Presentation Title Pg 1 Introduction to the PIMS












- Slides: 21

Presentation Title Pg 1 | Introduction to the PIMS Certification Scheme in Korea Presenter Heung Youl YOUM, Ph. D. /Professor, TTA/Soonchunhyang University Session Strategic Topic #3: Security & Privacy Document Name/Version GSC 20_Session#8_Security_Heung. Youl_TTA Rev 0 Submission/Revision date: 20 April 2016 1

Recent major data leakage incidents in Korea Pg 2 |

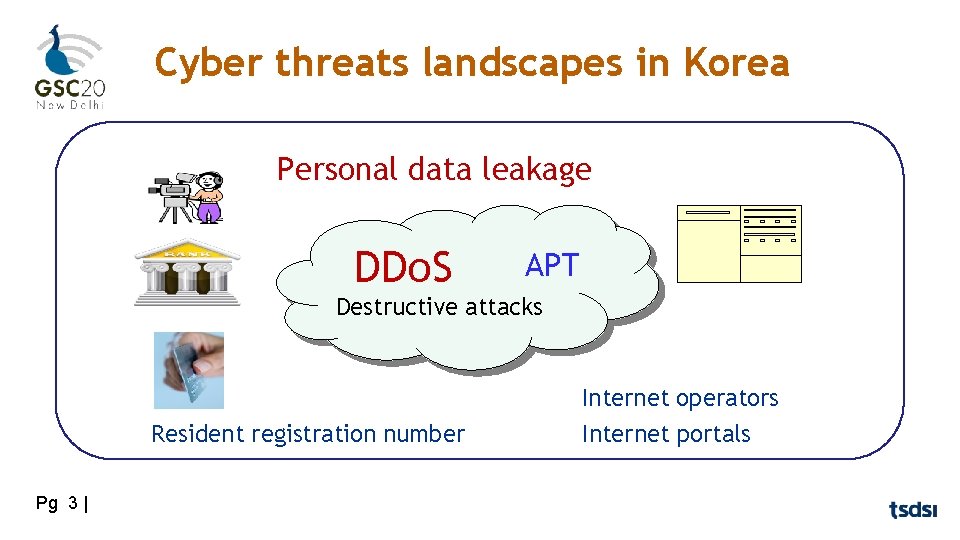
Cyber threats landscapes in Korea Personal data leakage DDo. S APT Destructive attacks Resident registration number Pg 3 | Internet operators Internet portals

Recent major PII leakage incidents (1/3) q April 17, 2011, Personal Information leakage incident against the KR’s financial institute. § Personal information leakage of 420, 000 customers, including their name, email, and cell phone information, was caused by a hacking. § First unprecedented systematic accessing of customer financial information by hackers in Korea. q July 26, 2011, Major portal’s personal information leakage. § Personal information of its 35 million online users had been hacked. § A leakage of customers’ information took place due to hacking on July 26, 2011 Pg 4 | § Personal information of users’ name, phone numbers, email, resident registration numbers and passwords was leaked.

Recent major PII leakage incidents (2/3) q November 26, 2011, Personal information leakage against the online game site. § The personal data of 13. 2 million subscribers was leaked from the online game site. § The password and the resident registration number are encrypted § Presumably, originated from a malicious code in China. q Pg 5 | January 19, 2014, major credit card data leakage incidents. § Disclosed by the Korea Prosecutors’ Office on January 19, 2014 § Victims: three local credit card companies, the K* Card, the L* Card and the N* Card § Who stole personal data: An employee of the subcontractor, suppliers of credit companies, who had been dispatched to upgrade the fraud detection systems of three credit card companies. § Volume of personal data leaked : 104 million pieces of cardholders’ personal and financial information.

Recent major PII leakage incidents (3/3) q March 6, 2014, Personal data leakage against the Internet service operator’s website. § Personal data of 9. 81 million customers leaked between last August 2013 and February 2014 in a hack on its website: the vulnerabilities of the operator’s web site were exploited to steal the personal data of customers. § Three suspects, including a telemarketer, were arrested for allegedly hacking into the company’s website and stealing the personal data of 9. 81 million clients of the mobile carrier. § The leaked personal data included names, resident registration numbers, places of employment, and bank account details. § fined with 85 million won ($83, 650) by the Korea Communications Commission (KCC) for personal data being leaked. Pg 6 |

ISMS/PIMS certification systems Pg 7 |

Overview of ISMS/PIMS certification q There are two types of management systems in Korea: ISMS and PIMS. q ISMS certification was put into force in 2001, while PIMS was put into force in 2011. q Legal grounds: § The ISMS and/PIMS are based on Article 47 (Certification of information security management system) in ‘Act on the Promotion of Information and Communication Network Utilization and Information Protection, etc. § Mandatory ISMS certification requirements for sizable enterprises, was enforced since 2013. q Local standards and criteria compatible with ISO/IEC 27001 § The ordinance of MSIP for ISMS certification and KCS for PIMS certification that aim to help organizations improve the safety and reliability of their information networks. § KCS. KO-12. 0001, Personal information management system Pg 8 |

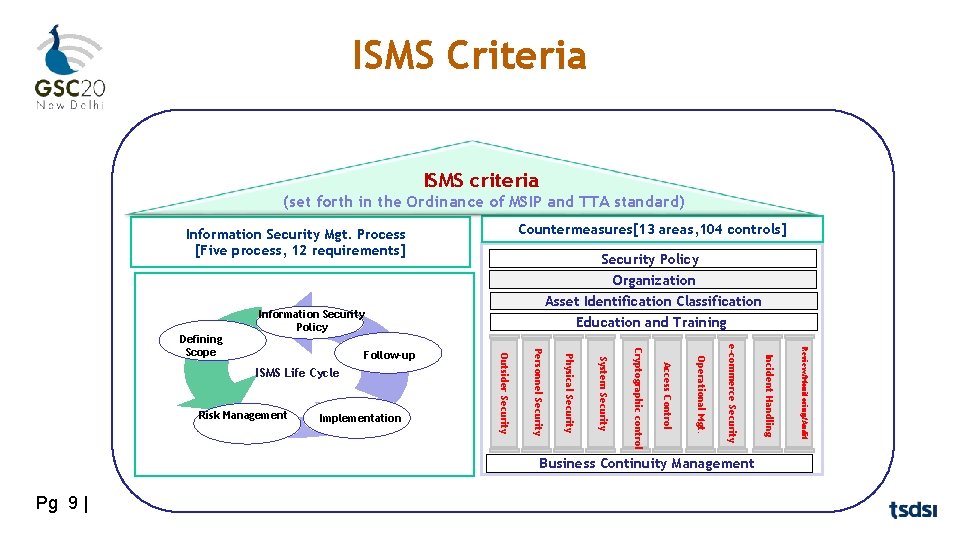
ISMS Criteria ISMS criteria (set forth in the Ordinance of MSIP and TTA standard) Countermeasures[13 areas, 104 controls] Information Security Mgt. Process [Five process, 12 requirements] Security Policy Organization Pg 9 | Review/Monitoring/Audit Business Continuity Management Incident Handling e-commerce Security Operational Mgt. Access Control Cryptographic control Implementation System Security Risk Management Physical Security ISMS Life Cycle Personnel Security Follow-up Education and Training Outsider Security Defining Scope Asset Identification Classification Information Security Policy

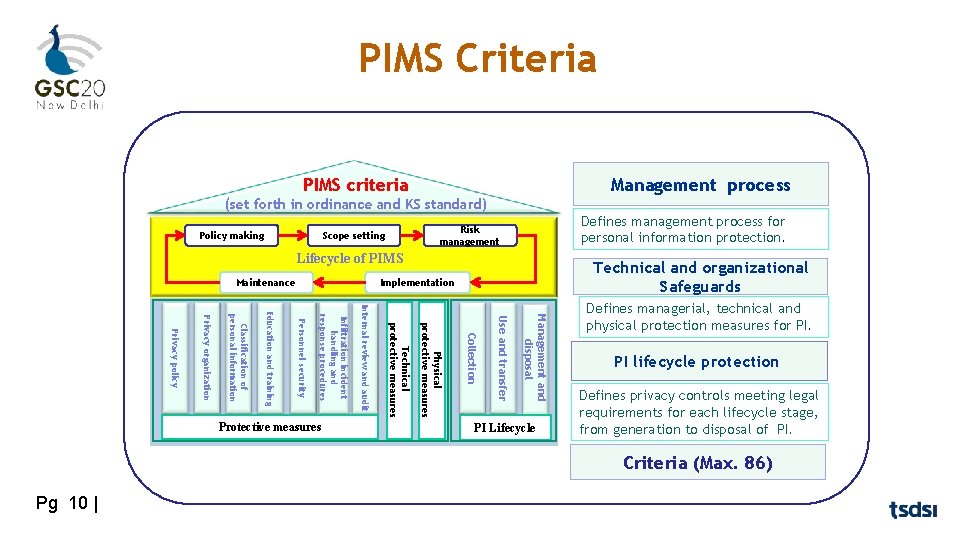
PIMS Criteria Management process PIMS criteria (set forth in ordinance and KS standard) Policy making Defines management process for personal information protection. Risk management Scope setting Lifecycle of PIMS Maintenance Technical and organizational Safeguards Implementation Management and disposal Use and transfer Collection Physical protective measures Technical protective measures Internal review and audit Infiltration incident handling and response procedures Personnel security Education and training Classification of personal information Privacy organization Privacy policy Protective measures PI Lifecycle Defines managerial, technical and physical protection measures for PI. PI lifecycle protection Defines privacy controls meeting legal requirements for each lifecycle stage, from generation to disposal of PI. Criteria (Max. 86) Pg 10 |

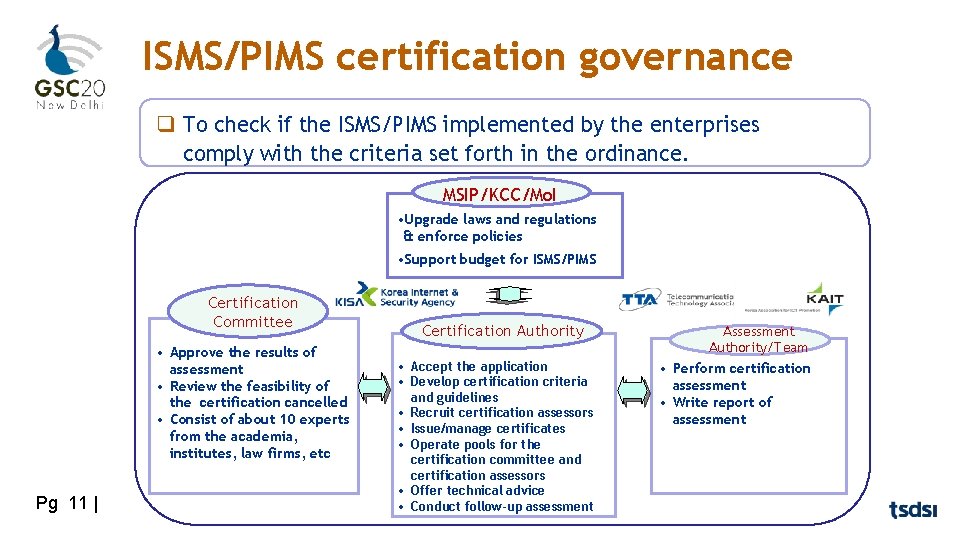
ISMS/PIMS certification governance q To check if the ISMS/PIMS implemented by the enterprises comply with the criteria set forth in the ordinance. MSIP/KCC/Mo. I • Upgrade laws and regulations & enforce policies • Support budget for ISMS/PIMS Certification Committee • Approve the results of assessment • Review the feasibility of the certification cancelled • Consist of about 10 experts from the academia, institutes, law firms, etc Pg 11 | Certification Authority • Accept the application • Develop certification criteria and guidelines • Recruit certification assessors • Issue/manage certificates • Operate pools for the certification committee and certification assessors • Offer technical advice • Conduct follow-up assessment Authority/Team • Perform certification assessment • Write report of assessment

Certified organizations q As of April 2016, • 410 organizations have obtained ISMS certification from KISA. § 1(2002), 2(‘ 03), 1 (‘ 04), 3(‘ 05), 0(‘ 06), 5(‘ 07), 8(’ 08), 8(‘ 09), 8(’ 10), 5(‘ 11), 11(‘ 12), 118(‘ 13), 174(‘ 14), 52(‘ 15), 14(‘ 16) • 60 organizations have got PIMS certification. § 2(‘ 11), 7(’ 12), 11(‘ 13), 7(‘ 14), 14(‘ 15), 19(‘ 16) q The number of certified organizations for ISMS/PIMS is expected to increase in 2016. Pg 12 | http: //isms. kisa. or. kr/kor/issue 01. jsp? cert. Type=ISMS

Ready for the global PIMS certification scheme Pg 13 |

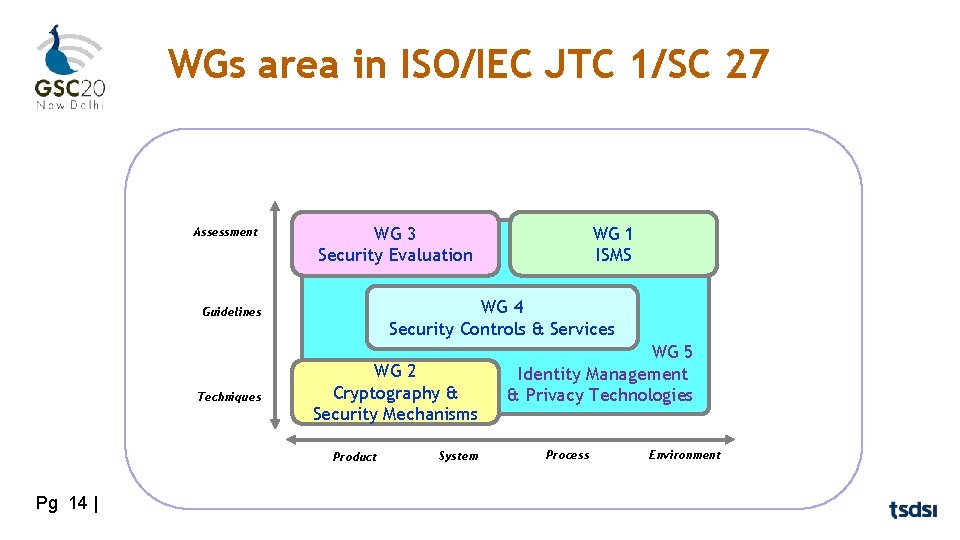
WGs area in ISO/IEC JTC 1/SC 27 Assessment WG 3 Security Evaluation WG 4 Security Controls & Services Guidelines Techniques WG 2 Cryptography & Security Mechanisms Product Pg 14 | WG 1 ISMS System WG 5 Identity Management & Privacy Technologies Process Environment

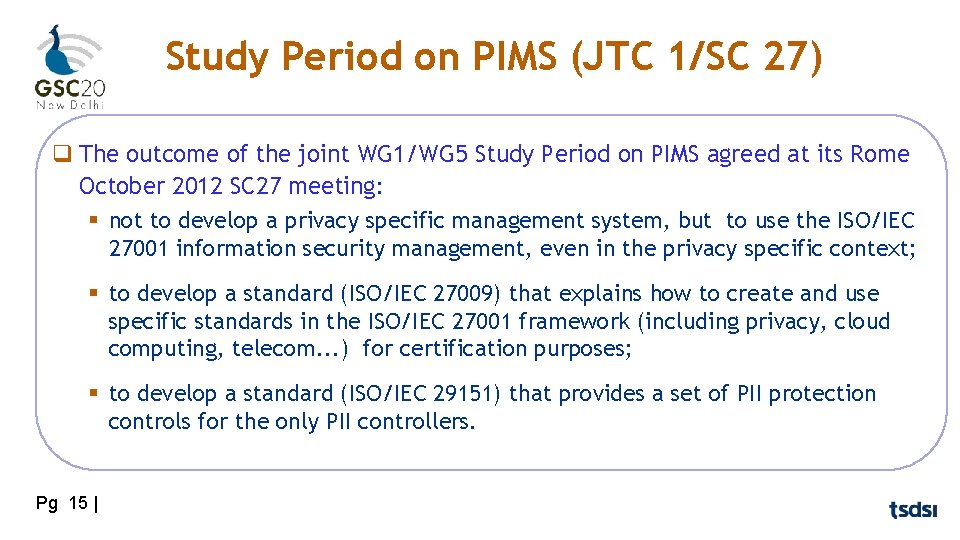
Study Period on PIMS (JTC 1/SC 27) q The outcome of the joint WG 1/WG 5 Study Period on PIMS agreed at its Rome October 2012 SC 27 meeting: § not to develop a privacy specific management system, but to use the ISO/IEC 27001 information security management, even in the privacy specific context; § to develop a standard (ISO/IEC 27009) that explains how to create and use specific standards in the ISO/IEC 27001 framework (including privacy, cloud computing, telecom. . . ) for certification purposes; § to develop a standard (ISO/IEC 29151) that provides a set of PII protection controls for the only PII controllers. Pg 15 |

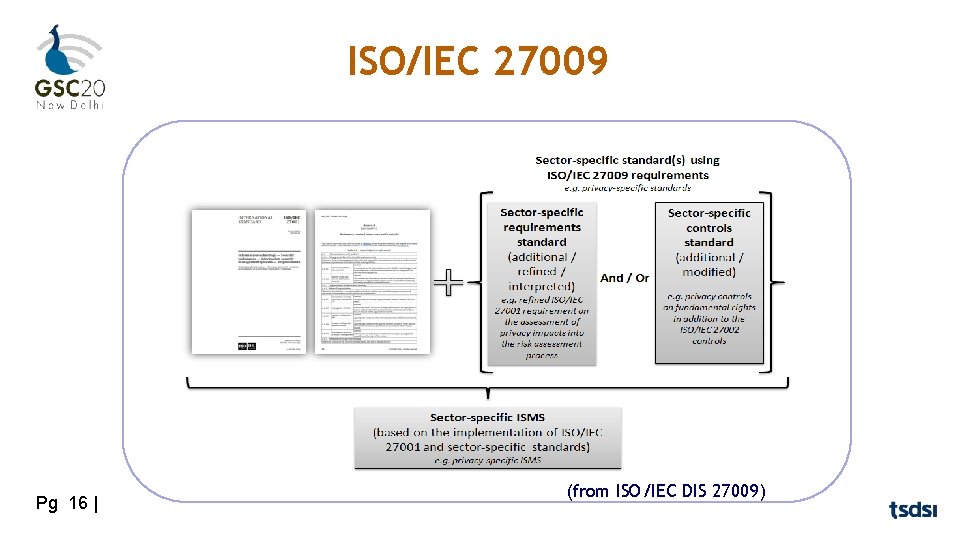
ISO/IEC 27009 Pg 16 | (from ISO/IEC DIS 27009)

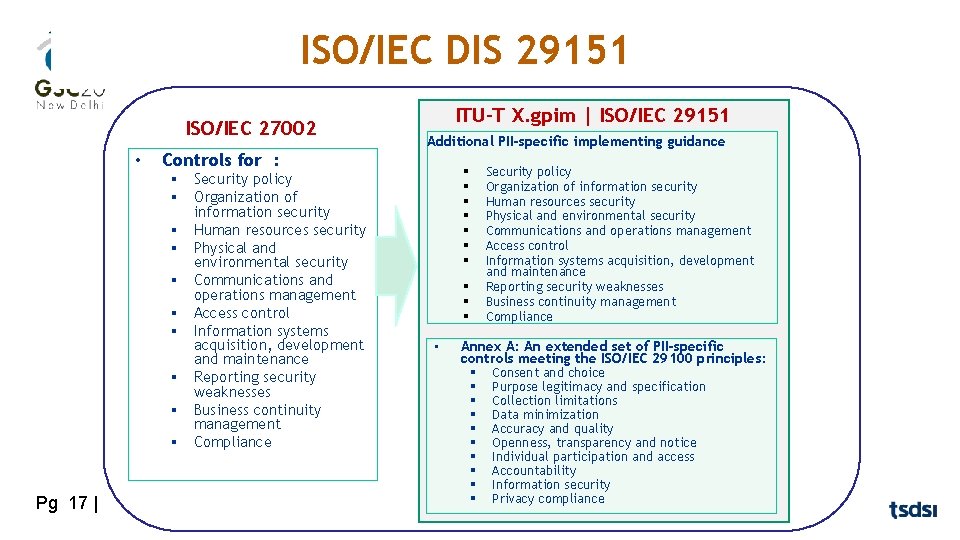
ISO/IEC DIS 29151 ISO/IEC 27002 • Additional PII-specific implementing guidance Controls for : § Security policy § Organization of information security § Human resources security § Physical and environmental security § Communications and operations management § Access control § Information systems acquisition, development and maintenance § Reporting security weaknesses § Business continuity management § Compliance Pg 17 | ITU-T X. gpim | ISO/IEC 29151 § § § § § • Security policy Organization of information security Human resources security Physical and environmental security Communications and operations management Access control Information systems acquisition, development and maintenance Reporting security weaknesses Business continuity management Compliance Annex A: An extended set of PII-specific controls meeting the ISO/IEC 29100 principles: § Consent and choice § Purpose legitimacy and specification § Collection limitations § Data minimization § Accuracy and quality § Openness, transparency and notice § Individual participation and access § Accountability § Information security § Privacy compliance

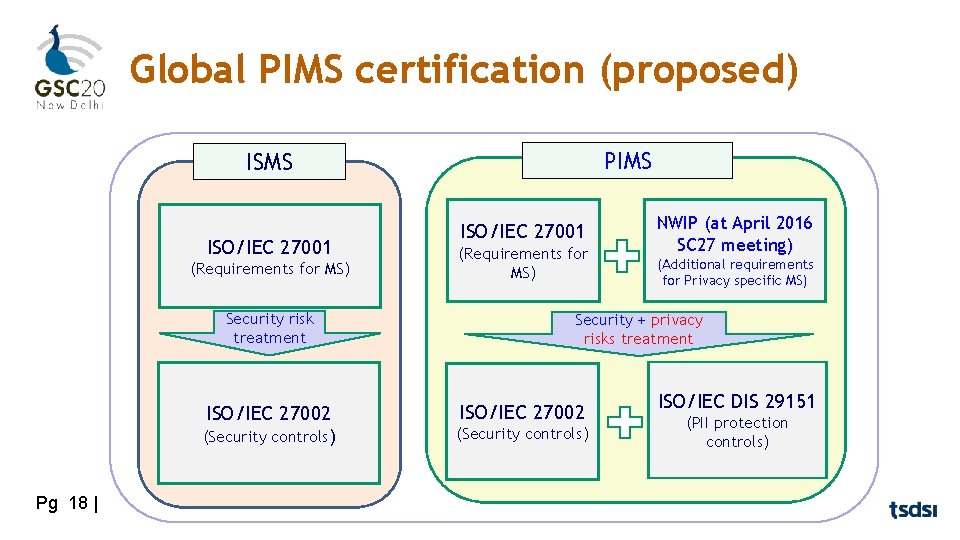
Global PIMS certification (proposed) PIMS ISO/IEC 27001 (Requirements for MS) Security risk treatment Pg 18 | ISO/IEC 27001 (Requirements for MS) NWIP (at April 2016 SC 27 meeting) (Additional requirements for Privacy specific MS) Security + privacy risks treatment ISO/IEC 27002 (Security controls) ISO/IEC DIS 29151 (PII protection controls)

Concluding remark Pg 19 |

Concluding remark q Challenges for PII protection § § q International standards for the global PIMS certification ready by April 2018. § § § Pg 20 | Data leakage incidents are growing. Increasing need for data transfer across the borders. Need to provide confidence of level of PII protection of the organizations who wish to receive data transferred across the border. Comprehensive solution: the PIMS certification. ISO/IEC 27001: 2013, ISO/IEC 27002: 2013, ISO/IEC 27009: 2016 ITU-T X. gpim | ISO/IEC DIS 29151 (April, 2016) NWIP for additional requirement for PIMS (agreed NWIP at April 2016 Tampa SC 27 meeting)

Thank you very much. CONTACT Pg 21 | E-mail: hyyoum at sch. ac. kr