Privacy and Security in Library RFID Issues Practices

Privacy and Security in Library RFID Issues, Practices, and Architectures David Molnar, David Wagner - Authors Eric Mc. Cambridge - Presenter

What is RFID? RFID = Radio Frequency Identification � Microchips with antennae affixed to objects � Powered by radio waves emitted by reader � Communicates ID number to reader (and possibly other information)

RFID in the Wild �Corporate Supply Chain • Originally designed for fast inventory checking • Quickly identify all of the items in a certain bin �Enhanced Drivers License and Passports • Recent research from UW �K. Koscher, A. Juels, T. Kohno, and V. Brajkovic • www. komonews. com/news/local/33205899. html • www. rsa. com/rsalabs/node. asp? id=3557

RFID in Libraries �RFID tags on individual books (and other items) �Readers (exit sensors) placed at exit

Privacy Questions �Hotlisting: Who is reading this book? �Tracking: What is this person reading? �What people are reading the same books as this known terrorist? Security Questions Can we prevent people from checking out this book?
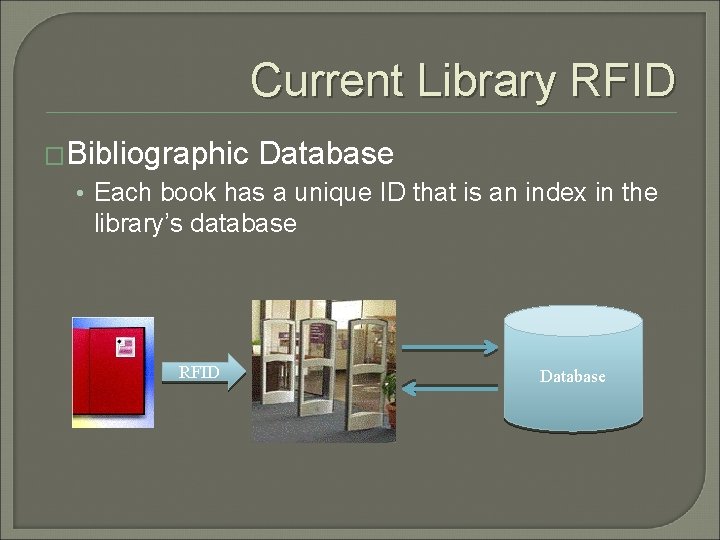
Current Library RFID �Bibliographic Database • Each book has a unique ID that is an index in the library’s database RFID Database

Current Library RFID �Status stored on tag • “Security Bit” = Is this book checked out? • Set on each check-in/check-out I’m checked out! You’re checked out! RFID Then… RFID

Concerns �Bibliographic Database • Fast enough? �Status on tag • Denial of service (write-lock) • Easy to fake (not addressed) �Both - Privacy • Can identify individual books by their RFID number

Privacy Concerns �Can easily identify books by the data on their RFID tag • Bibliographic DB can hide book’s title, but can identify individual copies • Even hiding RFID number, unique collision ID is easy to get with off-the-shelf readers

Solution? �Randomized Transaction IDs • Book has randomized, separate ID when it is checked out �Password Encryption via One-Time Pad • Channel from tag to reader much harder to eavesdrop than reader to tag so… • Pad is sent (in cleartext) to exit sensor by tag �Private Authentication • Rest of this paper

Tree-Based Scheme �Tags are leaves in a balanced binary search tree �Edges of tree are shared secrets • Generated uniformly at random �Traverse tree by finding which secret tag knows �O(log n) storage on tag �O(log n) work for reader

Two-Phased Tree �Previous solution is O(k * log n) work where k is branching factor �Want O(k + log n) work: �How does this work? • Identify the tag in the first phase: determine which branch to take • Follow that branch

Open Questions & Areas for Improvement �Demonstrations of attacks • Not as important – clear that these attacks are possible in the architectures they describe �Implementation of protocol • Will this fit on a small, low-power RFID tag? • Can the protocol be executed quickly enough that it works as people walk by exit sensors?
- Slides: 13