POLYGRAPH Automatically Generating Signatures for Polymorphic Worms Authors









- Slides: 22

POLYGRAPH: Automatically Generating Signatures for Polymorphic Worms Authors: James Newsome, Brad Karp, Dawn Song PUBLICATION: IEEE Security and Privacy Symposium, May 2005 CLASS PRESENTATION BY: Anvita Priyam

POLYGRAPH n Intrusion Detection Systems(IDS) > Monitor networking traffic for suspicious activity > Alert the system or administrator > May block user or source IP n Signature based IDS > monitors packets on the n/w & compares them against database of signatures > lag in case of a new threat

POLYGRAPH n. Currently Used Techniques By IDS > string matching at arbitrary payload offsets > string matching at fixed payload offsets > matching of regular expressions within a flow’s payload

POLYGRAPH n Polymorphic Worm > changes its appearance with every instance > byte sequences of worm instances vary > code remains the same n Mechanism > encrypt the code with a random key > generate a short decryptor(PD) > PD and the key keep changing

POLYGRAPH n Motivation for automating signatures > earlier, signatures were generated manually > slow paced

POLYGRAPH n Polygraph comes into picture > signatures consist of multiple disjoint content substring > substrings: protocol framing, return addresses, poorly obfuscated code > often present in all variants of a payload PS: It does not consider single substring signature

POLYGRAPH n Underlying Assumption > possible to generate signatures automatically that match the many variants of PW > offer low false positives and low false negatives n BASIS > share invariant content as they exploit same vulnerability

POLYGRAPH n Sources of Invariant Content > Exploit Framing( e. g. , reserved keywords, binary constants that are part of wire protocol) > Exploit Payload

POLYGRAPH n Signature Classes for PW > Conjunction Signatures > Token Subsequence Signature > Bayes Signature

POLYGRAPH n Conjunction Signatures > signature consists of a set of tokens > all the tokens must match > order of matching is not particular

POLYGRAPH n Token-subsequence Signatures > consists of ordered set of tokens > identical ordering is required for a match > can be easily expressed as regular expressions > more specific compared to conjunction signature

POLYGRAPH n Bayes Signature > associated with a score and an overall threshold > instead of exact matching it provides probabilistic matching > construction and matching is less rigid

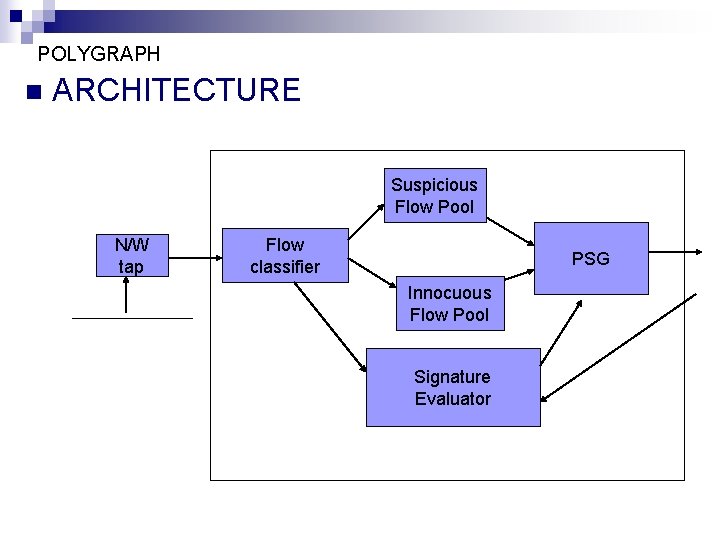
POLYGRAPH n ARCHITECTURE Suspicious Flow Pool N/W tap Flow classifier PSG Innocuous Flow Pool Signature Evaluator

POLYGRAPH n Design Goals > Signature quality > Efficient signature generation > Efficient signature matching > Generation of small signature sets > Robustness against noise and multiple worms > Robustness against evasion and subversion

POLYGRAPH n Signature Generation Algorithms > Pre-processing: Token extraction > first step to eliminate irrelevant parts > extract all distinct substrings of min length > Generating single signatures > for conjunction signature just use token extraction, signature is this set of tokens > for token subsequence signature find a subsequence of tokens that is present in sample. Iteratively apply string alignment

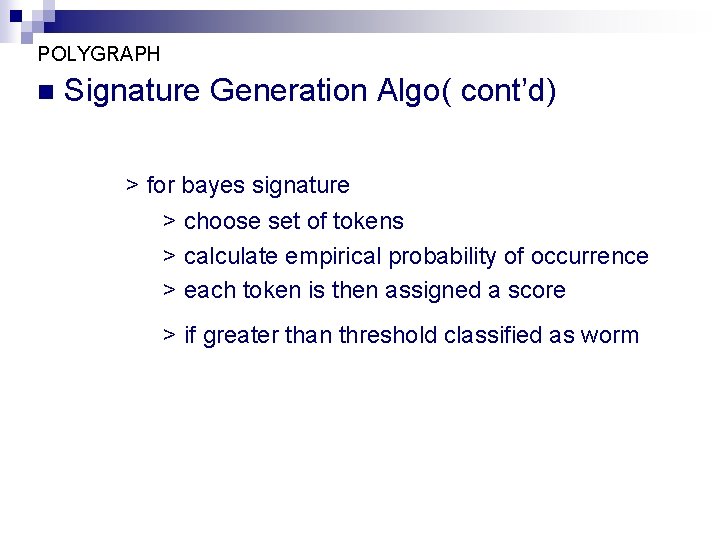
POLYGRAPH n Signature Generation Algo( cont’d) > for bayes signature > choose set of tokens > calculate empirical probability of occurrence > each token is then assigned a score > if greater than threshold classified as worm

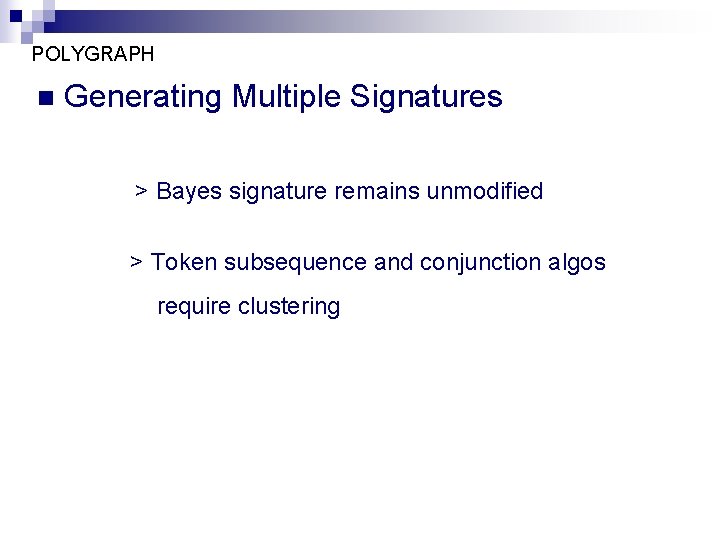
POLYGRAPH n Generating Multiple Signatures > Bayes signature remains unmodified > Token subsequence and conjunction algos require clustering

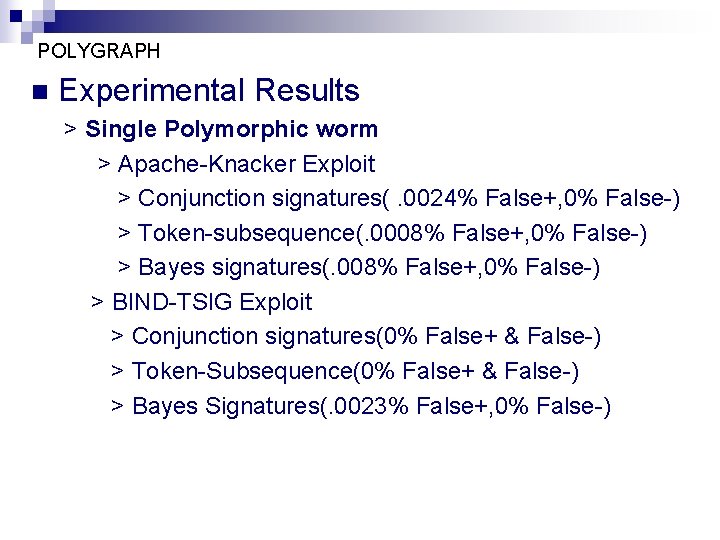
POLYGRAPH n Experimental Results > Single Polymorphic worm > Apache-Knacker Exploit > Conjunction signatures(. 0024% False+, 0% False-) > Token-subsequence(. 0008% False+, 0% False-) > Bayes signatures(. 008% False+, 0% False-) > BIND-TSIG Exploit > Conjunction signatures(0% False+ & False-) > Token-Subsequence(0% False+ & False-) > Bayes Signatures(. 0023% False+, 0% False-)

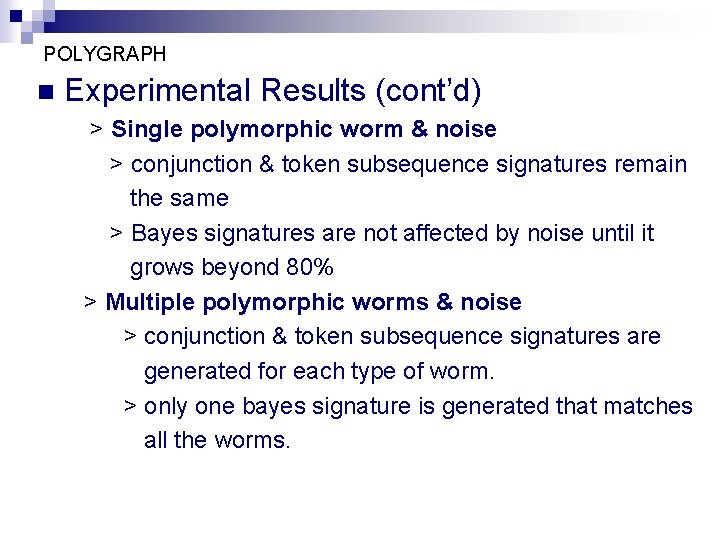
POLYGRAPH n Experimental Results (cont’d) > Single polymorphic worm & noise > conjunction & token subsequence signatures remain the same > Bayes signatures are not affected by noise until it grows beyond 80% > Multiple polymorphic worms & noise > conjunction & token subsequence signatures are generated for each type of worm. > only one bayes signature is generated that matches all the worms.

POLYGRAPH n CONCLUSION > content based filtering holds great promise for tackling PW > Polygraph automatically derives signatures for PW > It generates high quality signatures even in the presence of multiple flows and noise > rumors of demise of content based filtering is exaggerated

POLYGRAPH n WEAKNESS > very little insight into how PWs function > payload invariance assumptions are naïve > no clear reference to situational applications of signature generation algorithms

POLYGRAPH n SUGGESTIONS > should be more informative on initial topics > a wider range of studies required