Preliminary Knowledge Encoding Password Cryptography Related Concepts and






























- Slides: 50

Preliminary Knowledge ▎Encoding & Password & Cryptography ▎Related Concepts and Terminology

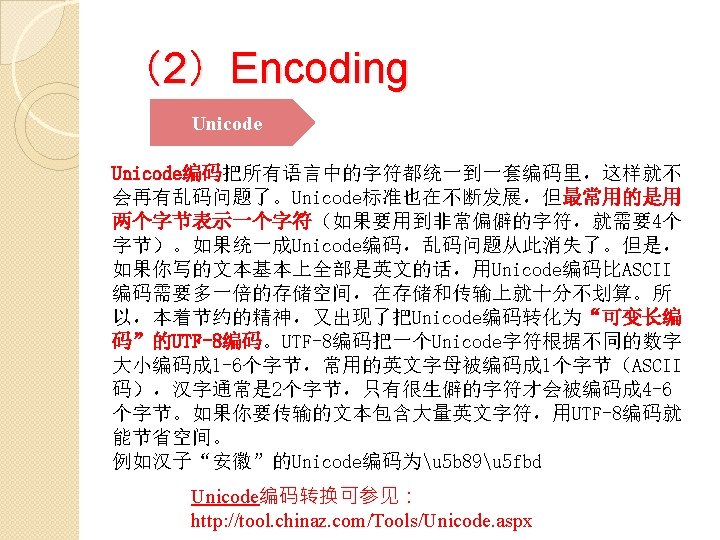
1. Encoding


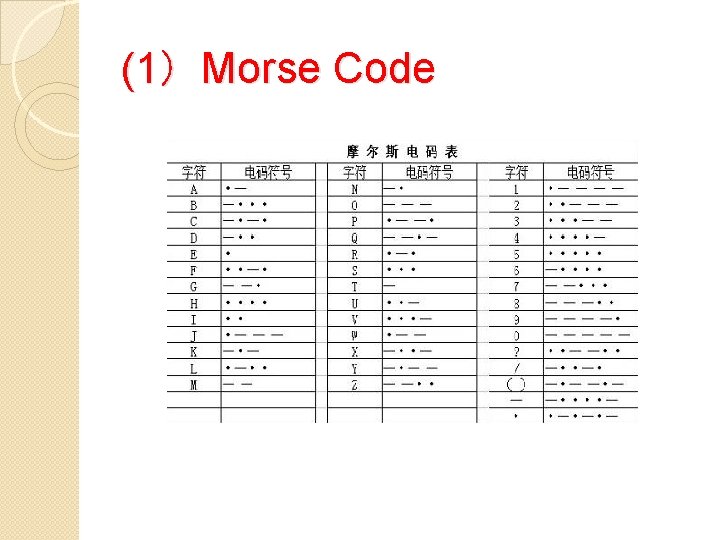
(1)Morse Code


(1)Morse Code You can visit Wikipedia for Morse code: https: //en. wikipedia. org/wiki/Morse_code However, Morse code is a kind of telegraph code(电 报 码 ), not belong to Modern Cryptography(现代密码学).

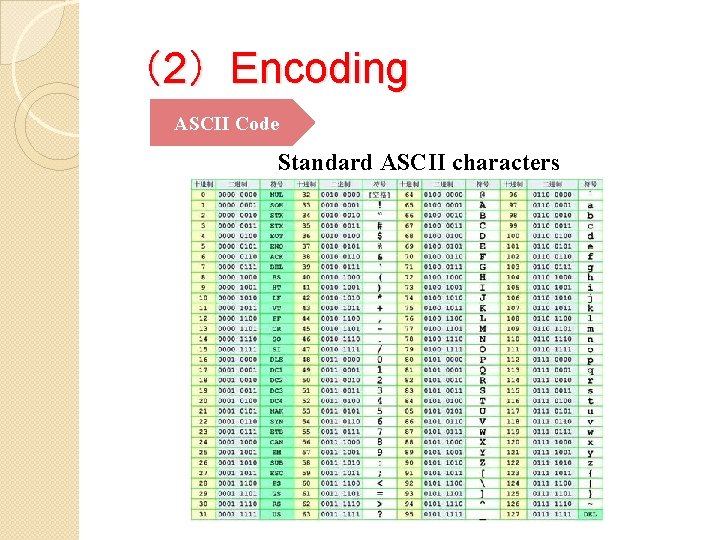
(2)Encoding ASCII Code Standard ASCII characters

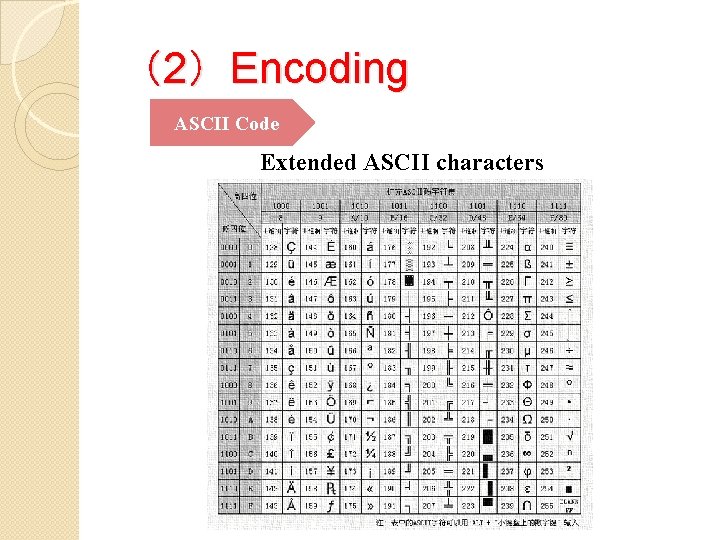
(2)Encoding ASCII Code Extended ASCII characters

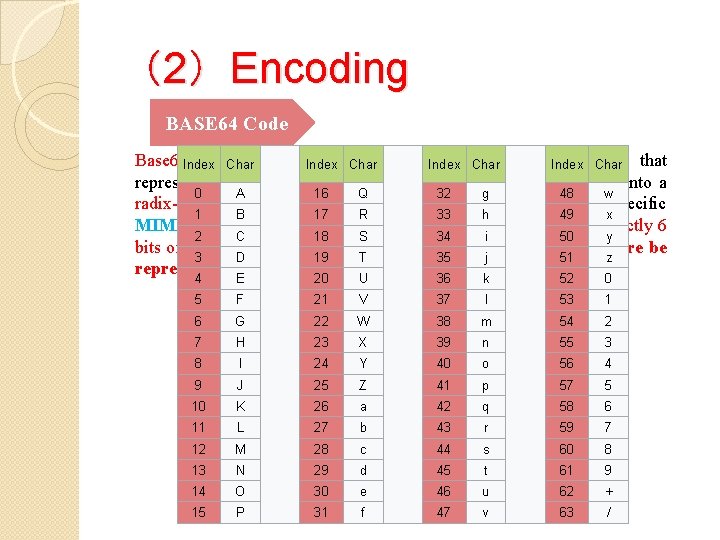
(2)Encoding BASE 64 Code Base 64 Index is a. Char group of. Index similar encoding. Index schemes Char binary-to-text Index Char that represent binary data in an ASCII string format by translating it into a 0 A 16 Q 32 g 48 w radix-64 representation. The term Base 64 originates from a specific 1 B 17 R 33 h 49 x MIME content transfer encoding. Each Base 64 digit represents exactly 6 2 C 18 S 34 i 50 y bits of data. Three 8 -bit bytes (i. e. , a total of 24 bits) can therefore be 3 D 19 T 35 j 51 z represented by four 6 -bit Base 64 digits. 4 E 20 U 36 k 52 0 5 F 21 V 37 l 53 1 6 G 22 W 38 m 54 2 7 H 23 X 39 n 55 3 8 I 24 Y 40 o 56 4 9 J 25 Z 41 p 57 5 10 K 26 a 42 q 58 6 11 L 27 b 43 r 59 7 12 M 28 c 44 s 60 8 13 N 29 d 45 t 61 9 14 O 30 e 46 u 62 + 15 P 31 f 47 v 63 /

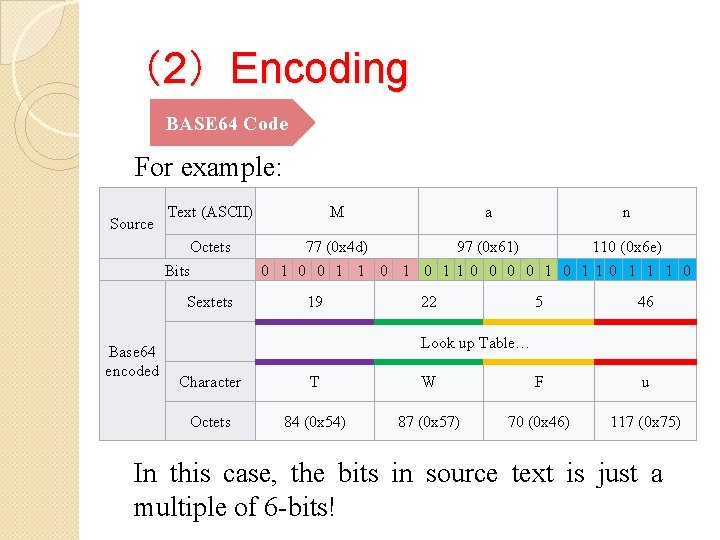
(2)Encoding BASE 64 Code For example: Source Text (ASCII) Octets Bits Sextets Base 64 encoded M a n 77 (0 x 4 d) 97 (0 x 61) 110 (0 x 6 e) 0 1 0 0 1 1 0 11 0 0 1 0 110 1 1 1 0 19 22 5 46 Look up Table… Character T W F u Octets 84 (0 x 54) 87 (0 x 57) 70 (0 x 46) 117 (0 x 75) In this case, the bits in source text is just a multiple of 6 -bits!

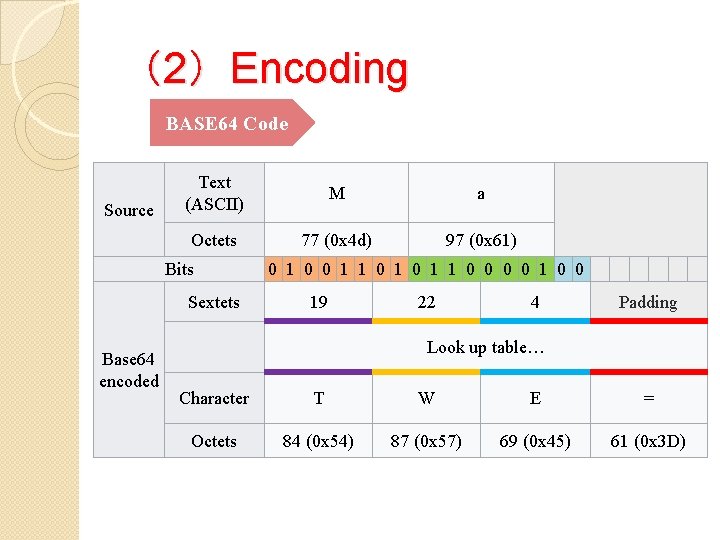
(2)Encoding BASE 64 Code =, padding characters might be added to make the last encoded block contain four Base 64 characters. If there are only two significant input octets (e. g. , 'Ma'), or when the last input group contains only two octets, all 16 bits will be captured in the first three Base 64 digits (18 bits); the two least significant bits of the last content -bearing 6 -bit block will turn out to be zero, and discarded on decoding (along with the following = padding characters):

(2)Encoding BASE 64 Code Source Text (ASCII) M a Octets 77 (0 x 4 d) 97 (0 x 61) Bits Sextets Base 64 encoded 0 1 0 0 1 1 0 0 19 22 4 Padding Look up table… Character T W E = Octets 84 (0 x 54) 87 (0 x 57) 69 (0 x 45) 61 (0 x 3 D)

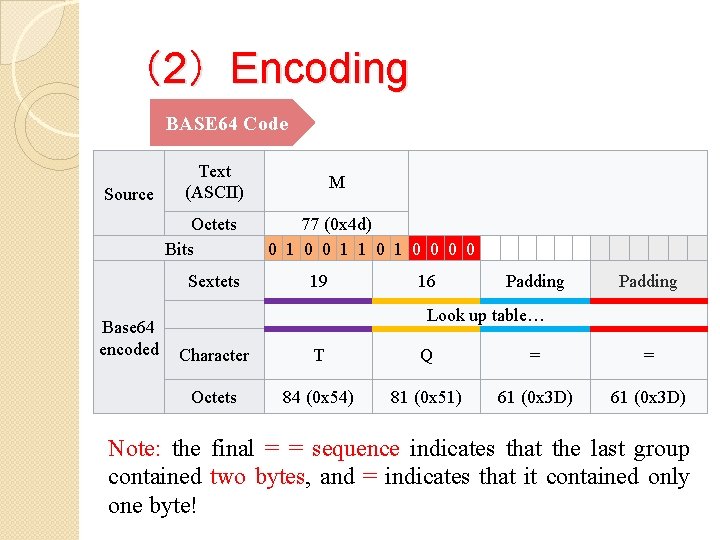
(2)Encoding BASE 64 Code If there is only one significant input octet (e. g. , 'M'), or when the last input group contains only one octet, all 8 bits will be captured in the first two Base 64 digits (12 bits); the four least significant bits of the last contentbearing 6 -bit block will turn out to be zero, and discarded on decoding (along with the following = padding characters):

(2)Encoding BASE 64 Code Source Text (ASCII) Octets Bits Sextets Base 64 encoded M 77 (0 x 4 d) 0 1 0 0 1 1 0 0 0 0 19 16 Padding Look up table… Character T Q = = Octets 84 (0 x 54) 81 (0 x 51) 61 (0 x 3 D) Note: the final = = sequence indicates that the last group contained two bytes, and = indicates that it contained only one byte!


2. PASSWORD

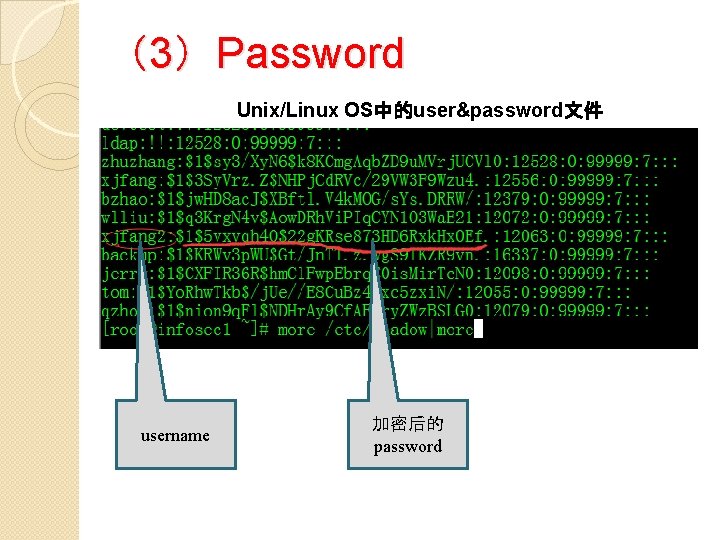
(3)Password Unix/Linux OS中的user&password文件 username 加密后的 password



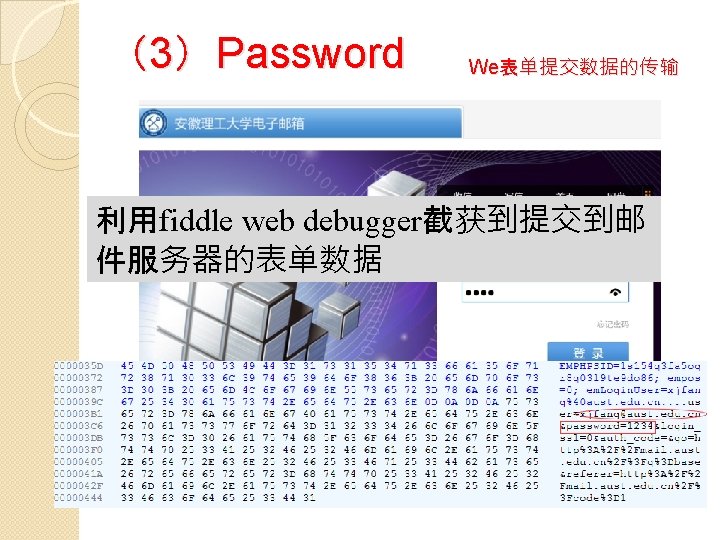
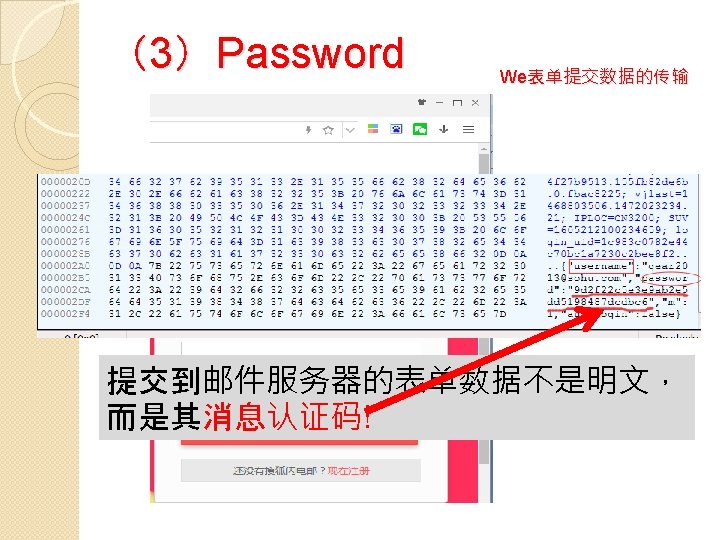
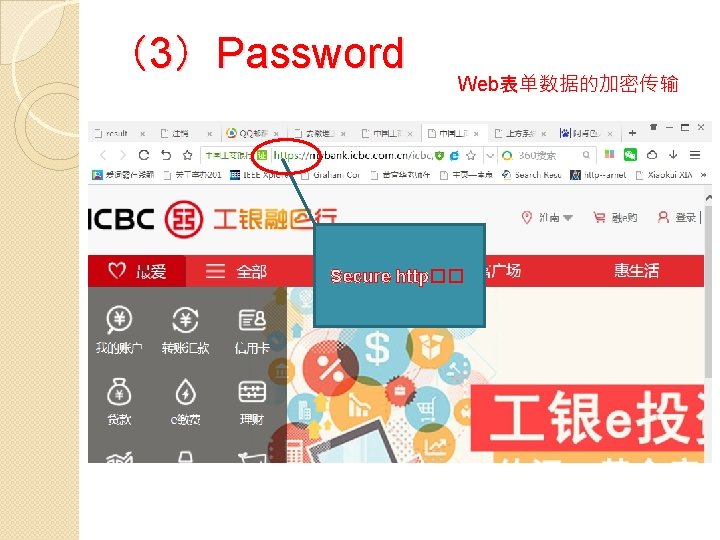
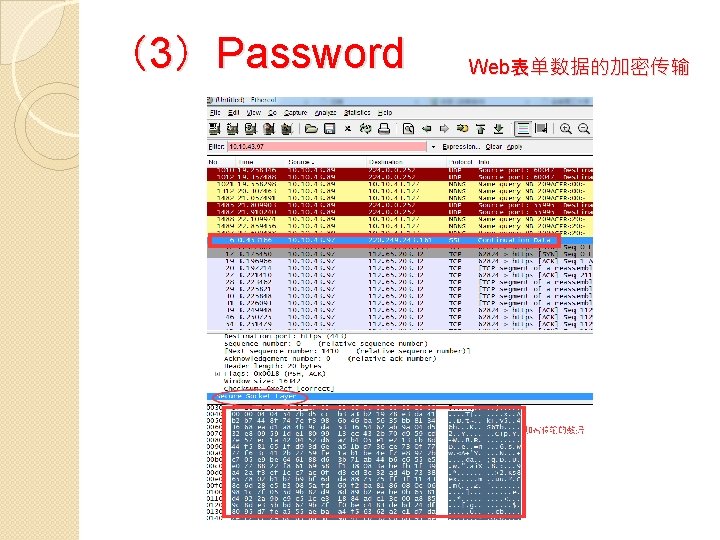
(3)Password Web表单数据的加密传输 Secure http��


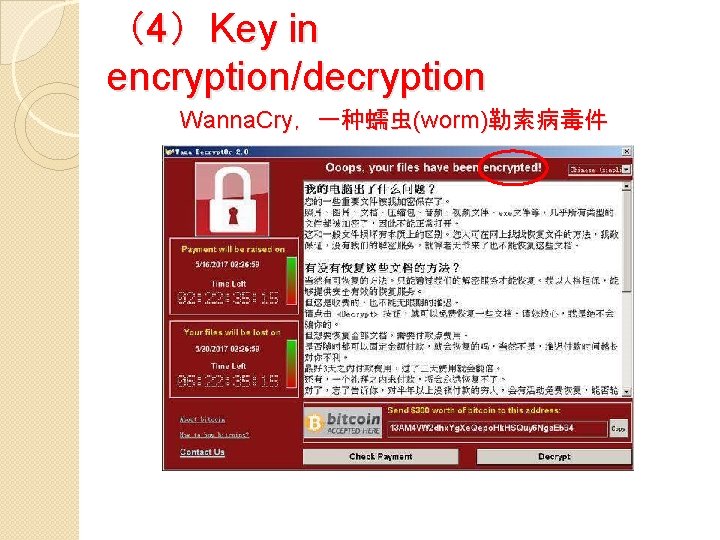
(4)Key in encryption/decryption Wanna. Cry,一种蠕虫(worm)勒索病毒件

3. Cryptography





现代密码学(二) 1976年 , Diffie和 Hellman在 刊 物 “IEEE Transactions on Information Theory”发 表 论 文“New Directions in Cryptography”, 提出了 公钥密码体制(Public key Cryptosystem)。 1978年 MIT的 Rivest, Shamir, Adleman提 出 了 RSA 公钥加密体制算法。 Rabin, Elgamal, ECC等其它公钥密码体制。 近年出现DNA密码、混沌密码、量子密码等。







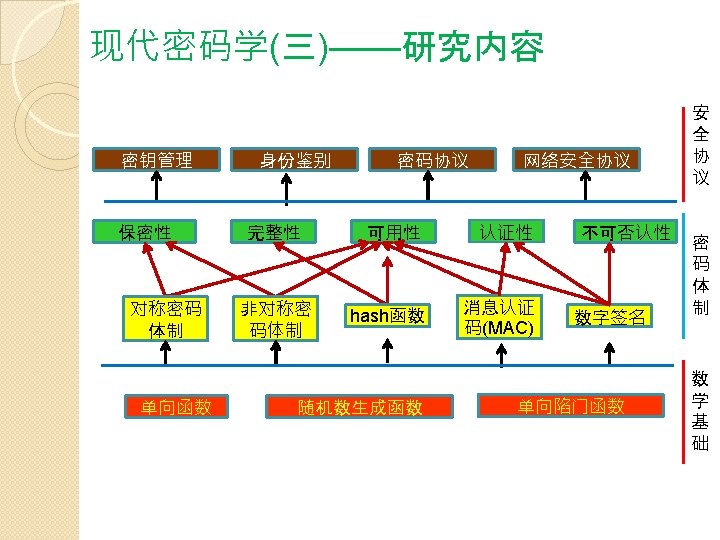
4. Concepts and Terminology



Information Security From Wikipedia, the free encyclopedia: Information security, sometimes shortened to Info. Sec, is the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. It is a general term that can be used regardless of the form the data may take (e. g. electronic, physical).




The role of Cryptography in information system security With the development of Internet, mobile Internet, Electronic Commerce, electronic-payment, big data and cloud Computing, user’s identity, data confidentiality and data integrity are related to the cryptography. l Confidentiality is implemented via encryption techniques l Integrity is implemented via message authentication code(Hash algorithm) l Identity authentication is done by authentication protocol. l Non-repudiation is established by digital signature and digital certificate. l Network security protocol also needs cryptography.

The role of Cryptography in information system security n. Cryptography is the core and foundation of information security. n. However, the cryptography is not only technology for guaranteeing information security. n. Information security 30% relies on Technology, 70% replies on management.


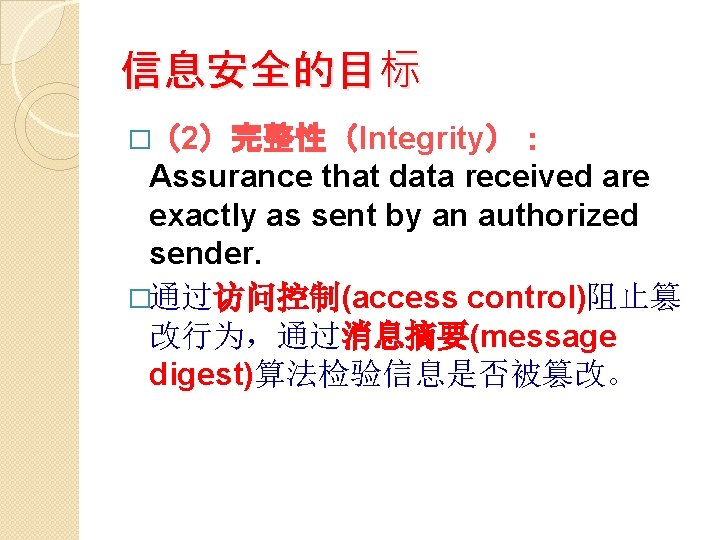
信息安全的目标 �(2)完整性(Integrity): Assurance that data received are exactly as sent by an authorized sender. �通过访问控制(access control)阻止篡 改行为,通过消息摘要(message digest)算法检验信息是否被篡改。


信息安全的目标 �(4)真实性(Authentication): passurance that the communicating entity is the one it claims to be. ppeer entity authentication. p. Data-origin authentication.

信息安全的目标 �(5)不可抵赖性(Non-Repudiation): pprotection against denial by one of the parties in a communication. p. Origin non-repudiation:proof that the message was sent by the specified party. p. Destination non-repudiation:proof that the message was received by the specified party. 一般通过数字签名(digital signature)来 提供不可抵赖性服务。

