PHYSICAL SECURITY PROFESSIONAL PSP Certification Examination Review October

PHYSICAL SECURITY PROFESSIONAL (PSP) Certification Examination Review October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT ASIS Board Certification The worldwide standard for professional competency. Offering three security certifications, including two specialty certifications. • Certified Protection Professional (CPP) • Physical Security Professional (PSP) Focus of this review • Professional Certified Investigator (PCI) ASIS board-certified security practitioners are employed by more than 3, 500 organizations in 77 countries around the globe. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security Awarded to practitioners who have demonstrated knowledge and experience in: • Physical Security Assessment • Application, Design, and Integration of Physical Security Systems • Implementation of Physical Security Measures October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security PSP EXAM CONTENT • Candidate must pass a comprehensive examination • Approximately 125 multiple-choice questions o 100 “live” scoreable questions o Up to 25 pre-test questions October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security ALL PSP EXAM QUESTIONS ARE FROM THE REVIEW MATERIALS • “Physical Security Principles” (hardcover, softcover, or Kindle) • “Implementing Physical Protection Systems: A Practical Guide, 2 nd Ed” (hardcover, softcover, or Kindle) • “ASIS Business Continuity Guideline: A Practical Approac”h (PDF or print) • “ASIS Facilities Physical Security Measures Guideline” (PDF or print) • • • https: //www. asisonline. org/ASIS-Store/Certification/Pages/PSP-Reference-Material. aspx https: //www. amazon. com/Physical-Security-Principles-Michael-Knokeebook/dp/B 016 Z 1 GL 46/ref=pd_sbs_351_6? _encoding=UTF 8&psc=1&ref. RID=0 YDY 5 R 71 ECX 6 P 3 QYJGVK https: //www. amazon. com/Implementing-Physical-Protection-Systems-Practicalebook/dp/B 00 D 675 XPG/ref=pd_sim_351_1? _encoding=UTF 8&psc=1&ref. RID=F 6 ZR 5 FTP 5 D 8 TZ 5 C 5 B 6 PQ October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security REMEMBER: • ALL PSP EXAM QUESTIONS ARE FROM THE REVIEW MATERIALS • ALL QUESTIONS ARE BASED ON THE DOMAINS, TASKS & REQUIRED KNOWLEDGE • The specific subject areas (Domains – Tasks – Knowledge subjects) can be found here: https: //www. asisonline. org/Certification/Board. Certifications/PSP/Pages/PSP-Exam-Domains-and-Knowledge. Statements. aspx • ALL 125 “scoreable” exam questions are divided based on the following breakdown: October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security ALL 125 “scoreable” exam questions are divided based on the following breakdown: Domains (Subjects) 32% 34% Physical Security Assessment Application, Design and Integration of Physical Security Systems Implementation of Physical Security Measures Total October 2017 % of # of Questions 34% 42 32% 41 100% 125 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security Application for the Exam: • Apply online (if you can pay with a credit card online) • Cost: o ASIS Members: US$300 o Non-ASIS Members: US$450 • Are you eligible to be approved to take the exam? October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security Application for the Exam: • A high level of English comprehension both written and oral. • An earned Bachelor's degree or higher from an accredited institution of higher education and four (4) years of physicalsecurity experience. OR • A high level of English comprehension both written and oral. • An earned High School Diploma or Associate's Degree (College Diploma) and six (6) years of physical-security experience. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security Application for the Exam – Defining Experience: • Experience is defined as having: o Experience as a security professional in the protection of assets, in the public or private sector, criminal justice system, government intelligence, or investigative agencies. o Experience with companies, associations, government, or other organizations providing services or products, including consulting firms, provided the duties and responsibilities substantively relate to the design, evaluation, and application of systems, programs, or equipment, or development and operation of services, for protection of assets in the private or public sectors. o Experience as a full-time educator on the faculty of an accredited educational institution, provided the responsibilities for courses and other duties relate primarily to knowledge areas pertinent to the management and operation of protection of assets programs in the public or private sectors. October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security Application for the Exam: • Apply online but print off a paper application first, complete it, then apply online. (Recommend allowing the Review Instructor to assess the application before submitting) • Apply ASAP – Once approved a candidate has up to 90 -days to schedule a test. • Once approved, the exam is conducted at a Prometric Testing Center • Prometric (www. prometric. com/ASIS) has testing centers in Dammam, Manama (Bahrain) & Doha (Qatar) • Testing rules - https: //www. asisonline. org/Certification/Resources/Documents/CBT-Fact. Sheet. pdf October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security What is the Passing Grade: • Each question is pretested to determine a level of difficulty. • Since each question has a different difficulty level – questions are not scored based on a percentage correct our of a total (example: 50/100 = 50%) • Scaled Scoring is the method used to measure the passing score. • Candidates must achieve 650 to successfully pass the exam. • To learn more about scaled scoring – search on Google. • THERE IS NO RELATIONSHIP TO A PERCENTAGE SCORE! October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Professional (PSP) Board Certification in Physical Security MUST READ RESOURCE: • The Professional Certification Guide • file: ///Users/dennisshepp/Documents/ASIS%20 Saudi%20 CPP&PSP%2 0 Review/Certification%20 Handbook_final. pdf October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Contact for PSP Review Instructor/Facilitator: Dennis Shepp, CPP Email 1: dennisshepp@shaw. ca Email 2: dennisshepp@gmail. com Telephone: +1. 587. 989. 1511 Skype: dennisshepp October 2017 Dennis Shepp, CPP
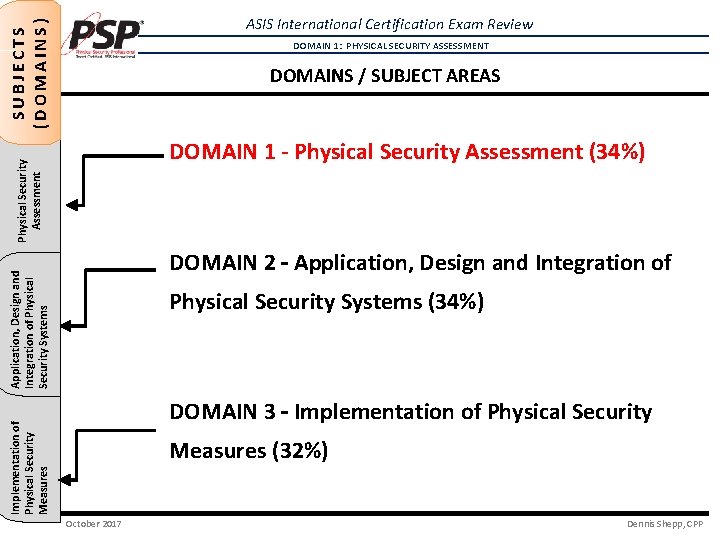
SUBJECTS (DOMAINS) ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT DOMAINS / SUBJECT AREAS ACCESS CONTROL Application, Design and Physical Security SYSTEMS Integration of Physical Assessment Security Systems DOMAIN 1 - Physical Security Assessment (34%) DOMAIN 2 – Application, Design and Integration of Physical Security Systems (34%) Implementation of Physical Security Measures DOMAIN 3 – Implementation of Physical Security Measures (32%) October 2017 Dennis Shepp, CPP

PHYSICAL SECURITY PROFESSIONAL (PSP) Certification Examination Review 1 DOMAIN PHYSICAL SECURITY ASSESSMENT (34%) October 2017 Dennis Shepp, CPP

Implementation of Physical Security Measures ACCESS CONTROL Application, Design and Physical Security SYSTEMS Integration of Physical Assessment Security Systems SUBJECTS (TASKS) ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT TASKS TO LEARN • TASK 1: Develop a physical security assessment plan. • TASK 2: Identify assets to determine their value, criticality, and loss impact. • TASK 3: Assess the nature of the threats so that the scope of the problem can be determined. • TASK 4: Conduct an assessment to identify and quantify vulnerabilities of the organization. • TASK 5: Perform a risk analysis so that appropriate countermeasures can be developed. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan TASK TO LEARN TASK 1: Develop a physical security assessment plan. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: 1. Risk assessment models and considerations 2. Qualitative and quantitative assessment methods 3. Key areas of the facility or assets that may be involved in assessment 4. Types of resources needed for assessment October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Risk assessment models and considerations Risk Assessment: The process of assessing security-related risks from internal and external threats to an entity, its assets and personnel. (Facilities Physical Security Guideline, ASIS International, Page 3) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review Physical Security Assessment Plan DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Security Survey: • Most common reliable tool for determining adequacy and foreseeability • Focuses on: o The risks to the physical assets and property o The protection measures (against any risk) that comprise the realm of physical security • Measures three basic factors: quality, reliability and cost (Michael E. Knoke. Physical Security Principles (Kindle Locations 1374 -1375). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment Plan DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Security Survey: • More than a checklist - uses techniques of: o Observing o Questioning o Analyzing o Verifying o Investigating o Evaluating. (Michael E. Knoke. Physical Security Principles (Kindle Locations 13761377) Page 34. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Security Survey: • A comprehensive risk assessment focuses equally on assets, threats, vulnerabilities, & consequences • Security survey places more emphasis on vulnerabilities. (Michael E. Knoke. Physical Security Principles (Kindle Locations 14031404). Page 35. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Vulnerability: • Security vulnerability: “An exploitable security weakness” 1 • “a weakness or organizational practice that may facilitate or allow a threat to be implemented or increase the magnitude of a loss event” 2 1. (Facilities Physical Security Guideline, ASIS International, Page 4) 2. (Michael E. Knoke. Physical Security Principles (Kindle Locations 791 -792). Page 6. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Vulnerability versus Threats: • Vulnerability is a characteristic of the organization or facility – controllable to some degree. • Threats are usually outside the control of the organization. (Michael E. Knoke. Physical Security Principles (Kindle Locations 7941 -795). Page 6. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Vulnerability Assessment: • Used in CPTED assessments • Used as part of “Design Basis” assessments (countermeasures designed to protect against specific threats. ) (Michael E. Knoke. Physical Security Principles (Kindle Locations 5252 & 10618). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Risk assessment models are based on the following baseline approach: ASSETS THREATS (Michael E. Knoke. Physical Security Principles (Kindle Locations 1163 -1165). ASIS International. Kindle Edition. ) VULNERABILITIES IMPACT ANALYSIS October 2017 MITIGATION Dennis Shepp, CPP

ASIS General Security Risk Assessment Guideline (2003), page 7

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Qualitative and quantitative assessment methods • “Each component of the assessment process must be evaluated, either qualitatively or quantitatively. ” (Michael E. Knoke. Physical Security Principles (Kindle Locations 1196 -1198). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Qualitative analysis: • Any approach that does not use numbers or numeric values to describe the risk components. • Terms such as critical, high, medium, low, and negligible may be used to gauge the asset value & levels of risk components & risk itself. • Most suitable when evaluating basic security applications. (Michael E. Knoke. Physical Security Principles (Kindle Locations 1202 -1205). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Quantitative analysis: • Uses numeric measures to describe the value of assets or the level (severity or probability) of threats, vulnerabilities, impact, or loss events. • Varies from simple scale ratings (1 to 5) to sophisticated statistical methods and mathematical formulas. (Michael E. Knoke. Physical Security Principles (Kindle Locations 1205 -1208). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Quantitative analysis: • Used to measure effectiveness of a physical protection system (PPS) where primary functions are to detect, delay, and respond. (Michael E. Knoke. Physical Security Principles (Kindle Locations 1205 -1209). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
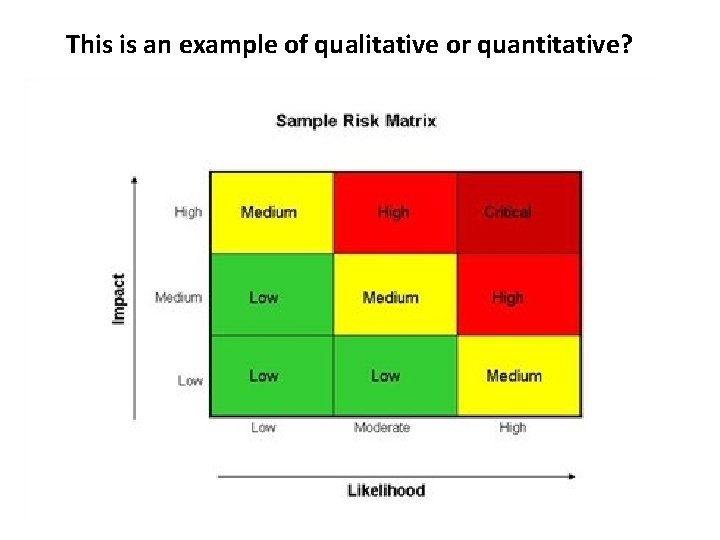
This is an example of qualitative or quantitative?
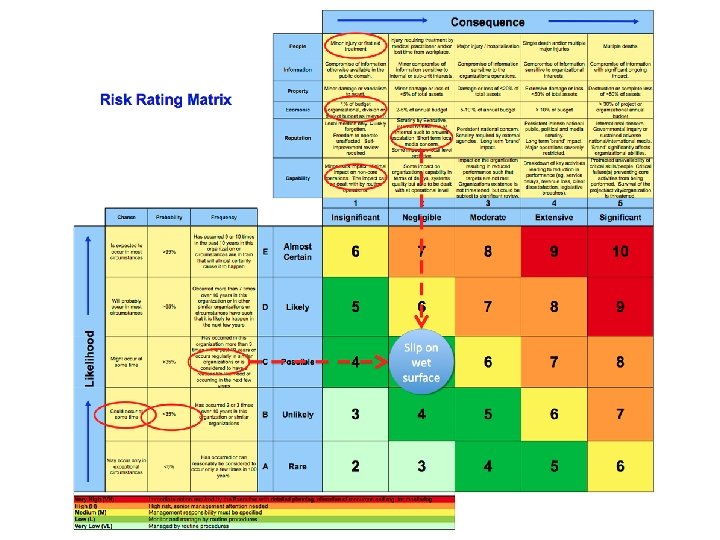
This is an example of qualitative or quantitative?

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Assessment approaches: • Outside-Inward Approach o Assessment team acts as adversary o Attempts to penetrate into facility o Local environment & criminal activity considered o Team moves between layers (outer – middle – inner) • Inside Outward Approach o Assessment team acts as defender (security professional) o Focus from inside outward o How do defenses measure “deter – detect – delay - deny” concept (Michael E. Knoke. Physical Security Principles (Kindle Locations 1425 -1429). ASIS International. Kindle Edition) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Assessment approaches: • Functional Security Discipline Approach o Follows the outline of the book “Physical Security Principles” o Security Architecture & Engineering (Chap. 7) o Structural Security Measures (Chap. 9) o CPTED (Chap. 10) o Electronic Security Systems (Chap. 11) o Security officers & the Human Element (Chap. 12) (Michael E. Knoke. Physical Security Principles (Kindle Locations 14591470). ASIS International. Kindle Edition) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Evaluation of these functional areas and disciplines must be integrated with: • Consideration of environmental factors • Peripheral risks (e. g. , neighbors • Relevant policies and procedures. (Michael E. Knoke. Physical Security Principles (Kindle Locations 14741475). ASIS International. Kindle Edition) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment Plan DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Key areas of the facility or assets that may be involved in assessment • Teams should evaluate potential risk from: o Neighbors o Surrounding area • Evaluate facility’s: o Perimeter barriers (fences, gates) & outer bldgs o Property perimeter = Outer ring o Building's perimeter = Middle ring o Internal controls = Inner ring (Michael E. Knoke. Physical Security Principles (Kindle Locations 14981501). ASIS International. Kindle Edition & ASIS Int’l Guideline, Facilities Physical Security, pges 5 - 9. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Typical areas to assess: • • • Barriers (Examples) Doors (Door components) Windows (Components) Other openings (Describe) Locks (Details) Safes & Containers (Types) Signs (Describe) Lighting (Describe) Alarm & Detection (Types) (Michael E. Knoke. Physical Security Principles (Kindle Locations 15011585). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Typical areas to assess (cont. ): • • • Electronic security systems (Describe) Security officer services (Explain) Vehicle, traffic & parking controls (Describe) Utilities security (Describe) Visitor management (Explain) Package & mail handling (Describe) (Michael E. Knoke. Physical Security Principles (Kindle Locations 15011585). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Testing the security (with management’s permission): • Shipping & Receiving • Alarms • Computer server area • Access controls (Michael E. Knoke. Physical Security Principles (Kindle Locations 1600 -1601). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: More Assessment approaches: SWOT Analysis • Strengths, weaknesses, opportunities, and threats • Technique originated in the business management community but can easily be adapted to security. • “SWOT is a situational business analysis that involves a strategic evaluation of key internal and external factors. ” (Michael E. Knoke. Physical Security Principles (Kindle Locations 14791483). ASIS International. Kindle Edition) October 2017 Dennis Shepp, CPP
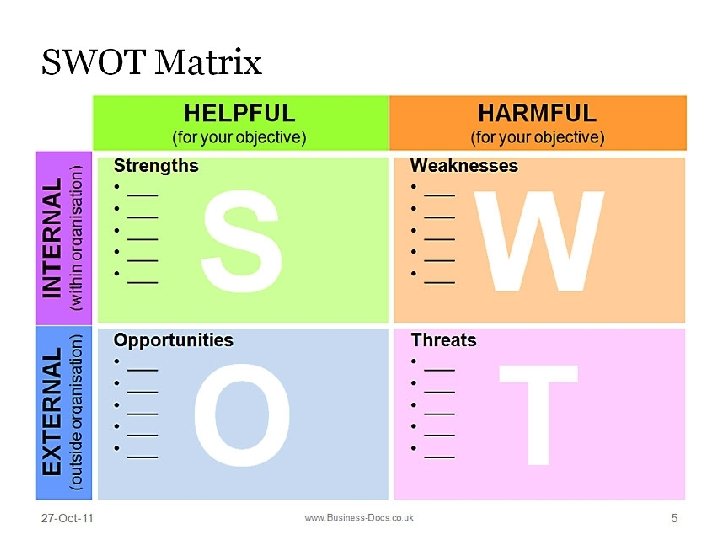
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Types of resources needed for assessments • Leveraging outside resources o Consultants (Pros) § “Fresh, untainted views” § Expertise § Current best practice knowledge § Strengthens position if audited o Consultants (Cautions) § Chose carefully based on expertise, specialty, professionalism & independence § Agreements should be clear § Bring in from project start – avoids scope creep (Michael E. Knoke. Physical Security Principles (Kindle Locations 13561368). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: CAUTIONS: • Avoid: o Conducting the assessment internally. o Influence by “salesmen” – not specialists • Leads to inadequate security & false sense of protection (Michael E. Knoke. Physical Security Principles (Kindle Locations 1368 -1362). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan TASK TO LEARN TASK 2: Identify assets to determine their value, criticality and loss impact. October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: 1. Definitions and terminology related to assets, value, loss impact and criticality. 2. The nature and types of assets (tangible and intangible). 3. How to determine the value of various types of assets and business operations. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Definitions and terminology related to assets, value, loss impact and criticality. • An asset is a resource of value to a business, organization, or individual. • Tangible, intangible, or mixed (for example, the people who make up the workforce in a company). • “Anything the company wants to protect because it is valuable, needs it to maintain business continuity, or it is difficult to replace in a timely fashion” (Michael E. Knoke. Physical Security Principles (Kindle Location 1225 -1257). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • The first step in risk assessment is identification and valuation of assets 1 • Asset – Any tangible or intangible value (People, property & information) to the organization. 2 1. (Michael E. Knoke. Physical Security Principles (Kindle Location 765). ASIS International. Kindle Edition. ) 2. (Facilities Physical Security Guideline, ASIS Int’l, Pge 2 October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • Asset Identification determines which assets are critical to the operation of the company. • Consider the company’s primary services and critical activities, as well as the site’s occupants and visitors. • Identifying a company’s critical assets is a three-step process: (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 984 -988). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • Step 1: Define and understand the company’s primary business functions and processes. • Step 2: Identify site and building infrastructure and systems: — Critical components — Life safety systems and safe haven areas — Secure and restricted areas (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 984 -996). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • Step 3: Identify the company’s critical tangible and intangible assets: — People — Information systems and data — Intellectual property — One-of-a-kind assets — High-value assets (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 984 -996). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • Risk is the potential for loss / damage to an asset. o Accounts the value of an asset, the threats or hazards that potentially impact the asset, and the vulnerability of the asset to the threat or hazard. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 959 -961). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: • An asset may be more critical or less critical. o Depends on organization’s mission o Resources used to perform that mission o How those resources interface with one another to achieve goals o How the organization would cope or maintain business continuity if any of the assets were lost. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 981 -983). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: The nature and type of assets (tangible and intangible) • Some assets are tangible, such as buildings, facilities, equipment, activities, operations, and some types of information. • Some assets are intangible, such as company processes, some types of information, and reputation. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 974 -981). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: How to determine the value of various types of assets and business operations • Asset value can be considered the economic replacement cost for infrastructure and equipment. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 981 -983). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Value assets by priority, consider the following: • Injuries or deaths related to facility or infrastructure damage • Replacement costs of assets • Loss of revenue due to lost functions • Existence of backups and system redundancy • Availability of replacements • Critical support agreements and lifelines in place • Critical or sensitive information value • Impact on reputation and revenue (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 997 -1005) October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Direct costs: • Financial losses like the value of goods lost or stolen • Increased insurance premiums • Deductible expenses on insurance coverage • Lost business from a loss event (stolen goods cannot be sold to consumers) • Labor expenses incurred as a result of the event • Management time dealing with the event • Damage awards not covered by ordinary insurance (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1007 -1014). October 2017 Dennis Shepp, CPP
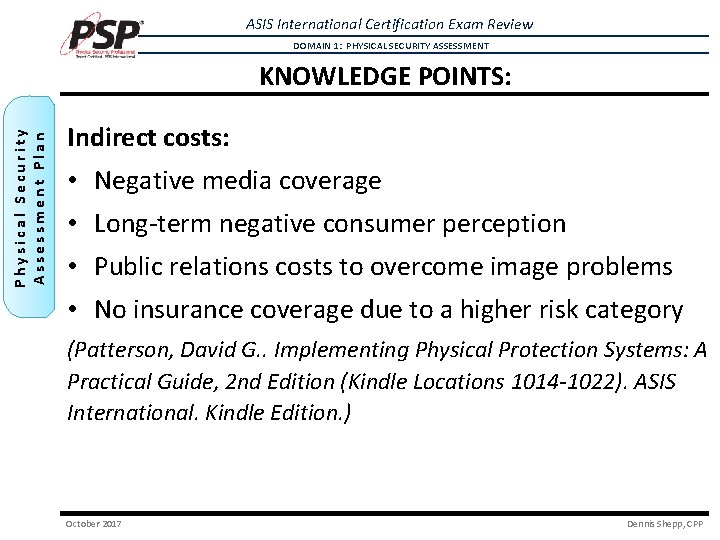
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Indirect costs: • Negative media coverage • Long-term negative consumer perception • Public relations costs to overcome image problems • No insurance coverage due to a higher risk category (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1014 -1022). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Indirect costs (cont. ): • Higher wages needed to attract future employees because of negative perceptions about the enterprise • Shareholder lawsuits for mismanagement • Poor employee morale, higher turnover, etc. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1014 -1022). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Key Risk Concepts - No security program should be implemented without: • Identifying the assets the company is trying to protect • The threats against those assets • How vulnerable the assets are to the various threats. • Values can be assigned to these three components of risk to provide an overall security risk rating. October 2017 Dennis Shepp, CPP
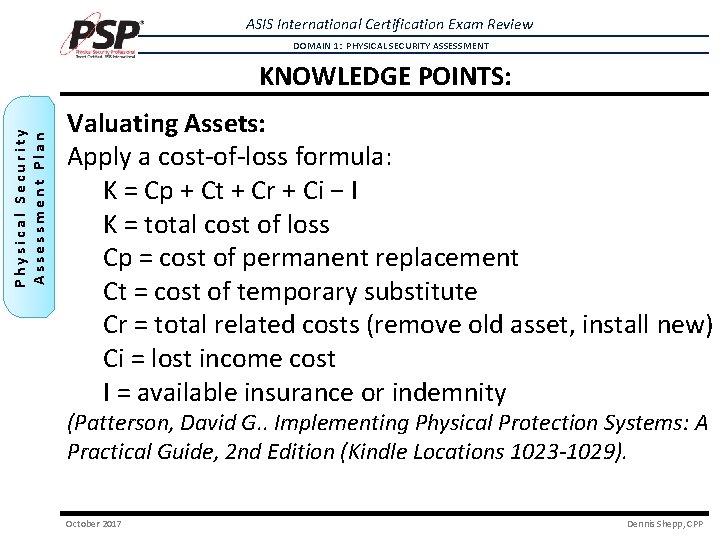
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Valuating Assets: Apply a cost-of-loss formula: K = Cp + Ct + Cr + Ci − I K = total cost of loss Cp = cost of permanent replacement Ct = cost of temporary substitute Cr = total related costs (remove old asset, install new) Ci = lost income cost I = available insurance or indemnity (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1023 -1029). October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Asset value rating x Threat likelihood rating x Severity of incident rating x Vulnerability rating = Security Risk Rating Risk can be defined as the potential for loss of or damage to an asset. It takes into account the value of an asset, the threats or hazards that potentially impact the asset, and the vulnerability of the asset to the threat or hazard Chapter 4: Risk Assessment Models, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 964). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment Plan KNOWLEDGE POINTS: Valuating Assets: • Assign assets a relative value (number from 1 (low) to 5 (high), based on priority). 1 • Executive decision makers need to be educated with respect to intangible and mixed assets. 2 • Such assets are certainly subject to loss events & cannot be ignored because of intangible value • They can have a significant impact on the organization’s vitality and mission performance. 1. (Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1023 -1029). ASIS International. Kindle Edition. ) 2. Michael E. Knoke. Physical Security Principles (Kindle Locations 1252 -1254). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment TASK TO LEARN TASK 3: Assess the nature of the threats so that the scope of the problem can be determined. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: 1. The nature, types, severity, and likelihood of threats and hazards (e. g. , natural disasters, cyber, criminal events, terrorism, socio-political, cultural) 2. Operating environment (e. g. , geography, socioeconomic environment, criminal activity) 3. Potential impact of external organizations (e. g. , competitors, supply chain, organizations in immediate proximity) on facility’s security program 4. Other external factors (e. g. , legal, loss of reputation, economic) and their impact on the facility’s security program October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: The nature, types, severity, and likelihood of threats and hazards (e. g. , natural disasters, cyber, criminal events, terrorism, socio-political, cultural) Threats are categorized: 1. Intentional threats • Study of potential adversaries • Use Adversary Sequence Diagrams • IDENTIFY RESOURCES TO ID POTENTIAL THREATS • IDENTIFY POTENTIAL ADVERSARIES & THREATS (Michael E. Knoke. Physical Security Principles (Kindle Location 1264). ASIS International. Kindle Edition. ) October 2017 Dennis Shepp, CPP

3. 2. 2 EVALUATING THREATS Physical Security Principles (Kindle Locations 1262 -1268). Threats can be divided into three categories: • Intentional threats - evaluation is based on identification and study of potential adversaries. • Assessors should think outside the box when listing potential adversaries: not just employees but also terrorist organizations, organized crime groups, aggressive business competitors, and activist groups (such as environmental groups). • The identification and assessment of adversaries is more asymmetric (less conventional and more difficult to define).

• Natural threats - typically evaluated using historical trends and statistics. • Long-term data collected on weather and other natural hazards for specific geographic areas, terrains, and environments. • Natural hazard effects data has been assembled for some particular industry sectors or facility types. • Assessors must recognize the unexpected can and usually does occur. • Comprehensive contingency planning and at least some degree of all-hazard preparedness is strongly recommended Inadvertent threats. accidents, errors, and omissions. • Subset of the inadvertent threat is the peripheral threat— for example, a threat that is targeted at a neighboring facility but that may have a major impact on one’s own operation.

• Peripheral threats can include utility interruptions, required evacuations, closure of access routes, unwanted attention or traffic, full or partial operations shutdowns, productivity disruptions, and environmental affects (e. g. , smoke, debris, water or chemical runoff, etc. ). • Inadvertent threats are the most difficult to predict and prepare for. • The nature of the workforce, operations, or other environmental factors may suggest a level of inadvertent threat, there is usually little or no historical data to use for planning purposes. • The best defenses are preparation, education and awareness, and the realization that the threat exists.
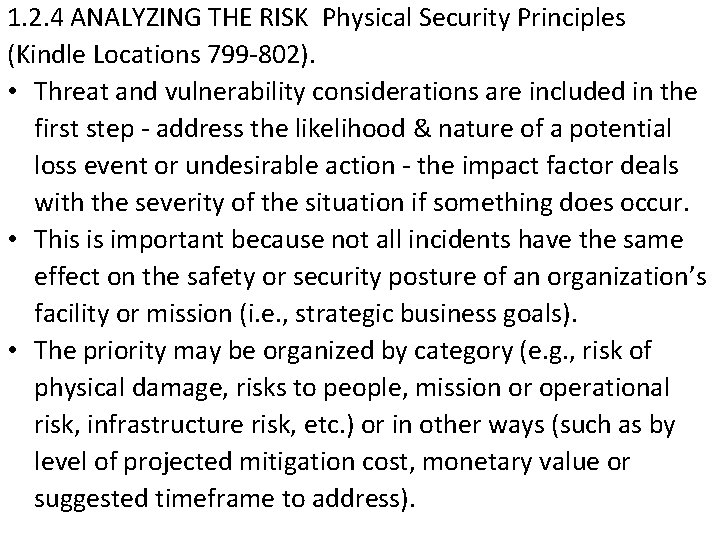
1. 2. 4 ANALYZING THE RISK Physical Security Principles (Kindle Locations 799 -802). • Threat and vulnerability considerations are included in the first step - address the likelihood & nature of a potential loss event or undesirable action - the impact factor deals with the severity of the situation if something does occur. • This is important because not all incidents have the same effect on the safety or security posture of an organization’s facility or mission (i. e. , strategic business goals). • The priority may be organized by category (e. g. , risk of physical damage, risks to people, mission or operational risk, infrastructure risk, etc. ) or in other ways (such as by level of projected mitigation cost, monetary value or suggested timeframe to address).

Chapter 4 “Risk Assessment Model” Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 980 -983). ASIS International. Kindle Edition. • An asset may be more critical or less critical. • Asset criticality depends on: o organization’s mission o the resources used to perform that mission o how those resources interface with one another to achieve goals o how the organization would cope or maintain business continuity if any of the assets were lost.

• Asset value can be considered the economic replacement cost for infrastructure and equipment. Asset Identification - determines which assets are critical to the operation of the company. • Identifying a company’s critical assets is a three-step process Step 1: Define and understand the company’s primary business functions and processes. Step 2: Identify site and building infrastructure and systems: — Critical components — Life safety systems and safe haven areas — Secure and restricted areas Step 3: Identify the company’s critical tangible and intangible assets: — People — Information systems and data — Intellectual property — One-of-a-kind assets

Chapter 4: Risk Analysis Model, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1078 -1085). • Physical environment: construction, location, composition, configuration • Social environment: demographics, crime rates, population characteristics • Political environment: type & stability of government, local law enforcement resources & management • Historical experience: type and frequency of prior loss events • Procedures and processes: how assets used, stored, secured • Criminal capabilities: criminals state of art

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: 3. Potential impacts of external organizations on the organization/facility’s security programs (EXAMPLE: competitors, supply chain, neighboring organizations) and, 4. Other external “threat” factors, and how do they impact the organization. (Example: legal issues, loss of reputation, political issues, etc. ) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Competitive intelligence or espionage = market share & income loss • Suppliers having labor issues or economic problems = quality issues, JIT, reputation, legal issues • Neighbors = impact perimeter, incident liability, proximity issues (fire, explosion, crime, etc) • Loss of reputation = potential sabotage, vandalism, violence, etc • Legal issues = loss of reputation, personnel issues, workplace violence, etc • Poor economy = higher turnover, theft, etc. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT TASK 4: Conduct an assessment to identify and quantify vulnerabilities of the organization. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: 1. Relevant data and methods for collection (e. g. , security survey, interviews, past incident reports, crime statistics, employee issues, issues experienced by other similar organizations) 2. Qualitative and quantitative methods for assessing vulnerabilities to probable threats and hazards 3. Existing equipment, physical security systems, personnel, and procedures October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS (Continued): 4. Effectiveness of security technologies and equipment currently in place 5. Interpretation of building plans, drawings and schematics 6. Applicable standards/regulations/codes and where to find them 7. Environmental factors and conditions (e. g. , facility location, architectural barriers, lighting, entrances) that impact physical security October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Relevant data and methods for collection (e. g. , security survey, interviews, past incident reports, crime statistics, employee issues, issues experienced by other similar organizations) • Do not limit the analysis to certain facilities or certain operating times. • Include the entire scope of operations & identify critical control points (the locations, processes, functions, and times at which the operation is at greatest risk). • It’s impossible to eliminate all hazards - employ reasonable countermeasures, along with documentation and verification. Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 253 -256). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Management should regularly review and analyze numerous data sources that can reveal strengths and problems or areas of weakness in security force operations. • Some of those sources are: post logs, main or control logs, supervisor reports, independent inspector reports, employee disciplinary actions, and complaints or commendations. • Automated Web-based data management systems Michael E. Knoke. Physical Security Principles (Kindle Locations 10329 -10332)Page 428. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Automated Web-based data management systems o Generate reports quickly & good insight/overview o Helps management identify trends • Trend analysis: o Basis for continuous improvement o Fine-tuning security force operations o Justification for security operations Michael E. Knoke. Physical Security Principles (Kindle Locations 10329 -10332). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • A risk assessment focuses on assets, threats, vulnerabilities, and consequences • A security survey places more emphasis on vulnerabilities. Michael E. Knoke. Physical Security Principles (Kindle Locations 1403 -1404). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Qualitative and quantitative methods for assessing vulnerabilities to probable threats and hazards • Intentional threats • Evaluation based on identification and study of potential adversaries • Potential adversaries (employees, terrorist organizations, organized crime groups • Aggressive business competitors • Activist groups (such as environmental groups) Michael E. Knoke. Physical Security Principles (Kindle Locations 1264 -1267). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

Physical Security Assessment • Adversaries judged by capability & intentions • Sources of information (QUALITATIVE OR QUANTITATIVE): • • • Past history Adversary sequence diagrams Organization rhetoric Public pronouncements Intelligence and other open sources Communications (newsletters, Web sites, blog posts, etc. ) Law enforcement reports Crime analysis Professional organizations Automated databases Threat assessments Michael E. Knoke. Physical Security Principles (Kindle Locations 1269 -1273). ASIS International. Kindle Edition.

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Natural threats • Evaluated using historical trends and statistics • Long-term data collected on weather and other natural hazards, terrains, and environments • Some data collected for particular industry sectors or facility type • Assessors warned the unexpected can & usually does occur - contingency planning & some degree of all-hazard preparedness recommended Michael E. Knoke. Physical Security Principles (Kindle Locations 1274 -1278). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Inadvertent threats • Most neglected threats • Accidents, errors, and omissions • Human error – “people make mistakes, most likely to hurt you. ” • Also called peripheral threats • Utility interruptions, required evacuations, closure of access routes, unwanted attention or traffic, full or partial operations shutdowns, productivity disruptions, & environmental affects (e. g. , smoke, debris, water or chemical runoff, etc. ) Michael E. Knoke. Physical Security Principles (Kindle Locations 1282 -1285). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Inadvertent threats (Continued) • Most difficult to predict and prepare for • Nature of the workforce, operations, or other environmental factors may suggest a level of inadvertent threat • Usually little or no historical data to use • The best defenses are preparation, education and awareness & accepting the threat exists Michael E. Knoke. Physical Security Principles (Kindle Locations 1285 -1288). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Vulnerabilities evaluated by measuring in terms of: • Observability - ability of an adversary to see and identify a vulnerability • Example, a hole in a chain link perimeter fence will likely be highly observable by a potential adversary, whereas an inoperable video camera would not. • Exploitability - ability of the adversary to take advantage of the vulnerability once aware of it. Michael E. Knoke. Physical Security Principles (Kindle Locations 1296 -1299). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Assessing natural threats: • Observability requires mechanisms for early warning and notification of the impending threat • Exploitability is the natural threat’s ability to damage the facility, mission, or organization. Inadvertent threats (most difficult to measure): • Observability: security personnel aware of vulnerabilities? • Exploitability: opportunity for a loss event based on the nature of the mission, operation, or facility Michael E. Knoke. Physical Security Principles (Kindle Locations 1300 -1302). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: Collecting information: • Personnel surveys (employee, contractor, visitor, ) • External resources (police, neighbors, government) • Statistics (government, similar businesses, associations) • Evaluating trends October 2017 Dennis Shepp, CPP

CHAPTER 4 – RISK ANALYSIS MODEL Patterson, “Physical Protection Systems”, Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle: 1100 – 1107) • Factors: o Lack of redundancy or backups for critical functions or systems o Single points of failure o Collocation (Comparison) of critical systems, organizations, or components o Inadequate response capability to recover from an attack o Ease of aggressor access to a facility o Inadequate security measures in place o Presence of hazardous materials o Potential for collateral damage from other companies in the area • Defense-in-depth and the D’s: Deter – Detect – Delay – Trigger - Deny

3. 2. 3 Vulnerabilities, Michael E. Knoke. Physical Security Principles (Kindle Locations 1296 -1299). ASIS International. Kindle Edition. • Vulnerabilities evaluated by measuring in terms of: • Observability - ability of an adversary to see and identify a vulnerability • Example, a hole in a chain link perimeter fence will likely be highly observable by a potential adversary, whereas an inoperable video camera would not. • Exploitability - ability of the adversary to take advantage of the vulnerability once aware of it.

Chapter 5: Security Design Elements Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1289 -1291). • A successful security design recognizes technological developments and integrates three primary elements: architectural aspects, security systems, and operational factors. • Technology does not replace manpower but acts as a force multiplier. • The architectural aspect is one of the most significant factors in security design. • One of the deliverables of the design phase is the PPS specification.

Design Criteria - help identify the characteristics that the security system will have in terms of performance and operational factors. • The criteria also define the constraints, such as codes, standards and costs. 14. 3. 6 DRAWINGS Knoke, Physical Security Principles (Kindle Locations 10895 -10898) • Along with specifications, drawings are the cornerstone of any construction project. • To avoid ambiguity and to manage any discrepancies among the drawings, specifications have precedence over drawings. • Security system drawings usually consist of plans, elevations, details, risers, and hardware schedules. • Each drawing is either a site plan or floor plan showing the security system devices by type and location.

• Plans - each security system plan shows a top-down, map-like view of an area where security devices and systems are located. • The area may be a complete site, a building floor, or part of a floor. • Elevations - views of vertical surfaces and are included to show mounting heights and locations of wall-mounted devices, such as cameras, card readers, and motion sensors. • Riser diagrams are representations of complete subsystems, such as video or access control. They schematically demonstrate all the associated devices and components and their interconnecting cables. • Contractors tend to use the riser diagrams for device counts when developing their bid price for the project. For these reasons it is important that riser diagrams be accurate and complete.

APPENDIX A: Applicable Codes and Standards, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 2705). • ANSI – American National Standards Institute • ASTM – American Society for Testing Materials • EIA – Electronics Industries Alliance • IEEE – Institute for Electrical and Electronics Engineers • NEMA – National Electrical Manufacturers • NFPA – National Fire Protection Ass’n • UL – Underwriters Laboratories

Explain conducting an assessment to identify and quantify vulnerabilities of the organization including environmental factors and conditions (e. g. , facility location, architectural barriers, lighting, entrances) that impact physical security. 3. 2. 3 VULNERABILITIES Knoke. Physical Security Principles (Kindle Location 1292) • Vulnerabilities can be evaluated in terms of observability and exploitability: o Observability is the ability of an adversary to see and identify a vulnerability. For example, a hole in a chain link perimeter fence will likely be highly observable by a potential adversary, whereas an inoperable video camera would not. o Exploitability is the ability of the adversary to take advantage of the vulnerability once aware of it. • Using this observability/exploitability approach, security professionals can assess vulnerabilities and develop plans to mitigate them in both the long-term (strategic) and immediate (tactical) time frames.

Task 5. 1 & 5. 2. Explain conducting a risk analysis so that appropriate countermeasures can be developed identifying risk analysis strategies, methods and identify the risk management principles. 1. 3. 2 THE FIVE AVENUES TO ADDRESS RISK Physical Security Knoke • Risk Avoidance – removing opportunities of risk • Risk Spreading – Don’t keep valuable assets together. • Risk Transfer – Purchase insurance • Risk Reduction – security measures to reduce opportunities – decrease vulnerabilities • Risk Acceptance – accepting residual risk. RISK = THREAT X VULNERABILITY X IMPACT

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT TASK 5: Perform a risk analysis so that appropriate countermeasures can be developed October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: 1. Risk analysis strategies and methods 2. Risk management principles 3. Methods for analysis and interpretation of collected data 4. Threat and vulnerability identification 5. Loss event profile analyses 6. Appropriate countermeasures related to specific risks October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS (Continued): 7. Cost benefit analysis (e. g. return on investment (ROI) analysis, total cost of ownership) 8. Legal and regulatory considerations related to various countermeasures/security applications (e. g. , video surveillance, privacy issues, personally identifiable information) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: Methods for analysis and interpretation of collected data. (Risk analysis methods already reviewed) • Determine methods of evaluation by committee (multi-disciplinary team approach) • Justifying numbers challenging • Calculating risk results: Risk = (Threat × Vulnerability × Impact) Michael E. Knoke. Physical Security Principles (Kindle Location 1320). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Multiplies risk factors (if any factor is zero, the resulting risk is zero) • Evaluation factors (threat, vulnerability, and impact) are rated on a 0 to 100 scale. • Risk analysis results should be presented in a manner that helps them understand the data and make decisions. • List risks by priority Michael E. Knoke. Physical Security Principles (Kindle Locations 1321 -1326). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: • Collecting & evaluating data should consider two foundational principles: • The 4 -Ds (deter, detect, delay, and deny) • Security-in-depth / layered security (defense-in-depth). • Critical detection point = the point where the delay time remaining exceeds the response force time. Michael E. Knoke. Physical Security Principles (Kindle Locations 2142 -2146). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: Loss event profile analysis. • Vulnerability: “a weakness or organizational practice that may facilitate or allow a threat to be implemented or increase the magnitude of a loss event. ” • Threat & vulnerability factors to determine likelihood of loss event. • Impact factor deals with severity (criticality) of the loss event to the organization. Michael E. Knoke. Physical Security Principles (Kindle Locations 791 -792). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Loss event profile analysis. • A loss event profile is a list of the kinds of threats affecting the assets to be safeguarded. • Threats (loss risk event) categories: o Crimes o Noncriminal events (man-made incidents or natural disasters) • Consequential events caused by another organization (another organization’s poor/negative reputation adversely affects the enterprise. ) Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1038 -1044). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: Cost benefit analysis (e. g. return on investment (ROI) analysis, total cost of ownership). “When at the planning phase to analyze collected data & decide which physical security measures should be implemented. It will eventually be necessary, for each alternative, to state its costs, benefits, and impact on business operations. ” Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1252 -1254). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP
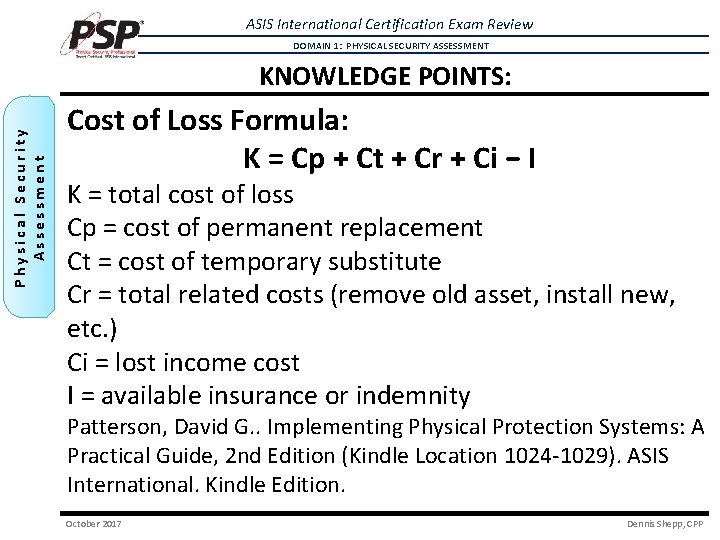
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT Physical Security Assessment KNOWLEDGE POINTS: Cost of Loss Formula: K = Cp + Ct + Cr + Ci − I K = total cost of loss Cp = cost of permanent replacement Ct = cost of temporary substitute Cr = total related costs (remove old asset, install new, etc. ) Ci = lost income cost I = available insurance or indemnity Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1024 -1029). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP
ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Cost Benefit: • For countermeasures/safeguards “…each alternative, to state its costs, benefits, and impact on business operations. ” PPS Project “Rules of Thumb” (PPS costs): • Design & engineering: 10 -15% / total cost • Hardware/software: 15 -20% / total cost • Installation: 40 -50% / total cost • Training: 3 -5% / total cost • Contingency: 10% / total cost Patterson, David G. Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 864 -875). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Life cycle: • The actual cost of a security system is its life-cycle cost. • Life-cycle cost estimates include: o Engineering and design costs (planning and design of the security system) o Hardware. (original equipment, spare parts) o Software (OS, application software) Michael E. Knoke. Physical Security Principles (Kindle Locations 11045 -11052). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Life cycle (continued): o Installation costs o Operating costs (personnel, power, consumables) o Maintenance costs (5% of original cost for parts) o Other cost (taxes, profit (10 percent), performance bonding (3 -5 percent), and contingency (5 -10 percent) o Adjustments Michael E. Knoke. Physical Security Principles (Kindle Locations 11053 -11059). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Life cycle: o Use system to “point of failure” or planned obsolescence. o TCO (total cost ownership) § When a PPS costs more to repair and keep running than buying a new one - threshold crossed for buying a new PPS. Patterson, David G. Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 3276 -3277). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Guidelines when to replace a system: • System has excessive failures, no longer achieves PPS objectives • Cost of maintenance has increased, parts unavailable/too expensive • Company wants to standardize on a particular security system Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 3279 -3286). October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Guidelines when to replace a system (continued): • No support from the integrator or equipment suppliers • Regulatory requirements call for a new system • Hardware/software is obsolete • Beneficial new technologies or features have become available • The life cycle cost analysis recommends Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 3279 -3288). October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Performance metrics provide: o the status of a program o identify performance trends o demonstrate the ROI or value-added • Metric: a measure based on a reference that involves at least two points o quantity over time. • The primary goal of metrics is to facilitate insight into performance Michael E. Knoke. Physical Security Principles (Kindle Locations 17051716). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: EXAMPLES of Metrics: • Security cost per square foot (Total system cost + Total contractor labor cost + Total FTE + Indirect cost) Total Square Footage (m 2) • Security cost per employee Total security dept. cost (Contract cost + FTE cost + Indirect cost) Total number of employees Michael E. Knoke. Physical Security Principles (Kindle Locations 20382041). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Cost Benefit: • Cost reductions and sharing resources using CPTED • Reducing the number of security officers or reassigning them • Reducing (sharing) the scope of a video surveillance system • Providing for natural access controls to offset the need for some structural barriers Michael E. Knoke. Physical Security Principles (Kindle Locations 55795581). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Legal and regulatory considerations related to various countermeasures/security applications (e. g. , video surveillance, privacy issues, personally identifiable information) • CODES AND REGULATIONS • Projects subject to a variety of federal, state, and local requirements • Code regulations (legally required) • Guidelines or standards (recommendations) • Permitting/contractual requirements Michael E. Knoke. Physical Security Principles (Kindle Locations 2604 -2606). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT • • • KNOWLEDGE POINTS: Recording systems – “check with organization’s legal counsel before installing a system. ” Attention to privacy a major consideration when using video surveillance systems. Use of hidden/covert cameras is legal under many circumstances, but consultation with legal counsel is recommended - enough justification or legal authority exists. “Dummy cameras” have a liability. Accepted legal practice to post video warning signs. Michael E. Knoke. Physical Security Principles (Kindle Location 8395 -8399). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT • • KNOWLEDGE POINTS: Recorded video information must meet certain standards to be admissible as legal evidence. Depending on the jurisdiction, quality of image, time/ date stamp, and percentage of scene occupied by the subject, an eyewitness may be required. A unique scene identifier may also be required. Ask legal counsel whether capturing audio with video is legal and appropriate Michael E. Knoke. Physical Security Principles (Kindle Location 8403 -8410). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Security guard contracts - A legal review will determine if some contractual agreements may shift a portion of the liability for certain actions or incidents away from the organization. • Recommended organizations have a well-defined use -of-force policy • Provide instructions on how disturbed individuals should be handled legal liability exists) • Provide a measure of legal protection Michael E. Knoke. Physical Security Principles (Kindle Locations 9438 -9439). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review Physical Security Assessment DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Logs and reports prepared by security officers have often been used in legal proceedings as an authoritative source to establish: • precise time an event occurred • presence of particular people at the facility • receipt of a telephone call • SO’s as enforcement/compliance agents: • Must be executed within the legal and cultural framework of a particular protected environment. Michael E. Knoke. Physical Security Principles (Kindle Locations 9488 -9492, 9533). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT • • KNOWLEDGE POINTS: Professional protection officers must be trained to understand the vast array of legal and quasi-legal (disciplinary) issues they might face in the work environment. Security officers must know and understand torts, negligence, and contracts. Need a working knowledge of criminal law procedures, . Understand comply with audit processes imposed by governmental, insurance, and professional organizations. Michael E. Knoke. Physical Security Principles (Kindle Locations 95429549). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Labor/employment laws regarding privacy rights disciplinary processes, and union contracts must also be understood. • Benefits of training = legal protection o Reduces complaints o Law suits o Once all legal requirements for training are known, the manager should identify relevant standards, guidelines, or industry best practices that can help set training parameters. Michael E. Knoke. Physical Security Principles (Kindle Locations 95499550, 9802, 9823 -9824). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Operating procedures: • Incident response policies should be reviewed periodically by legal counsel. • The legal review should ensure that procedures o are legally defensible and enforceable o comply with overall company policies and procedures (continued) o reflect known industry best practices demonstrating the exercise of due care Michael E. Knoke. Physical Security Principles (Kindle Locations 11908 -11914). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • The legal review should ensure that procedures (continued): o protect staff from lawsuits. o Define when to prosecute and what should be done to prosecute a person caught violating facility access rules o ensure the admissibility of evidence o Define when to report an incident to local, state, or national law enforcement agencies o conform to national, state, and local laws and regulations Michael E. Knoke. Physical Security Principles (Kindle Locations 11908 -11914). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Legal counsel can help the security manager develop policies & procedures to avoid lawsuits concerning: o Failure to adhere to duty guidelines o Breach of duty o Proximate cause (This term means an officer was the immediate cause of injury to a victim) o Foreseeability Michael E. Knoke. Physical Security Principles (Kindle Locations 11908 -11914). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: Codes & Regulations • As regulation and government oversight have expanded, using an outside resource to conduct a risk assessment may strengthen a company’s position during an audit. • Some codes and many guidelines address security design (such as life safety codes) Michael E. Knoke. Physical Security Principles (Kindle Locations 1363 -1364, 2608). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Some lighting is regulated by code (Nuclear Regulatory Commission (NRC) or OSHA). • NRC regulations specify 0. 2 fc of illumination at the perimeter and in the clear area between the two fences. • Increasingly governments are regulating security officers and the organizations that employ them. Michael E. Knoke. Physical Security Principles (Kindle Locations 4528 -4529). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT KNOWLEDGE POINTS: • Post orders are the most important written instructions for the security force • express the policies of the protected enterprise • summarize required officer duties • avoid the problems of word-of-mouth instructions • provide a basis for site-specific training • Clear and understandable post orders are important in serious incidents that may call into question the integrity, competence, or ability of an officer. Michael E. Knoke. Physical Security Principles (Kindle Locations 1015110157). ASIS International. Kindle Edition. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 1: PHYSICAL SECURITY ASSESSMENT PRACTICE EXAM QUESTIONS October 2017 Dennis Shepp, CPP

When conducting a thorough vulnerability analysis, which of the following is a step in identifying preventive measures? a. Determine and evaluate significant threats, hazards and exposure to determine the likelihood of occurrence. b. Identify the assets of the organization and determine the asset value as determined by management. c. Identify the threats to the organization and determine the impact of a loss to the organization. d. Interview employees to understand their experiences with loss events.

When conducting a thorough vulnerability analysis, which of the following is a step in identifying preventive measures? a. Determine and evaluate significant threats, hazards and exposure to determine the likelihood of occurrence. b. Identify the assets of the organization and determine the asset value as determined by management. c. Identify the threats to the organization and determine the impact of a loss to the organization. d. Interview employees to understand their experiences with loss events. Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 256). ASIS International. Kindle Edition.

The process of assessing security-related risks from internal and external threats to an entity, its assets and personnel, is called a ________. a. Vulnerability Assessment b. Risk Assessment c. Security Survey d. Loss Event Profile

The process of assessing security-related risks from internal and external threats to an entity, its assets and personnel, is called a ________. a. Vulnerability Assessment b. Risk Assessment c. Security Survey d. Loss Event Profile (Facilities Physical Security Guideline, ASIS International, Page 3)

This is considered the most common reliable tool for determining adequacy and foreseeability and focuses on: o The risks to the physical assets and property o The protection measures (against any risk) that comprise the realm of physical security o Measuring three basic factors: quality, reliability and cost This process is called a ________. a. Risk Analysis b. Vulnerability Analysis c. Security Survey d. Loss Event Survey

This is considered the most common reliable tool for determining adequacy and foreseeability and focuses on: o The risks to the physical assets and property o The protection measures (against any risk) that comprise the realm of physical security o Measuring three basic factors: quality, reliability and cost This process is called a ________. a. Risk Analysis b. Vulnerability Analysis c. Security Survey d. Loss Event Survey (Michael E. Knoke. Physical Security Principles (Kindle Locations 1374 -1375). ASIS International. Kindle Edition. )

These are described as the most important written instructions for the security force which express the policies of the protected enterprise, summarize required officer duties and provide a basis for site-specific training. They are called: a. Corporate Policy & Procedures b. Security Department Policy & Procedures c. Security Post Orders d. Security Training Manual

These are described as the most important written instructions for the security force which express the policies of the protected enterprise, summarize required officer duties and provide a basis for site-specific training. They are called: a. Corporate Policy & Procedures b. Security Department Policy & Procedures c. Security Post Orders d. Security Training Manual Michael E. Knoke. Physical Security Principles (Kindle Locations 1015110157). ASIS International. Kindle Edition.
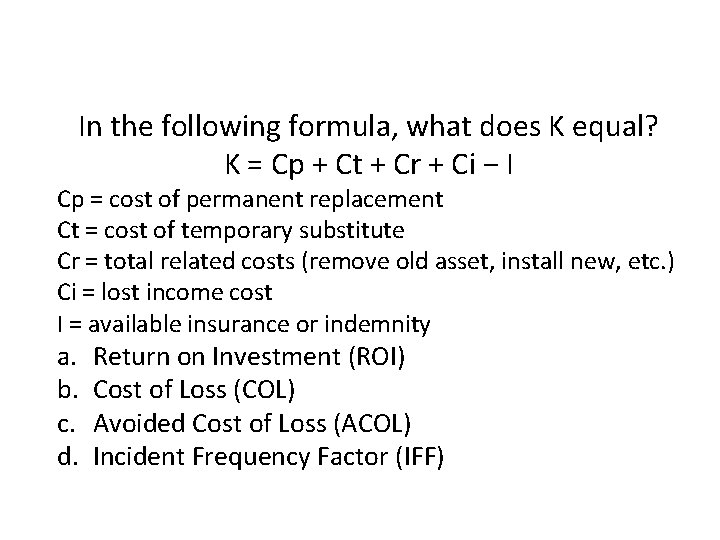
In the following formula, what does K equal? K = Cp + Ct + Cr + Ci − I Cp = cost of permanent replacement Ct = cost of temporary substitute Cr = total related costs (remove old asset, install new, etc. ) Ci = lost income cost I = available insurance or indemnity a. b. c. d. Return on Investment (ROI) Cost of Loss (COL) Avoided Cost of Loss (ACOL) Incident Frequency Factor (IFF)

In the following formula, what does K equal? K = Cp + Ct + Cr + Ci − I Cp = cost of permanent replacement Ct = cost of temporary substitute Cr = total related costs (remove old asset, install new, etc. ) Ci = lost income cost I = available insurance or indemnity a. b. c. d. Return on Investment (ROI) Cost of Loss (COL) Avoided Cost of Loss (ACOL) Incident Frequency Factor (IFF) Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1024 -1029). ASIS International. Kindle Edition.

Which of the following processes places more focus on evaluating vulnerabilities? a. Risk Assessment b. Security Survey c. Loss Event Likelihood Profile d. Loss Event Impact Profile

Which of the following processes places more focus on evaluating vulnerabilities? a. Risk Assessment b. Security Survey c. Loss Event Likelihood Profile d. Loss Event Impact Profile Michael E. Knoke. Physical Security Principles (Kindle Locations 1296 -1299). ASIS International. Kindle Edition.

Which of the following is suggested as part of evaluating an Inadvertent Threat? a. Long-term data collected on weather and other natural hazards, terrains, and environments. b. Evaluate information provided by neighboring businesses for natural events which have caused losses. c. Unexpected natural events can occur so some degree of all-hazard preparedness is evaluated. d. Utility interruptions, closure of access routes, unwanted attention or traffic, full or partial operation shutdowns and productivity disruptions.

Which of the following is suggested as part of evaluating Inadvertent Threats? a. Long-term data collected on weather and other natural hazards, terrains, and environments. b. Evaluate information provided by neighboring businesses for natural events which have caused losses. c. Unexpected natural events can occur so some degree of all-hazard preparedness is evaluated. d. Utility interruptions, closure of access routes, unwanted attention or traffic, full or partial operation shutdowns and productivity disruptions. Michael E. Knoke. Physical Security Principles (Kindle Locations 1274 -1278). ASIS International. Kindle Edition.

A measure which is based on a reference that involves at least two points, quantity over time, is called a ______. a. Qualitative process b. Measurement indicator. c. Quantity over time process. d. Metric indicator.

A measure which is based on a reference that involves at least two points, quantity over time, is called a ______. a. Qualitative process b. Measurement indicator. c. Quantity over time process. d. Metric indicator. Michael E. Knoke. Physical Security Principles (Kindle Locations 1705 -1716). ASIS International. Kindle Edition.

A list of the kinds of threats or hazards affecting the assets to be protected in an organization is called a _______ Profile. a. Asset Identification b. Loss Event c. Loss Impact d. Security Survey

A list of the kinds of threats or hazards affecting the assets to be protected in an organization is called a _______ Profile. a. Asset Identification b. Loss Event c. Loss Impact d. Security Survey Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1038 -1044). ASIS International. Kindle Edition.

Collecting site historical loss data, neighborhood makeup/historical loss data, overall geographical location, political and social conditions is involved in the process of determining a loss event’s ____. a. Impact b. Criticality c. Likelihood d. Observabiity

Collecting site historical loss data, neighborhood makeup/historical loss data, overall geographical location, political and social conditions is involved in the process of determining a loss event’s ____. a. Impact b. Criticality c. Likelihood d. Observabiity Michael E. Knoke. Physical Security Principles (Kindle Locations 1173 -1174). ASIS International. Kindle Edition.

When evaluating PPS solutions, including engineering, design, hardware and software costs is part of _______. a. Threat assessments b. Life cycle cost estimates c. Cost of loss estimations d. Loss event likelihood estimates

When evaluating PPS solutions, including engineering design, hardware and software costs is part of _______. a. Threat assessments b. Life cycle cost estimates c. Cost of loss estimations d. Loss event likelihood estimates Michael E. Knoke. Physical Security Principles (Kindle Locations 11045 -11052). ASIS International. Kindle Edition.

“A weakness or organizational practice that may facilitate or allow a threat to be implemented or increase the magnitude of a loss event”, is a definition of which of the following? a. Loss event b. Vulnerability c. Risk d. Criticality

“A weakness or organizational practice that may facilitate or allow a threat to be implemented or increase the magnitude of a loss event”, is a definition of which of the following? a. Loss event b. Vulnerability c. Risk d. Criticality Michael E. Knoke. Physical Security Principles (Kindle Locations 791 -792). ASIS International. Kindle Edition.
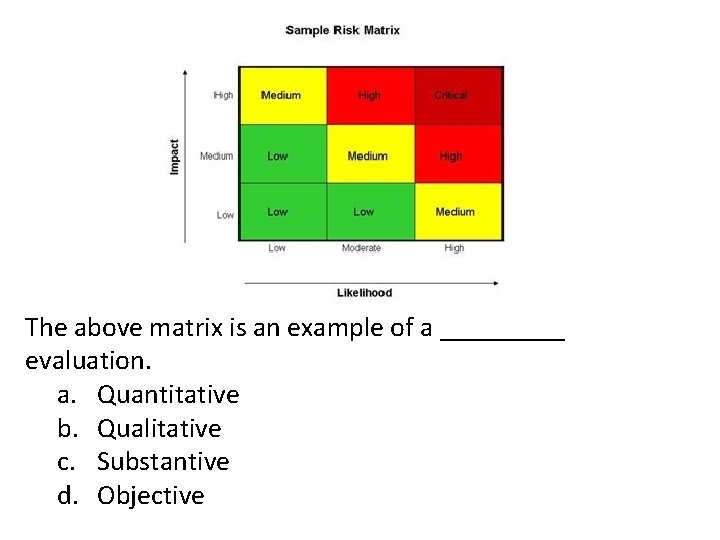
The above matrix is an example of a _____ evaluation. a. Quantitative b. Qualitative c. Substantive d. Objective
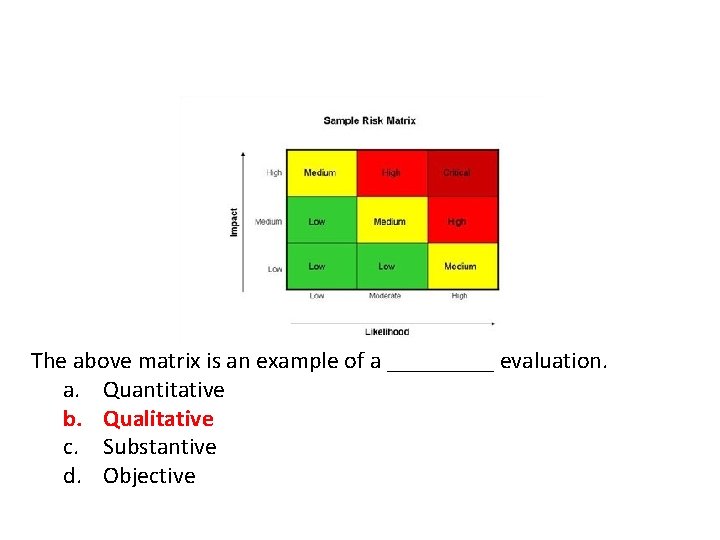
The above matrix is an example of a _____ evaluation. a. Quantitative b. Qualitative c. Substantive d. Objective

Which of the following is a TRUE statement regarding threats and vulnerabilities? a. Vulnerability is a characteristic of the organization and controllable to some degree. b. Threats are a characteristic of the organization and controllable to some degree. c. Vulnerabilities are usually outside the control of the organization. d. Threats are all predictable using a properly applied threat assessment process.

Which of the following is a TRUE statement regarding threats and vulnerabilities? a. Vulnerability is a characteristic of the organization and controllable to some degree. b. Threats are a characteristic of the organization and controllable to some degree. c. Vulnerabilities are usually outside the control of the organization. d. Threats are all predictable using a properly applied threat assessment process. Michael E. Knoke. Physical Security Principles (Kindle Locations 7941 -795). ASIS International. Kindle Edition. )

Which of the following is considered part of developing an effective PPS using security-in-depth principles of the 4 -D’s? a. Deter, detect, delay, and deny b. Deter, detect, delay, and dispatch c. Detect, delay, dispatch and detain d. Detect, delay, deny and dispatch

Which of the following is considered part of developing an effective PPS using security-in-depth principles of the 4 -D’s? a. Deter, detect, delay, and deny b. Deter, detect, delay, and dispatch c. Detect, delay, dispatch and detain d. Detect, delay, deny and dispatch Michael E. Knoke. Physical Security Principles (Kindle Locations 2142 -2146). ASIS International. Kindle Edition.

Which of the following is considered a “Direct Cost” when considering the costs of loss? a. Long-term negative consumer perception. b. Higher wages needed to attract future employees. c. Deductible expenses on insurance claims. d. Employee turnover due to poor employee morale.

Which of the following is considered a “Direct Cost” when considering the costs of loss? a. Long-term negative consumer perception. b. Higher wages needed to attract future employees. c. Deductible expenses on insurance claims. d. Employee turnover due to poor employee morale. ASIS General Security Risk Assessment Guideline page 14

Which of the following is considered an “Indirect Cost” when considering the costs of loss? a. Additional public relations costs to overcome poor image. b. Punitive damage awards not covered by insurance. c. Management time dealing with a disaster. d. Lost business from immediate post-risk incident.

Which of the following is considered an “Indirect Cost” when considering the costs of loss? a. Additional public relations costs to overcome poor image. b. Punitive damage awards not covered by insurance. c. Management time dealing with a disaster. d. Lost business from immediate post-risk incident. ASIS General Security Risk Assessment Guideline page 14

A risk mitigation technique which provides for purchasing insurance to mitigate the security risk, is BEST described as which of the following? a. Risk Acceptance b. Risk Assumption c. Risk Limitation d. Risk Transfer

A risk mitigation technique which provides for purchasing insurance to mitigate the security risk, is BEST described as which of the following? a. Risk Acceptance b. Risk Assumption c. Risk Limitation d. Risk Transfer Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1116).

When applying risk mitigation techniques, it is often not practical to address all identified risks, so which of the following statements BEST explains how to mitigate the risk? a. Priority should be given to the threat and vulnerability that have the most likelihood to occur. b. Priority should be given to the asset–threat and vulnerability that have the potential to cause significant impact. c. Priority should be given to the asset and vulnerability risk with highest likelihood. d. Priority should be given to the asset and threat risk with highest likelihood.

When applying risk mitigation techniques, it is often not practical to address all identified risks, so which of the following statements BEST explains how to mitigate the risk? a. Priority should be given to the threat and vulnerability that have the most likelihood to occur. b. Priority should be given to the asset–threat and vulnerability that have the potential to cause significant impact. c. Priority should be given to the asset and vulnerability risk with highest likelihood. d. Priority should be given to the asset and threat risk with highest likelihood. Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1127 -1128).

Based on simulation or actual tests, one can compute the time an access control system will take to process the peak number of access requests. For an efficient access control system, response time at any card reader should be no longer than ______ at peak load. a. 2 seconds b. 5 seconds c. 30 seconds d. 60 seconds

Based on simulation or actual tests, one can compute the time an access control system will take to process the peak number of access requests. For an efficient access control system, response time at any card reader should be no longer than ______ at peak load. a. 2 seconds b. 5 seconds c. 30 seconds d. 60 seconds Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1343 -1345)

“These diagrams show complete security subsystems, including all the devices and how they are connected in a building or campus”, they are BEST described as: a. Elevation drawings b. Plan drawings c. Riser drawings d. Details drawings

“These diagrams show complete security subsystems, including all the devices and how they are connected in a building or campus”, they are BEST described as: a. Elevation drawings b. Plan drawings c. Riser drawings d. Details drawings Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition

This type of drawing shows an area in map-like form to specify where at a particular site the security devices are located. What type of drawing is this? a. Plan Drawing b. Elevation Drawing c. Details Drawing d. Riser Drawing

This type of drawing shows an area in map-like form to specify where at a particular site the security devices are located. What type of drawing is this? a. Plan Drawing b. Elevation Drawing c. Details Drawing d. Riser Drawing Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1409).

A risk mitigation technique which provides for the application of physical security, policy and procedures, deployed security officers all integrated to mitigate the security risk, is BEST described as which of the following? a. Risk Acceptance b. Risk Assumption c. Risk Limitation d. Risk Transfer

A risk mitigation technique which provides for the application of physical security, policy and procedures, deployed security officers all integrated to mitigate the security risk, is BEST described as which of the following? a. Risk Acceptance b. Risk Assumption c. Risk Limitation d. Risk Transfer Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1121). ASIS International. Kindle Edition.

Which of the following is considered to have the most significant implementation cost as a risk mitigation measure? a. Risk Transfer b. Risk Avoidance c. Risk Assumption d. Site Hardening

Which of the following is considered to have the most significant implementation cost as a risk mitigation measure? a. Risk Transfer b. Risk Avoidance c. Risk Assumption d. Site Hardening Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 1121). ASIS International. Kindle Edition.

Which of the following is considered the MOST IMPORTANT phase in the PPS Life Cycle Phase? a. Planning Phase b. Design and Estimation Phase c. Procurement Phase d. Testing and Warranty Phase

Which of the following is considered the MOST IMPORTANT phase in the PPS Life Cycle Phase? a. Planning Phase b. Design and Estimation Phase c. Procurement Phase d. Testing and Warranty Phase Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 505). ASIS International. Kindle Edition.

In this part of the Life Cycle Phase, security staff and other members of the project team develop all the necessary documentation to support the procurement of the PPS. This is BEST described in which phase? a. The Planning Phase b. The Design and Estimation Phase c. The Procurement Phase d. The Installation, Operation and Training Phase

In this part of the Life Cycle Phase, security staff and other members of the project team develop all the necessary documentation to support the procurement of the PPS. This is BEST described in which phase? a. The Planning Phase b. The Design and Estimation Phase c. The Procurement Phase d. The Installation, Operation and Training Phase Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 517 -519).

When tests are performed by the implementation team which involve equipment, personnel, procedures, or any combination that simulate realistic conditions and provide conclusive evidence about the effectiveness of the security system, this is BEST described as which of the following? a. Procurement Phase b. Installation, Operation and Training Phase c. Commissioning and Warranty Phase d. Maintenance, Evaluation and Replacement Phase

When tests are performed by the implementation team which involve equipment, personnel, procedures, or any combination that simulate realistic conditions and provide conclusive evidence about the effectiveness of the security system, this is BEST described as which of the following? a. Procurement Phase b. Installation, Operation and Training Phase c. Commissioning and Warranty Phase d. Maintenance, Evaluation and Replacement Phase Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 542 -543)

PHYSICAL SECURITY PROFESSIONAL (PSP) Certification Examination Review 1 DOMAIN PHYSICAL SECURITY ASSESSMENT (34%) October 2017 Dennis Shepp, CPP
- Slides: 188