Power BI Compliance This is a Header Michael

Power BI Compliance This is a Header Michael Askins THIS IS A SUBTITLE

s This is a Header THIS IS A SUBTITLE eht st htiw
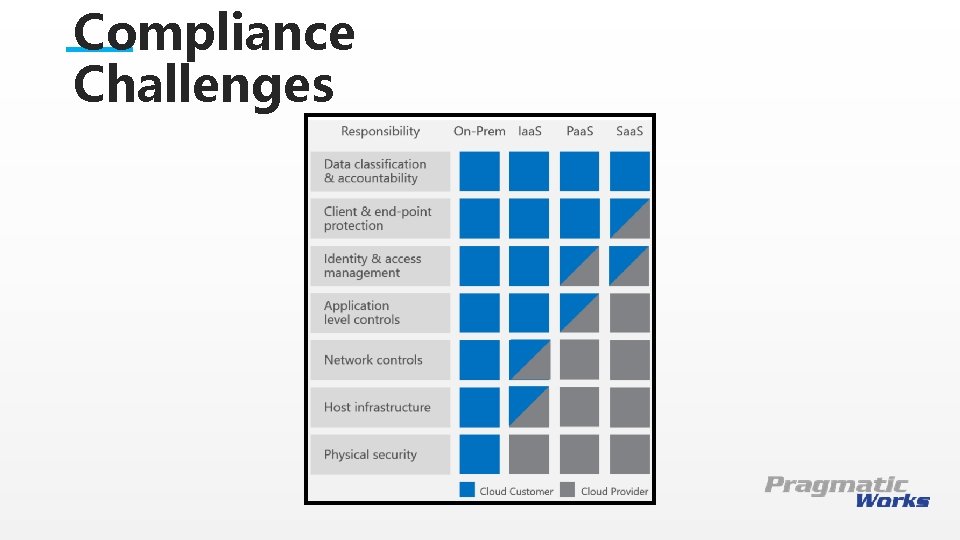
Compliance Challenges This is a Header THIS IS A SUBTITLE
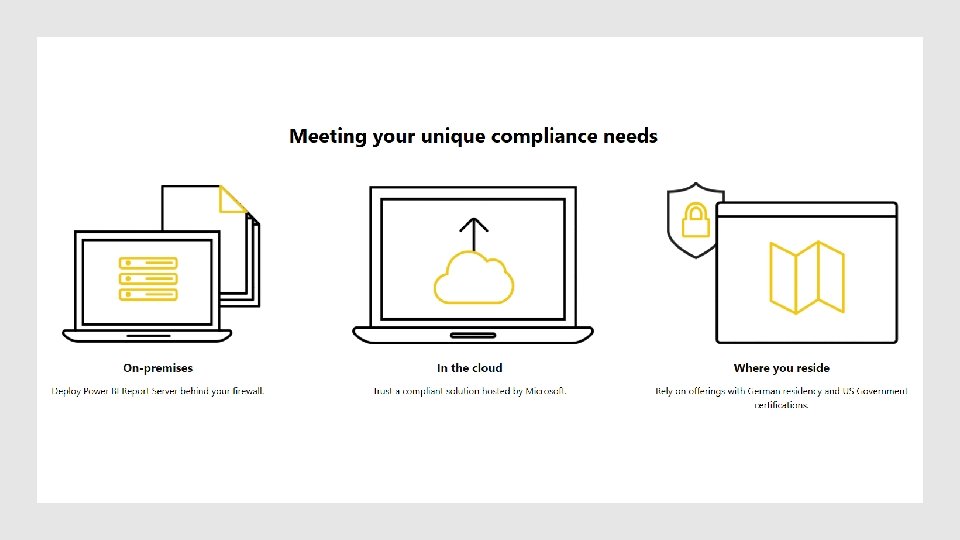
This is a Header THIS IS A SUBTITLE
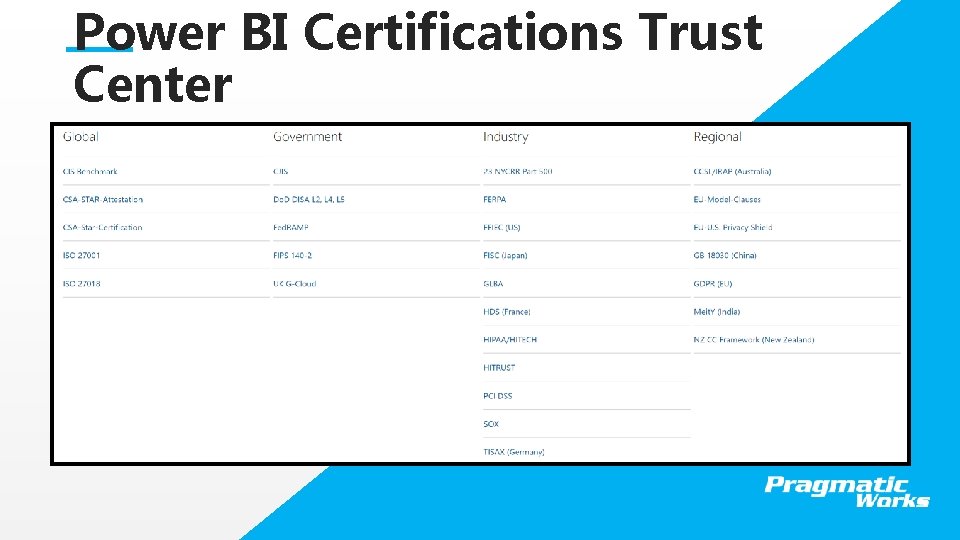
Power BI Certifications Trust Center This is a Header THIS IS A SUBTITLE
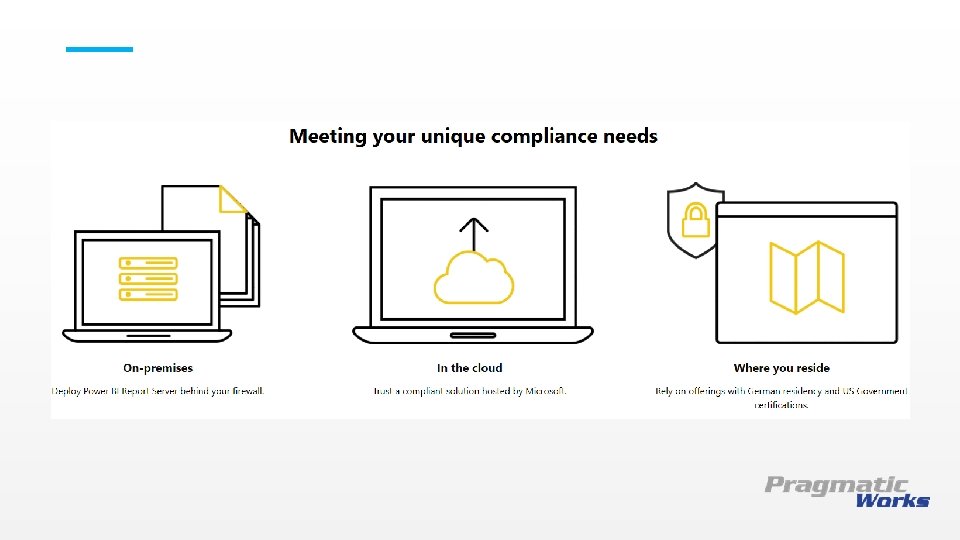
This is a Header THIS IS A SUBTITLE

Power BI On Prem – Power BI Report Server • Enabling Power BI Pro users to publish to an on premises report server to deliver reports org wide on premises or in the cloud • Power BI Report Server • Create reports with Power BI Desktop This is a Header • Your organizations on premises data center compliance policies and procedures apply THIS IS A SUBTITLE • Publish to Power BI Report Server • Governance or Compliance rules that may affect your organization may require a specific need to satisfy a vendor or customer • • Canvas style report building with modern visualizations Manage Access and Report accordingly • Distribute • Share reports to your organization
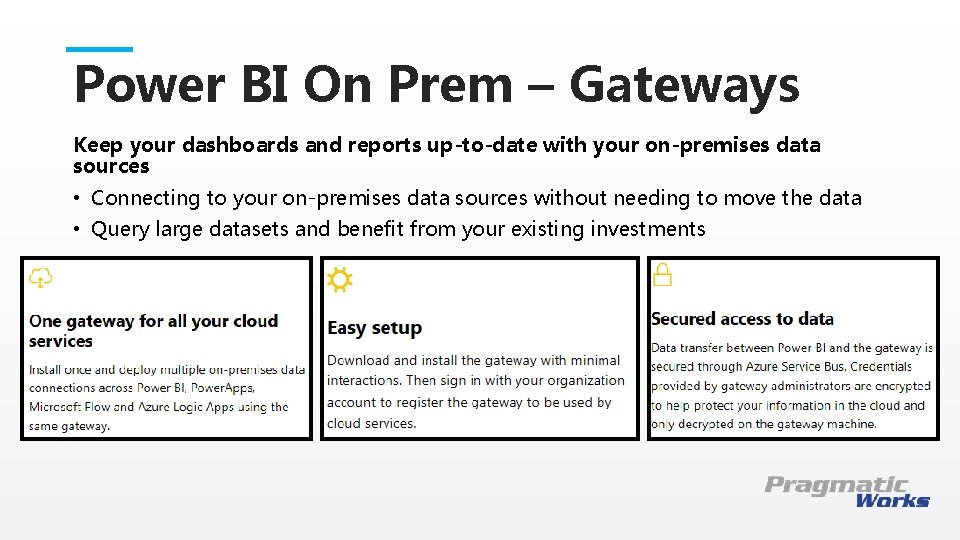
Power BI On Prem – Gateways Keep your dashboards and reports up-to-date with your on-premises data sources • Connecting to your on-premises data sources without needing to move the data • Query large datasets and benefit from your existing investments This is a Header THIS IS A SUBTITLE
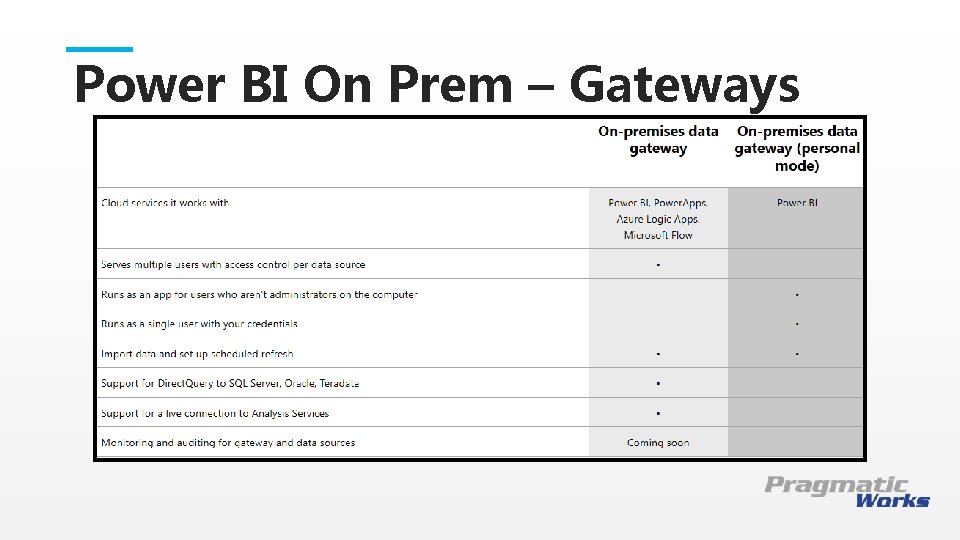
Power BI On Prem – Gateways This is a Header THIS IS A SUBTITLE
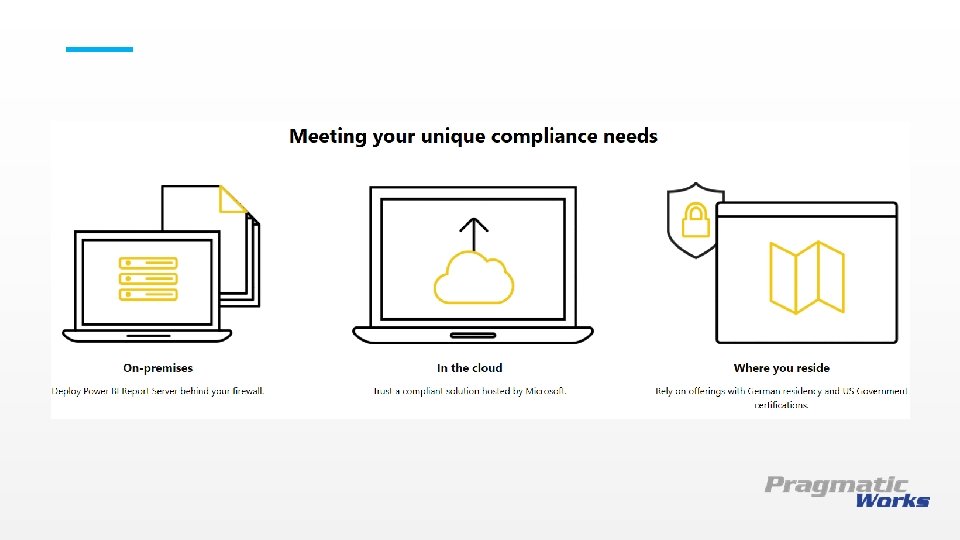
This is a Header THIS IS A SUBTITLE

Power BI in the Cloud Architecture Business application platform services are deployed in datacenters around the world, and each deployment consists of two clusters: • WFE Cluster • Back-End Cluster Users directly interact only with the Gateway role and Azure API Management which are accessible through the internet: • Authentication • Authorization • Distributed denial-of-service (DDo. S) protection • Bandwidth throttling • Load balancing • Routing • Other security, performance, and availability functions This is a Header THIS IS A SUBTITLE There is a distinct boundary between the roles that users can access and the roles that are accessible only by the system.
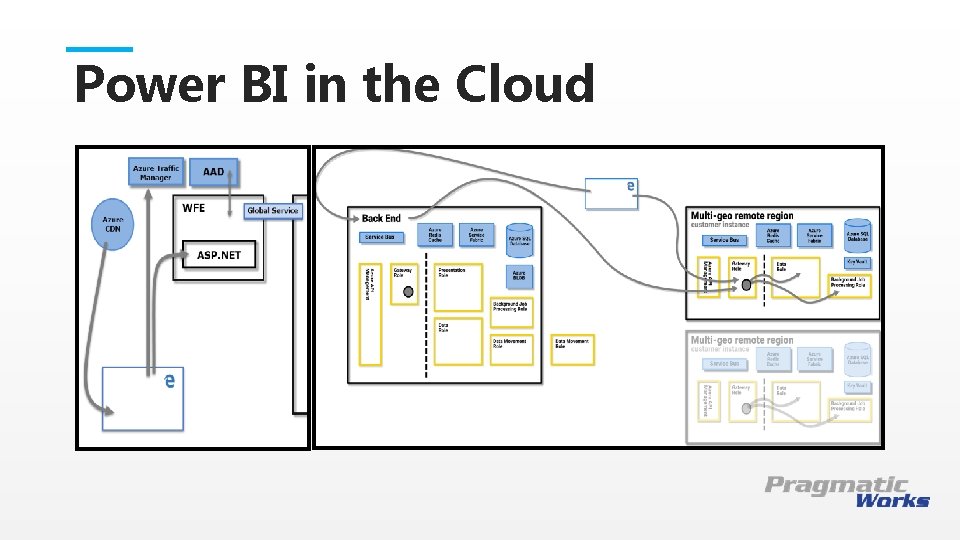
Power BI in the Cloud This is a Header THIS IS A SUBTITLE
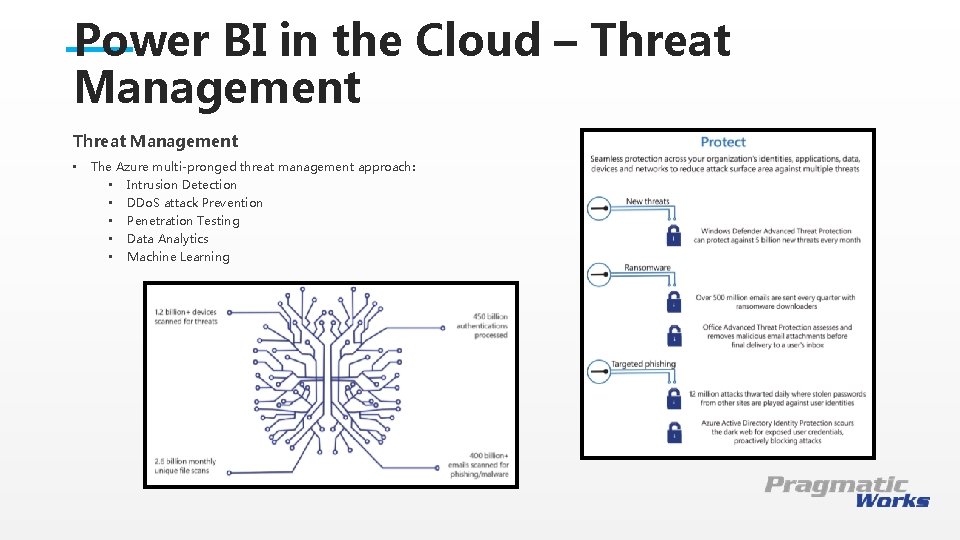
Power BI in the Cloud – Threat Management • The Azure multi-pronged threat management approach: • Intrusion Detection • DDo. S attack Prevention • Penetration Testing • Data Analytics • Machine Learning This is a Header THIS IS A SUBTITLE

Power BI in the Cloud – Physical Security Datacenters are protected by layers of defense-in-depth security: • Access Request - An individual only has access to the discrete area, based on the Microsoft-approved business justification • Facility’s Perimeter – Tall steel fences with cameras encompass the perimeter. A security team constantly monitors videos This is a Header • Building Entrance – Professional security officers patrol the datacenter THIS ISroutinely A SUBTITLE • Inside the Building – You must pass two -factor authentication with biometrics to move through the datacenter • Datacenter Floor – Full-body metal detection on entrance and exit. Only approved devices allowed. Video cameras monitor the front and back of every server rack
This is a Header THIS IS A SUBTITLE

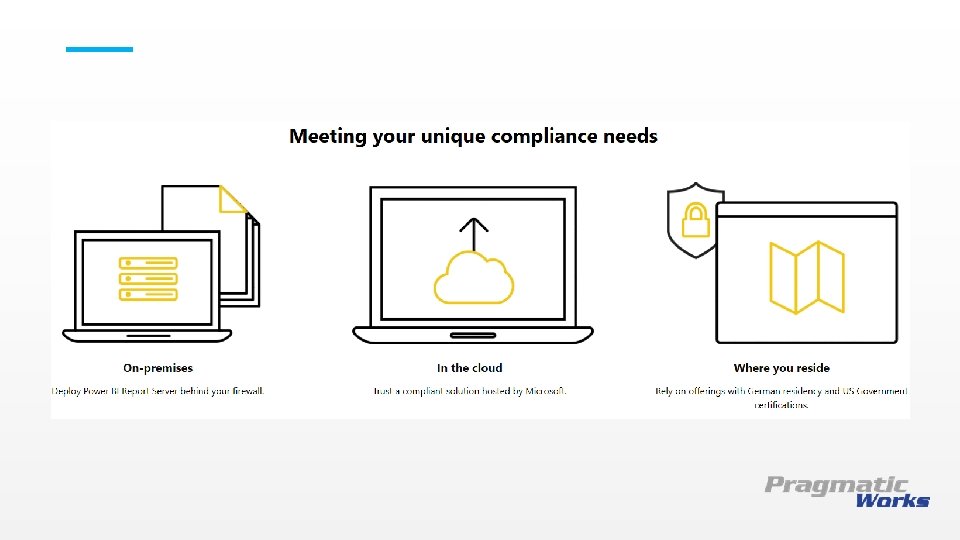
Power BI – Geo Specific Deployments This is a Header THIS IS A SUBTITLE
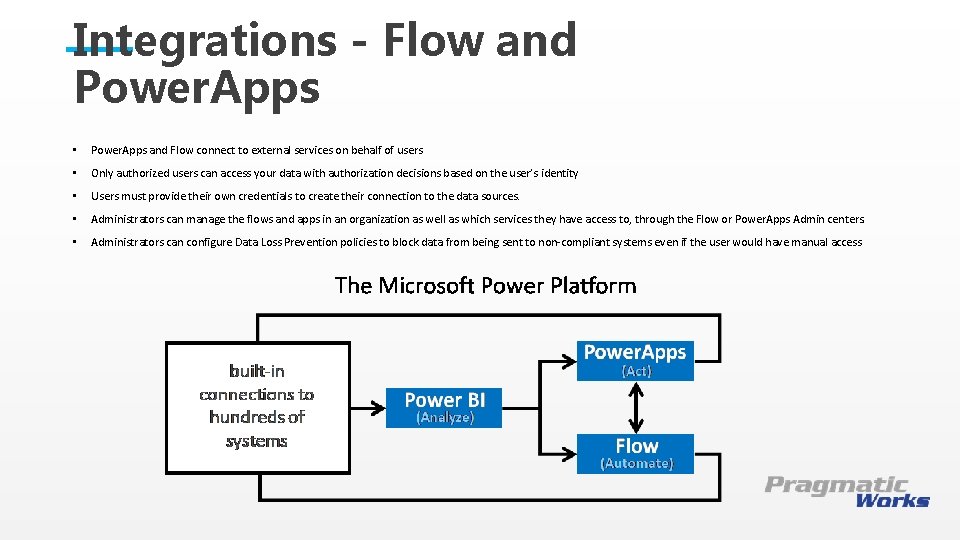
Integrations - Flow and Power. Apps • Power. Apps and Flow connect to external services on behalf of users • Only authorized users can access your data with authorization decisions based on the user’s identity • Users must provide their own credentials to create their connection to the data sources. • Administrators can manage the flows and apps in an organization as well as which services they have access to, through the Flow or Power. Apps Admin centers. • Administrators can configure Data Loss Prevention policies to block data from being sent to non-compliant systems even if the user would have manual access This is a Header THIS IS A SUBTITLE
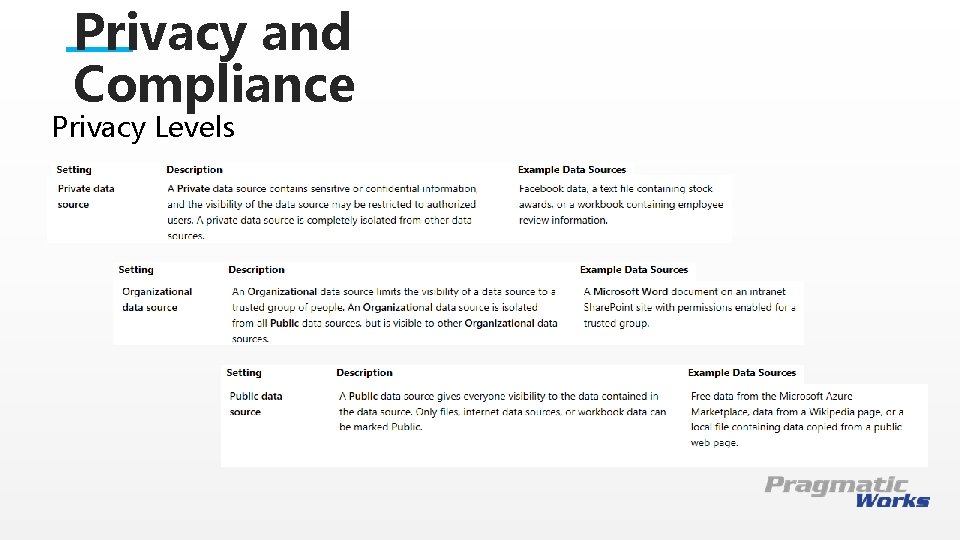
Privacy and Compliance Privacy Levels This is a Header THIS IS A SUBTITLE
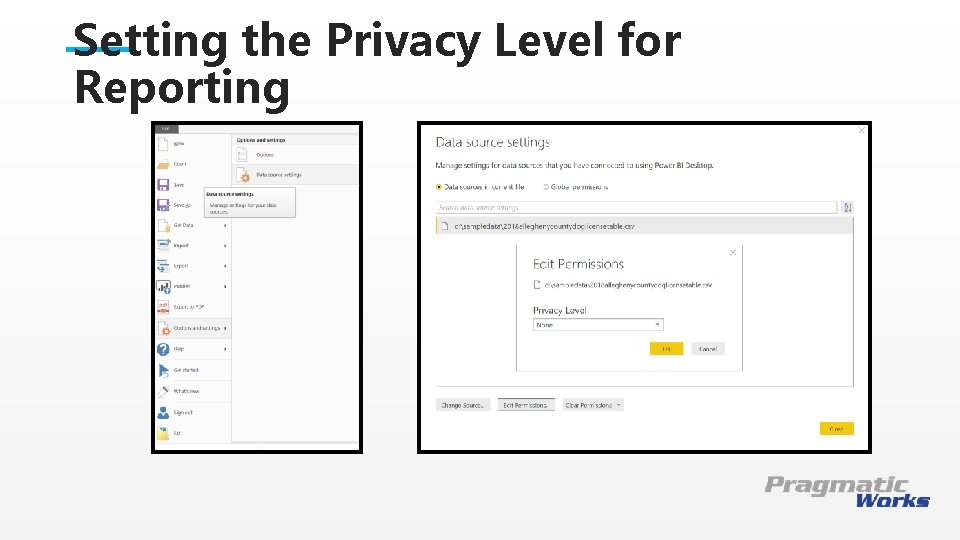
Setting the Privacy Level for Reporting This is a Header THIS IS A SUBTITLE
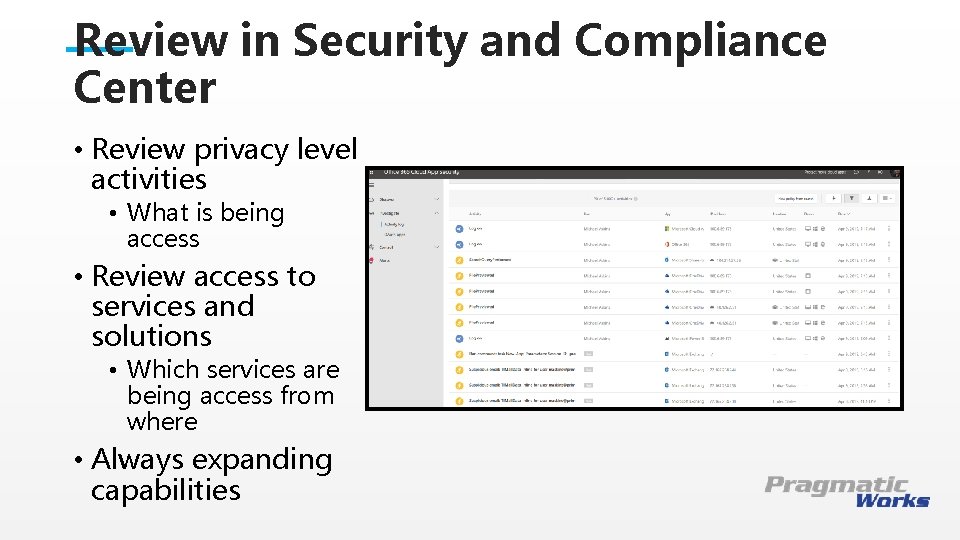
Review in Security and Compliance Center • Review privacy level activities • What is being access This is a Header • Review access to services and THIS IS A SUBTITLE solutions • Which services are being access from where • Always expanding capabilities

Next Level: Leverage Power BI as a Compliance Dashboard • Create a rich reporting tool that can deliver IT compliance data to security and compliance teams • Eliminates the need to maintain additional RBAC groups for each solution • Aggregate compliance metrics from different systems and solutions into a tool that can create actionable outcomes THIS IS A SUBTITLE • Increase confidence in your data stewardship by providing a holistic view to your employees, customers and vendors This is a Header

Need Help – Managed Services and Consulting Challenge • Knowing who has access to what datasets • Widespread dataset duplication across the enterprise • Understand what reports have personal / HIPPA data in them This is a Header Solution THIS IS A SUBTITLE • Initial audit is done to inventory and categorize datasets & reports • Reporting is built on who has access to data sets and to identify dataset duplication. • *Reporting on reports and data sets with PII information and who has access to them
Have Any Questions? Please feel free to reach out for any additional information!! This is a Header THIS IS A SUBTITLE Sources for this presentation: pragmaticworks. com, microsoft. com, dataonwheels. com
- Slides: 23