pilar PILAR standard quick tour infopilartools com version


- Slides: 41

pilar PILAR standard quick tour <info@pilar-tools. com> version 7. 4

PILAR standard tour - v 7. 4 2

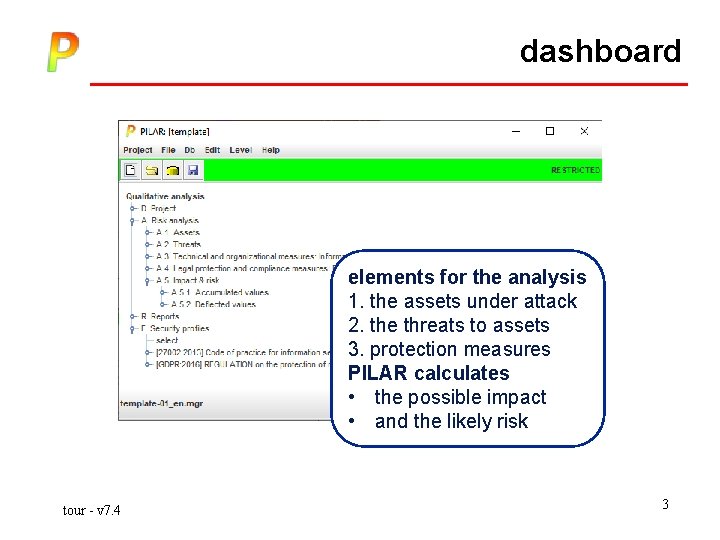
dashboard elements for the analysis 1. the assets under attack 2. the threats to assets 3. protection measures PILAR calculates • the possible impact • and the likely risk tour - v 7. 4 3

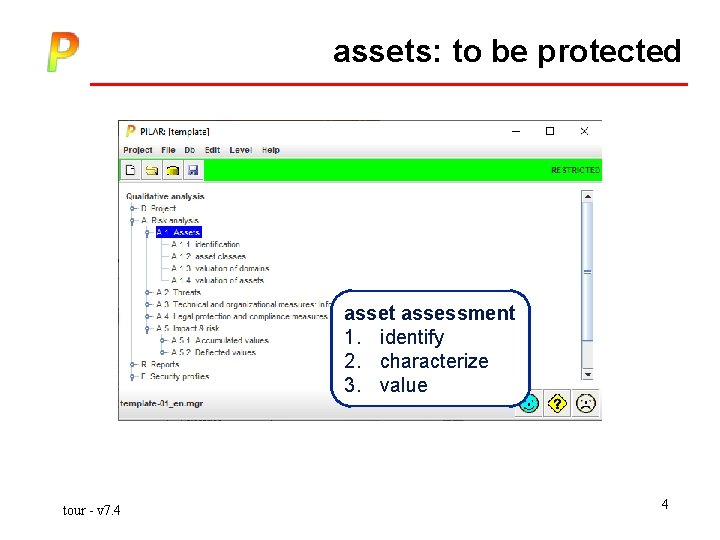
assets: to be protected asset assessment 1. identify 2. characterize 3. value tour - v 7. 4 4

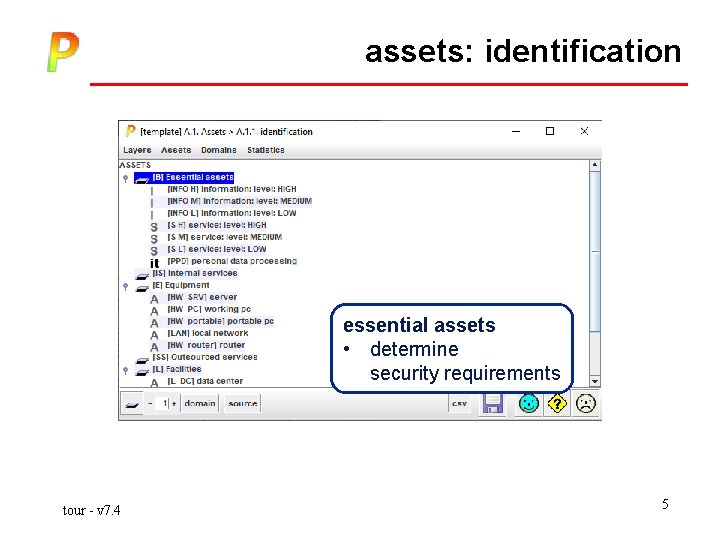
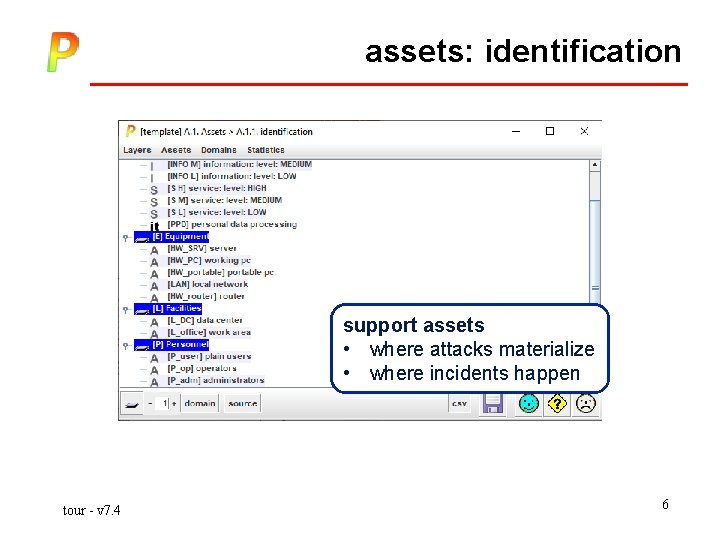
assets: identification essential assets • determine security requirements tour - v 7. 4 5

assets: identification support assets • where attacks materialize • where incidents happen tour - v 7. 4 6

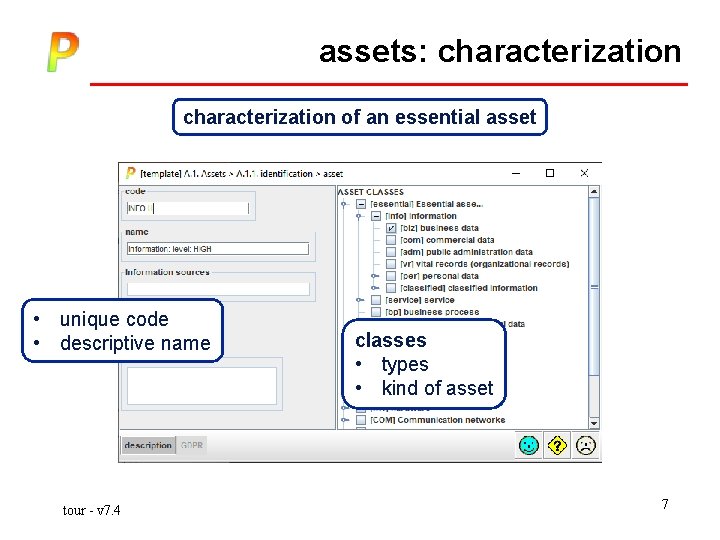
assets: characterization of an essential asset • unique code • descriptive name tour - v 7. 4 classes • types • kind of asset 7

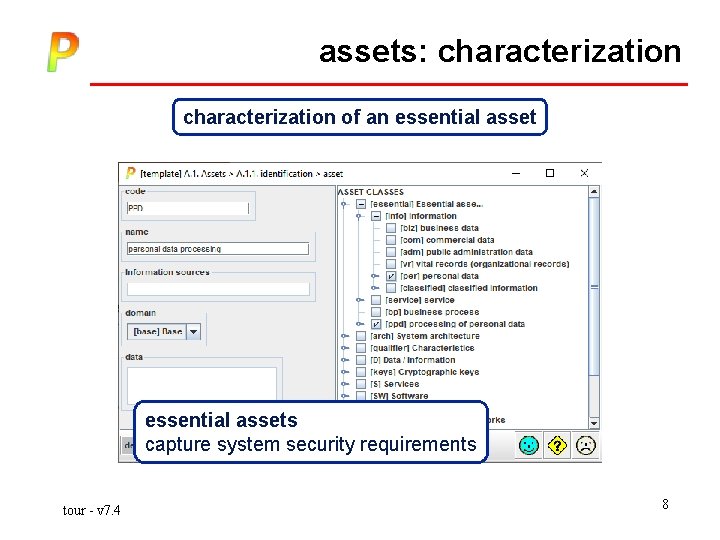
assets: characterization of an essential assets capture system security requirements tour - v 7. 4 8

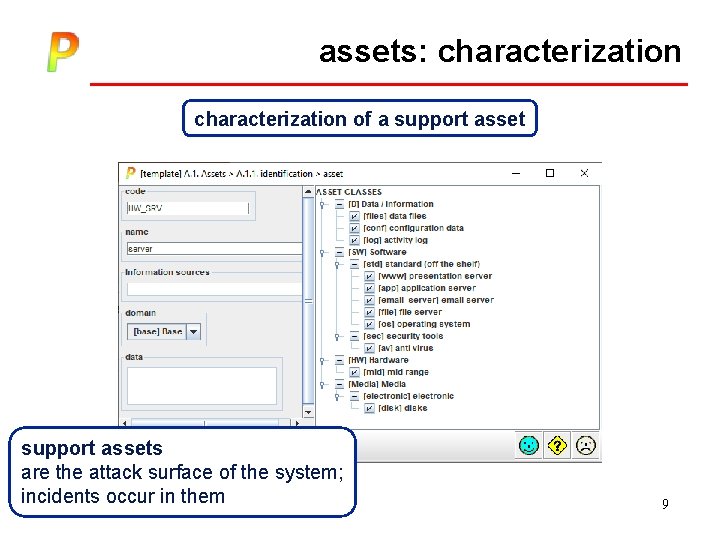
assets: characterization of a support assets are the attack surface of the system; incidents occur in them tour - v 7. 4 9

asset attributes tour - v 7. 4 10

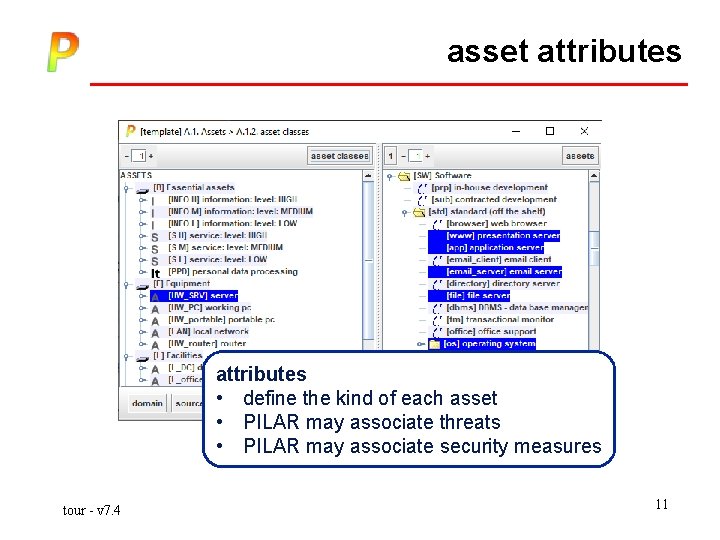
asset attributes • define the kind of each asset • PILAR may associate threats • PILAR may associate security measures tour - v 7. 4 11

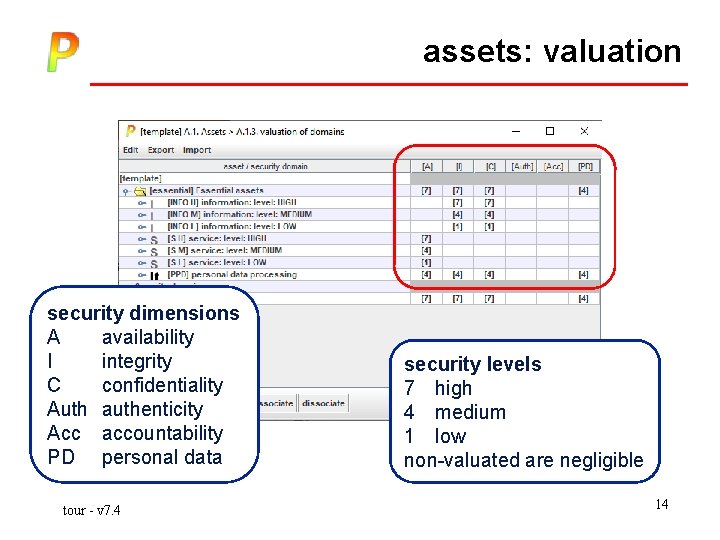
assets: valuation assets are grouped into security domains • you may valuate the domains, and every asset in the domain receives the same values • you could also valuate asset by asset. . . if needed tour - v 7. 4 12

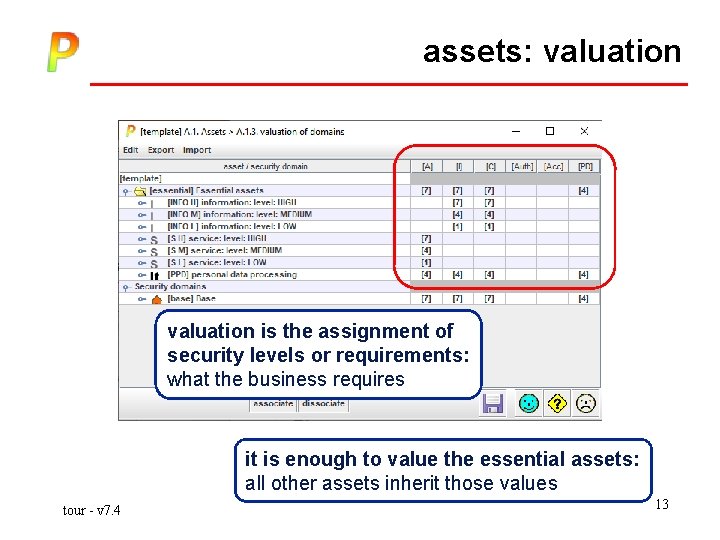
assets: valuation is the assignment of security levels or requirements: what the business requires it is enough to value the essential assets: all other assets inherit those values tour - v 7. 4 13

assets: valuation security dimensions A availability I integrity C confidentiality Auth authenticity Acc accountability PD personal data tour - v 7. 4 security levels 7 high 4 medium 1 low non-valuated are negligible 14

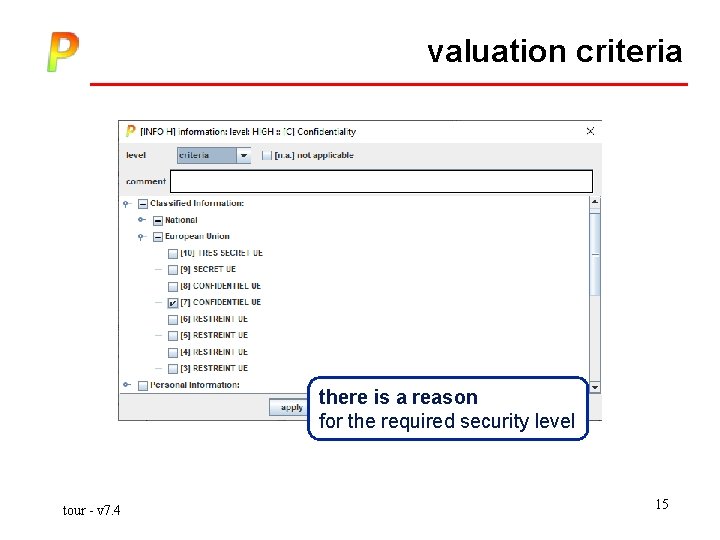
valuation criteria there is a reason for the required security level tour - v 7. 4 15

threats or security incidents: what can happen tour - v 7. 4 16

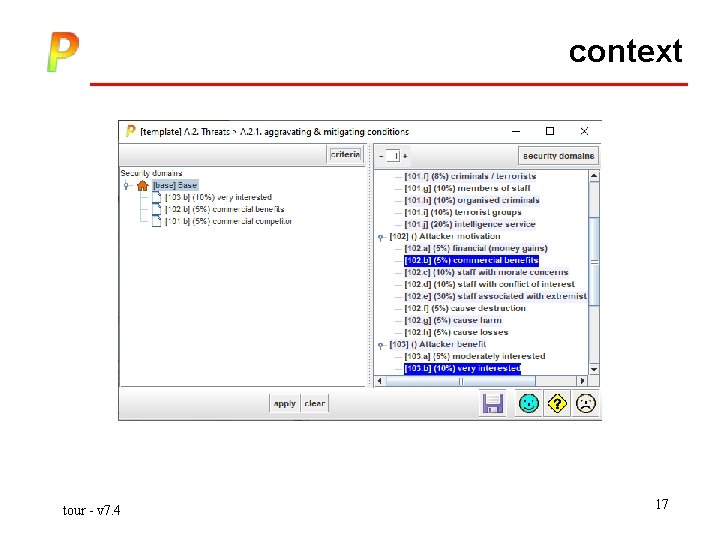
context tour - v 7. 4 17

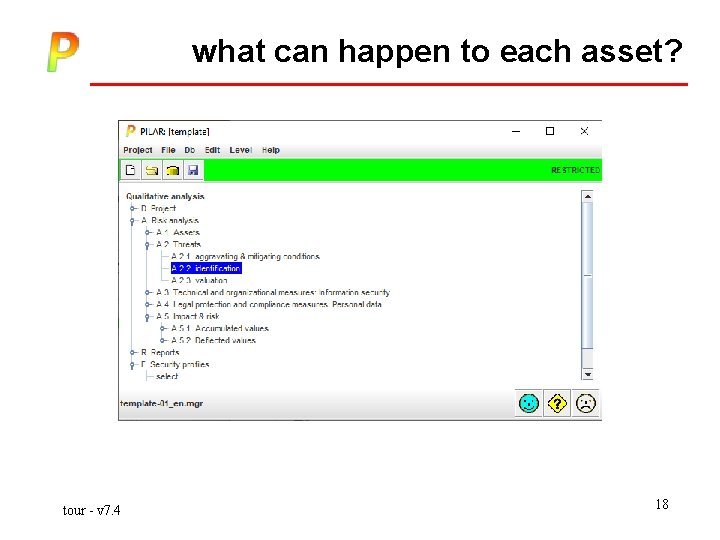
what can happen to each asset? tour - v 7. 4 18

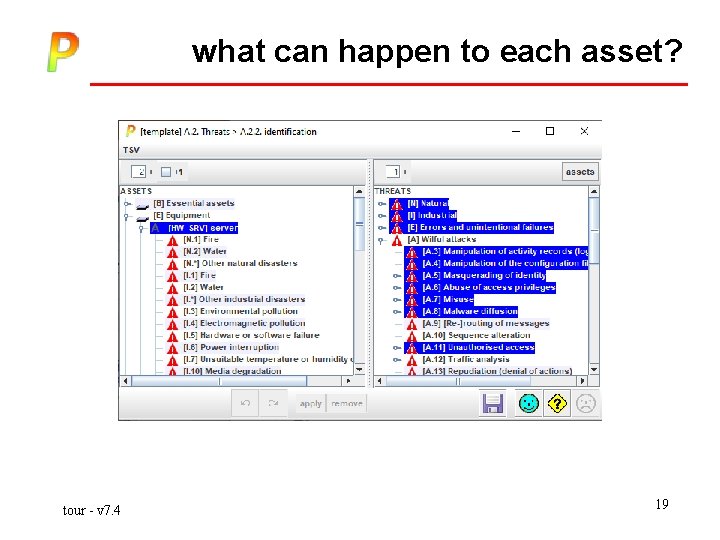
what can happen to each asset? tour - v 7. 4 19

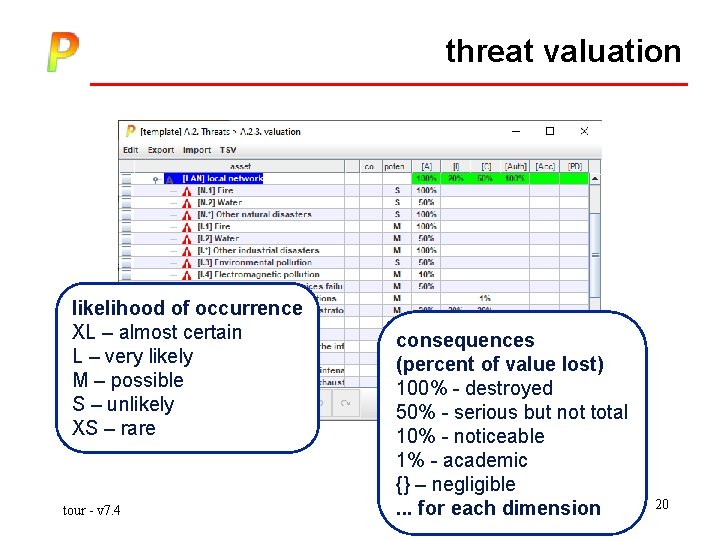
threat valuation likelihood of occurrence XL – almost certain L – very likely M – possible S – unlikely XS – rare tour - v 7. 4 consequences (percent of value lost) 100% - destroyed 50% - serious but not total 10% - noticeable 1% - academic {} – negligible. . . for each dimension 20

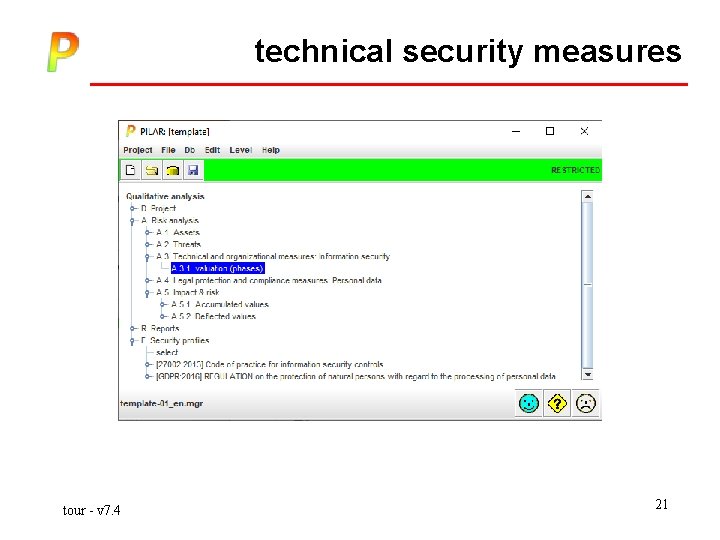
technical security measures tour - v 7. 4 21

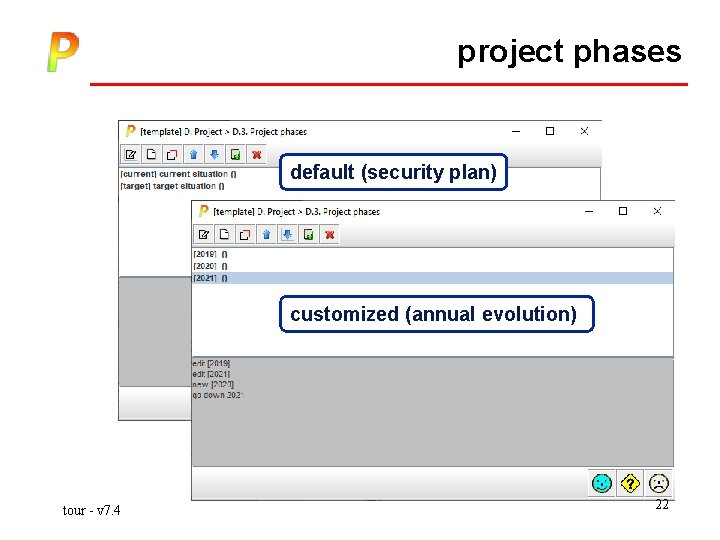
project phases default (security plan) customized (annual evolution) tour - v 7. 4 22

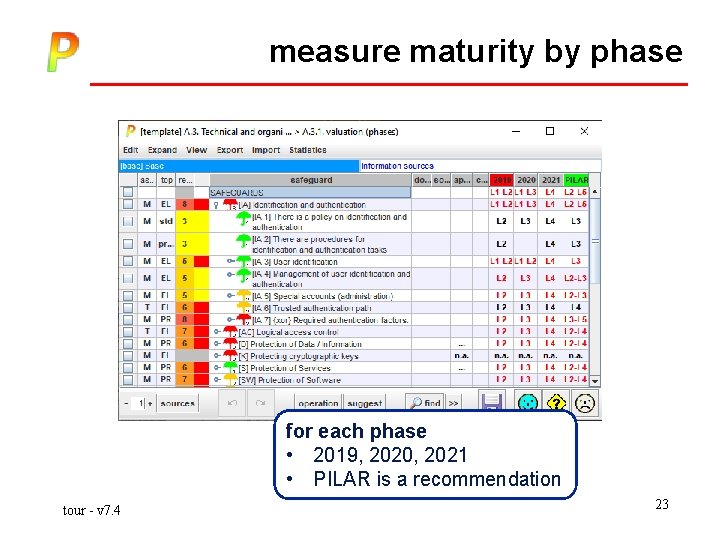
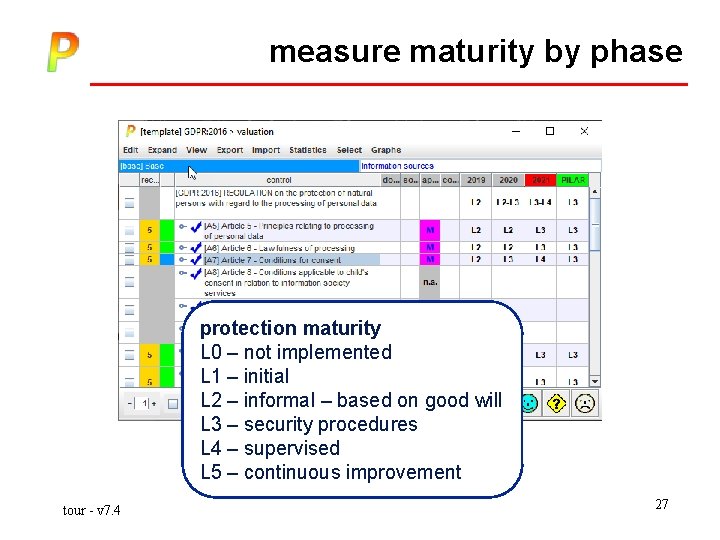
measure maturity by phase for each phase • 2019, 2020, 2021 • PILAR is a recommendation tour - v 7. 4 23

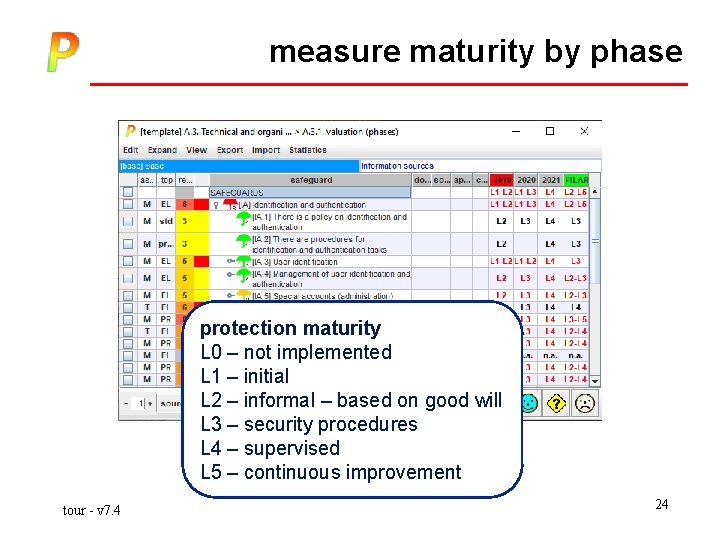
measure maturity by phase protection maturity L 0 – not implemented L 1 – initial L 2 – informal – based on good will L 3 – security procedures L 4 – supervised L 5 – continuous improvement tour - v 7. 4 24

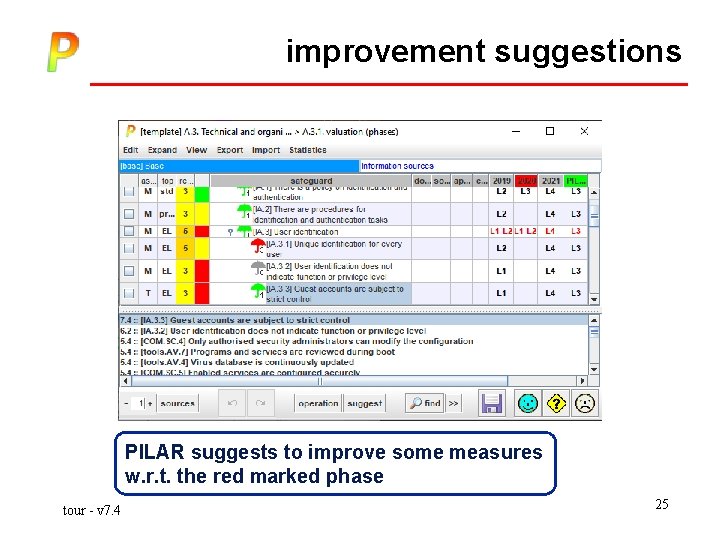
improvement suggestions PILAR suggests to improve some measures w. r. t. the red marked phase tour - v 7. 4 25

legal measures tour - v 7. 4 26

measure maturity by phase protection maturity L 0 – not implemented L 1 – initial L 2 – informal – based on good will L 3 – security procedures L 4 – supervised L 5 – continuous improvement tour - v 7. 4 27

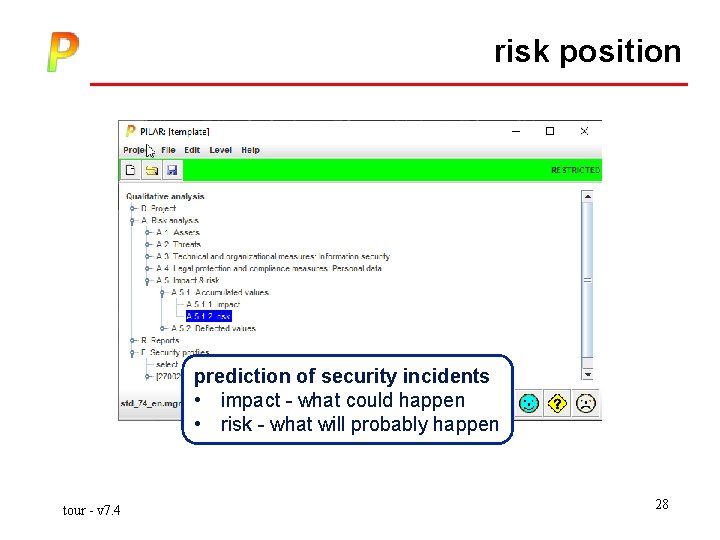
risk position prediction of security incidents • impact - what could happen • risk - what will probably happen tour - v 7. 4 28

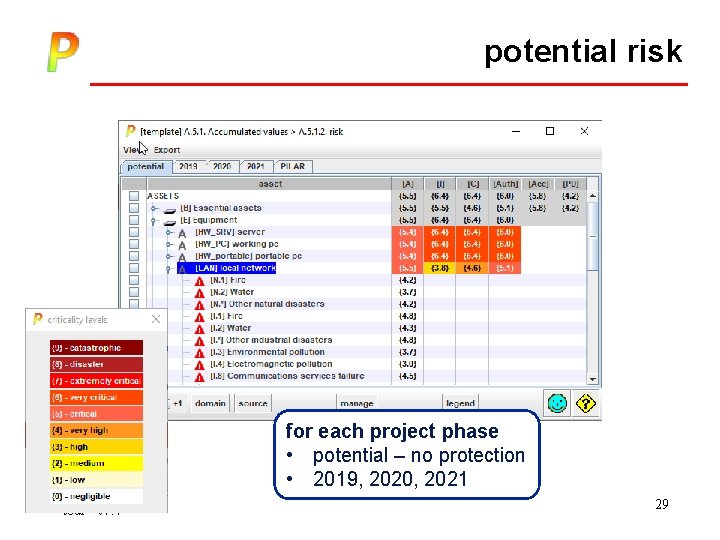
potential risk for each project phase • potential – no protection • 2019, 2020, 2021 tour - v 7. 4 29

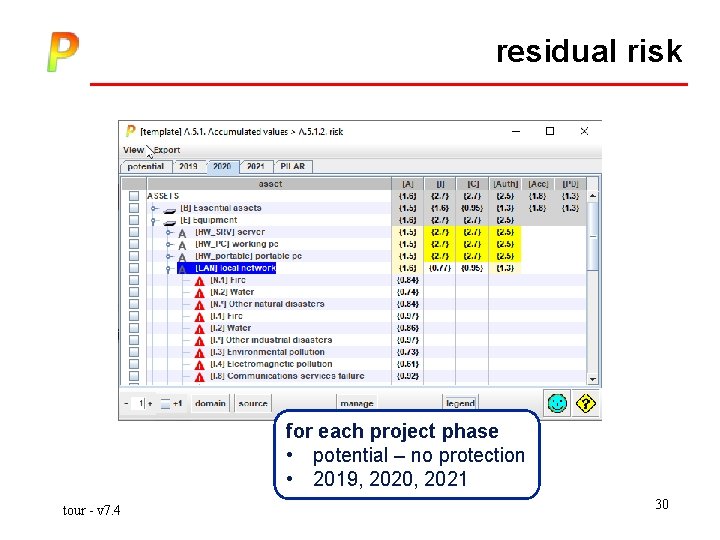
residual risk for each project phase • potential – no protection • 2019, 2020, 2021 tour - v 7. 4 30

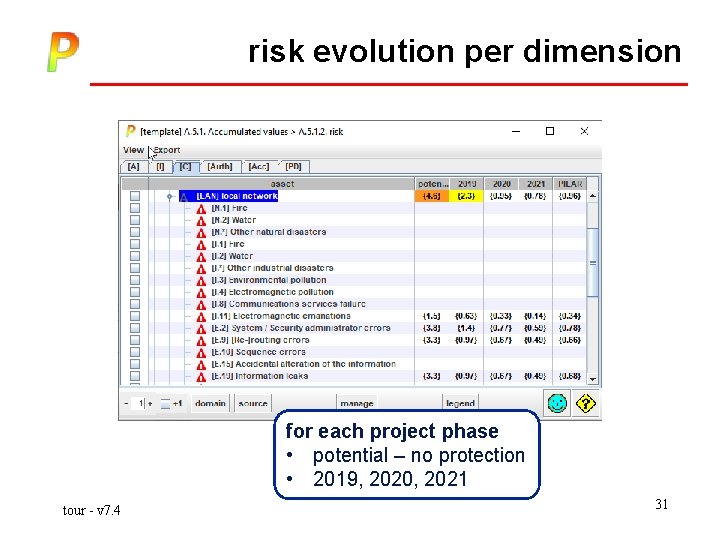
risk evolution per dimension for each project phase • potential – no protection • 2019, 2020, 2021 tour - v 7. 4 31

indirect risk on essential business tour - v 7. 4 32

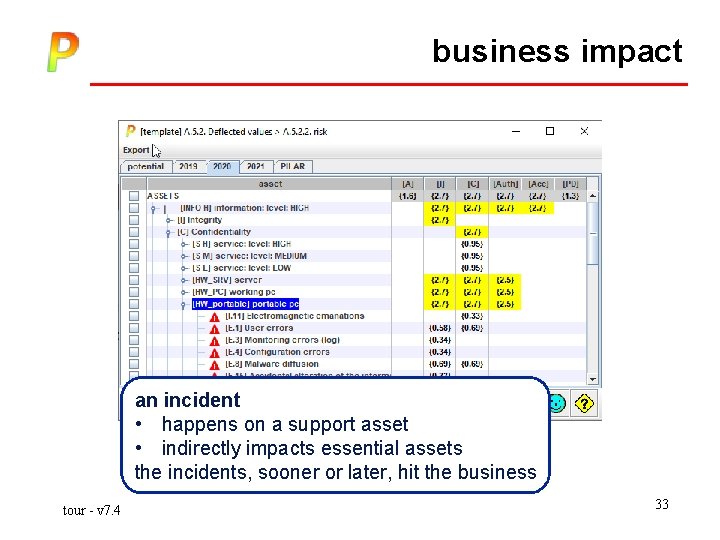
business impact an incident • happens on a support asset • indirectly impacts essential assets the incidents, sooner or later, hit the business tour - v 7. 4 33

template-based reports tour - v 7. 4 34

predefined graphical reports tour - v 7. 4 35

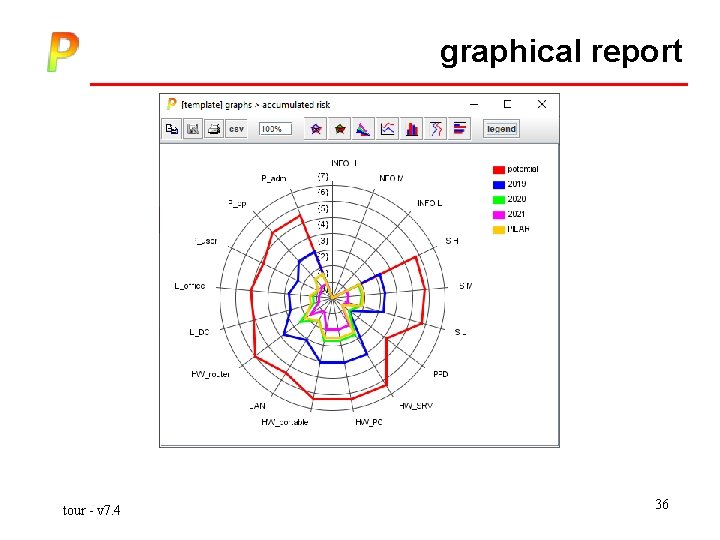
graphical report tour - v 7. 4 36

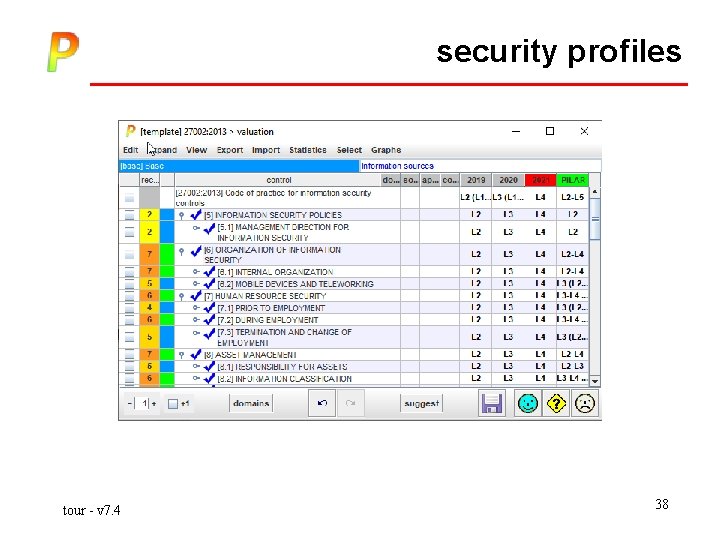
security profiles tour - v 7. 4 37

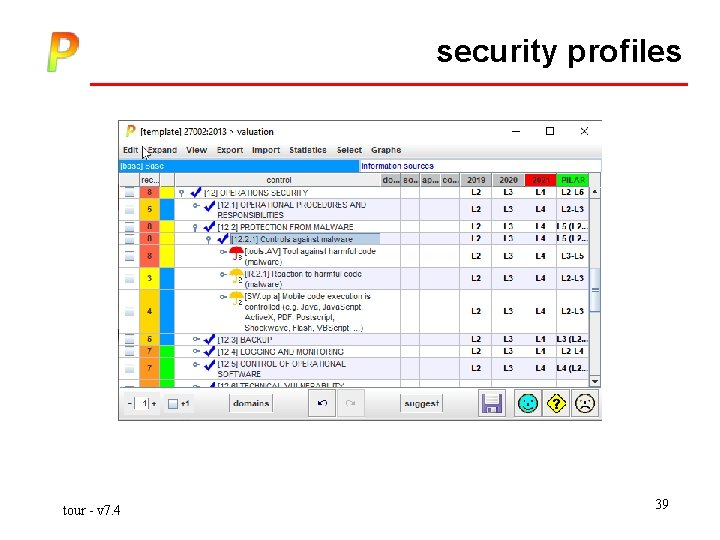
security profiles tour - v 7. 4 38

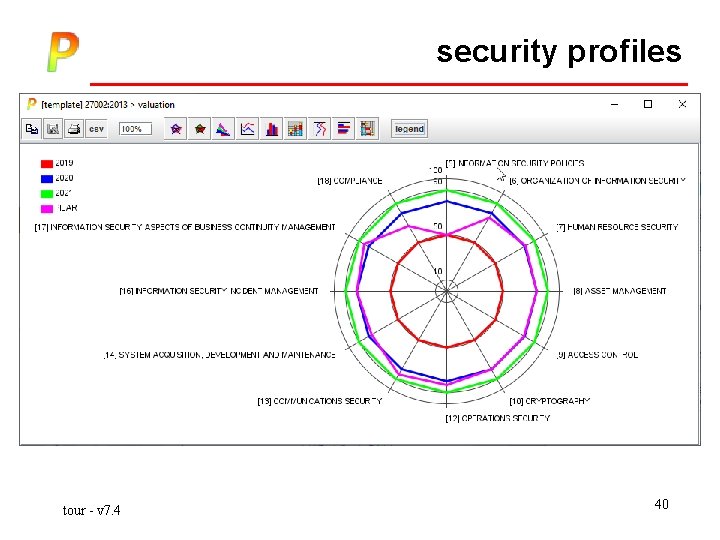
security profiles tour - v 7. 4 39

security profiles tour - v 7. 4 40

questions? support@pilar-tools. com tour - v 7. 4 41