PPP Point to Point ProtocolRFC 1661 Overview Layer







- Slides: 9

PPP Point to Point Protocol(RFC 1661)

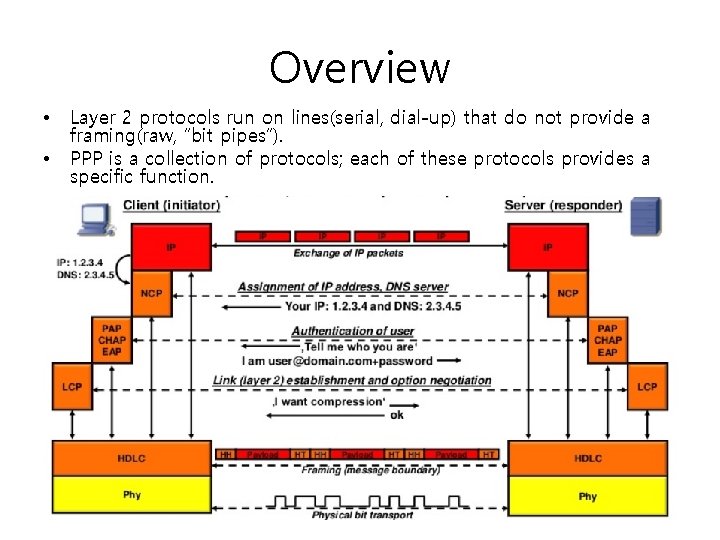
Overview • • Layer 2 protocols run on lines(serial, dial-up) that do not provide a framing(raw, “bit pipes”). PPP is a collection of protocols; each of these protocols provides a specific function.

SLIP(Serial line IP, RFC 1055) versus PPP • SLIP was used as framing protocol over serial lines before the advent of PPP. • SLIP framing: – Frame delimiter : The byte 0 xc 0 serves as frame delimiter. – Transparency : 0 xdb, 0 xdc is used as escape sequence for 0 xc 0 in payload • 0 xc 0 in payload becomes 0 xdb 0 xdc in SLIP frame. • 0 xdb in payload becomes 0 xdb 0 xdd in SLIP frame. • SLIP has some deficiencies : – SLIP does not have error detection mechanism(left to TCP to detect and recover from errors on the transmission line). – SLIP only supports IP(no other layer 3 protocols) – SLIP does not provide dynamic IP address assignment. – SLIP does not provide authentication. • PPP was devised in order to overcome the deficiencies of SLIP.

PPP protocol features • PPP is not a single protocol but a protocol suite and consists of • • PPP affords error detection(checksum). PPP allows to dynamically assign an IP address(NCP). PPP provides authentication(PAP/CHAP). PPP is a symmetric protocol : the 2 parties in a PPP session are the Initiator(I, usually client) and the responder(R, usually server). – Framing method(frame/ packet delineation) : serial lines provide bit transport, thus a means for finding the start of packet is required. – Link control protocol(LCP) : LCP is used for establishing a data link including options for the operation. – Network control protocol(NCP) : each network protocol, e. g. IP, has it’s own NCP for establishing and configuring the network-layer operation. – Authentication protocols(CHAP, PAP, EAP) : Client(and optional server) authentication make sure the right communication partners talk to each other. – Encryption protocols(ECP, DES, AES 등) for privacy. – Bandwidth control(BACP) : “Bonding” of multiple channels(Multilink PPP-MLPPP) to provide more bandwidth. – Compression control(CCP) : serial line are usually comparably slow. Compression provides more throughput.

PPP protocol stack • • CCP : Compression control protocol – Negotiation and control of compression on both ends of link IPCP control protocol – is a NCP – • • Establishment of IP on both ends of Point to point link(mainly assignment of IP address, default gateway and DNS server from responder to initiation) BCP(Bridging control protocol) – establishment of bridging modules on both ends of point to point link(similar to IPCP, but instead of routing initializes bridging). BAP/BACP(Bandwidth allocation control protocol) – BAP/BACP can be used to add/remove individual links in a multi-link bundle(Multilink PPP). ECP(Encryption control protocol) – Configuring and enabling of encryption on both ends of the link. CHAP(Challenge authentication protocol) – description see below PAP(Password authentication protocol) – description see below EAP(Extension authentication protocol) – Protocol supporting a range of authentication algorithms/ protocols LCP(Link control protocol) – Negotiation and control of link parameters on both ends(MRU Max, Receive Unit, Header compression, Encapsulation). LQR(Link quality report) – Monitoring of link quality.

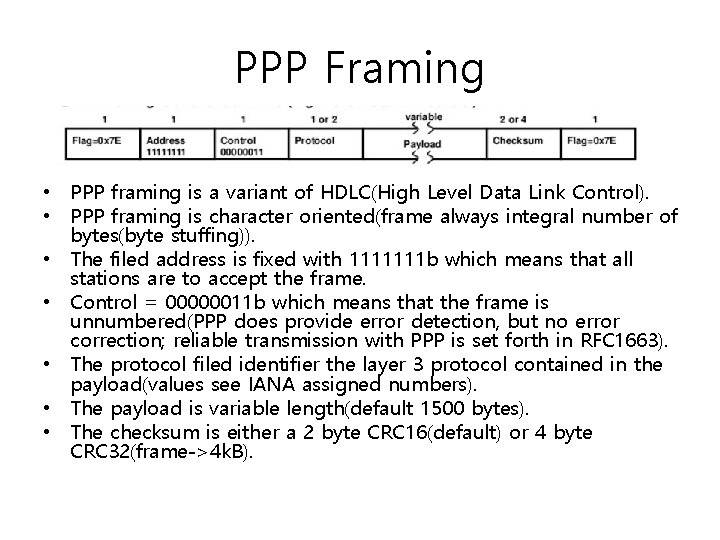
PPP Framing • PPP framing is a variant of HDLC(High Level Data Link Control). • PPP framing is character oriented(frame always integral number of bytes(byte stuffing)). • The filed address is fixed with 1111111 b which means that all stations are to accept the frame. • Control = 00000011 b which means that the frame is unnumbered(PPP does provide error detection, but no error correction; reliable transmission with PPP is set forth in RFC 1663). • The protocol filed identifier the layer 3 protocol contained in the payload(values see IANA assigned numbers). • The payload is variable length(default 1500 bytes). • The checksum is either a 2 byte CRC 16(default) or 4 byte CRC 32(frame->4 k. B).

LCP and NCP • LCP(Link Control Protocol) : – Used for establishing the link. – Allows to negotiate link options(authentication protocol to be used. Header compression/address field compression. MRU(maximum receive unit). – Periodically test the link(LCP echo request/ reply). – Bring down the link gracefully when no longer in use. • NCP(Network control protocol) : – Dynamic assignment of IP address. – Dynamic assignment of DNS primary and secondary server. – The host set a default route to the PPP interface since there is no default gateway IP address(the link is point-to-point with no IP address = unnumbered).

Typical PPP session

PPP authentication • PAP and CHAP are used for authentication with PPP(is the one I am talking to the one he pretends to be? ). PAP RFC 1661, Password authentication protocol: • CHAP RFC 1994, Challenge handshake authentication protocol: • – PAP simply sends a username and password(cleartext) to the remote computer. – Thus PAP is considered insecure. – PAP is symmetric and does not allow asymmetric settings with an authenticator and a peer(authenticator authenticates peer). – With CHAP an authenticator(usually server) authenticates a peer(usually client); thus CHAP is asymmetric. – CHAP Procedure: • • • Authenticator computes random value(=challenge) Authenticator sends challenge(random value to foil replay attacks) to peer. Peer computes a hash(MD 5) value on identifier(username), secret(password) and challenge. Peer sends hash value to authenticator. Authenticator performs the same calculation and checks if the result is ok. – CHAP trace see PPP trace above.