Physical Layer Security DivideandConquer Based Cooperative Jamming Addressing

Physical Layer Security Divide-and-Conquer Based Cooperative Jamming Addressing Multiple Eavesdroppers in Close Proximity Zhihong Liu, Jiajia Liu, Nei Kato, Jianfeng Ma, and Qiping Huang School of Cyber Engineering Xidian University, Xi’an, China
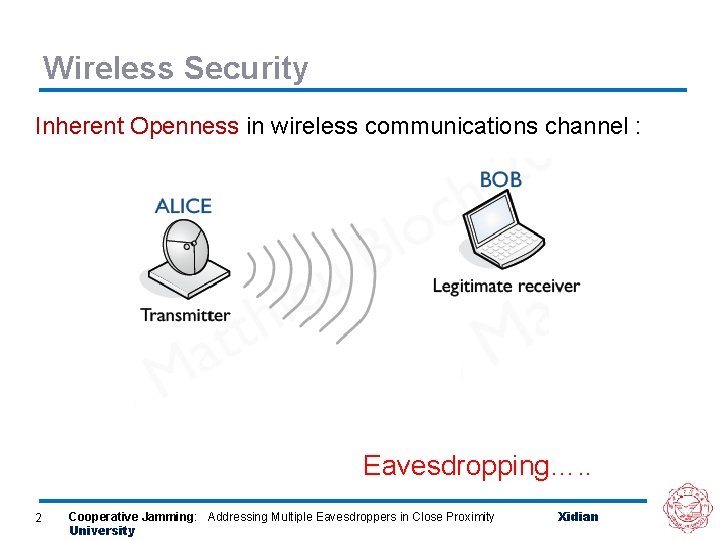
Wireless Security Inherent Openness in wireless communications channel : Eavesdropping…. . 2 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
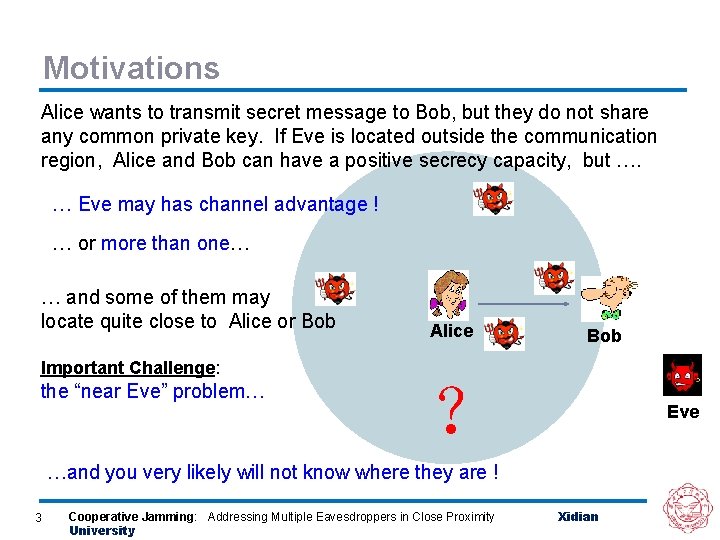
Motivations Alice wants to transmit secret message to Bob, but they do not share any common private key. If Eve is located outside the communication region, Alice and Bob can have a positive secrecy capacity, but …. … Eve may has channel advantage ! … or more than one… … and some of them may locate quite close to Alice or Bob Important Challenge: the “near Eve” problem… Alice Bob ? Eve …and you very likely will not know where they are ! 3 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
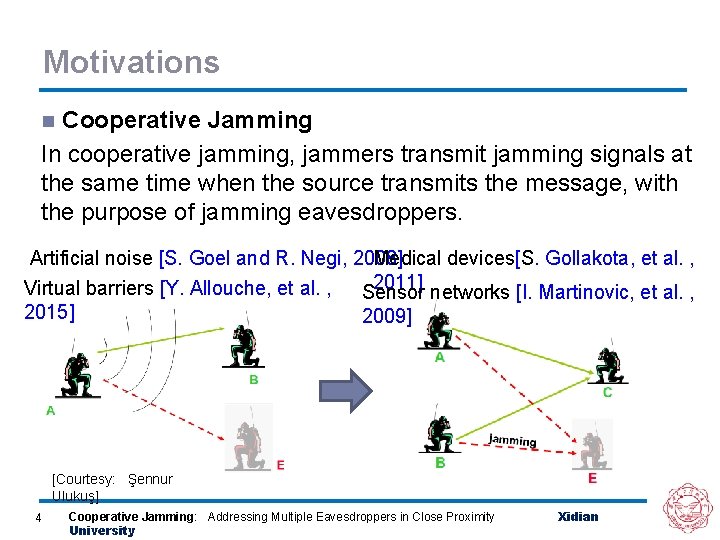
Motivations Cooperative Jamming In cooperative jamming, jammers transmit jamming signals at the same time when the source transmits the message, with the purpose of jamming eavesdroppers. n Artificial noise [S. Goel and R. Negi, 2008] Medical devices[S. Gollakota, et al. , 2011] networks [I. Martinovic, et al. , Virtual barriers [Y. Allouche, et al. , Sensor 2015] 2009] [Courtesy: Şennur Ulukuş] 4 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
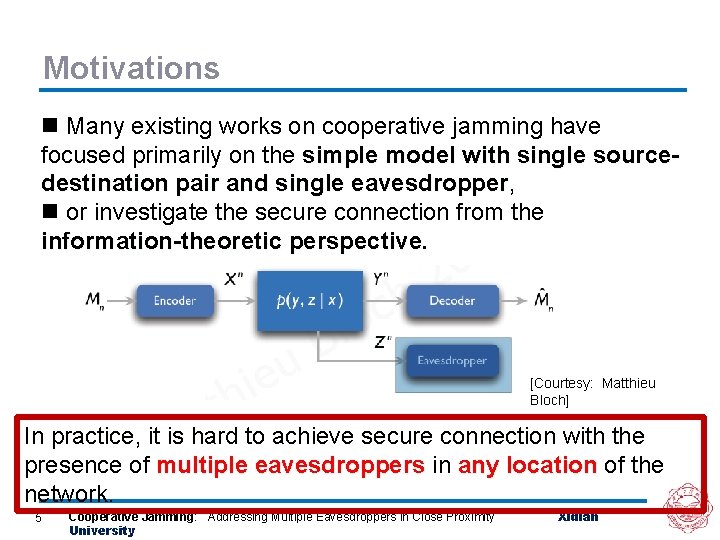
Motivations n Many existing works on cooperative jamming have focused primarily on the simple model with single sourcedestination pair and single eavesdropper, eavesdropper n or investigate the secure connection from the information-theoretic perspective. [Courtesy: Matthieu Bloch] In practice, it is hard to achieve secure connection with the presence of multiple eavesdroppers in any location of the network. 5 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian

Basic Ideas We consider the following scenario: n A source-destination pair S-D without a common private key, and in the presence of multiple eavesdroppers, eavesdroppers n the eavesdroppers may located near S or D, D n no constrict on the number of eavesdroppers, n and no location knowledge of eavesdroppers is available. Approaches: n Smart Jamming Strategy (Divide and Conquer Method) n Helper-Based Two-Stage Scheme (addressing nearby eavesdroppers) n Cooperative Jamming Strategy 6 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
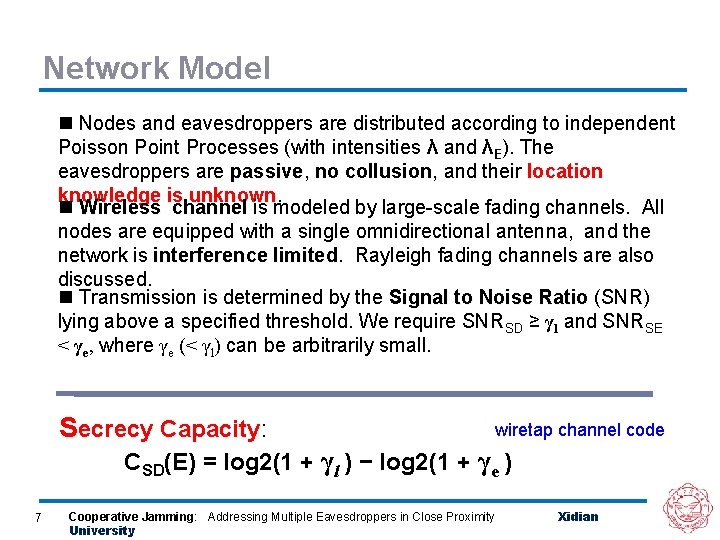
Network Model n Nodes and eavesdroppers are distributed according to independent Poisson Point Processes (with intensities λ and λE). The eavesdroppers are passive, passive no collusion, and their location knowledge is unknown n Wireless channel is modeled by large-scale fading channels. All nodes are equipped with a single omnidirectional antenna, and the network is interference limited Rayleigh fading channels are also discussed. n Transmission is determined by the Signal to Noise Ratio (SNR) lying above a specified threshold. We require SNRSD ≥ γl and SNRSE < γe, where γe (< γl) can be arbitrarily small. Secrecy Capacity: Capacity wiretap channel code CSD(E) = log 2(1 + γl ) − log 2(1 + γe ) 7 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian

Smart Jamming Strategy Divide and Conquer Smart jamming strategy has three steps: n Jammer Selection and Power Adjustment : Choose t legitimate nodes to act as jammers, and tune each jammer’s transmit power PJ until SNRSD ≥ γl. n Block construction : Each jammer can jam a M = M 1⊕M 2⊕ …⊕Mt, region. If t jammers can cover the whole n Message Transmission: Transmission communication region any eavesdropper Transmit each block one by one. w. h. p. , will lose at least one block When a block is delivering, a and can not recover the emits. Addressing noise. Multiple with. Eavesdroppers proper in Closemessage. Cooperative Jamming: Proximity Xidian 8 jammer University
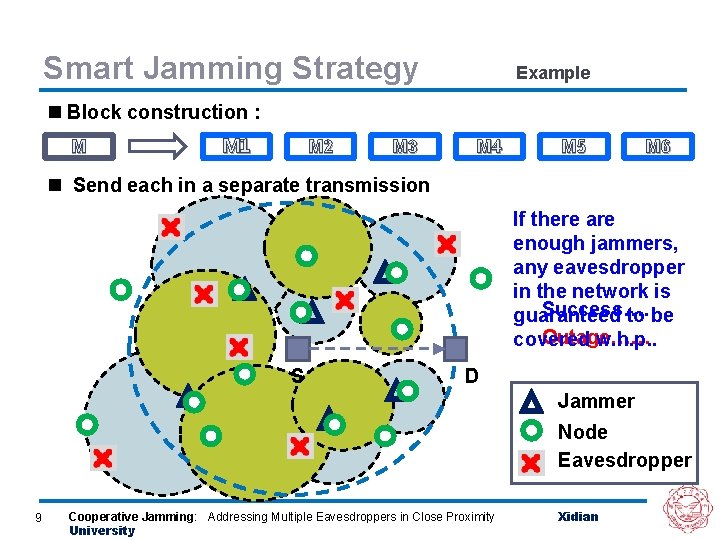
Smart Jamming Strategy Example n Block construction : M M 1 M 2 M 3 M 4 M 5 M 6 n Send each in a separate transmission If there are enough jammers, any eavesdropper in the network is Success…… guaranteed to be Outage…… covered w. h. p. . S D Jammer Node Eavesdropper 9 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
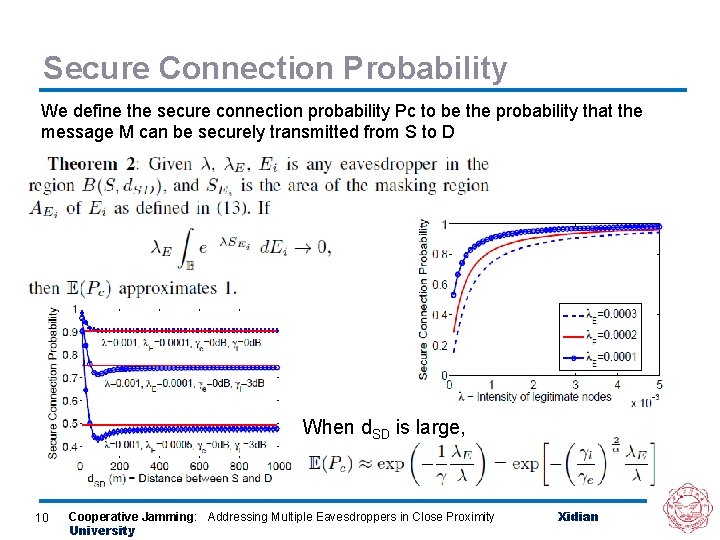
Secure Connection Probability We define the secure connection probability Pc to be the probability that the message M can be securely transmitted from S to D When d. SD is large, 10 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
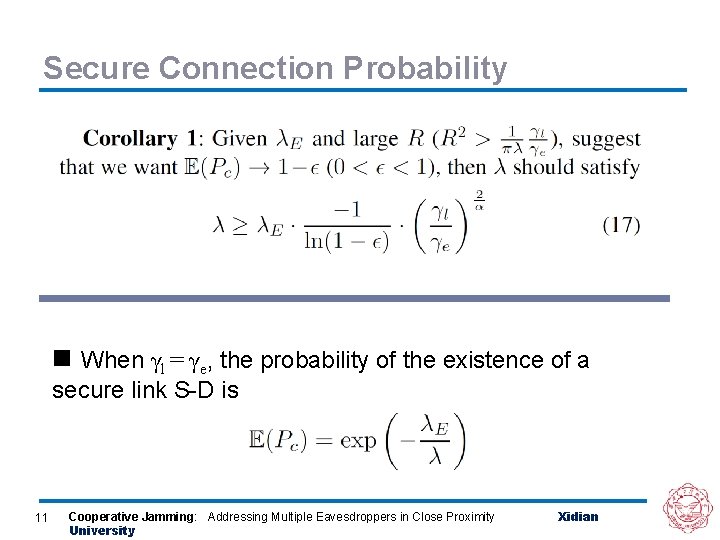
Secure Connection Probability n When γl = γe, the probability of the existence of a secure link S-D is 11 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
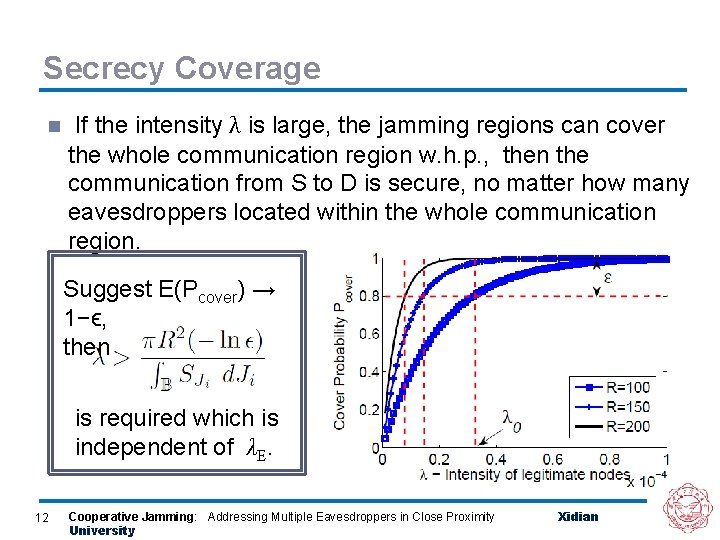
Secrecy Coverage n If the intensity λ is large, the jamming regions can cover the whole communication region w. h. p. , then the communication from S to D is secure, no matter how many eavesdroppers located within the whole communication region. Suggest E(Pcover) → 1−ϵ, then is required which is independent of λE. 12 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
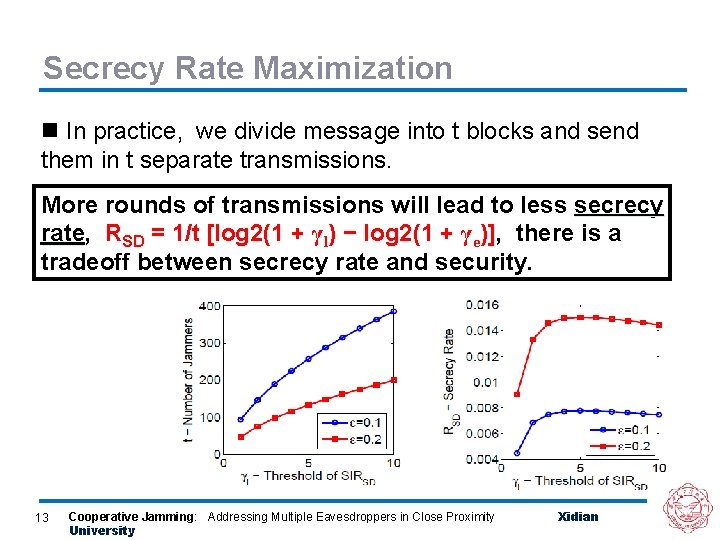
Secrecy Rate Maximization n In practice, we divide message into t blocks and send them in t separate transmissions. More rounds of transmissions will lead to less secrecy rate, rate RSD = 1/t [log 2(1 + γl) − log 2(1 + γe)], there is a tradeoff between secrecy rate and security. 13 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
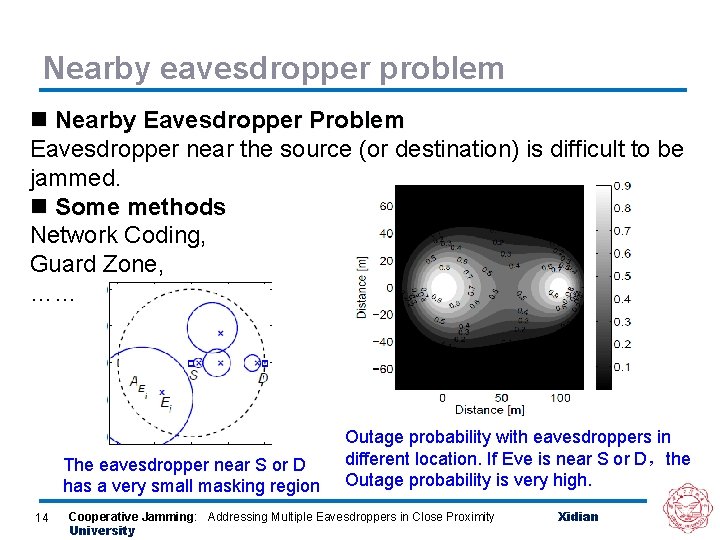
Nearby eavesdropper problem n Nearby Eavesdropper Problem Eavesdropper near the source (or destination) is difficult to be jammed. n Some methods Network Coding, Guard Zone, …… The eavesdropper near S or D has a very small masking region 14 Outage probability with eavesdroppers in different location. If Eve is near S or D,the Outage probability is very high. Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
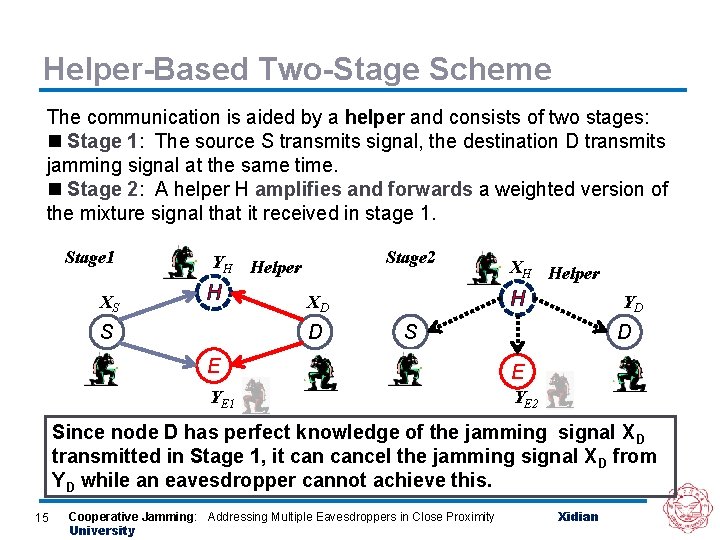
Helper-Based Two-Stage Scheme The communication is aided by a helper and consists of two stages: n Stage 1: The source S transmits signal, the destination D transmits jamming signal at the same time. n Stage 2: A helper H amplifies and forwards a weighted version of the mixture signal that it received in stage 1. Stage 1 XS Stage 2 YH Helper H S H XD D XH Helper YD S D E E YE 1 YE 2 Since node D has perfect knowledge of the jamming signal X D transmitted in Stage 1, it cancel the jamming signal X D from YD while an eavesdropper cannot achieve this. 15 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
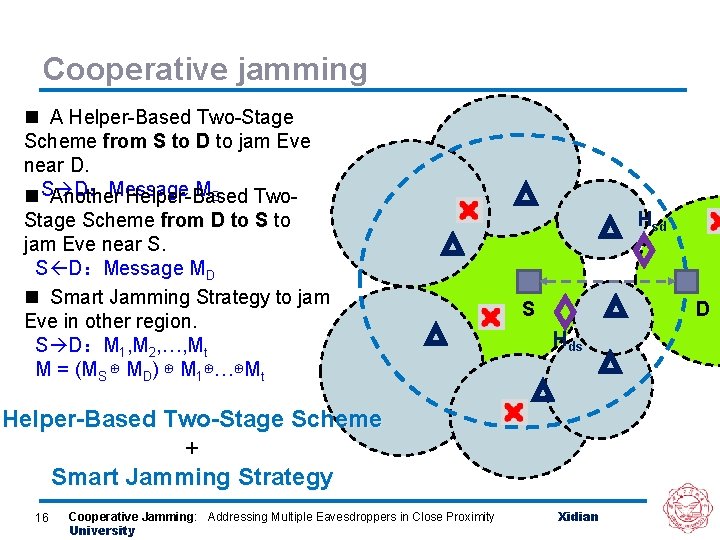
Cooperative jamming n A Helper-Based Two-Stage Scheme from S to D to jam Eve near D. MS n S D:Message Another Helper-Based Two. Stage Scheme from D to S to jam Eve near S. S D:Message MD n Smart Jamming Strategy to jam Eve in other region. S D:M 1, M 2, …, Mt M = (MS ⊕ MD) ⊕ M 1⊕…⊕Mt Hsd S D Hds Helper-Based Two-Stage Scheme + Smart Jamming Strategy 16 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
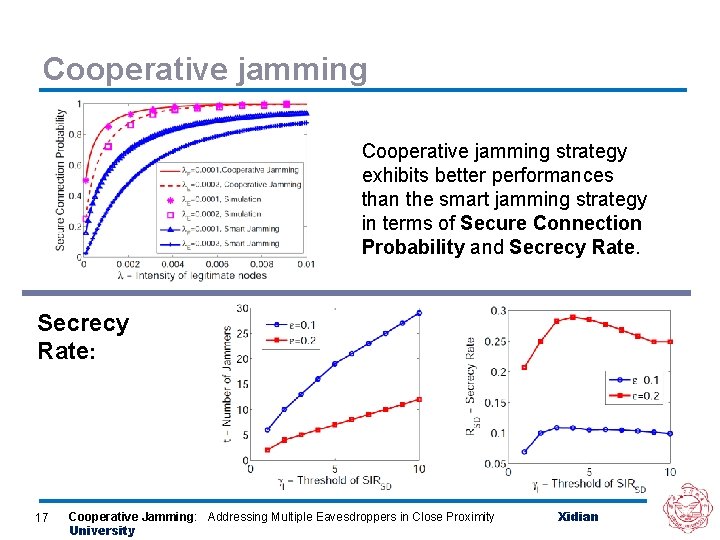
Cooperative jamming strategy exhibits better performances than the smart jamming strategy in terms of Secure Connection Probability and Secrecy Rate: 17 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
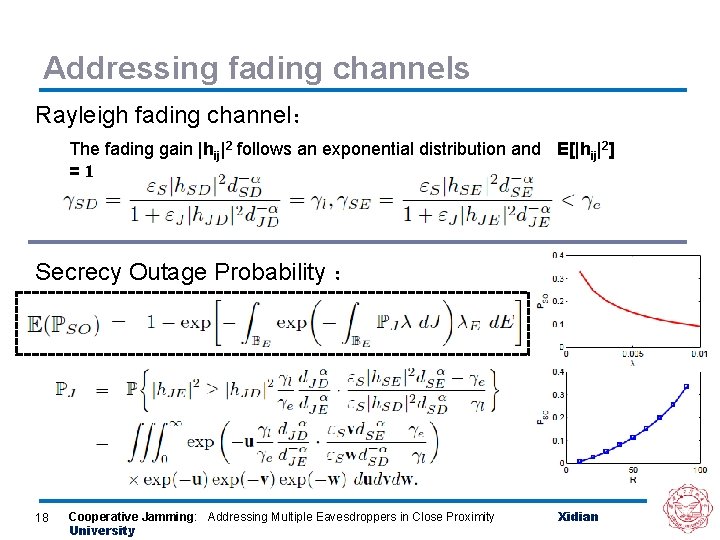
Addressing fading channels Rayleigh fading channel: The fading gain |hij|2 follows an exponential distribution and E[|hij|2] =1 Secrecy Outage Probability : 18 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
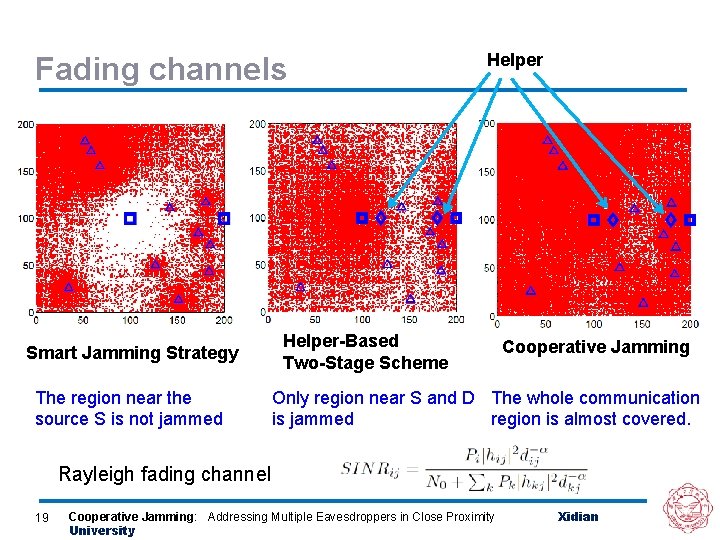
Fading channels Smart Jamming Strategy The region near the source S is not jammed Helper-Based Two-Stage Scheme Cooperative Jamming Only region near S and D The whole communication is jammed region is almost covered. Rayleigh fading channel 19 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian
Conclusions Cooperative jamming is a powerful tool to increase the security of wireless networks: n It can jam eavesdroppers anywhere in the network, even they are located quite close to the source or the destination, n and can tolerate any number of independent eavesdroppers. Many problems: n implementing in the existing infrastructure n better modeling adversary –e. g. , active adversaries n combining with cryptographic method … 20 Cooperative Jamming: Addressing Multiple Eavesdroppers in Close Proximity University Xidian

Thanks !
- Slides: 21