Privacy And Authentication for Wireless Local Area Networks




- Slides: 12

Privacy And Authentication for Wireless Local Area Networks Ashar Aziz Whitfield Diffie Sun Microsystems, Inc Presented by: Naveen Srinivasan. Privacy and Authentication for Wireless LAN 1

OUTLINE • Loopholes in wireless • Design Goals • Design Overview • Message Exchange in Protocol • Other Issues Privacy and Authentication for Wireless LAN 2

• Loopholes in Wireless medium – Wireless receivers – No physical constraints • Design Goals – Privacy of wireless data communication and authenticity of the communicating parties – Seamless integration into existing wired network – Mutual authentication – To take advantage of shared key cryptography Privacy and Authentication for Wireless LAN 3

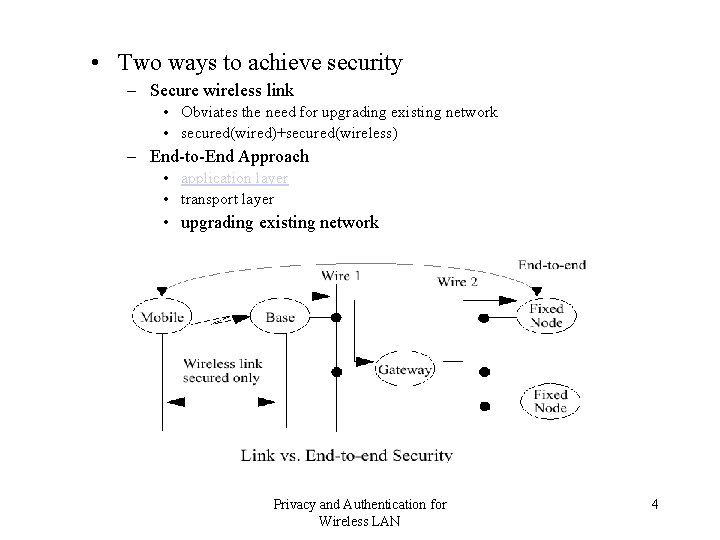
• Two ways to achieve security – Secure wireless link • Obviates the need for upgrading existing network • secured(wired)+secured(wireless) – End-to-End Approach • application layer • transport layer • upgrading existing network Privacy and Authentication for Wireless LAN 4

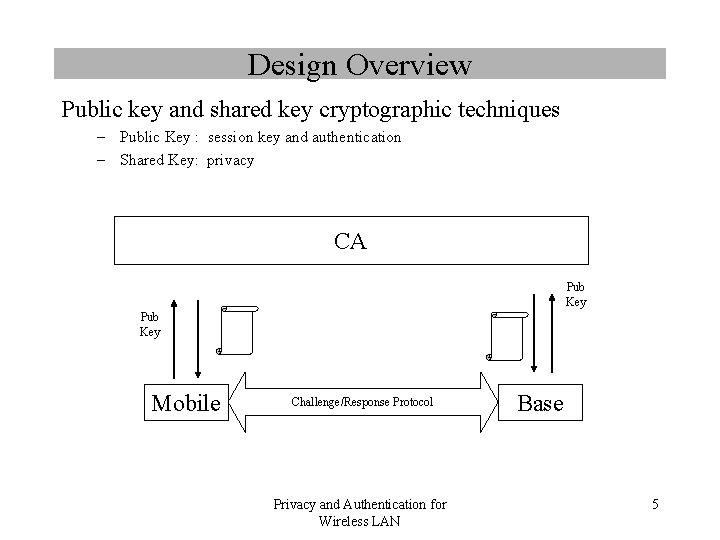
Design Overview Public key and shared key cryptographic techniques – Public Key : session key and authentication – Shared Key: privacy CA Pub Key Mobile Challenge/Response Protocol Privacy and Authentication for Wireless LAN Base 5

Content of the Certificate CA Contents: • Serial Number • Validity Period • Machine Name • Machine Public Key • CA Name Privacy and Authentication for Wireless LAN 6

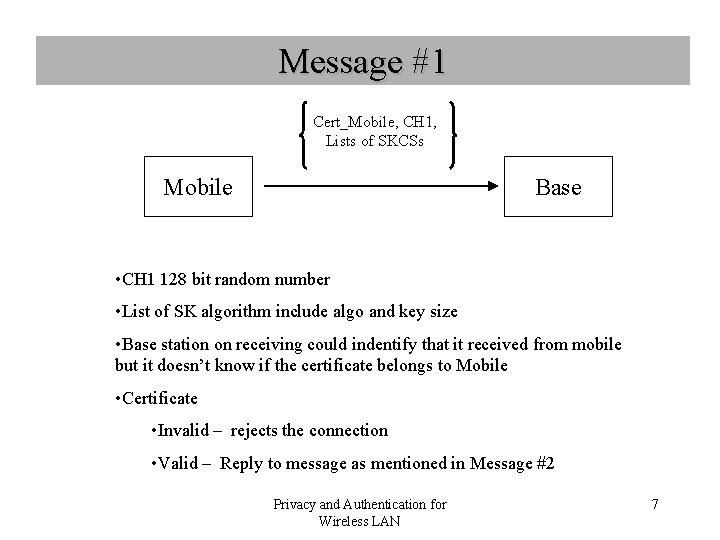
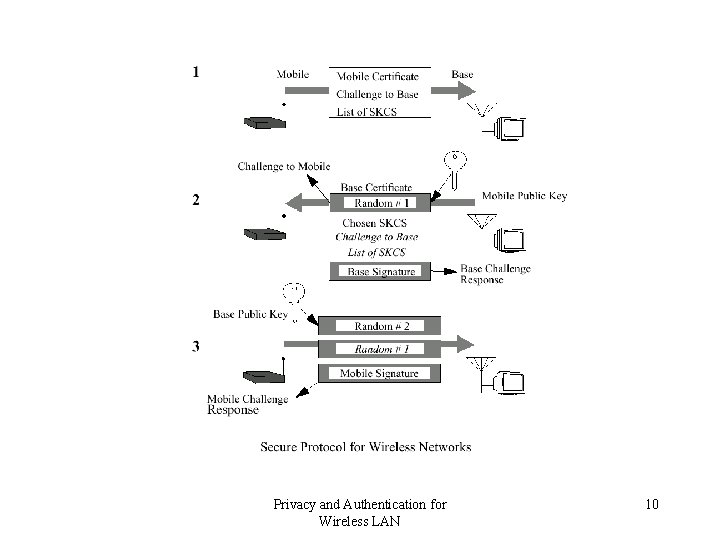
Message #1 Cert_Mobile, CH 1, Lists of SKCSs Mobile Base • CH 1 128 bit random number • List of SK algorithm include algo and key size • Base station on receiving could indentify that it received from mobile but it doesn’t know if the certificate belongs to Mobile • Certificate • Invalid – rejects the connection • Valid – Reply to message as mentioned in Message #2 Privacy and Authentication for Wireless LAN 7

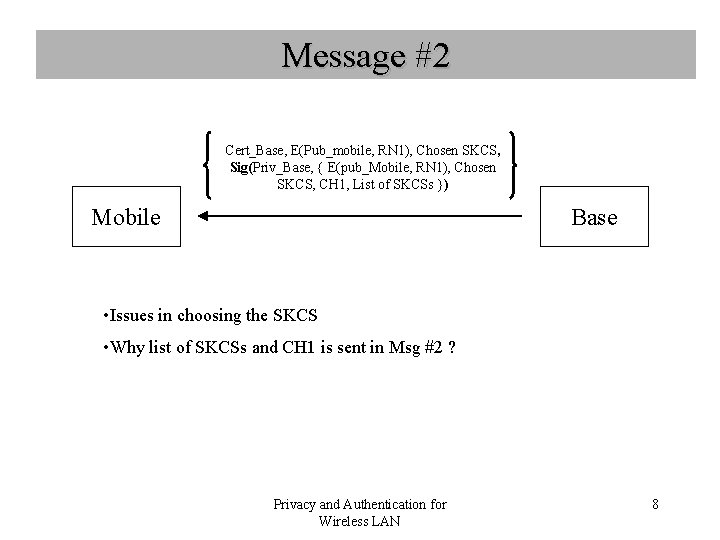
Message #2 Cert_Base, E(Pub_mobile, RN 1), Chosen SKCS, Sig(Priv_Base, { E(pub_Mobile, RN 1), Chosen SKCS, CH 1, List of SKCSs }) Mobile Base • Issues in choosing the SKCS • Why list of SKCSs and CH 1 is sent in Msg #2 ? Privacy and Authentication for Wireless LAN 8

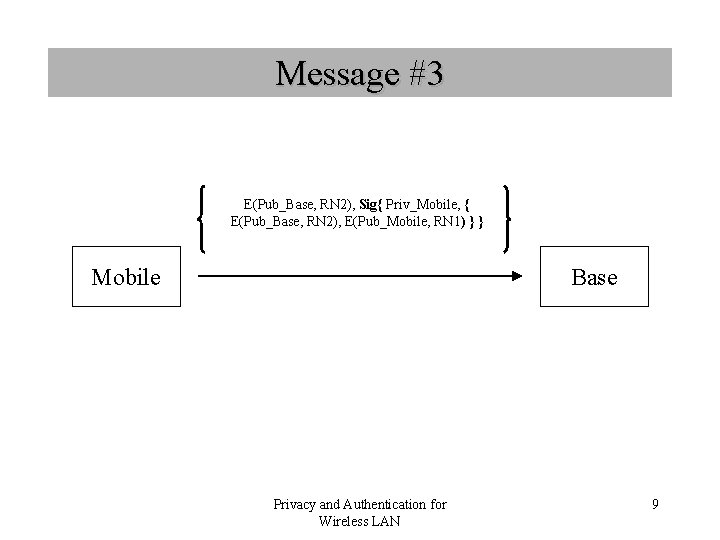
Message #3 E(Pub_Base, RN 2), Sig{ Priv_Mobile, { E(Pub_Base, RN 2), E(Pub_Mobile, RN 1) } } Mobile Base Privacy and Authentication for Wireless LAN 9

Privacy and Authentication for Wireless LAN 10

Data Packet Issues Problems: • Packet losses • Playback attack Solutions: • Message ID • Count of no. of 64 -bits blocks that have been sent • Last 64 -bits of the cipher-text of the last packet • Assumes taken care by higher layer protocol Privacy and Authentication for Wireless LAN 11

Operation with Multiple CAs Previous protocol description single network wide CA – not feasible Hierarchy of CA s is employed Base Station • Not only include the certificate but also the certificate path Mobile • Just its own certificate Privacy and Authentication for Wireless LAN 12