Prastudy Fauzi Helger Lipmaa Michal Zajac University of






![§ Commitment: Pi (X) are linearly independent, well-chosen polynomials [Ai(X)]i = [a. IPI (X) § Commitment: Pi (X) are linearly independent, well-chosen polynomials [Ai(X)]i = [a. IPI (X)](https://slidetodoc.com/presentation_image_h/f8b51c9e62b4d9bb80d870330c23d366/image-22.jpg)



- Slides: 27

Prastudy Fauzi, Helger Lipmaa, Michal Zajac University of Tartu, Estonia ASIACRYPT 2016 Estonian-Latvian Joint Theory Days, 14. 10. 2016

§ A new efficient CRS-based NIZK shuffle argument § Four+ times more efficient verification than in prior work § Verification time more critical § Soundness proof in the Generic Bilinear Group Model § Very complicated machine-assisted proof § Use computer algebra to solve systems of polyn. eq. § Esp. to find Gröbner bases § Enables proof verification by practitioners § Possible future work: synthesis?

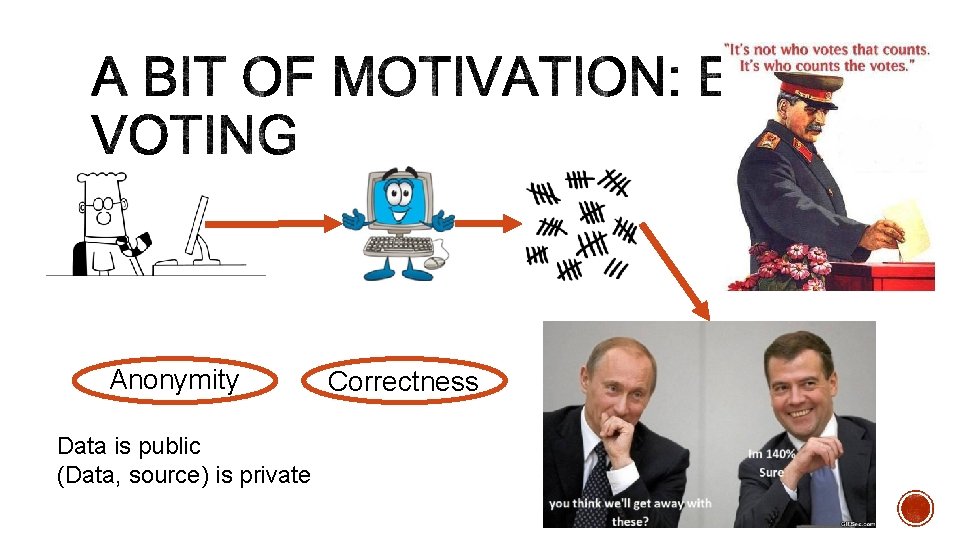
Anonymity Data is public (Data, source) is private Correctness

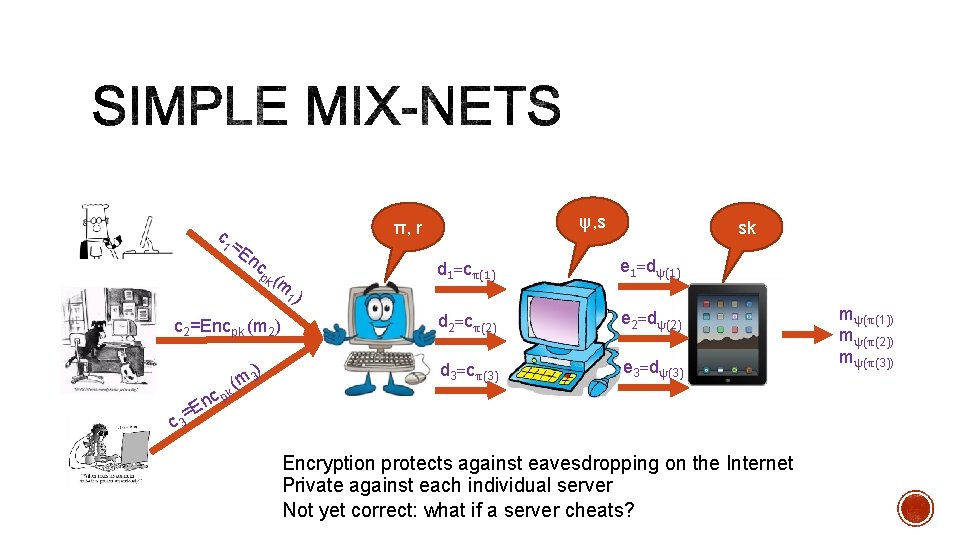
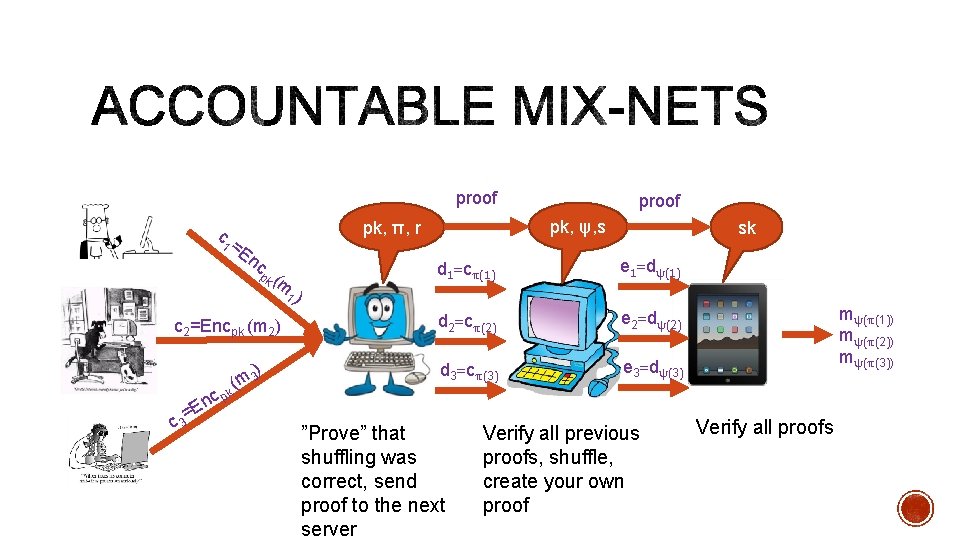
c 1= En c pk ( m c 2=Encpk (m 2) cp En k ψ, s π, r ) 3 m ( sk d 1=cπ(1) e 1=dψ(1) d 2=cπ(2) e 2=dψ(2) d 3=cπ(3) e 3=dψ(3) 1) c 3= Encryption protects against eavesdropping on the Internet Private against each individual server Not yet correct: what if a server cheats? mψ(π(1)) mψ(π(2)) mψ(π(3))

proof c En c pk ( m c 2=Encpk (m 2) cp En k c 3= pk, ψ, s pk, π, r 1= ) 3 m ( proof sk d 1=cπ(1) e 1=dψ(1) d 2=cπ(2) e 2=dψ(2) d 3=cπ(3) e 3=dψ(3) 1) ”Prove” that shuffling was correct, send proof to the next server Verify all previous proofs, shuffle, create your own proof mψ(π(1)) mψ(π(2)) mψ(π(3)) Verify all proofs

§ Shuffle argument: § efficient zero knowledge argument of correctness of shuffling § Many shuffles in the ”random oracle model” exist § Several of them are quite efficient § Existing CRS model arguments much less efficient

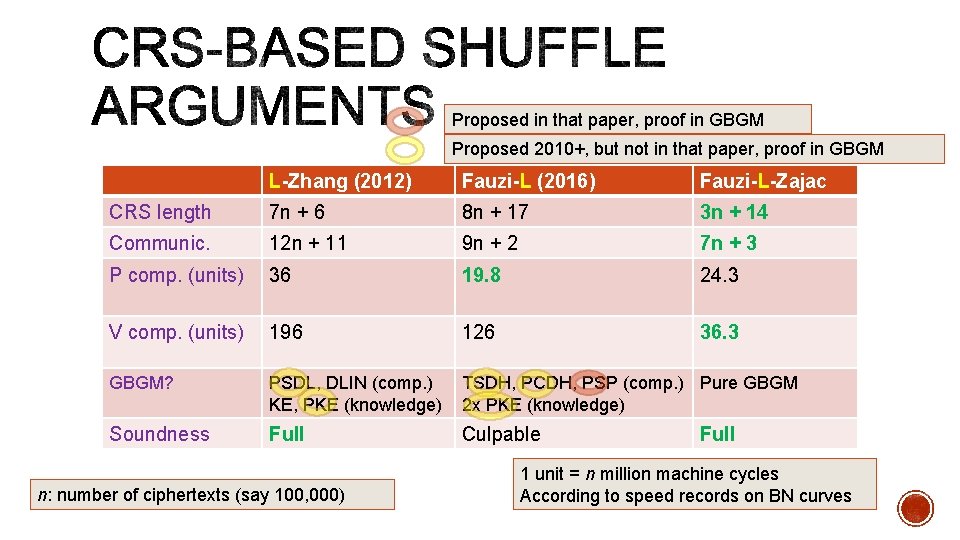
Proposed in that paper, proof in GBGM Proposed 2010+, but not in that paper, proof in GBGM L-Zhang (2012) Fauzi-L (2016) Fauzi-L-Zajac CRS length 7 n + 6 8 n + 17 3 n + 14 Communic. 12 n + 11 9 n + 2 7 n + 3 P comp. (units) 36 19. 8 24. 3 V comp. (units) 196 126 36. 3 GBGM? PSDL, DLIN (comp. ) KE, PKE (knowledge) TSDH, PCDH, PSP (comp. ) Pure GBGM 2 x PKE (knowledge) Soundness Full Culpable n: number of ciphertexts (say 100, 000) Full 1 unit = n million machine cycles According to speed records on BN curves

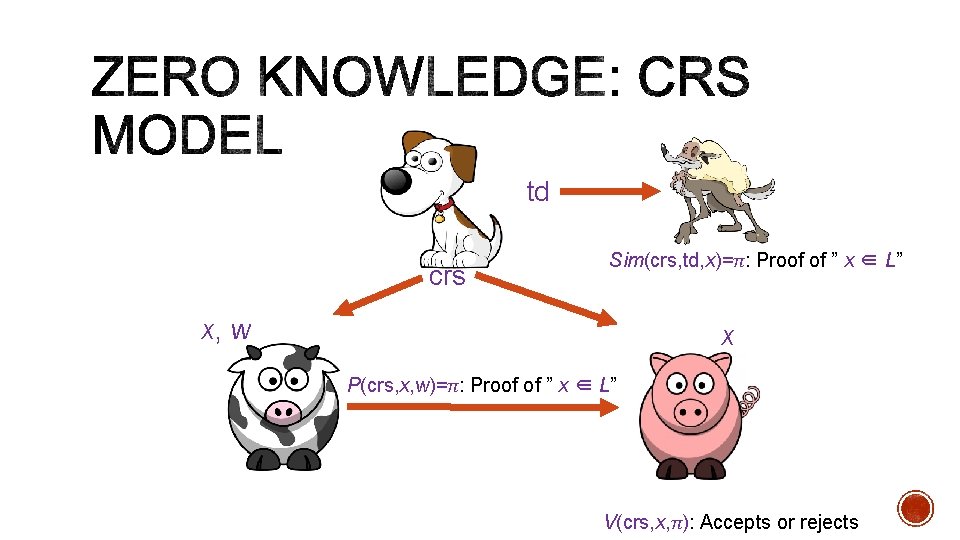
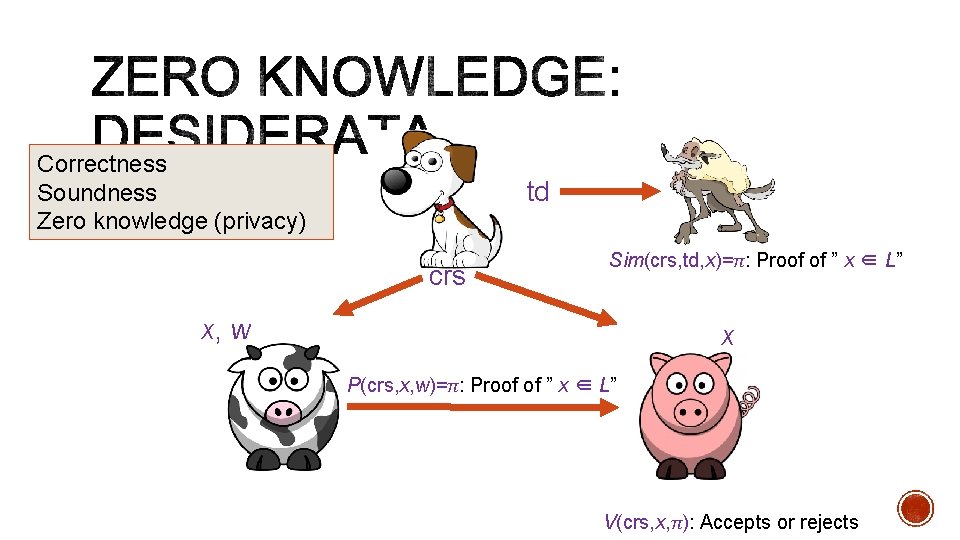
td crs Sim(crs, td, x)=π: Proof of ” x ∈ L” x, w x P(crs, x, w)=π: Proof of ” x ∈ L” V(crs, x, π): Accepts or rejects

Correctness Soundness Zero knowledge (privacy) td crs Sim(crs, td, x)=π: Proof of ” x ∈ L” x, w x P(crs, x, w)=π: Proof of ” x ∈ L” V(crs, x, π): Accepts or rejects

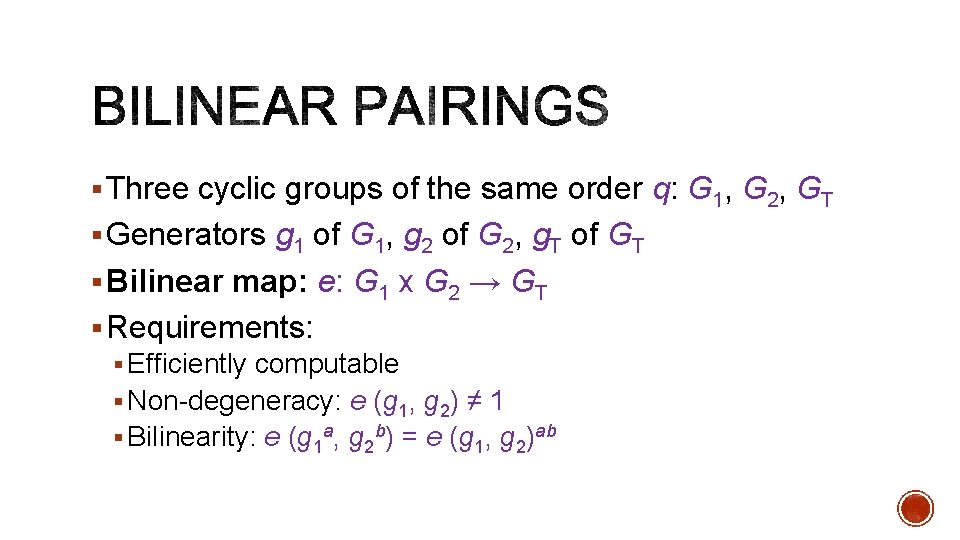
§ Three cyclic groups of the same order q: G 1, G 2, GT § Generators g 1 of G 1, g 2 of G 2, g. T of GT § Bilinear map: e: G 1 x G 2 → GT § Requirements: § Efficiently computable § Non-degeneracy: e (g 1, g 2) ≠ 1 § Bilinearity: e (g 1 a, g 2 b) = e (g 1, g 2)ab

§Inverting pairings should be hard § Given e (A, B), compute either A or B § Analogous to DL: given ga, compute a §What else should be hard?

§ People disagree… § A few hundred (thousand? ) known pairing-related hardness assumptions § Each of them has to be cryptanalysed § ”Easiest” sanity check: § does this assumption hold in the generic model?

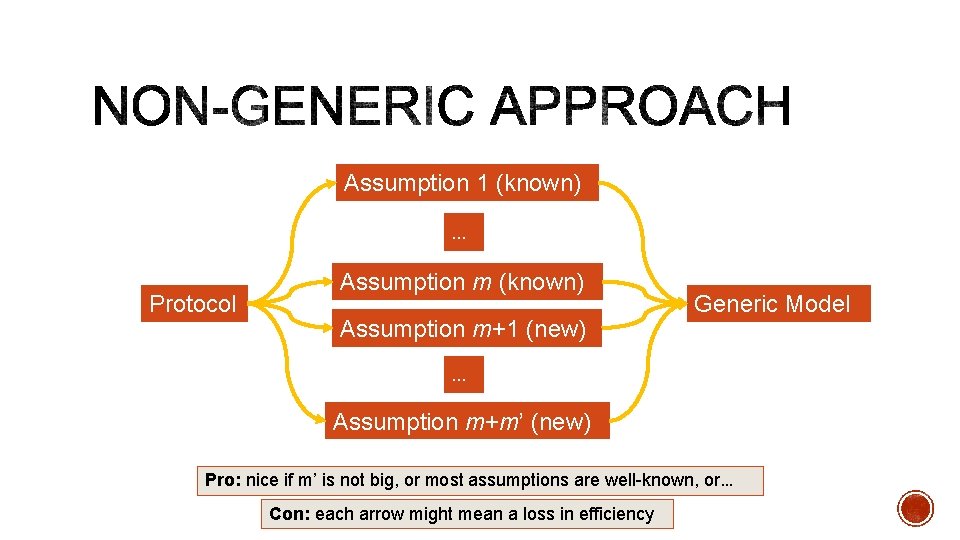
Assumption 1 (known) … Protocol Assumption m (known) Assumption m+1 (new) Generic Model … Assumption m+m’ (new) Pro: nice if m’ is not big, or most assumptions are well-known, or… Con: each arrow might mean a loss in efficiency

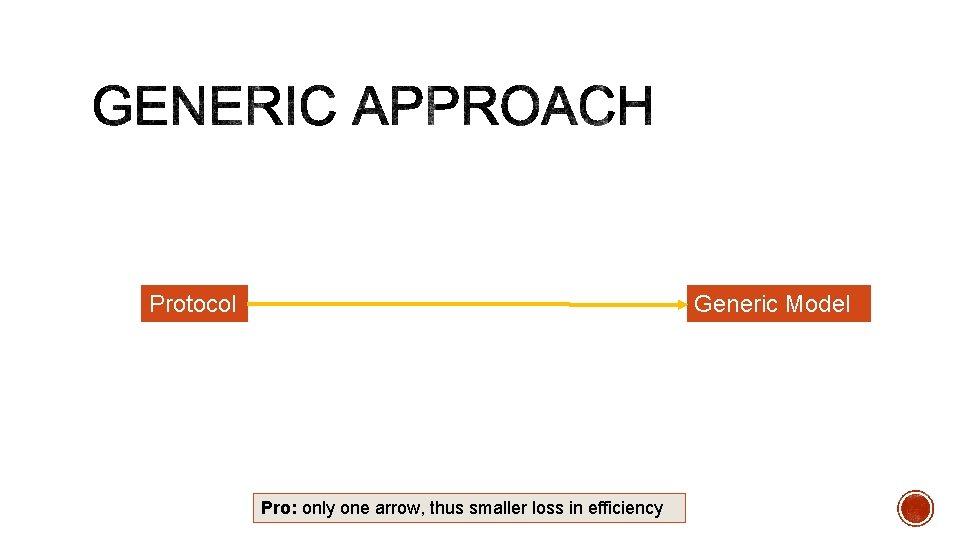
Protocol Generic Model Pro: only one arrow, thus smaller loss in efficiency

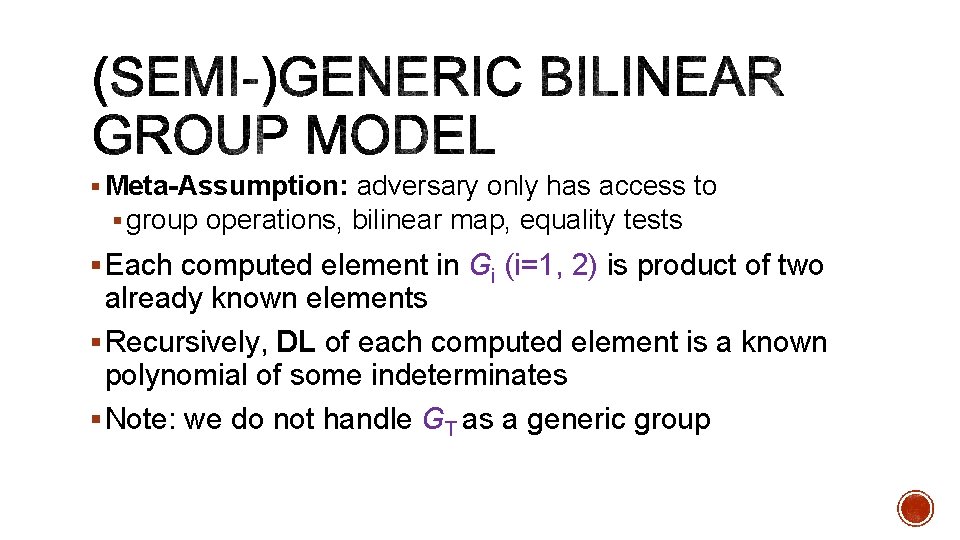
§ Meta-Assumption: adversary only has access to § group operations, bilinear map, equality tests § Each computed element in Gi (i=1, 2) is product of two already known elements § Recursively, DL of each computed element is a known polynomial of some indeterminates § Note: we do not handle GT as a generic group

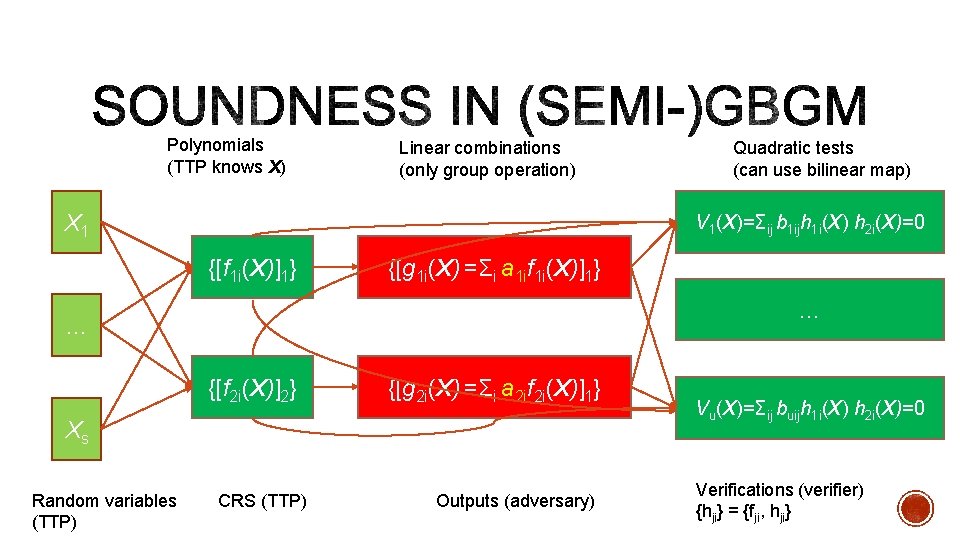
Polynomials (TTP knows X) Linear combinations (only group operation) X 1 V 1(X)=Σij b 1 ijh 1 i(X) h 2 i(X)=0 {[f 1 i(X)]1} {[g 1 i(X) =Σi a 1 if 1 i(X)]1} … … {[f 2 i(X)]2} {[g 2 i(X) =Σi a 2 if 2 i(X)]1} Xs Random variables (TTP) Quadratic tests (can use bilinear map) CRS (TTP) Outputs (adversary) Vu(X)=Σij buijh 1 i(X) h 2 i(X)=0 Verifications (verifier) {hji} = {fji, hji}

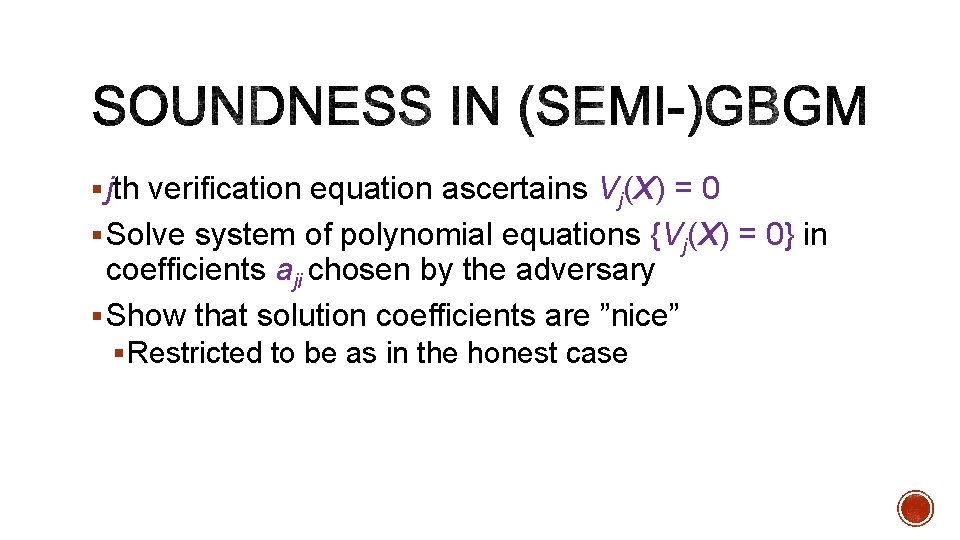
§ jth verification equation ascertains Vj(X) = 0 § Solve system of polynomial equations {Vj(X) = 0} in coefficients aji chosen by the adversary § Show that solution coefficients are ”nice” § Restricted to be as in the honest case

§ Decomposing: § Write down main building blocks you need to prove in argument § Each ”subargument” should be efficiently verifiable (by a single pairing) § Ascertain each subargument is sound independently § CRS composition: § Compose CRS-s of individual subarguments together, getting one big CRS

§ Soundness check: § Is the composed protocol sound? § Subarguments get extra inputs in CRS § If not: introduce new random variables that guarantee CRS elements are used in only correct subarguments, reiterate

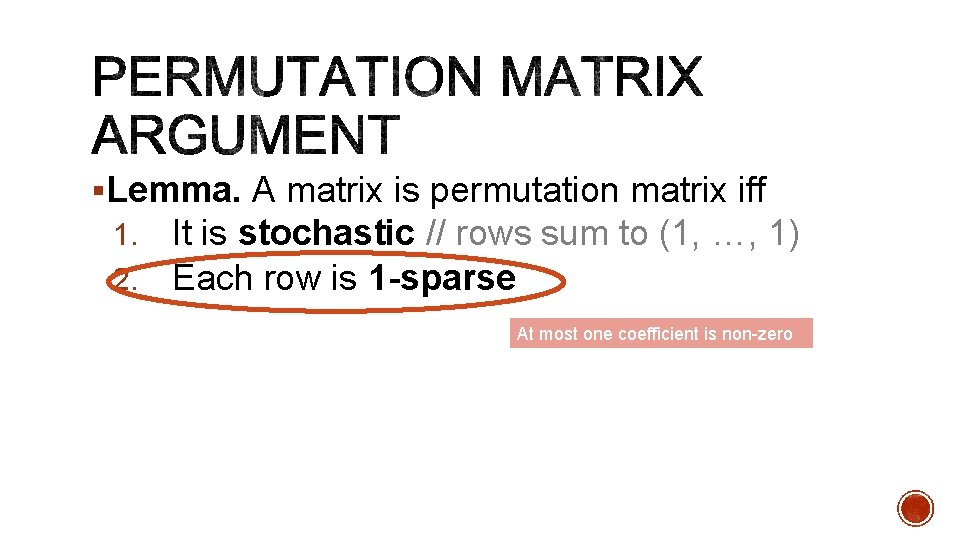
§ ”Permutation matrix argument”: § Prover commits to permutation; proves this is done correctly § ”Consistency argument”: § Prover proves she used the committed permutation to shuffle ciphertexts § ”Validity argument”: § Prover proves each ciphertext has been formed ”correctly” § Correctly: so that the soundness proof goes through

§Lemma. A matrix is permutation matrix iff 1. It is stochastic // rows sum to (1, …, 1) 2. Each row is 1 -sparse At most one coefficient is non-zero
![Commitment Pi X are linearly independent wellchosen polynomials AiXi a IPI X § Commitment: Pi (X) are linearly independent, well-chosen polynomials [Ai(X)]i = [a. IPI (X)](https://slidetodoc.com/presentation_image_h/f8b51c9e62b4d9bb80d870330c23d366/image-22.jpg)
§ Commitment: Pi (X) are linearly independent, well-chosen polynomials [Ai(X)]i = [a. IPI (X) + r. Xρ]i // i = 1, 2 § Argument: // ”square span programs” [π(X)]1 = [((a. IPI (X) + P 0 (X) + r. Xρ)2 - 1) / Xρ]1 § Verification equation: V (X) : = (A 1(X) + Xα+ P 0 (X)) (A 2(X) - Xα+ P 0 (X)) - π(X) Xρ – (1 - Xα)2 =0

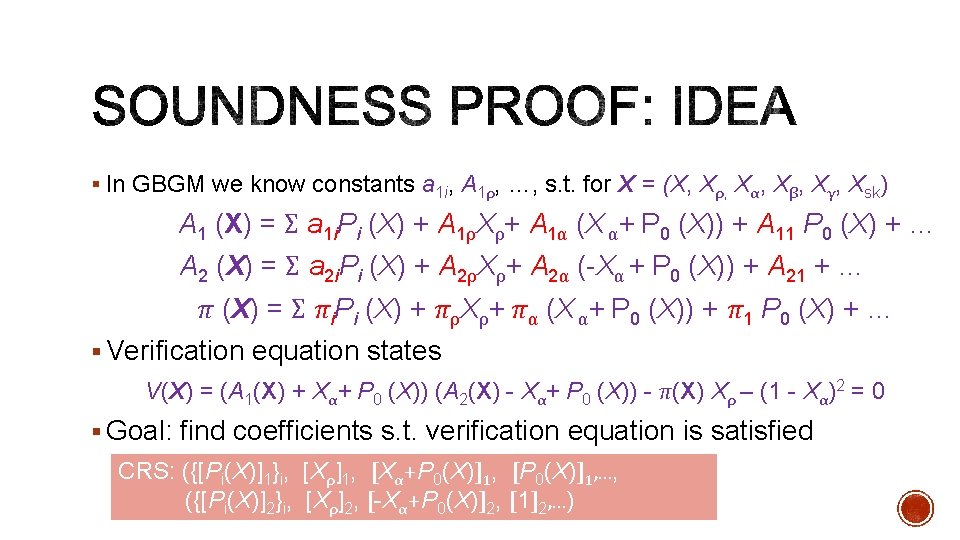
§ In GBGM we know constants a 1 i, A 1ρ, …, s. t. for X = (X, Xρ, Xα, Xβ, Xγ, Xsk) A 1 (X) = Σ a 1 i. Pi (X) + A 1ρXρ+ A 1α (X α+ P 0 (X)) + A 11 P 0 (X) + … A 2 (X) = Σ a 2 i. Pi (X) + A 2ρXρ+ A 2α (-Xα + P 0 (X)) + A 21 + … π (X) = Σ πi. Pi (X) + πρXρ+ πα (X α+ P 0 (X)) + π1 P 0 (X) + … § Verification equation states V(X) = (A 1(X) + Xα+ P 0 (X)) (A 2(X) - Xα+ P 0 (X)) - π(X) Xρ – (1 - Xα)2 = 0 § Goal: find coefficients s. t. verification equation is satisfied CRS: ({[Pi(X)]1}i, [Xρ]1, [Xα+P 0(X)]1, [P 0(X)]1, …, ({[Pi(X)]2}i, [Xρ]2, [-Xα+P 0(X)]2, [1]2, …)

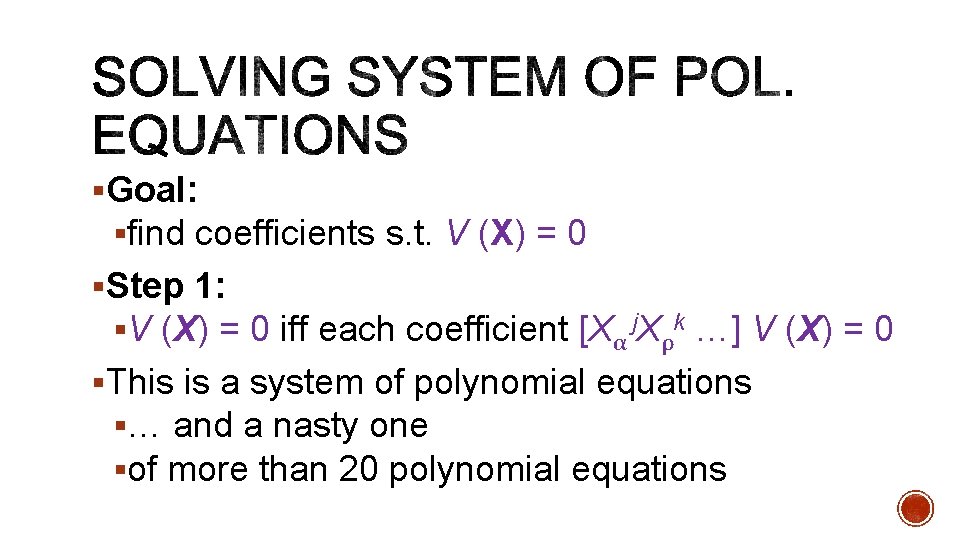
§Goal: §find coefficients s. t. V (X) = 0 §Step 1: §V (X) = 0 iff each coefficient [Xα j. Xρk …] V (X) = 0 §This is a system of polynomial equations §… and a nasty one §of more than 20 polynomial equations


§ Too large a system for a simple human researcher… § Used a mixture of computer algebra system and manual labor 1. Use linear independence of Pi (X) to split some coefficients 2. Construct Gröbner basis of system of polynomial equations • Needs(? ) a CAS… 3. Solve the Gröbner basis • Can be done manually or by using CAS • Obtain that Ai (X) = a. I PI (X) => Sound

 Lipmaa
Lipmaa Cholid fauzi
Cholid fauzi @andi fadhel:http://work4unity.in/haicantik.html
@andi fadhel:http://work4unity.in/haicantik.html Radosť skloňovanie
Radosť skloňovanie Prechladnuty zajac
Prechladnuty zajac Ken zajac
Ken zajac Stanislaw zajac
Stanislaw zajac Minister zdravotníctva zajac
Minister zdravotníctva zajac Ronen basri
Ronen basri Michal irani
Michal irani Michal grešlik
Michal grešlik Michal sroka
Michal sroka Michal skloňování
Michal skloňování Michal bick
Michal bick Michal heczko
Michal heczko Michal lehnert
Michal lehnert Michal vajcik
Michal vajcik Michal avny
Michal avny Kolko fazul vojde do hrnca
Kolko fazul vojde do hrnca Casus nocet domino
Casus nocet domino Michal hozza
Michal hozza Matilda evans
Matilda evans Michal kalman vek
Michal kalman vek Michal miloslav hodža
Michal miloslav hodža Michal tulek
Michal tulek Michal inbar-feigenberg
Michal inbar-feigenberg Michal kolcun
Michal kolcun Michal tkaczyk
Michal tkaczyk