Physical Security Introduction to Cyber Security The Security

Physical Security Introduction to Cyber Security

The Security Problem • Physical access negates all other security measures

Firewalls and Intrusion Detection Systems • No matter how impenetrable they are, if an attacker can find a way to walk up to and touch a server, they can break it • Any machine on a company network operates inside the firewall • All it takes is one machine to compromise an entire network

Smartphones and wireless attacks • Attackers can plug in a smartphone into any open Ethernet jack • Using a laptop, they can use the smartphone connection to attack the network from outside the building

Other Methods of Physical Attacks • Bootdisk-any media used to boot a computer into an operating system that is not the native OS on its hard drive (i. e. flash drives) • Live. CD-bootable version of an entire operating system and use a list of attacks on the computer to infiltrate the company network

Physical Security Safeguards • Walls and Guards • Lighting • Signs • Fences • Barricades • Guards • Alarms

Physical Access Controls and Monitoring • Layered access-creating multiple perimeters • Contactless access cards • Locks • Key locks can be easily picked • Controls for making copies of keys • Combinations of keys and locks to gain access

Physical Access and Monitoring • Doors • Should have characteristics to make them less obvious • Self-closing • Fail-soft: lock is unlocked in a power interruption • Fail-secure: lock is locked in a power interruption • Mantraps • Two doors closely spaced, prevents “tailgating” • Turnstiles • Only one person can pass at a time (can be used for entrance and exit)

Physical Access and Monitoring • Cameras • Closed-Circuit Television (CCTV)-should be placed on its own separate network if IP-based • Camera placement • Types of cameras being used • Infrared Detection • Technical means of looking for things that may not have otherwise been noticed • Motion Detection • Used so that large amounts of “empty” activity is not recorded

Physical Access and Monitoring • Safes • Secure cabinets/enclosures • Protected Distribution/Protected Cabling • Airgap: network not physically connected to other networks • Faraday cage: providing shielding against electromagnetic interference • Cable locks • Screen filters • Key management • Logs

Physical Security Policies and Procedures • Relate to two distinct areas • Those that affect the computers themselves • Those that affect users

Physical Security Policies and Procedures • Good safeguard: Remove the removable media devices from the boot sequence of the computer’s BIOS (basic input/output system) • Specifics depend on the individual machine • Can set a BIOS password • Impacted drives: • Flash Drives • External Hard Drives • CD/DVD Players • MP 3 Players

Physical Security Policies and Procedures • Unified Extensible Firmware Interface (UEFI) • Has a functionality known as a secure boot which allows only digitally signed drivers and OS loaders to be used during the boot process, preventing bootkit attacks • USB Devices • Automatically recognized a device being plugged into the system and usually work with the user needing to add drivers or configure software • Large capacity drives have ability to carry own OS • Disabling AUTOPLAY function helps prevent USB attacks from happening
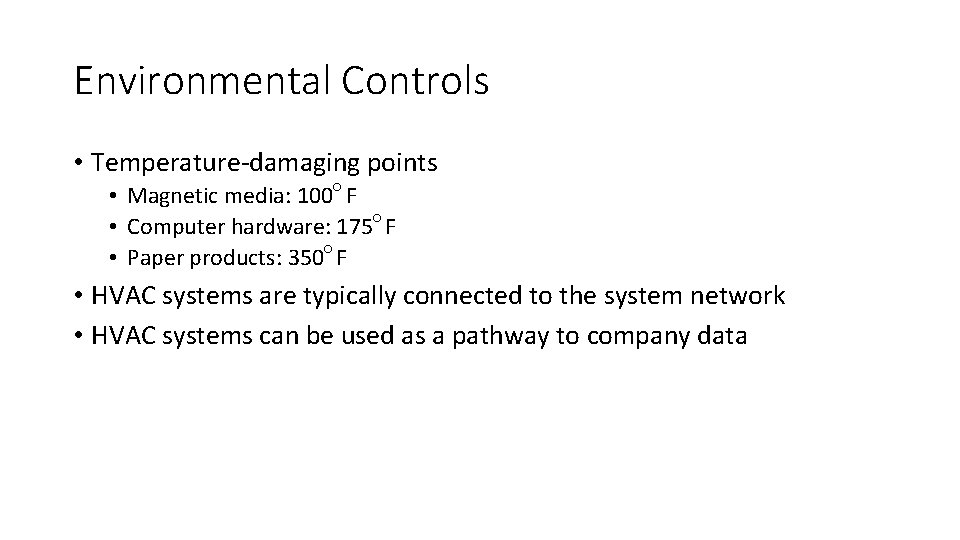
Environmental Controls • Temperature-damaging points • Magnetic media: 100○ F • Computer hardware: 175○ F • Paper products: 350○ F • HVAC systems are typically connected to the system network • HVAC systems can be used as a pathway to company data

Assignment • Page 232 in book (Essay Questions) • Choose one of the four questions to write #1 Pros and cons of IP CCTV (Closed Caption Television) #2 Memo justifying layered access for devices in an organization #3 Memo justifying more user education about physical security MEMO: An internal message sent to employees, managers, etc. #4 Sample policy regarding use of USB devices in an organization
- Slides: 15