Personal Data Protection and Security Measures Justin Law















- Slides: 21

Personal Data Protection and Security Measures Justin Law IT Services - Information Security Team 25 & 27 November 2013

Agenda Ø Data protection Ø Data Classification Ø IT Security Good practices

Data protection Ø Data is one of the most valuable assets of the University Ø Data could be any factual information that is stored on computer, USB drive, Cloud and of course, on paper. Ø Risks of Data: 1. Theft 2. Loss 3. Leakage 4. Tamper

Data Classification

The importance of data classification • Allow us to identify the data • Manage the data better • Employ appropriate level of security for the data

Three-level Data Classification In order to handle data properly, data should be classified into categoriesclassification level. Three-level Classification: Public Sensitive Restricted

Three-level Classification Public • Data is generally open to the public. • No existing local, national or international legal restrictions on access. Example: Events and Activities, communications notices and publications. Public Sensitive Restricted

Three-level Classification Sensitive • Data is “Official Use Only” • Protected from unauthorized access due to proprietary, ethical or privacy considerations Example: Student Data; University partner or sponsor information where no NDA exists Public Sensitive Restricted

Three-level Classification Restricted • Data is protected by regulations, University policies or contractual agreement • Unauthorized access may result in significant financial risk or negative impacts on the reputation of the University Example: Personal Information, Payment Records, Medical records Public Sensitive Restricted

Data Handling Ø Level of precautions and security controls are relevant to the data classification Ø More protections for more sensitive data

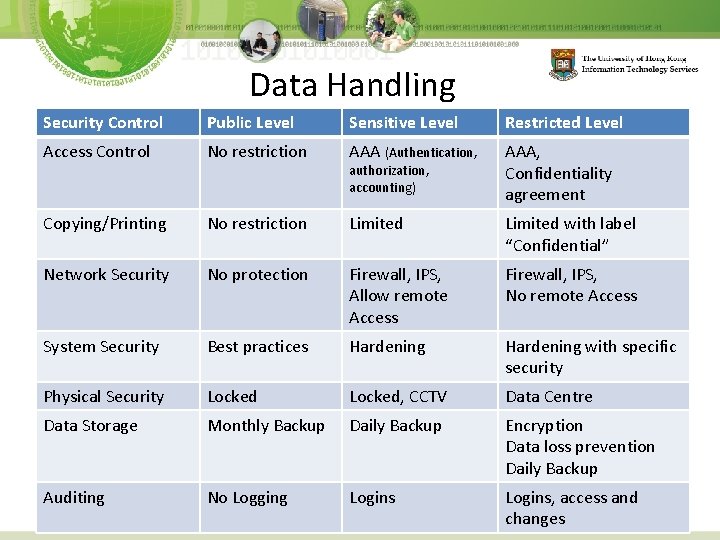
Data Handling Security Control Public Level Sensitive Level Restricted Level Access Control No restriction AAA (Authentication, AAA, Confidentiality agreement Copying/Printing No restriction Limited with label “Confidential” Network Security No protection Firewall, IPS, Allow remote Access Firewall, IPS, No remote Access System Security Best practices Hardening with specific security Physical Security Locked, CCTV Data Centre Data Storage Monthly Backup Daily Backup Encryption Data loss prevention Daily Backup Auditing No Logging Logins, access and changes authorization, accounting)

IT Security Good practices

Workstation Ø Use complex password, more than 8 characters Ø Enable login password and screen saver password Ø Logout when unattended Ø Do not install P 2 P software on computer that handles confidential data Ø Physically secure the notebook PC, tablet PC Ø Avoid using public computer to access confidential files Ø Using VPN or other secure channel for remotely access from the outside of the university

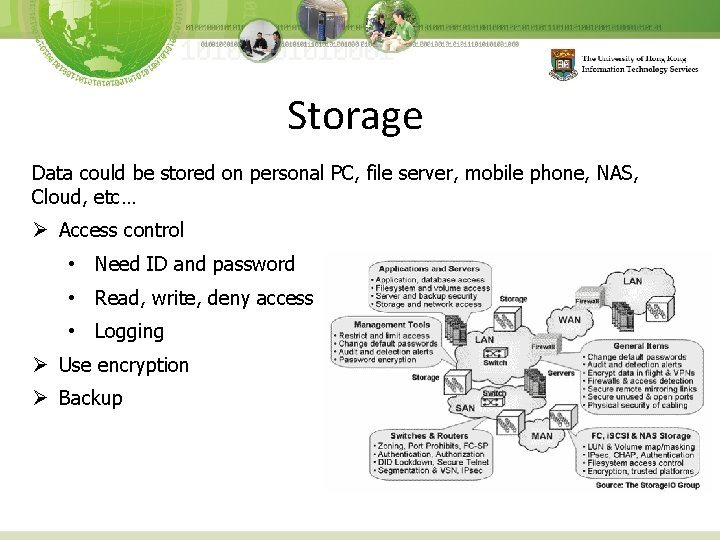
Storage Data could be stored on personal PC, file server, mobile phone, NAS, Cloud, etc… Ø Access control • Need ID and password • Read, write, deny access • Logging Ø Use encryption Ø Backup

Removable Storage Ø Only store sensitive data on portable devices or media when absolutely necessary Ø Use Encryption Ø Erase the data after use Ø Don’t leave USB drive unattended Ø Keep it safe Ø Don’t use USB drive from unknown source. Ø Report to supervisor if lost USB drive that contains sensitive data

Cloud storage Before putting data to Cloud, you should consider: Ø Privacy and confidentiality Ø Data retention § Impossible to eliminate Ø Data ownership Ø Data Encryption § being uploaded to, or downloaded from, and stored in the cloud Ø Exposure of data § to operator, local and foreign government and government agency

Social Networks Social networks are a great way to stay connected with others, but you should be wary about how much personal information you post. • Privacy and security settings • Once posted, always posted • Keep personal info personal • Know and manage your friends

Mobile Security “New Technology, old Privacy and Security issue” Ø Lost or stolen devices § Enable screen lock § Encrypt the data, such as email and documents § Alert the automatically login of company email and file server Ø Malware and virus § Steal bank details, Company Data, Personal identities, Email addresses Ø Install mobile security apps § Use Remote Wipe, Encryption and Anti-Virus

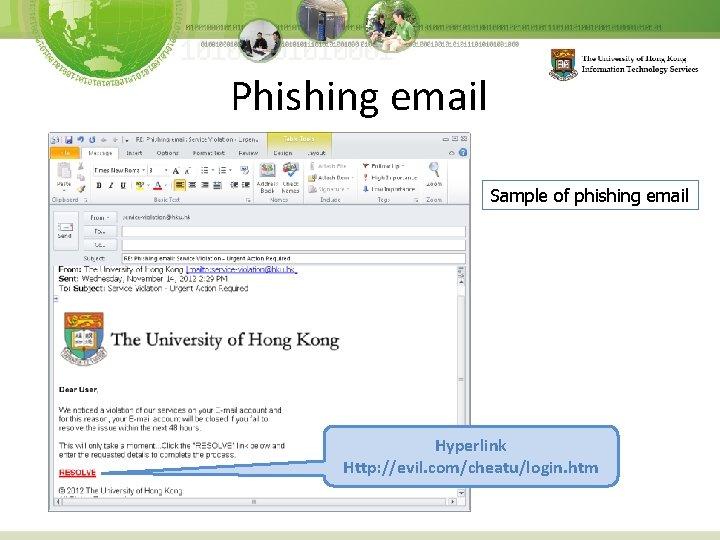
Phishing email Sample of phishing email Hyperlink Http: //evil. com/cheatu/login. htm

Phishing is the act of attempting to acquire information such as usernames and password by pretending from a trusted entity, e. g. ITS or other department of the university Ø Signs of a phishing email: • Not addressed to you by name • Asks for your username and password • “Business letters” but comes from suspicious email accounts Ø What to do if you received phishing email § Delete these suspicious emails § Don’t reply or click any link on them. § Refer to HKU Spam report web site http: //www. its. hku. hk/spam-report

Thank You