PMHS Library Guide five Referencing in Harvard Mr

PMHS Library Guide five Referencing in Harvard Mr. K. N. Naismith, Park Mains High School, Renfrewshire. 2019. 1

What do we mean by “referencing”? When you are writing a piece of work and use some else’s words or ideas you must reference them. This means that you need to include detailed information on all sources used, both within your text (intext citations) and at the end of your work (reference list or bibliography). 2

Why do we reference? 1. To give credit to the source 2. To avoid plagiarism, that is, claiming someone else's work as your own 3

Different types of sources Primary Source • An artifact, a document, a recording, or other source of information that was created at the time under study. Could also be a person with direct knowledge of a situation, or a document written by such a knowledge. 4

Secondary Source • A document or recording that relates or discusses information originally presented elsewhere. 5

Tertiary Source • An index and/or contextual consolidation of primary and secondary sources. Examples: bibliography, database etc. 6

How to reference Harvard referencing style 7

Journal Articles Wood, N. , Duffy, M. & Smith, S, J. (2007) ‘The art of doing (geographies of) music’, Environment and Planning D: Society and Space, 25, pp. 867 -889 8

Books Marshall, T. (2015) Prisoners of Geography: Ten Maps That Tell You Everything You Need To Know About Global Politics, London: Elliott and Thompson Limited 9
![Websites BBC (2016) Charities urge Cameron to Boost NHS and social care [Online] Available Websites BBC (2016) Charities urge Cameron to Boost NHS and social care [Online] Available](http://slidetodoc.com/presentation_image_h2/6e4046d28593ef89d61e797ef70f5827/image-10.jpg)
Websites BBC (2016) Charities urge Cameron to Boost NHS and social care [Online] Available from: http: //www. bbc. co. uk/ news/uk-35266706 [Accessed: 11 th January 2016] 10

Activities Create a reference for each of the sources handed out. Imagine these are the sources you have used for your project/dissertation. Use these to create a bibliography. 11
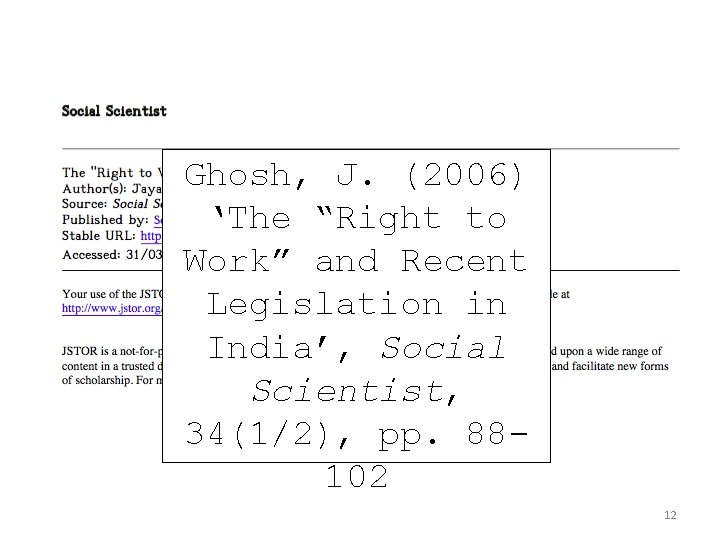
Ghosh, J. (2006) ‘The “Right to Work” and Recent Legislation in India’, Social Scientist, 34(1/2), pp. 88102 12

In practice, Harvard Chapter One: Introduction 1. 1 Overview of the dissertation Privacy has been argued to be a central concern for the library profession by several commentators over the years (Johnston, 2000, Sturges, 2003, Zimmer, 2013 b, Gorman, 2015). However, the increasing expansion of computer information technologies in service delivery poses challenges to this principle in several ways, especially around protection and usage of user data in linked internet formats (Kang, 1998, Hakkani-Tür et al. , 2005, Kesan et al. , 2013). This dissertation explores an expanding aspect of this debate, namely the increasing use of cloud-based services to host Library Management System (LMS) data. This is the first UK study to explore the phenomenon, and examines in detail the Scottish public library service as a detailed case study. Privacy for a person is a concept which has been an issue for centuries and for several decades it has been explicitly built into the ethics of librarians around the world. From the United States of America (US), the American Library Association (ALA) issued a Code of Ethics in 1939 which they have updated through the years (American Library Association, 2008). In the United Kingdom (UK), the first Code of Professional Practice was ratified and issued in 1983, again with regular updates (CILIP, 2012) and in a world setting with the International Federation of Library Associations (IFLA) Code of Ethics in 2012 (IFLA, 2012). 13

In practice, Harvard • Johnston, S. D. (2000) 'Rethinking Privacy in the Public Library'. International Information and Library Review, 32 (3 -4), pp. 509 -517. • Sturges, P. (2003) 'Doing the right thing: professional ethics for information workers in Britain'. New Library World, 104 (3), pp. 94102. • Zimmer, M. (2013 b) 'Patron Privacy in the “ 2. 0” Era: Avoiding the Faustian Bargain of Library 2. 0'. Journal of Information Ethics, 22 (1), pp. 44. • Gorman, M. (2015) Our enduring values revisited: librarianship in an ever-changing world. Chicago: ALA Editions, an imprint of the American Library Association. • IFLA (2012) IFLA Code of Ethics for Librarians and other Information Workers (full version). Available at: http: //www. ifla. org/publications/node/11092 (Accessed: 9 th March 2017). 14

In practice, Harvard Hakkani-Tür, D. et al. (2005) 'Document Sanitization in the Age of Data Mining'. In: Strandburg, K. J. and Raicu, D. S. (eds. ) Privacy and Technologies of Identity: A Cross- Disciplinary Conversation. Springer US. IFLA (2012) IFLA Code of Ethics for Librarians and other Information Workers (full version). Available at: http: //www. ifla. org/publications/node/11092 (Accessed: 9 th March 2017). Infor (2017) Library Software | Library Management System | Infor. Available at: http: //www. infor. com/industries/publicsector/libraries/ (Accessed: 11 th August 2017). Janger, E. and Schwartz, P. (2002) 'The Gramm- Leach- Bliley Act, information privacy, and the limits of default rules'. Minn. Law Rev. 15
Useful Websites • University of Strathclyde, CIS Faculty Librarian Guides. • Harvard. Accessed 17 th June 2019 http: //guides. lib. strath. ac. uk/ referencing_guide/harvard 16
Useful Websites • Glasgow Caledonian University • Harvard. Accessed 17 th June 2019 https: //www. gcu. ac. uk/library/s ubjecthelp/referencing/harvardr eferencing/ 17
Useful Websites • Imperial Collage London • Harvard. Accessed 17 th June 2019 https: //www. imperial. ac. uk/medi a/imperialcollege/administration-andsupportservices/library/public/harvard. pdf 18
Useful Websites • University of Aberdeen • Harvard. Accessed 17 th June 2019 https: //www. abdn. ac. uk/library/ documents/guides/qgcit 002. pdf • General guidance. Accessed 17 th June 2019 http: //www. abdn. ac. uk/library/d ocuments/guides/qgcit 001. pdf 19

References Naismith, K. N. (2017). A review of the use of Third-Party online catalogue provision in Scottish Public Libraries and any Data Protection implications. Glasgow: University of Strathclyde. 20
- Slides: 20