Practical OrderRevealing Encryption with Limited Leakage Nathan Chenette

![Order-Revealing Encryption [BRLSZZ 15] Client Server secret-key encryption scheme Order-Revealing Encryption [BRLSZZ 15] Client Server secret-key encryption scheme](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-2.jpg)
![Order-Revealing Encryption [BRLSZZ 15] Server Application: range queries / binary search on encrypted data Order-Revealing Encryption [BRLSZZ 15] Server Application: range queries / binary search on encrypted data](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-3.jpg)
![Order-Revealing Encryption [BRLSZZ 15] given any two ciphertexts there is a publically evaluatable function Order-Revealing Encryption [BRLSZZ 15] given any two ciphertexts there is a publically evaluatable function](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-4.jpg)
![Defining Security Starting point: semantic security (IND-CPA) [GM 84] challenger adversary Defining Security Starting point: semantic security (IND-CPA) [GM 84] challenger adversary](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-5.jpg)
![Best-Possible Security [BCLO 09] must impose restriction on messages: otherwise trivial to break semantic Best-Possible Security [BCLO 09] must impose restriction on messages: otherwise trivial to break semantic](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-6.jpg)
![Best-Possible Security [BCLO 09] Best-Possible Security [BCLO 09]](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-7.jpg)
![Best-Possible Security [BCLO 09] order of “left” set of messages same as order of Best-Possible Security [BCLO 09] order of “left” set of messages same as order of](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-8.jpg)

![Existing Approaches Multilinear-map-based Solution [BRLSZZ 15] • • Much more efficient than general purpose Existing Approaches Multilinear-map-based Solution [BRLSZZ 15] • • Much more efficient than general purpose](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-10.jpg)
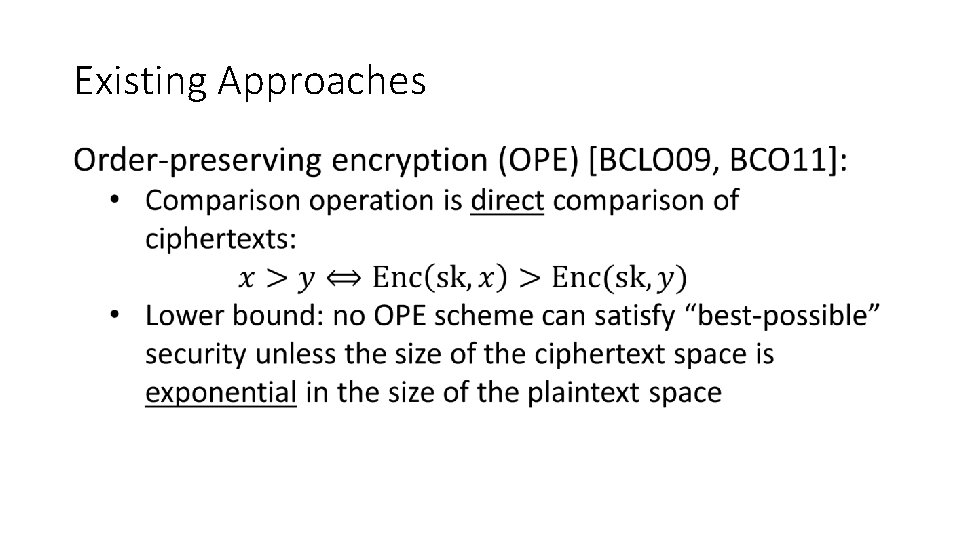
![Existing Approaches Order-preserving encryption (OPE) [BCLO 09, BCO 11]: • No “best-possible” security, so Existing Approaches Order-preserving encryption (OPE) [BCLO 09, BCO 11]: • No “best-possible” security, so](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-12.jpg)
![Existing Approaches Properties of a random order-preserving function [BCO’ 11]: • • Each ciphertext Existing Approaches Properties of a random order-preserving function [BCO’ 11]: • • Each ciphertext](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-13.jpg)






- Slides: 38

Practical Order-Revealing Encryption with Limited Leakage Nathan Chenette, Kevin Lewi, Stephen A. Weis, and David J. Wu Fast Software Encryption March, 2016
![OrderRevealing Encryption BRLSZZ 15 Client Server secretkey encryption scheme Order-Revealing Encryption [BRLSZZ 15] Client Server secret-key encryption scheme](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-2.jpg)
Order-Revealing Encryption [BRLSZZ 15] Client Server secret-key encryption scheme
![OrderRevealing Encryption BRLSZZ 15 Server Application range queries binary search on encrypted data Order-Revealing Encryption [BRLSZZ 15] Server Application: range queries / binary search on encrypted data](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-3.jpg)
Order-Revealing Encryption [BRLSZZ 15] Server Application: range queries / binary search on encrypted data
![OrderRevealing Encryption BRLSZZ 15 given any two ciphertexts there is a publically evaluatable function Order-Revealing Encryption [BRLSZZ 15] given any two ciphertexts there is a publically evaluatable function](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-4.jpg)
Order-Revealing Encryption [BRLSZZ 15] given any two ciphertexts there is a publically evaluatable function that evaluates the comparison function
![Defining Security Starting point semantic security INDCPA GM 84 challenger adversary Defining Security Starting point: semantic security (IND-CPA) [GM 84] challenger adversary](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-5.jpg)
Defining Security Starting point: semantic security (IND-CPA) [GM 84] challenger adversary
![BestPossible Security BCLO 09 must impose restriction on messages otherwise trivial to break semantic Best-Possible Security [BCLO 09] must impose restriction on messages: otherwise trivial to break semantic](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-6.jpg)
Best-Possible Security [BCLO 09] must impose restriction on messages: otherwise trivial to break semantic security using comparison operator
![BestPossible Security BCLO 09 Best-Possible Security [BCLO 09]](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-7.jpg)
Best-Possible Security [BCLO 09]
![BestPossible Security BCLO 09 order of left set of messages same as order of Best-Possible Security [BCLO 09] order of “left” set of messages same as order of](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-8.jpg)
Best-Possible Security [BCLO 09] order of “left” set of messages same as order of “right” set of messages

Existing Approaches
![Existing Approaches Multilinearmapbased Solution BRLSZZ 15 Much more efficient than general purpose Existing Approaches Multilinear-map-based Solution [BRLSZZ 15] • • Much more efficient than general purpose](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-10.jpg)
Existing Approaches Multilinear-map-based Solution [BRLSZZ 15] • • Much more efficient than general purpose indistinguishability obfuscation Achieves best-possible security Security of multilinear maps not well-understood Still quite inefficient (e. g. , ciphertexts on the order of GB)

Existing Approaches
![Existing Approaches Orderpreserving encryption OPE BCLO 09 BCO 11 No bestpossible security so Existing Approaches Order-preserving encryption (OPE) [BCLO 09, BCO 11]: • No “best-possible” security, so](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-12.jpg)
Existing Approaches Order-preserving encryption (OPE) [BCLO 09, BCO 11]: • No “best-possible” security, so instead, compare with random order-preserving function (ROPF) encryption function implements a random order-preserving function domain range
![Existing Approaches Properties of a random orderpreserving function BCO 11 Each ciphertext Existing Approaches Properties of a random order-preserving function [BCO’ 11]: • • Each ciphertext](https://slidetodoc.com/presentation_image_h/b80fb2a9182006b6d56c2901ce0dfae1/image-13.jpg)
Existing Approaches Properties of a random order-preserving function [BCO’ 11]: • • Each ciphertext roughly leaks half of the most significant bits Each pair of ciphertexts roughly leaks half of the most significant bits of their difference No semantic security for even a single message!

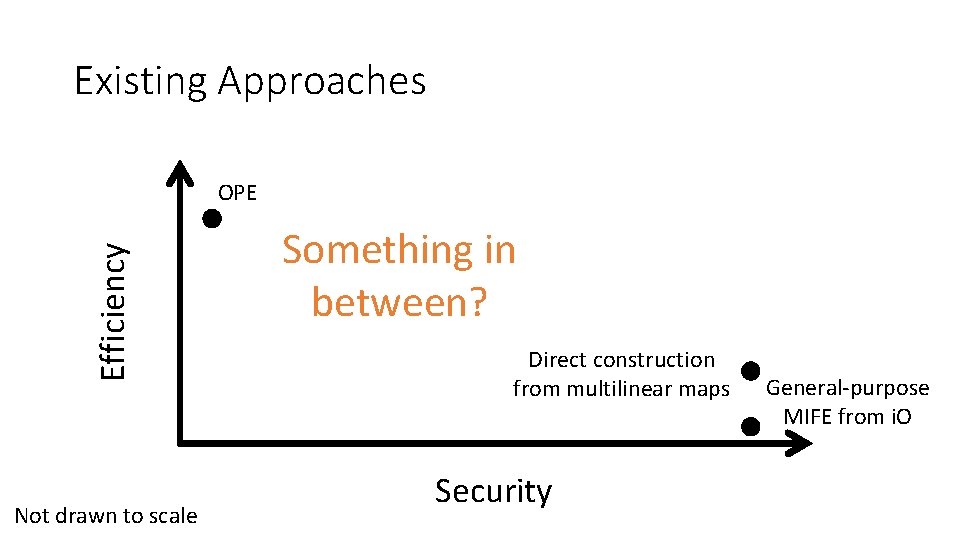
Existing Approaches Efficiency OPE Not drawn to scale Something in between? Direct construction from multilinear maps Security General-purpose MIFE from i. O

A New Security Notion Two existing security notions: • • IND-OCPA: strong security, but hard to achieve efficiently ROPF-CCA: efficiently constructible, but lots of leakage, and difficult to precisely quantify the leakage

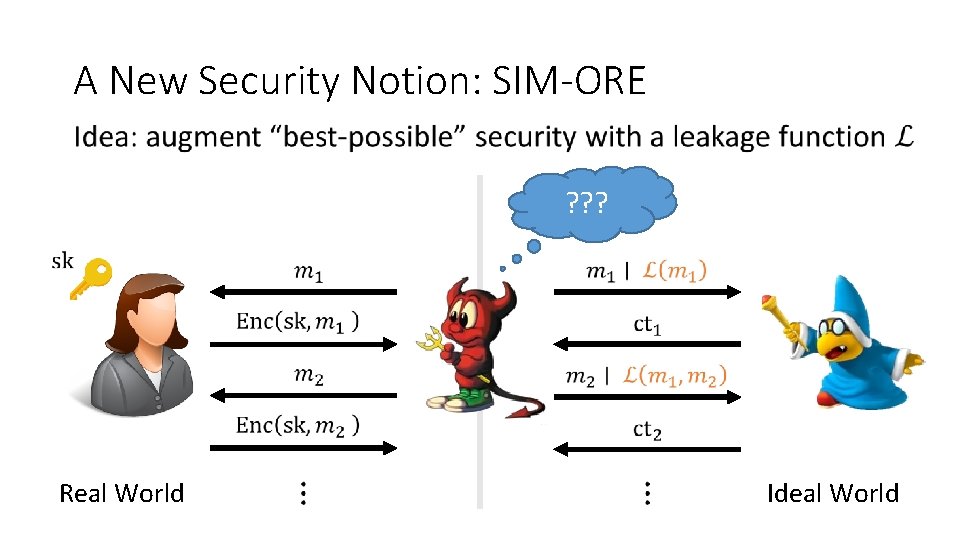
A New Security Notion: SIM-ORE ? ? ? Real World Ideal World

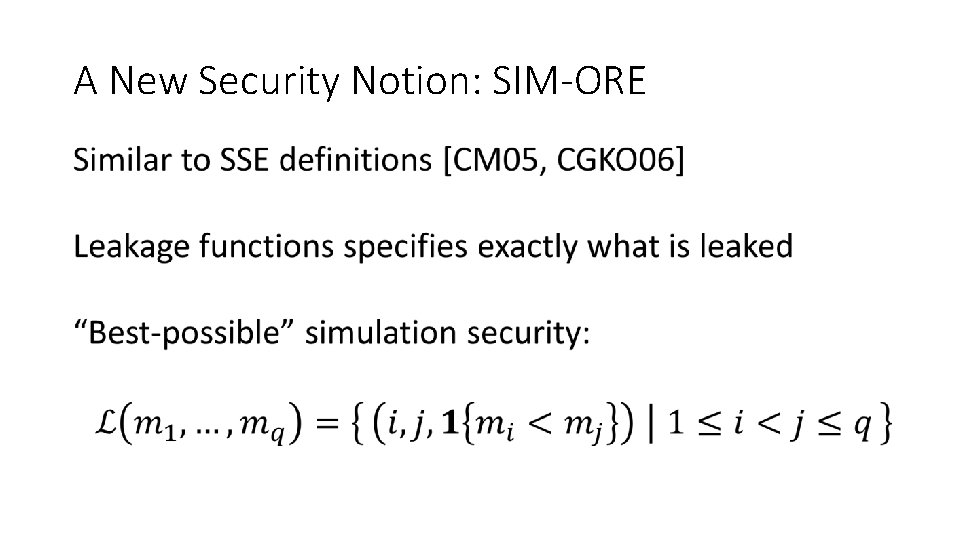
A New Security Notion: SIM-ORE

A New Security Notion: SIM-ORE

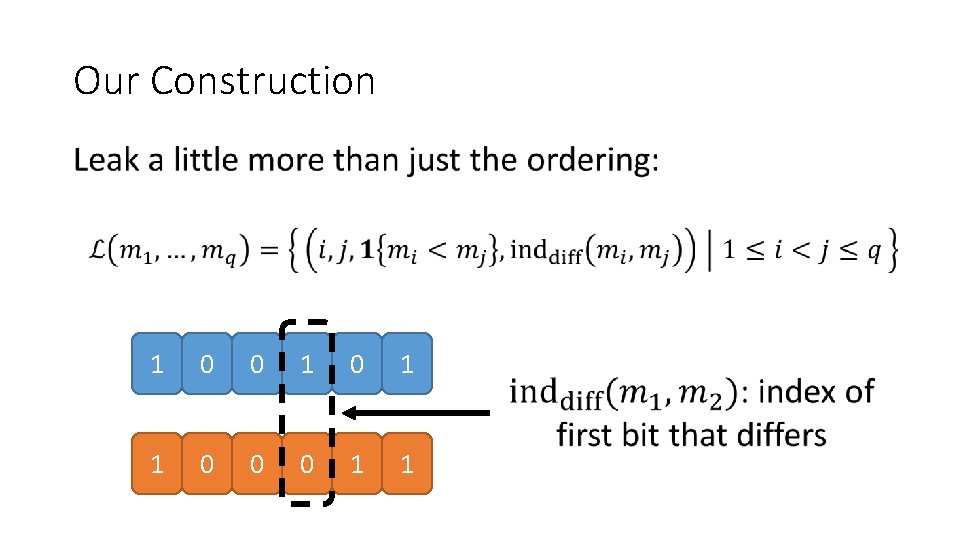
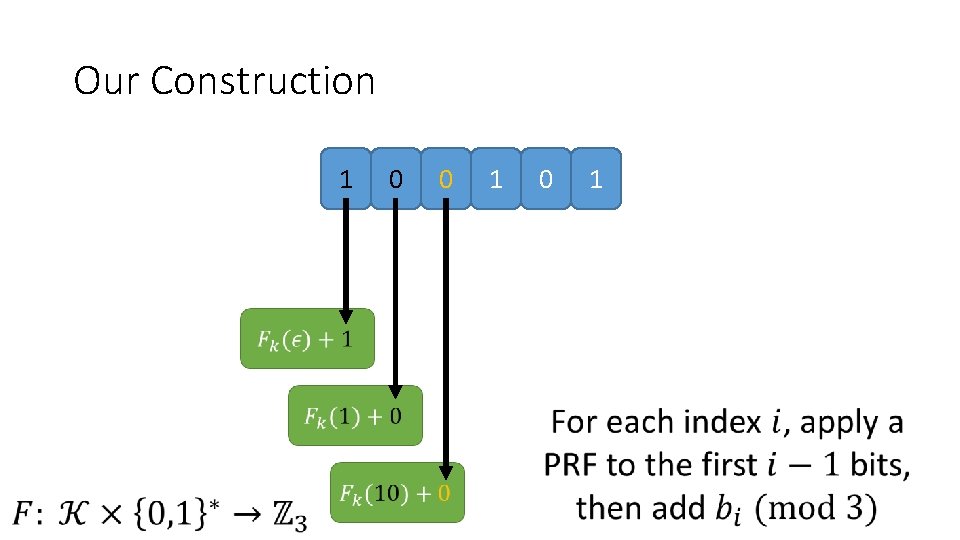
Our Construction 1 0 0 1 1 0 0 0 1 1

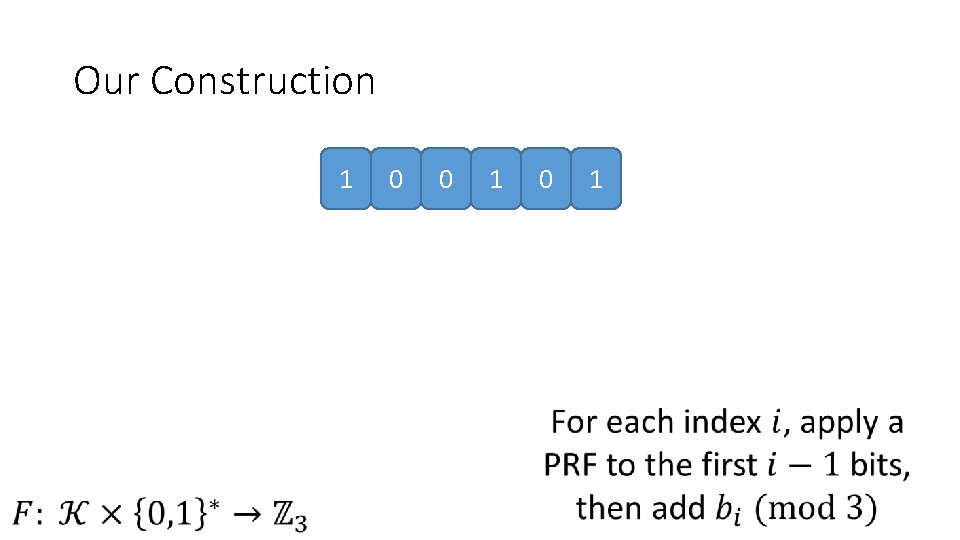
Our Construction 1 0 0 1

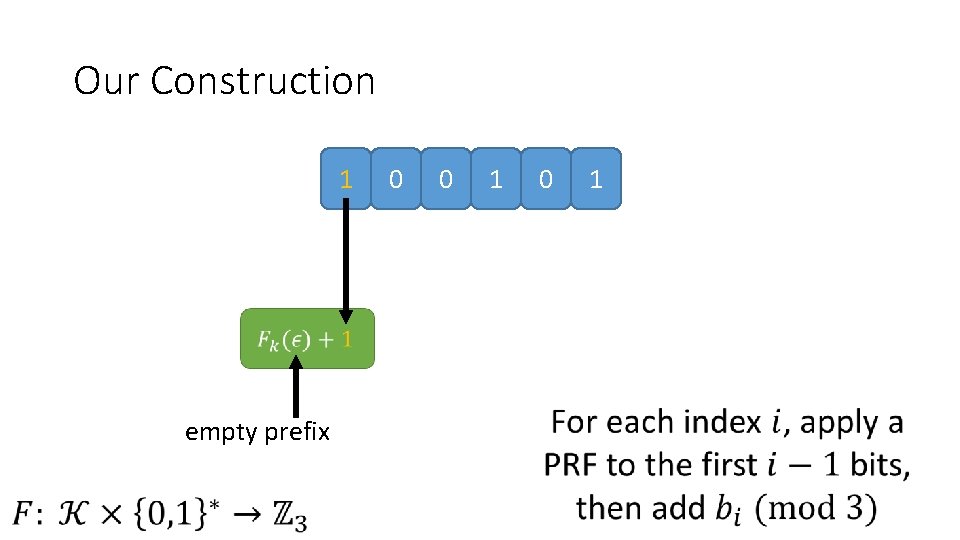
Our Construction 1 0 0 1 0 empty prefix 1

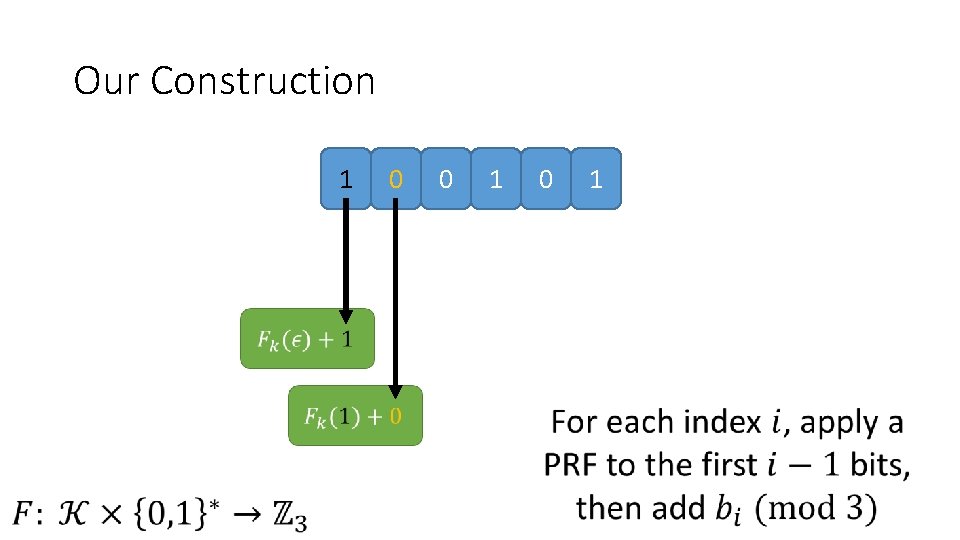
Our Construction 1 0 0 1 0 1

Our Construction 1 0 0 1 0 1

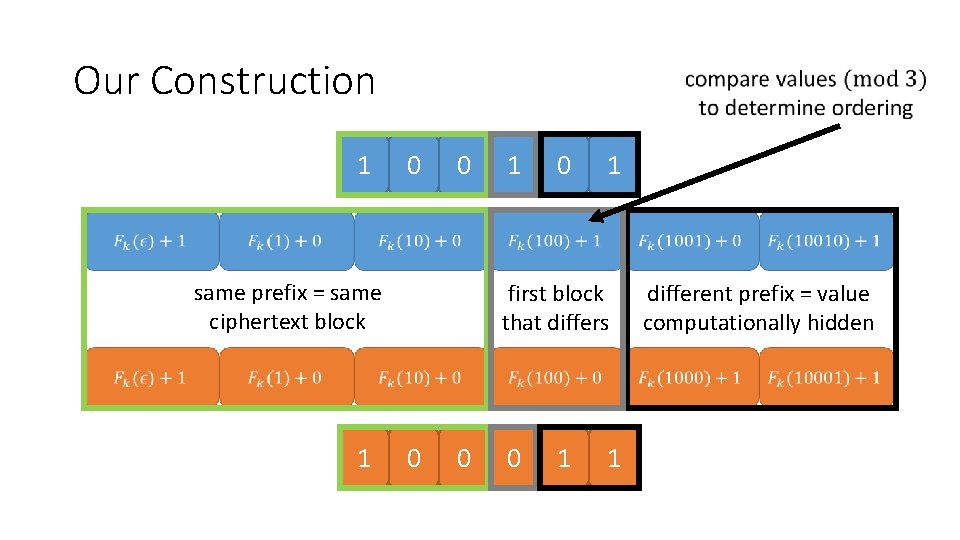
Our Construction 1 0 0 1 first block that differs 1 0 same prefix = same ciphertext block 1 0 0 different prefix = value computationally hidden 0 1 1

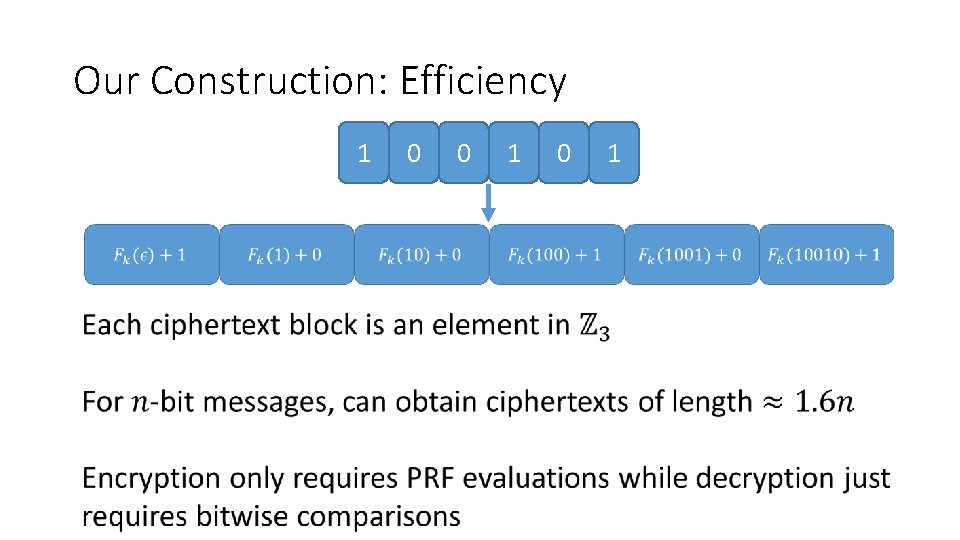
Our Construction: Efficiency 1 0 0 1

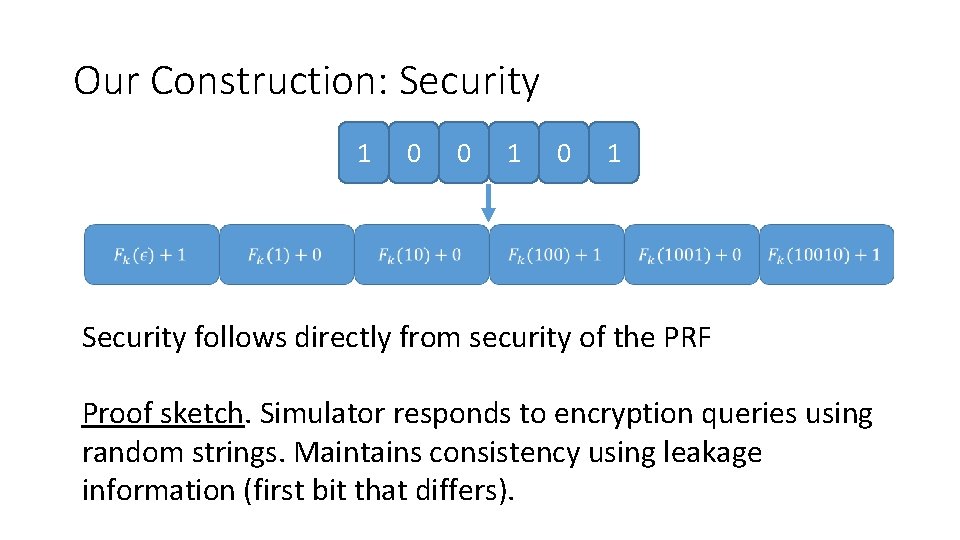
Our Construction: Security 1 0 0 1 Security follows directly from security of the PRF Proof sketch. Simulator responds to encryption queries using random strings. Maintains consistency using leakage information (first bit that differs).

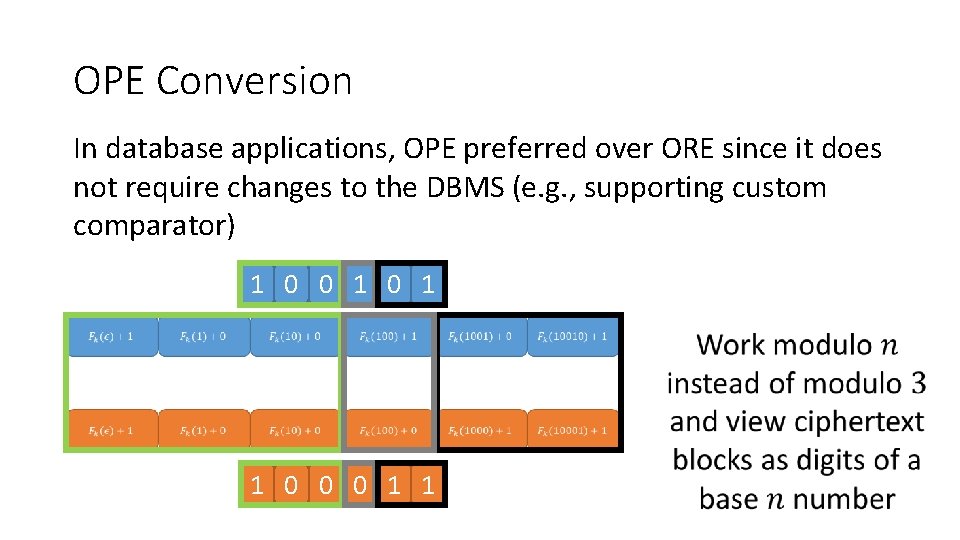
OPE Conversion In database applications, OPE preferred over ORE since it does not require changes to the DBMS (e. g. , supporting custom comparator) 1 0 0 1 1 0 0 0 1 1

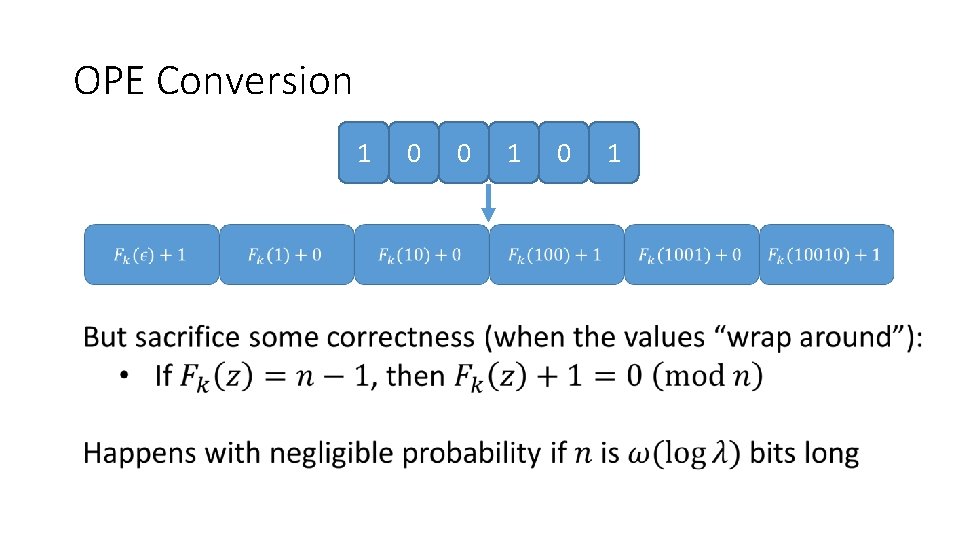
OPE Conversion 1 0 0 1

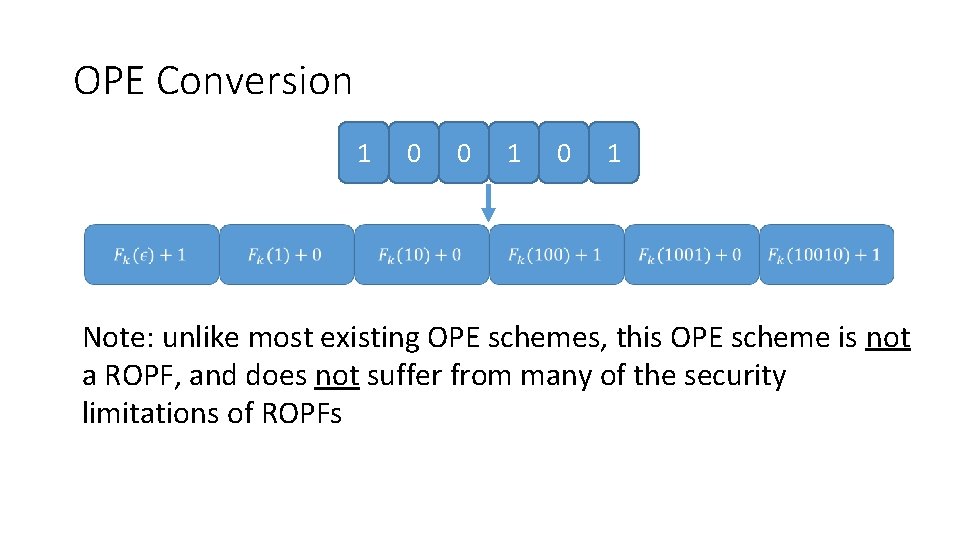
OPE Conversion 1 0 0 1 Note: unlike most existing OPE schemes, this OPE scheme is not a ROPF, and does not suffer from many of the security limitations of ROPFs

Comparison to Previous OPE Schemes

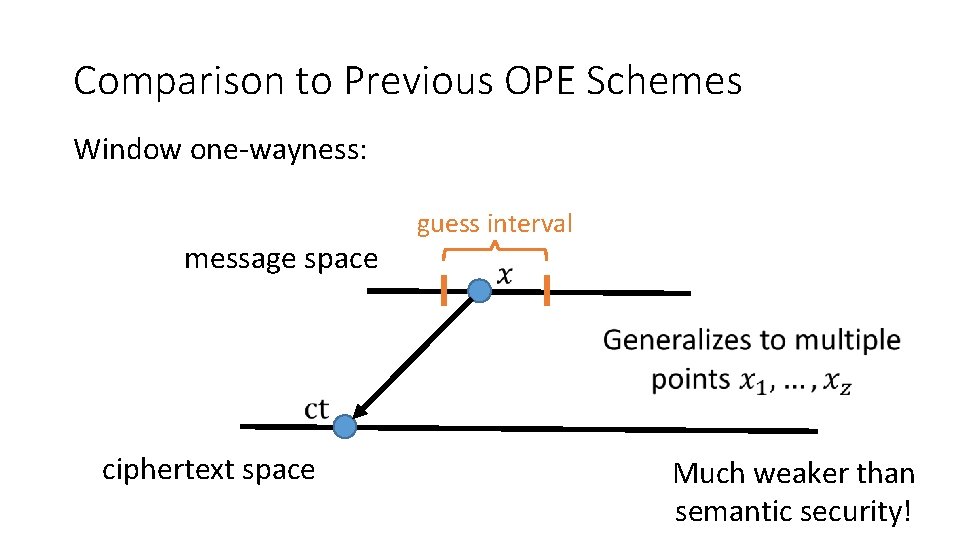
Comparison to Previous OPE Schemes Window one-wayness: message space guess interval ciphertext space Much weaker than semantic security!

Comparison to Previous OPE Schemes

Comparison to Previous OPE Schemes

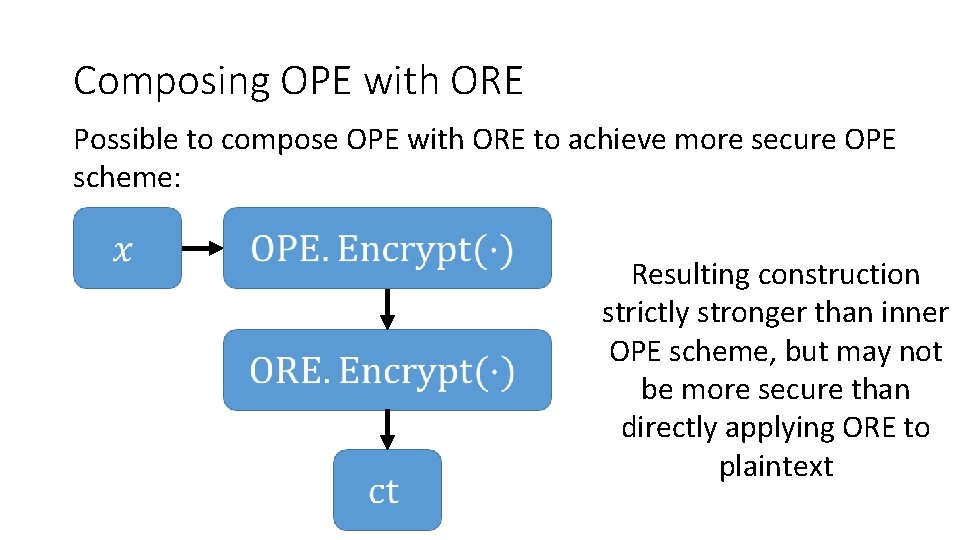
Composing OPE with ORE Possible to compose OPE with ORE to achieve more secure OPE scheme: Resulting construction strictly stronger than inner OPE scheme, but may not be more secure than directly applying ORE to plaintext

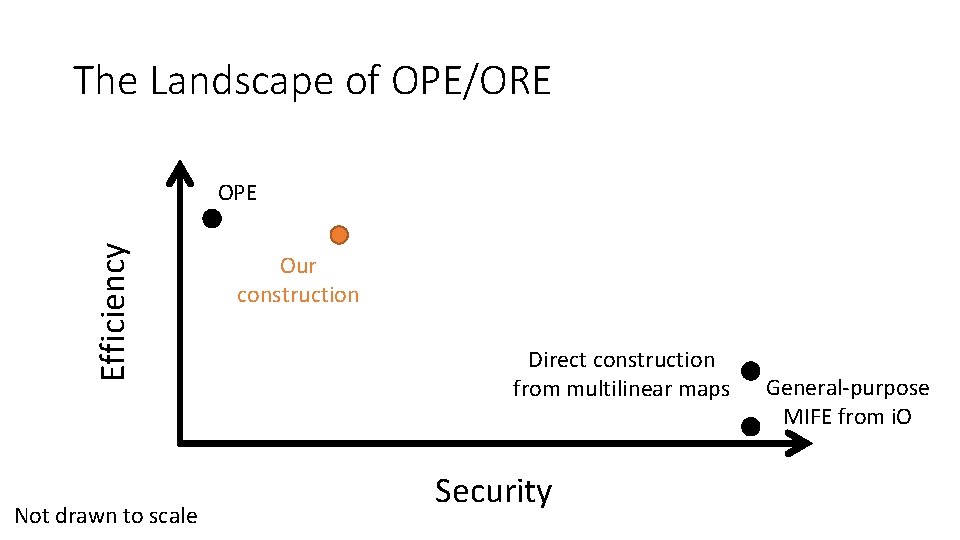
The Landscape of OPE/ORE Efficiency OPE Not drawn to scale Our construction Direct construction from multilinear maps Security General-purpose MIFE from i. O

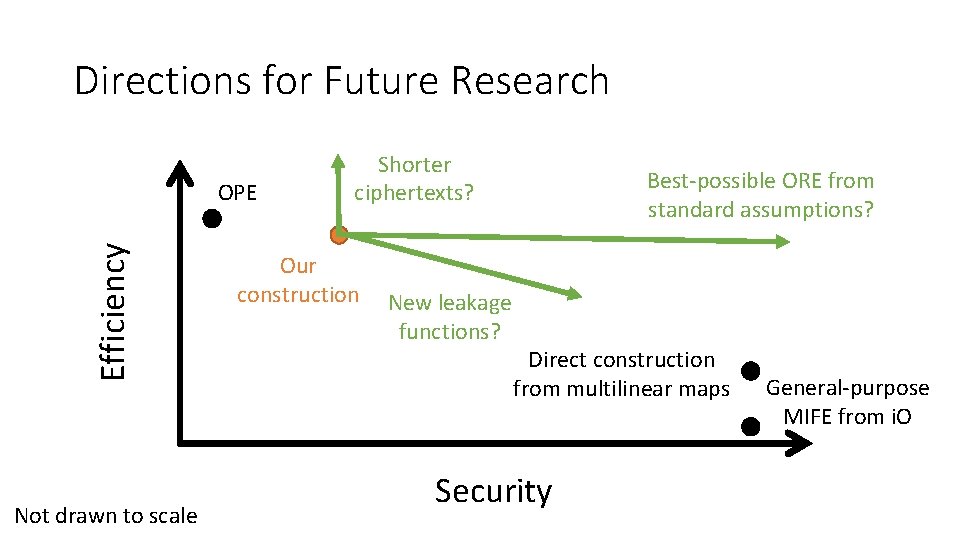
Directions for Future Research Efficiency OPE Not drawn to scale Shorter ciphertexts? Our construction Best-possible ORE from standard assumptions? New leakage functions? Direct construction from multilinear maps Security General-purpose MIFE from i. O

Sample Implementation: https: //github. com/kevinlewi/fastore Project Website: https: //crypto. stanford. edu/ore/

Questions? http: //eprint. iacr. org/2015/1125