Practical RSA vs ECC Speed Comparisons Dr Douglas













- Slides: 19

Practical RSA vs. ECC Speed Comparisons Dr. Douglas A. Kuhlman Motorola Labs

Public Key Primitives ¨ Key exchange: Share a “short” (128 -256 bit) key between two parties (server and client) – This key is used to encrypt all information passed during the session ¨ Sign: The process of binding some piece of information to a specific entity ¨ Verify: The process of validating a signature ¨ Certificate: A signed binding of public information to a certain entity (an individual, company, or device)

RSA Overview ¨ Based on the difficulty of factoring n = pq, where p and q are very large primes ¨ Public parameters: (n, e) ¨ Private key: d (value s. t. ed = 1 (mod φ(n)) ¨ Main strength parameter is |n|, the number of bits in n ¨ |n| = 1024 fairly common

ECC Overview ¨ Based on more complicated mathematics ¨ Public parameters: (E, P, Q) ¨ Private key: a (value s. t a. P = Q) ¨ Main strength parameter is |E|, the number of bits in the order of E ¨ |E| = 160/163 or 192 common

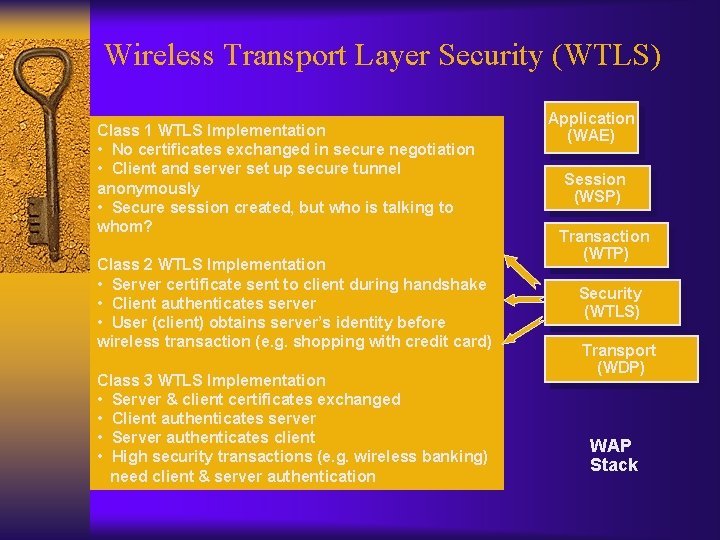
Wireless Transport Layer Security (WTLS) Class 1 WTLS Implementation • No certificates exchanged in secure negotiation • Client and server set up secure tunnel anonymously • Secure session created, but who is talking to whom? Class 2 WTLS Implementation • Server certificate sent to client during handshake • Client authenticates server • User (client) obtains server’s identity before wireless transaction (e. g. shopping with credit card) Class 3 WTLS Implementation • Server & client certificates exchanged • Client authenticates server • Server authenticates client • High security transactions (e. g. wireless banking) need client & server authentication Application (WAE) Session (WSP) Transaction (WTP) Security (WTLS) Transport (WDP) WAP Stack

WTLS Security Class 1 ¨ Key exchange only ¨ No infrastructure (PKI) needed ¨ No way to authenticate server or client – Encrypts credit card number, but to whom are you are giving it? ¨ Applications – When other methods of authentication are available • Telephone calls, visible results – When no infrastructure is available • Better than nothing • False sense of security?

WTLS Security Class 2 ¨ Key exchange, server signs, client verifies ¨ Equivalent to HTML browser, authenticates server ¨ Requires some PKI – Client must have a trusted root key – Server certificate must be signed by trusted authority • Possibly in a certificate tree – Server is responsible for keeping private key secret ¨ Best for transactions where client identity can be verified through different means – Ship to credit card address – Client provides password/pin to server

WTLS Security Class 3 ¨ Key exchange, server and client sign and verify ¨ Requires full PKI – Every server and client must have a certificate signed by a trusted authority – Server and client need to keep a key secret ¨ Adds a higher level of trust for service providers by authenticating client – Stock purchases, banking ¨ Electronic signature – Business approval signatures, access to medical data

Public Key Options in WTLS Standard ¨ RSA – Current wireline standard – Large key size (1024 bits) – Use of small exponent (65537 = 216 + 1) makes this fastest for WTLS class 2 ¨ Elliptic curve – Small key size (163 bits) – Fastest for WTLS class 3 (signing) – Conceptually most difficult

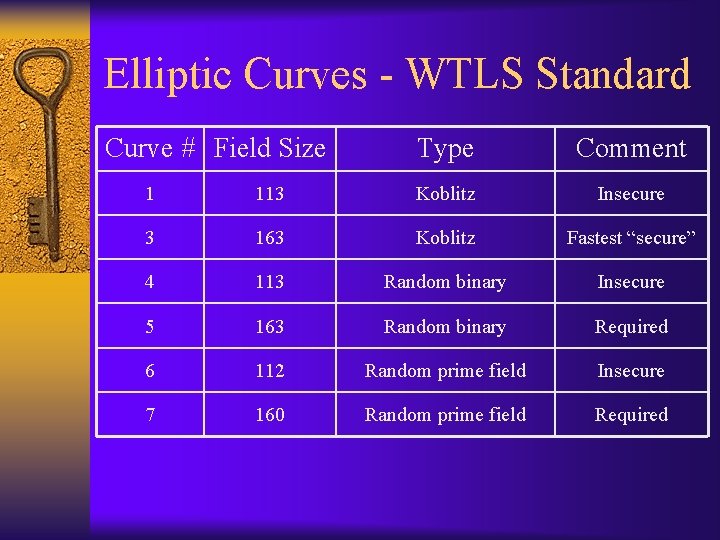
Elliptic Curves - WTLS Standard Curve # Field Size Type Comment 1 113 Koblitz Insecure 3 163 Koblitz Fastest “secure” 4 113 Random binary Insecure 5 163 Random binary Required 6 112 Random prime field Insecure 7 160 Random prime field Required

Execution time on a Cellular Phone Processing power available for cryptographic functions: • Varies depending on system and manufacturer • 50% to 90% taken for call processing • Varies depending on signal conditions • More call processing needed under low signal conditions Total execution time for class 3 security functions can range from < 1 sec for fast Elliptic Curve to > 10 sec for RSA/DH implementations under weak signal conditions. Hardware support can increase speed up to 10 times

RSA Implementation Techniques Used ¨ Montgomery multiplication ¨ Windowing for large exponent calculations ¨ Chinese Remainder Theorem (CRT) for private key calculations ¨ Small (216 + 1) public key ¨ No hand-coded assembly language

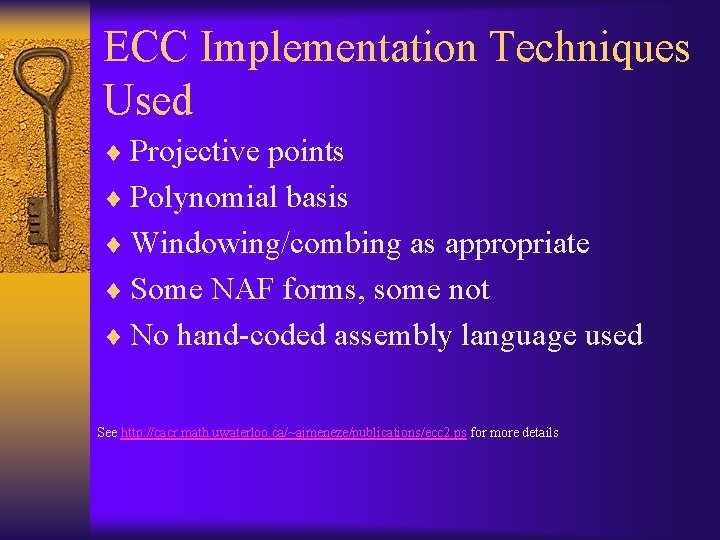
ECC Implementation Techniques Used ¨ Projective points ¨ Polynomial basis ¨ Windowing/combing as appropriate ¨ Some NAF forms, some not ¨ No hand-coded assembly language used See http: //cacr. math. uwaterloo. ca/~ajmeneze/publications/ecc 2. ps for more details

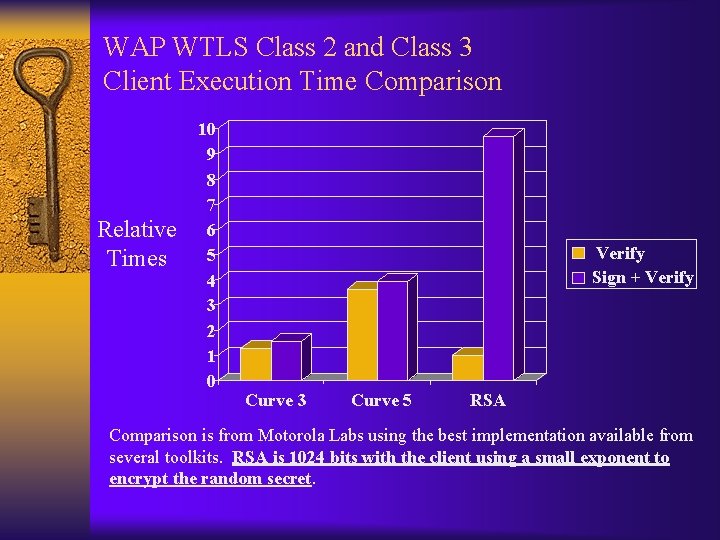
WAP WTLS Class 2 and Class 3 Client Execution Time Comparison Relative Times 10 9 8 7 6 5 4 3 2 1 0 Verify Sign + Verify Curve 3 Curve 5 RSA Comparison is from Motorola Labs using the best implementation available from several toolkits. RSA is 1024 bits with the client using a small exponent to encrypt the random secret.

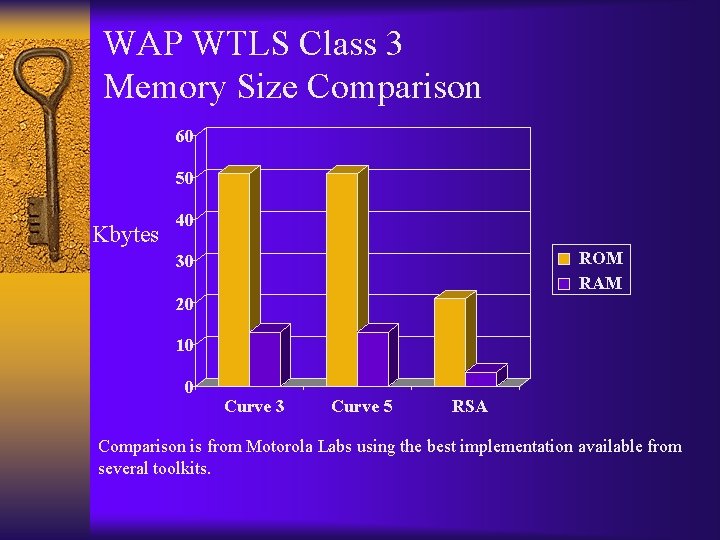
WAP WTLS Class 3 Memory Size Comparison 60 50 Kbytes 40 ROM RAM 30 20 10 0 Curve 3 Curve 5 RSA Comparison is from Motorola Labs using the best implementation available from several toolkits.

Other Algorithms ¨ NTRU, Arithmetica, XTR, HECC, braid groups, etc. ¨ Trying to get a foothold in standards/business – Only NTRU seems to be having any success ¨ Questions of security ¨ Hard to find/make good benchmarks – Biased sources – Algorithms change – Good optimization is a lengthy process

Future Considerations ¨ RSA has more momentum ¨ Patent issues could loom large ¨ Moore’s law and advances in algorithms suggest current key sizes will be inadequate in the future ¨ Doubling an RSA or an ECC key size multiplies the processing time by ~8 ¨ However, doubling an ECC key size adds more security than doubling an RSA key size – |E| = 320 probably more secure than |n| = 2048 – This implies ECC might have a future advantage

Future Considerations (Cont) ¨ Advances in factoring vs. advances in ECDLP – Both problems are pretty old mathematically – Businesses (with their $$$) have considered factoring – – – longer Community working on factoring appears to be larger Took years of study before “good” factoring algorithms (EC, QS, NFS, GNFS) were found Few real advances to date against ECC Problems are related Quantum algorithms exist for both ¨ Very hard to predict

Other Issues ¨ Scaling of servers in class 2 is easier with ECC ¨ Other speed/code size trade-offs are possible ¨ Key generation easier for ECC (using standardized curves) ¨ Signature sizes are smaller for ECC than with RSA