data source Whose information Date and time Nature of the activity

Key Features of a Secure System and Network: Availability l l Ensures information is immediately accessible and usable by authorized entity Methods – – – Back ups Protecting and restricting access Protecting against viruses

Key Features of a Secure System and Network: Data Storage l l l Protecting and maintaining the physical location of the data and the data itself Physical protection of processors, storage media, cables, terminals, and workstations Retention of data for mandated period of time

Key Features of a Secure System and Network: Data Transmission l l Exchange of data between person and program or program and program when the sender and receiver are remote from one another Encryption – – l Scrambles readable information De-encrypt with proper key by recipient Firewall – Filtering mechanism so that only authorized traffic is allowed to pass

Unique Identifiers l l l Employer Identifier Number (EIN) National Provider Identifier (NPI) – individual, group, or organization that provides medical or other health care services or supplies Unique health identifier – on hold