Practical exercise 2 Stakeholder analysis Exercise overview Emails






- Slides: 13

Practical exercise 2 Stakeholder analysis

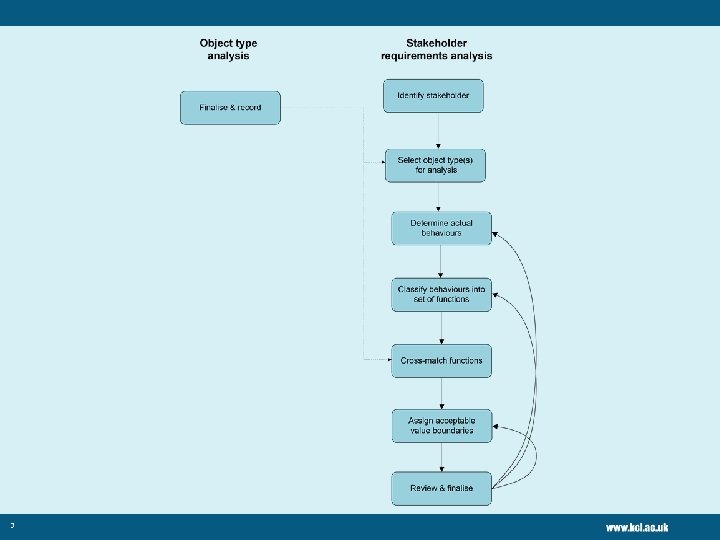
Exercise overview • Emails • Consider needs of different stakeholders – The creators of the resource – Repository manager as its curator – Users of the resource • Apply FBS-based analysis from In. SPECT method – Identify actual behaviours – Turn behaviours into functions – Express results as technical properties – Cross-match properties to those from Object Analysis 2

3

Identify Stakeholders • Creator – view, annotate • Researcher corresponds during research with colleagues, peers, administrators etc. • Recipient – reuses content • Student wants to understand research lifecycles by studying real-world practice • Custodian – evidential chain • Maintains permanent email record for externallyfunded projects, alongside data and eprint outputs 4

Select object type for analysis • Emails from Object Analysis phase 5

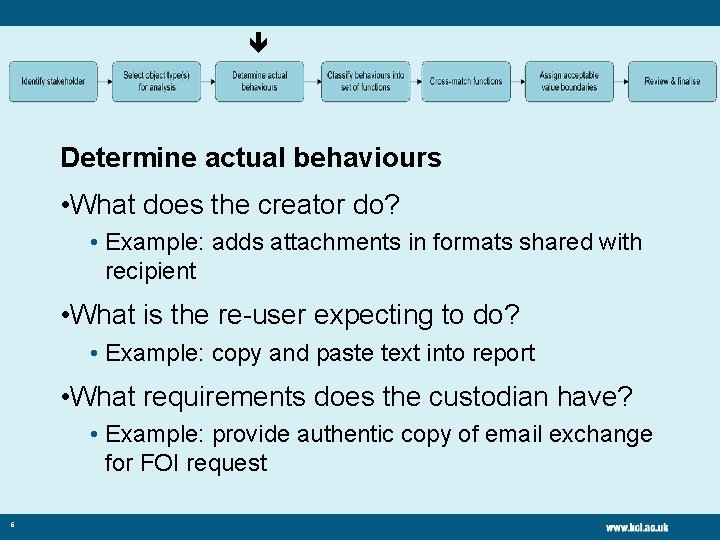
Determine actual behaviours • What does the creator do? • Example: adds attachments in formats shared with recipient • What is the re-user expecting to do? • Example: copy and paste text into report • What requirements does the custodian have? • Example: provide authentic copy of email exchange for FOI request 6

Determine actual behaviours - practical • Split into groups • Identify 2 -5 behaviours for each stakeholder • There may be repetition across stakeholders • 10 mins 7

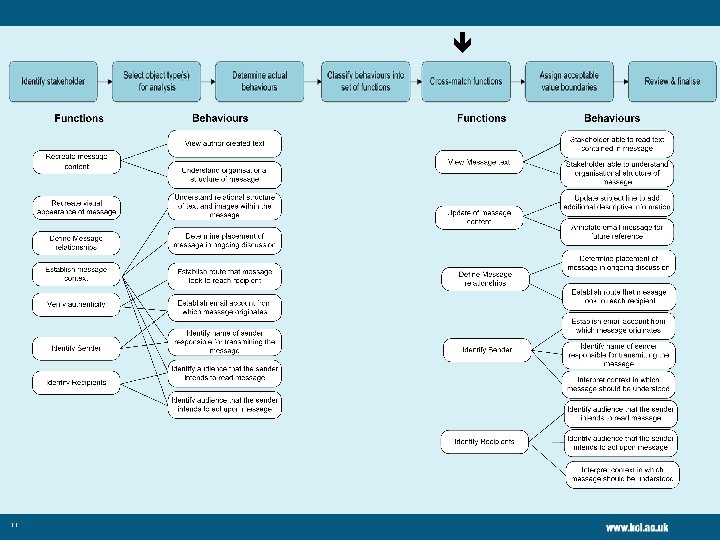
Classify behaviours into set of functions Taking your behaviours from the exercise, we turn them into functions e. g. “Know that emails were sent/received with attachments” >> “Identify association of attachments” (Category: structure) 8

9

Cross-match functions • Which functions can you see match those from the Object Analysis stage? 10

11

Assign acceptable value boundaries • This stage might not be needed in all cases • An example from audio files is loss of stereo channels – that might be acceptable to some users (e. g. oral historians) but not for others (e. g. musicians) • What might your various stakeholders accept? 12

Review and finalise • What behaviours did you determine for the different stakeholders? • What functions did you identify? • What correlation between object and stakeholder properties? • This process may be iterative in the real world, and repeated for a new/changed Designated Community or Archive 13