Pointers Alias Mod Ref Analyses Alina Sbirlea Google

Pointers, Alias & Mod. Ref Analyses Alina Sbirlea (Google), Nuno Lopes (Microsoft Research) Joint work with: Juneyoung Lee, Gil Hur (SNU), Ralf Jung (MPI-SWS), Zhengyang Liu, John Regehr (U. Utah)
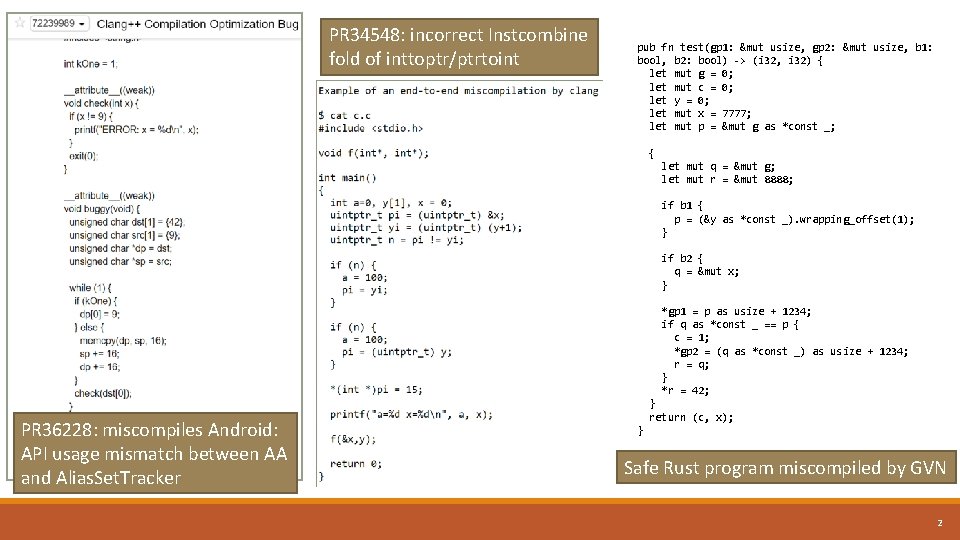
PR 34548: incorrect Instcombine fold of inttoptr/ptrtoint pub fn test(gp 1: &mut usize, gp 2: &mut usize, b 1: bool, b 2: bool) -> (i 32, i 32) { let mut g = 0; let mut c = 0; let y = 0; let mut x = 7777; let mut p = &mut g as *const _; { let mut q = &mut g; let mut r = &mut 8888; if b 1 { p = (&y as *const _). wrapping_offset(1); } if b 2 { q = &mut x; } PR 36228: miscompiles Android: API usage mismatch between AA and Alias. Set. Tracker *gp 1 = p as usize + 1234; if q as *const _ == p { c = 1; *gp 2 = (q as *const _) as usize + 1234; r = q; } *r = 42; } return (c, x); } Safe Rust program miscompiled by GVN 2

Pointers ≠ Integers 3
![What’s a Memory Model? char *p = malloc(4); char *q = malloc(4); q[2] = What’s a Memory Model? char *p = malloc(4); char *q = malloc(4); q[2] =](http://slidetodoc.com/presentation_image_h/36697805d6e416a0c49a94f2db233906/image-4.jpg)
What’s a Memory Model? char *p = malloc(4); char *q = malloc(4); q[2] = 0; p[6] = 1; print(q[2]); UB? 1) When is a memory operation UB? 2) What’s the value of a load operation? 0 or 1? 4
![Flat memory model p+6 char *p = malloc(4); char *q = malloc(4); q[2] = Flat memory model p+6 char *p = malloc(4); char *q = malloc(4); q[2] =](http://slidetodoc.com/presentation_image_h/36697805d6e416a0c49a94f2db233906/image-5.jpg)
Flat memory model p+6 char *p = malloc(4); char *q = malloc(4); q[2] = 0; p[6] = 1; Not UB print(q[2]); print(1) p[0] p[2] 01 q[0] q[2] Simple, but inhibits optimizations! 5
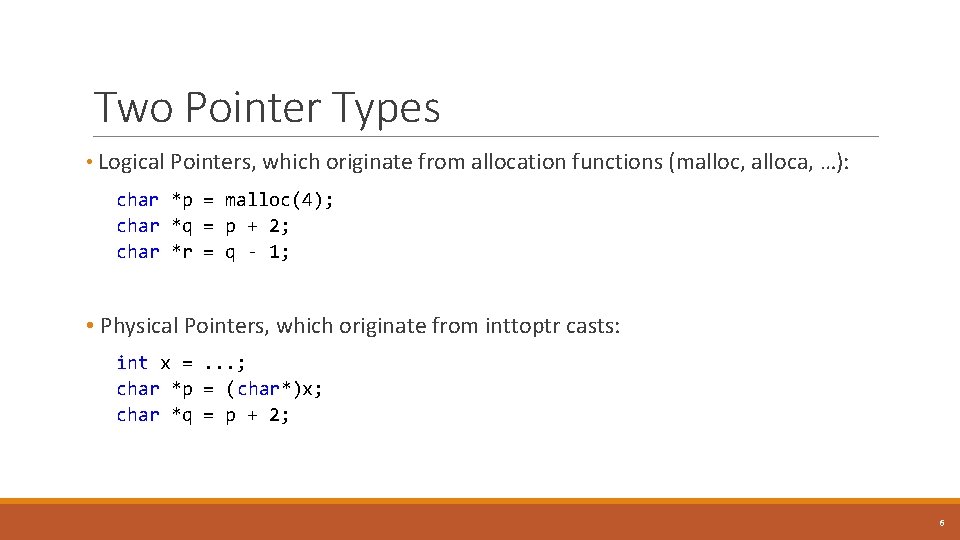
Two Pointer Types • Logical Pointers, which originate from allocation functions (malloc, alloca, …): char *p = malloc(4); char *q = p + 2; char *r = q - 1; • Physical Pointers, which originate from inttoptr casts: int x =. . . ; char *p = (char*)x; char *q = p + 2; 6
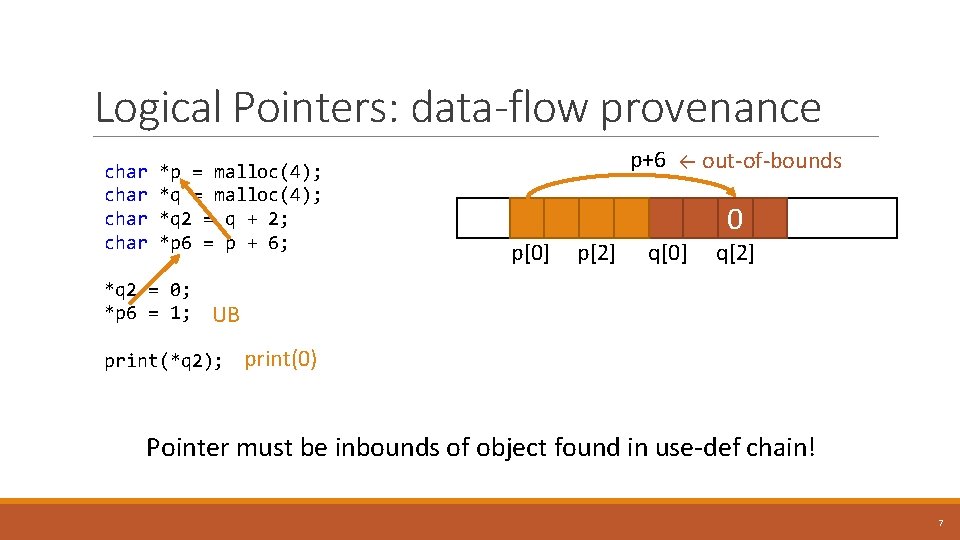
Logical Pointers: data-flow provenance char *p = malloc(4); char *q 2 = q + 2; char *p 6 = p + 6; p+6 ← out-of-bounds p[0] p[2] 0 q[0] q[2] *q 2 = 0; *p 6 = 1; UB print(*q 2); print(0) Pointer must be inbounds of object found in use-def chain! 7
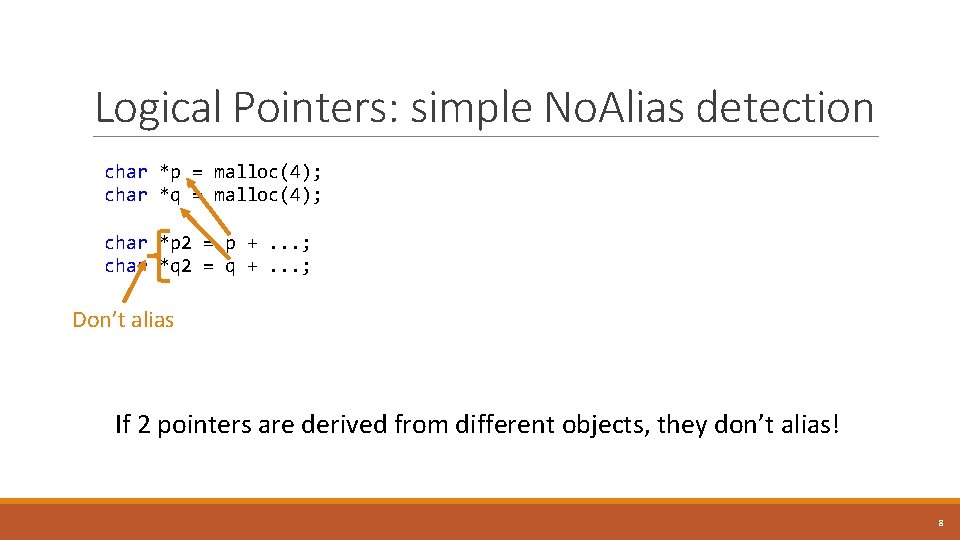
Logical Pointers: simple No. Alias detection char *p = malloc(4); char *q = malloc(4); char *p 2 = p +. . . ; char *q 2 = q +. . . ; Don’t alias If 2 pointers are derived from different objects, they don’t alias! 8
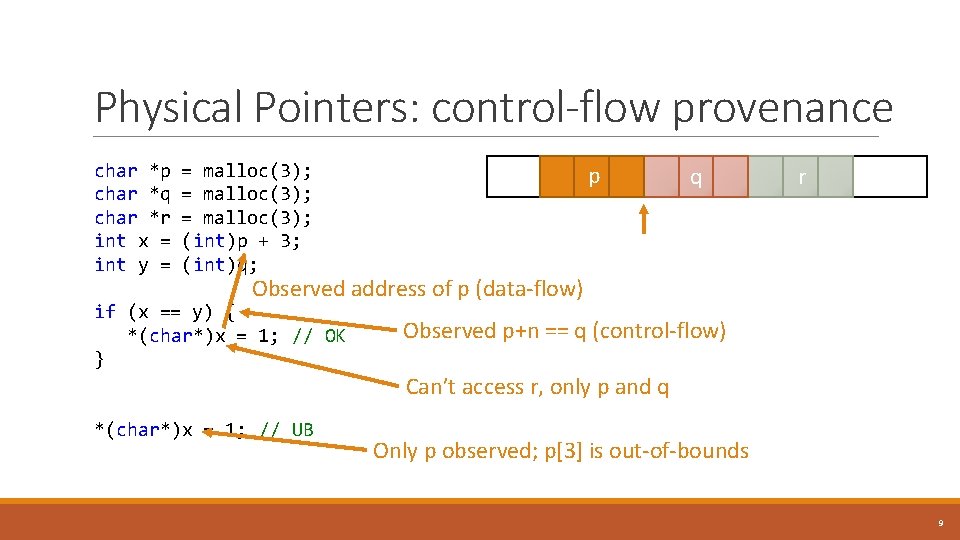
Physical Pointers: control-flow provenance char *p = malloc(3); char *q = malloc(3); char *r = malloc(3); int x = (int)p + 3; int y = (int)q; p q r Observed address of p (data-flow) if (x == y) { *(char*)x = 1; // OK } Observed p+n == q (control-flow) Can’t access r, only p and q *(char*)x = 1; // UB Only p observed; p[3] is out-of-bounds 9
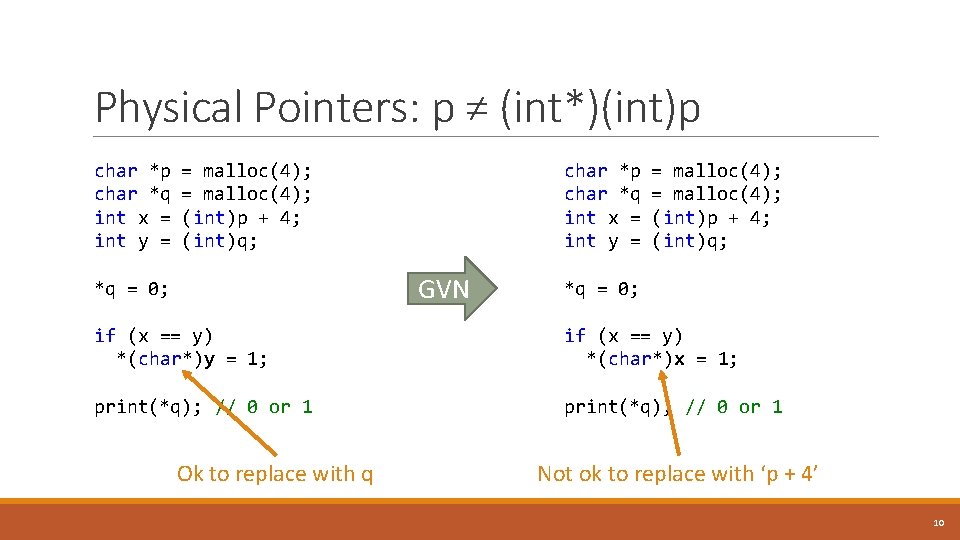
Physical Pointers: p ≠ (int*)(int)p char *p = malloc(4); char *q = malloc(4); int x = (int)p + 4; int y = (int)q; GVN *q = 0; if (x == y) *(char*)y = 1; if (x == y) *(char*)x = 1; print(*q); // 0 or 1 Ok to replace with q Not ok to replace with ‘p + 4’ 10
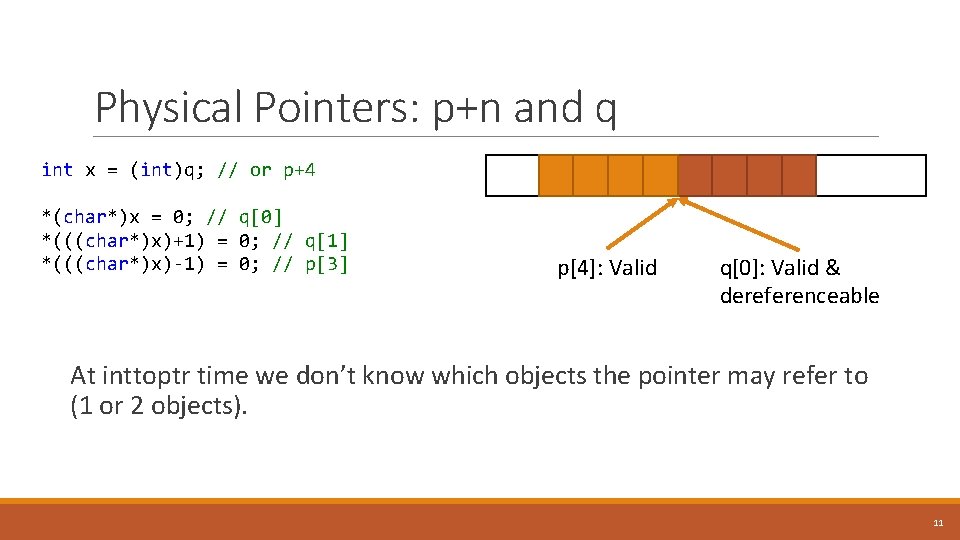
Physical Pointers: p+n and q int x = (int)q; // or p+4 *(char*)x = 0; // q[0] *(((char*)x)+1) = 0; // q[1] *(((char*)x)-1) = 0; // p[3] p[4]: Valid q[0]: Valid & dereferenceable At inttoptr time we don’t know which objects the pointer may refer to (1 or 2 objects). 11
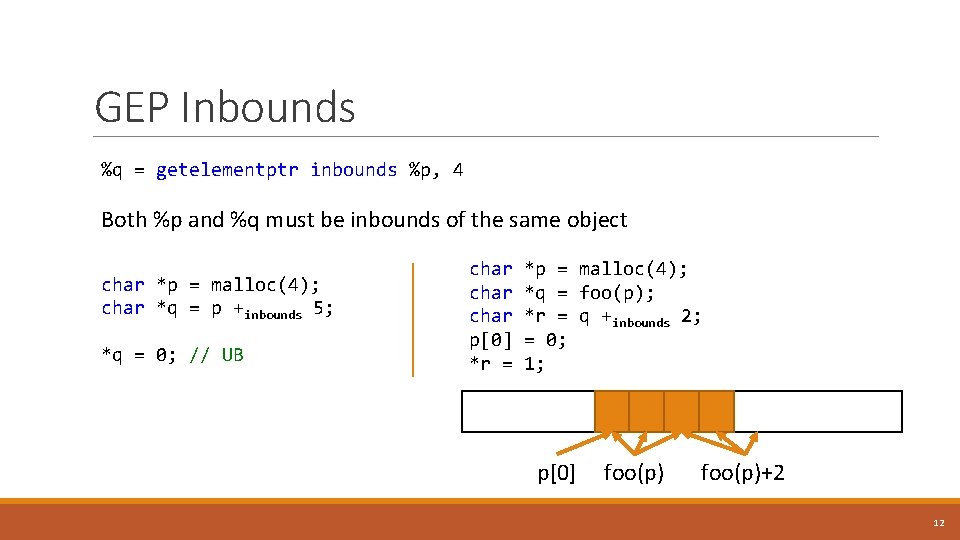
GEP Inbounds %q = getelementptr inbounds %p, 4 Both %p and %q must be inbounds of the same object char *p = malloc(4); char *q = p +inbounds 5; *q = 0; // UB char *p = malloc(4); char *q = foo(p); char *r = q +inbounds 2; p[0] = 0; *r = 1; p[0] foo(p)+2 12
![No Layout Guessing Dereferenceable pointers: p+2 == q+2 is always false p[2] q[2] p[4] No Layout Guessing Dereferenceable pointers: p+2 == q+2 is always false p[2] q[2] p[4]](http://slidetodoc.com/presentation_image_h/36697805d6e416a0c49a94f2db233906/image-13.jpg)
No Layout Guessing Dereferenceable pointers: p+2 == q+2 is always false p[2] q[2] p[4] q[0] Valid, but not dereferenceable pointers: p+n == q is undef 14
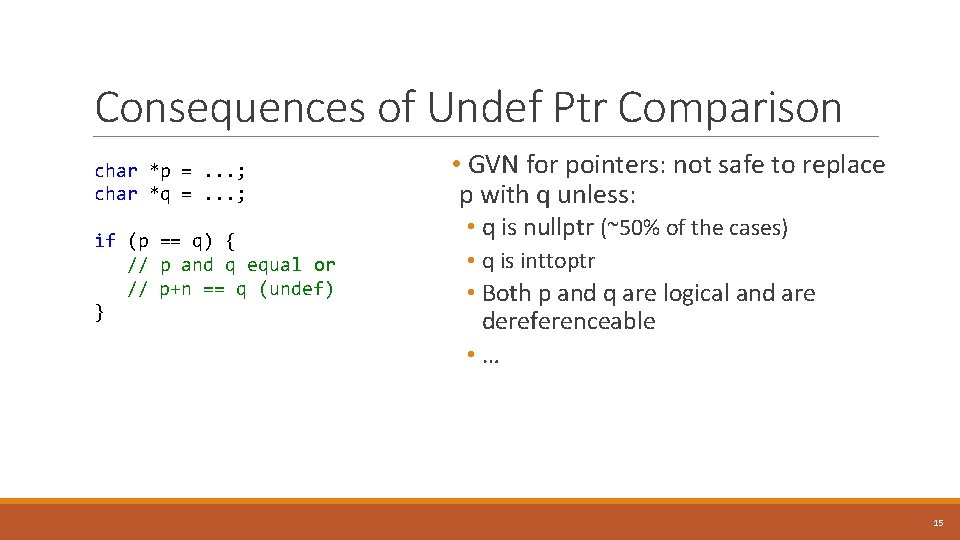
Consequences of Undef Ptr Comparison char *p =. . . ; char *q =. . . ; if (p == q) { // p and q equal or // p+n == q (undef) } • GVN for pointers: not safe to replace p with q unless: • q is nullptr (~50% of the cases) • q is inttoptr • Both p and q are logical and are dereferenceable • … 15
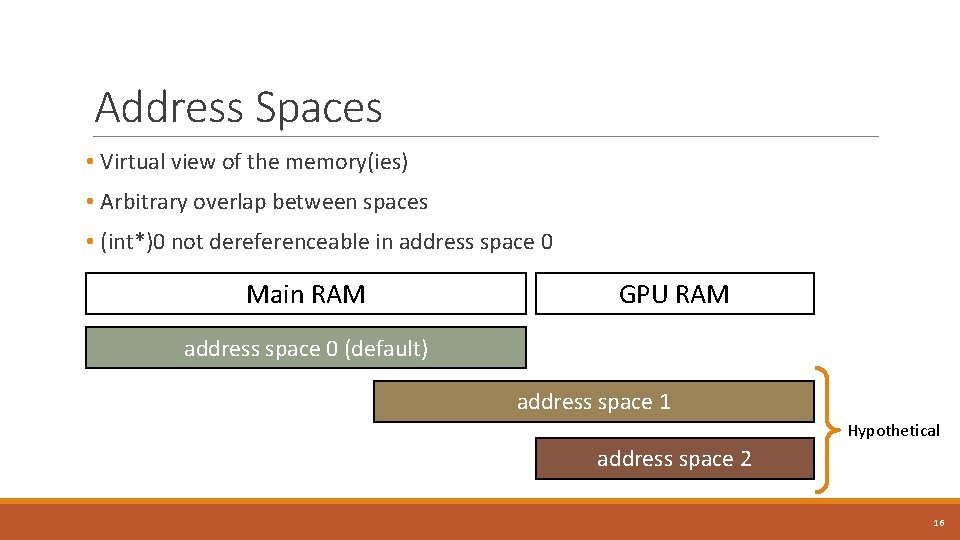
Address Spaces • Virtual view of the memory(ies) • Arbitrary overlap between spaces • (int*)0 not dereferenceable in address space 0 Main RAM GPU RAM address space 0 (default) address space 1 Hypothetical address space 2 16

Pointer Subtraction • Implemented as (int)p – (int)q • Correct, but loses information vs p – q (only defined for p, q in same object) • Analyses don’t recognize this idiom yet 17
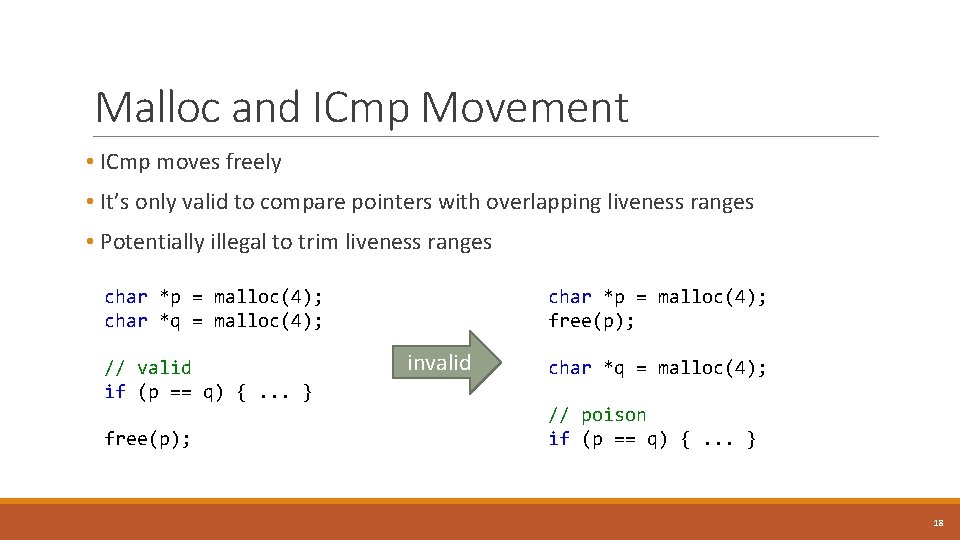
Malloc and ICmp Movement • ICmp moves freely • It’s only valid to compare pointers with overlapping liveness ranges • Potentially illegal to trim liveness ranges char *p = malloc(4); char *q = malloc(4); // valid if (p == q) {. . . } free(p); char *p = malloc(4); free(p); invalid char *q = malloc(4); // poison if (p == q) {. . . } 18
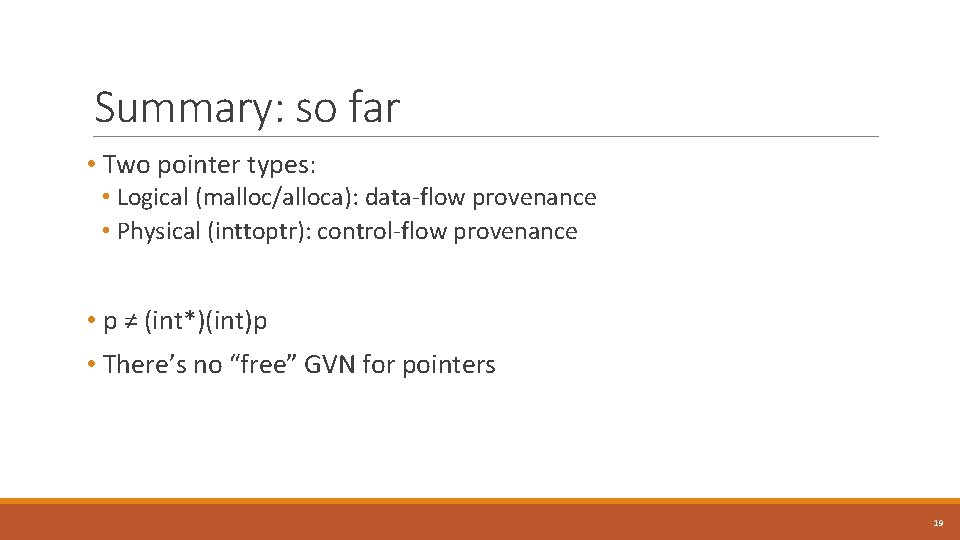
Summary: so far • Two pointer types: • Logical (malloc/alloca): data-flow provenance • Physical (inttoptr): control-flow provenance • p ≠ (int*)(int)p • There’s no “free” GVN for pointers 19

Alias Analysis 20

Alias Analysis queries • alias() • get. Mod. Ref. Info() 21

AA Query char *p =. . . ; int *q =. . . ; alias(p, szp, q, szq) what’s the aliasing between pointers p, q and resp. access sizes szp, szq *p = 0; *q = 1; print(*p); // 0 or 1? alias(p, 1 , q, 4) = ? 22
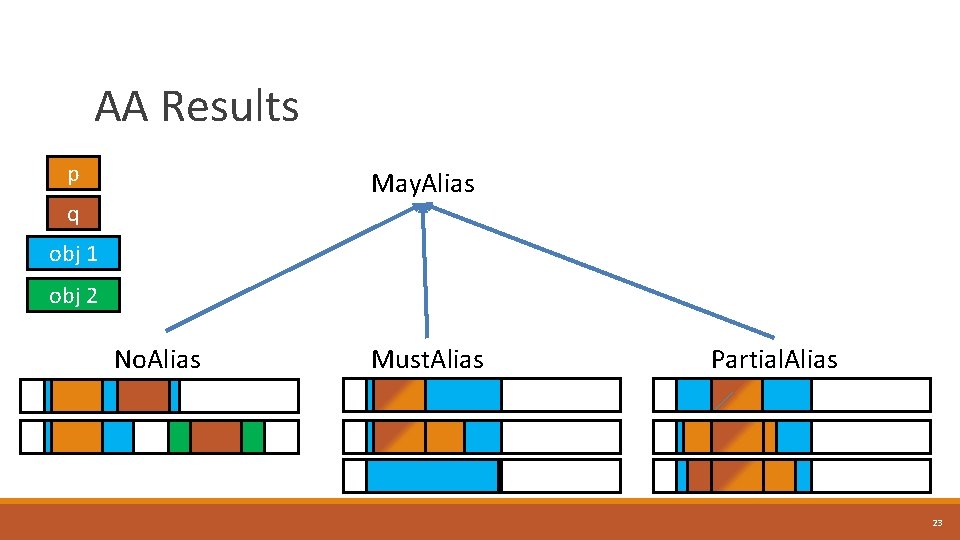
AA Results p May. Alias q obj 1 obj 2 No. Alias Must. Alias Partial. Alias 23
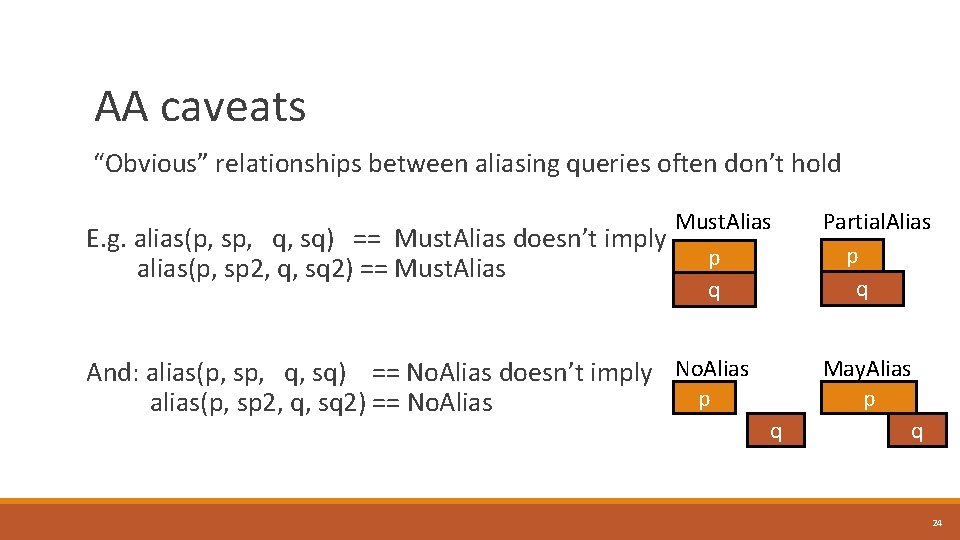
AA caveats “Obvious” relationships between aliasing queries often don’t hold Must. Alias E. g. alias(p, sp, q, sq) == Must. Alias doesn’t imply p alias(p, sp 2, q, sq 2) == Must. Alias q Partial. Alias p q And: alias(p, sp, q, sq) == No. Alias doesn’t imply No. Alias p alias(p, sp 2, q, sq 2) == No. Alias May. Alias p q q 24
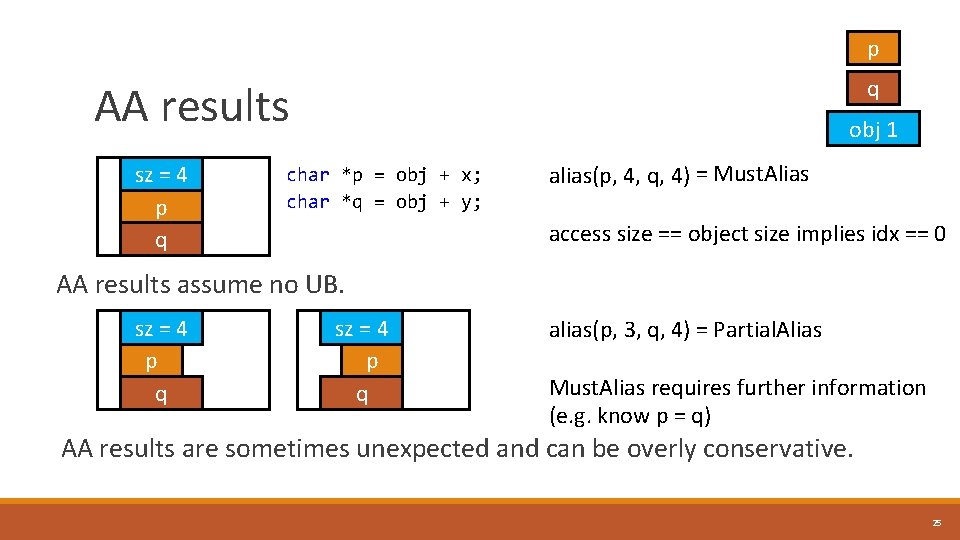
p q AA results sz = 4 p q obj 1 char *p = obj + x; char *q = obj + y; alias(p, 4, q, 4) = Must. Alias access size == object size implies idx == 0 AA results assume no UB. sz = 4 p q alias(p, 3, q, 4) = Partial. Alias Must. Alias requires further information (e. g. know p = q) AA results are sometimes unexpected and can be overly conservative. 25
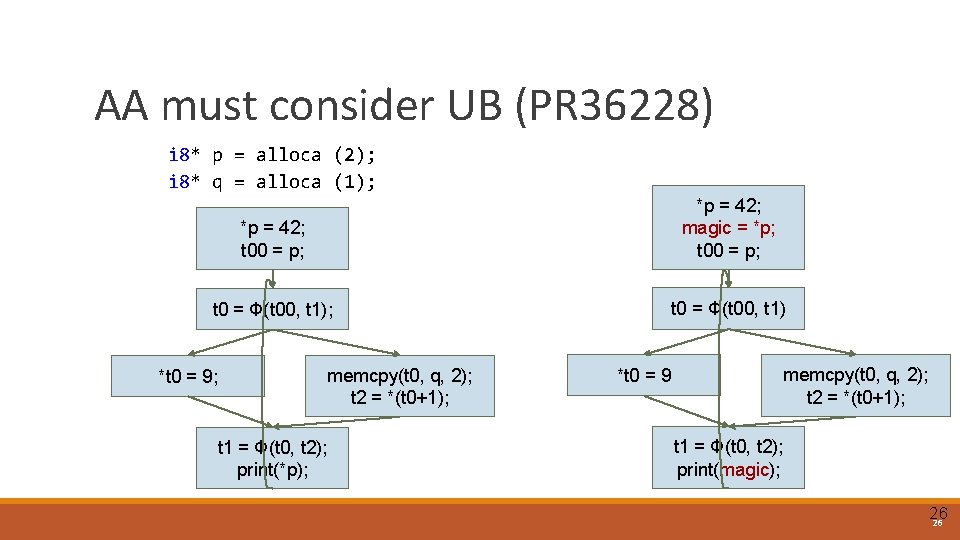
AA must consider UB (PR 36228) i 8* p = alloca (2); i 8* q = alloca (1); *p = 42; t 00 = p; *p = 42; magic = *p; t 00 = p; t 0 = Ф(t 00, t 1) *t 0 = 9; memcpy(t 0, q, 2); t 2 = *(t 0+1); t 1 = Ф(t 0, t 2); print(*p); *t 0 = 9 memcpy(t 0, q, 2); t 2 = *(t 0+1); t 1 = Ф(t 0, t 2); print(magic); 26 26

New in AA: precise access size • Recent API changes introduced two access size types: • Precise: when the exact size is known • Upper bound: maximum size, but no minimum size guaranteed (can be 0) • See D 45581, D 44748 27 27

Mod. Ref Analysis 28

Mod. Ref. Info • How instructions affect memory instructions: - Mod = modifies / writes - Ref = accesses / reads 29
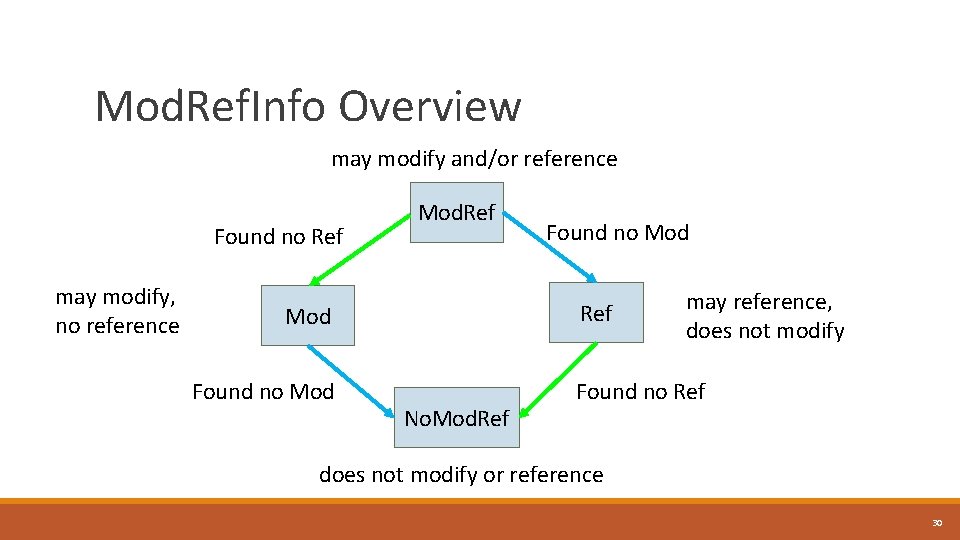
Mod. Ref. Info Overview may modify and/or reference Found no Ref may modify, no reference Mod. Ref Mod Found no Mod No. Mod. Ref may reference, does not modify Found no Ref does not modify or reference 30

Mod. Ref Example declare i 32 @g(i 8*) declare i 32 @h(i 8*) argmemonly define void @f(i 8* %p) { %1 = call i 32 @g(i 8* %p) ; Mod. Ref %p store i 8 0, i 8* %p ; Mod %p (no Ref %p) %2 = load i 8, i 8* %p ; Ref %p (no Mod %p) %3 = call i 32 @g(i 8* readonly %p) ; Mod. Ref %p (%p may be a global) %4 = call i 32 @h(i 8* readonly %p) ; Ref %p (h only accesses args) %a = alloca i 8 %5 = call i 32 @g(i 8* readonly %a) ; Mod. Ref %a (tough %a doesn’t escape) 31
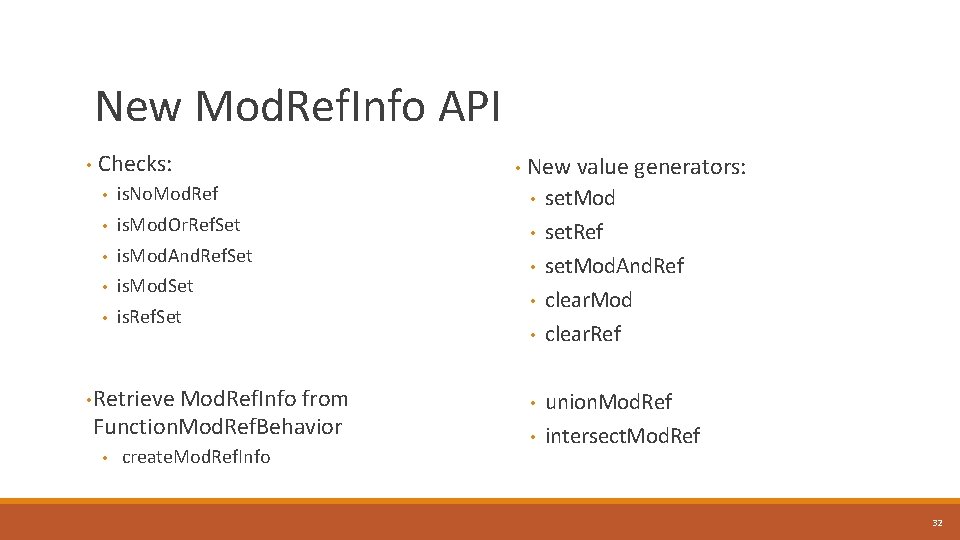
New Mod. Ref. Info API • Checks: • New value generators: • is. No. Mod. Ref • • is. Mod. Or. Ref. Set • is. Mod. And. Ref. Set • • is. Mod. Set • is. Ref. Set • Retrieve Mod. Ref. Info from Function. Mod. Ref. Behavior • create. Mod. Ref. Info • • • set. Mod set. Ref set. Mod. And. Ref clear. Mod clear. Ref union. Mod. Ref intersect. Mod. Ref 32
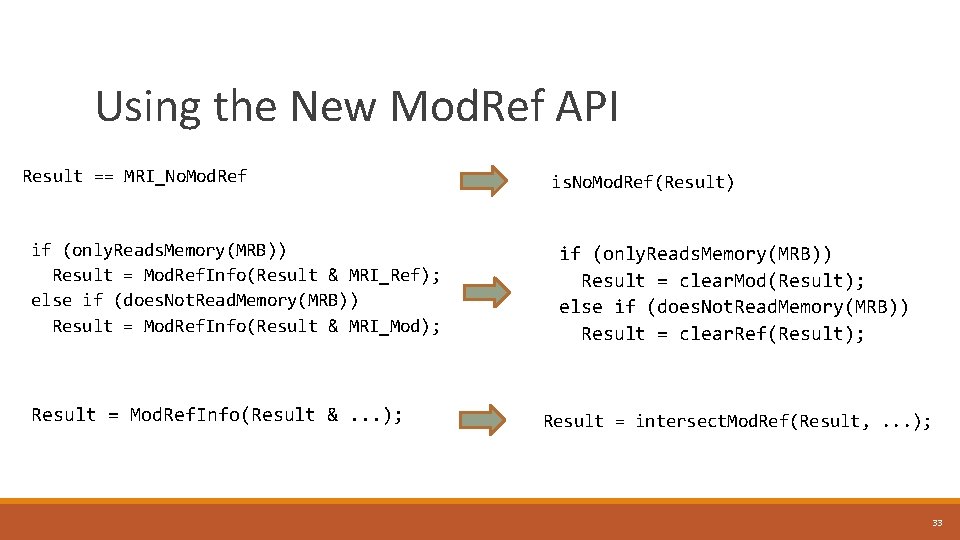
Using the New Mod. Ref API Result == MRI_No. Mod. Ref if (only. Reads. Memory(MRB)) Result = Mod. Ref. Info(Result & MRI_Ref); else if (does. Not. Read. Memory(MRB)) Result = Mod. Ref. Info(Result & MRI_Mod); Result = Mod. Ref. Info(Result &. . . ); is. No. Mod. Ref(Result) if (only. Reads. Memory(MRB)) Result = clear. Mod(Result); else if (does. Not. Read. Memory(MRB)) Result = clear. Ref(Result); Result = intersect. Mod. Ref(Result, . . . ); 33
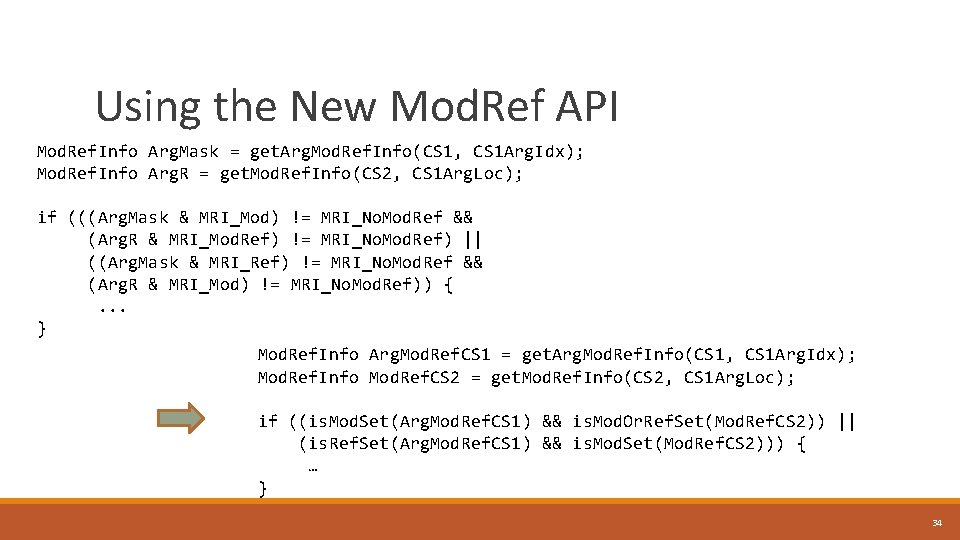
Using the New Mod. Ref API Mod. Ref. Info Arg. Mask = get. Arg. Mod. Ref. Info(CS 1, CS 1 Arg. Idx); Mod. Ref. Info Arg. R = get. Mod. Ref. Info(CS 2, CS 1 Arg. Loc); if (((Arg. Mask & MRI_Mod) != MRI_No. Mod. Ref && (Arg. R & MRI_Mod. Ref) != MRI_No. Mod. Ref) || ((Arg. Mask & MRI_Ref) != MRI_No. Mod. Ref && (Arg. R & MRI_Mod) != MRI_No. Mod. Ref)) { . . . } Mod. Ref. Info Arg. Mod. Ref. CS 1 = get. Arg. Mod. Ref. Info(CS 1, CS 1 Arg. Idx); Mod. Ref. Info Mod. Ref. CS 2 = get. Mod. Ref. Info(CS 2, CS 1 Arg. Loc); if ((is. Mod. Set(Arg. Mod. Ref. CS 1) && is. Mod. Or. Ref. Set(Mod. Ref. CS 2)) || (is. Ref. Set(Arg. Mod. Ref. CS 1) && is. Mod. Set(Mod. Ref. CS 2))) { … } 34

Why have Must. Alias in Mod. Ref. Info? • Alias. Analysis calls are expensive! • Avoid double AA calls when Mod. Ref + alias() info is needed. • Currently used in Memory. SSA 35
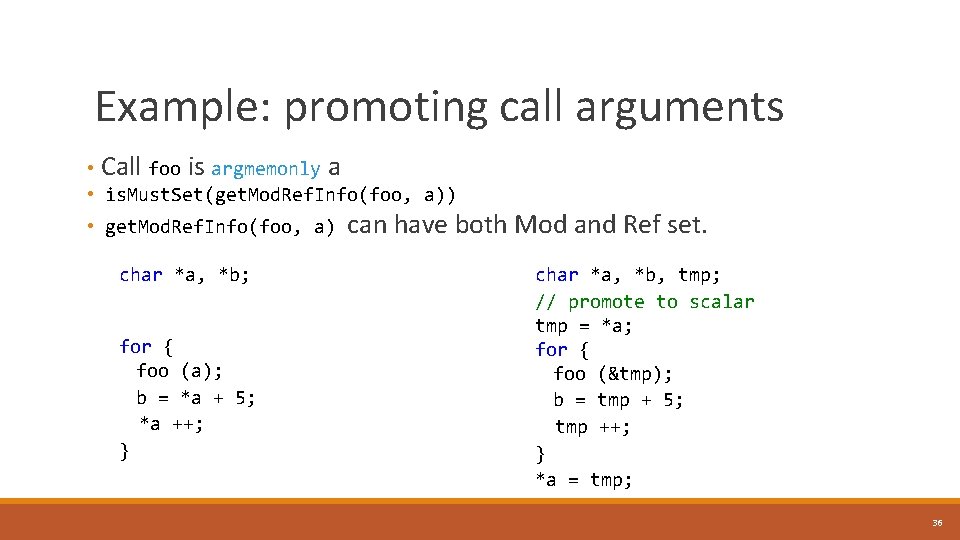
Example: promoting call arguments • Call foo is argmemonly a • is. Must. Set(get. Mod. Ref. Info(foo, a)) • get. Mod. Ref. Info(foo, a) can have both Mod and Ref set. char *a, *b; for { foo (a); b = *a + 5; *a ++; } char *a, *b, tmp; // promote to scalar tmp = *a; for { foo (&tmp); b = tmp + 5; tmp ++; } *a = tmp; 36
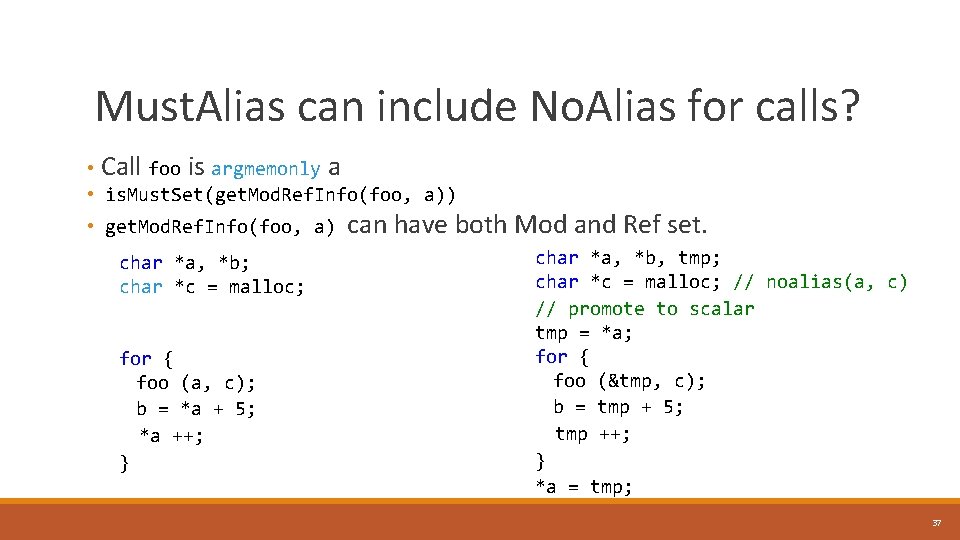
Must. Alias can include No. Alias for calls? • Call foo is argmemonly a • is. Must. Set(get. Mod. Ref. Info(foo, a)) • get. Mod. Ref. Info(foo, a) can have both Mod and Ref set. char *a, *b, tmp; char *a, *b; char *c = malloc; // noalias(a, c) char *c = malloc; // promote to scalar tmp = *a; for { foo (&tmp, c); foo (a, c); b = tmp + 5; b = *a + 5; tmp ++; *a ++; } } *a = tmp; 37
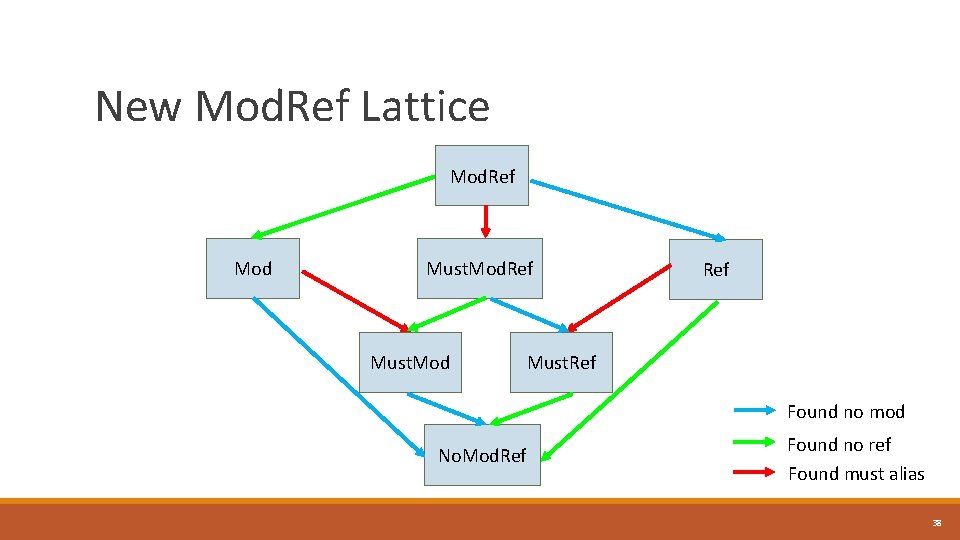
New Mod. Ref Lattice Mod. Ref Mod Must. Mod. Ref Must. Mod Ref Must. Ref Found no mod No. Mod. Ref Found no ref Found must alias 38

Common Misconceptions of Must in Mod. Ref. Info • Must. Mod = may modify, must alias found, NOT must modify ○ E. g. , foo has readnone attribute => Mod. Ref(foo(a), a) = No. Mod. Ref. • Must. Ref = may reference, must alias found, NOT must reference • Must. Mod. Ref = may modify and may reference, must alias found, NOT must modify and must reference 39

Key takeaways • Mod. Ref is the most general response: may modify or reference • Mod is cleared when we’re sure a location is not modified • Ref is cleared when we’re sure a location is not referenced • Must is set when we’re sure we found a Must. Alias • No. Mod. Ref means we’re sure location is neither modified or referenced, i. e. written or read • The “Must” bit in the Mod. Ref. Info enum class is provided for completeness, and is not used 40
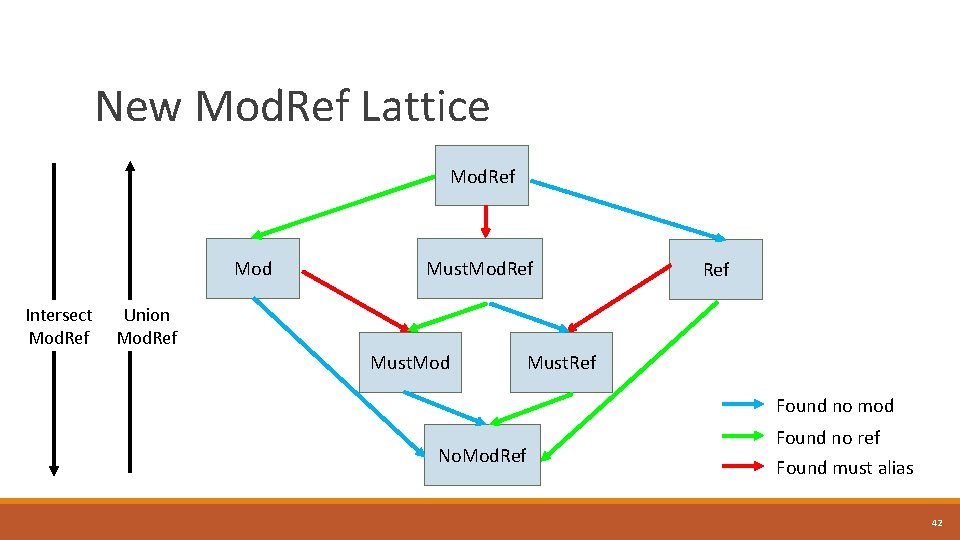
New Mod. Ref Lattice Mod. Ref Mod Intersect Mod. Ref Must. Mod. Ref Union Mod. Ref Must. Mod Must. Ref Found no mod No. Mod. Ref Found no ref Found must alias 42
Disclaimers / Implementation details • Globals. Mod. Ref relies on a certain number of bits available for alignments. To mitigate this, Must info is being dropped. • Function. Mod. Ref. Behavior still relies on bit-wise operations. Changes similar to Mod. Ref. Info may happen in the future. 43
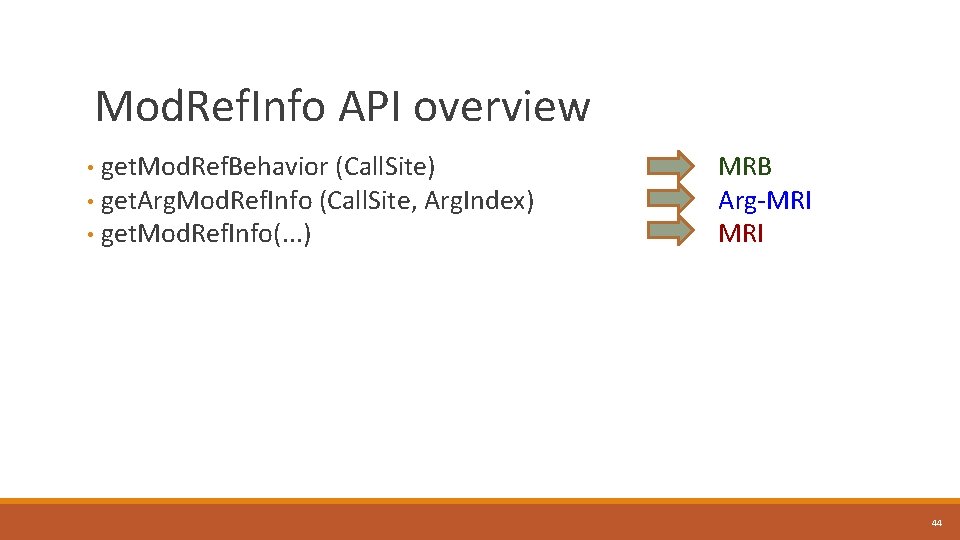
Mod. Ref. Info API overview • get. Mod. Ref. Behavior (Call. Site) • get. Arg. Mod. Ref. Info (Call. Site, Arg. Index) • get. Mod. Ref. Info(. . . ) MRB Arg-MRI 44
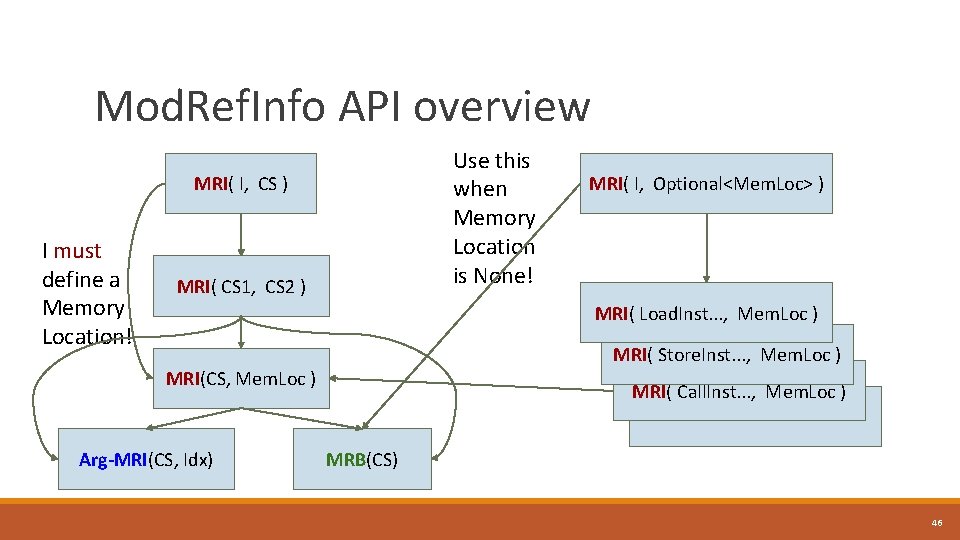
Mod. Ref. Info API overview Use this when Memory Location is None! MRI( I, CS ) I must define a Memory Location! MRI( CS 1, CS 2 ) MRI( I, Optional<Mem. Loc> ) MRI( Load. Inst. . . , Mem. Loc ) MRI( Store. Inst. . . , Mem. Loc ) MRI(CS, Mem. Loc ) Arg-MRI(CS, Idx) MRI( Call. Inst. . . , Mem. Loc ) MRB(CS) 46

Summary 52
Summary: Pointers ≠ Integers • Two pointer types: • Logical (malloc/alloca): data-flow provenance • Physical (inttoptr): control-flow provenance • AA: what’s the No. Alias/Must. Alias/Partial. Alias/May. Alias relation between 2 memory accesses? • Mod. Ref: what’s the (Must)No. Mod. Ref/Mod/Ref/Mod. Ref relation between 2 operations? • p ≠ (int*)(int)p • There’s no “free” GVN for pointers • Use new pointer analyses APIs to reduce compilation time 53
- Slides: 45