Performance and Security in a Distributed Wireless Networking

Performance and Security in a Distributed Wireless Networking Environment Thesis Proposal Defense Committee : Dr. Andrew Yang Dr. Alfredo Perez-Davila Ms. Wei Ding Presented by Karthik Sadasivam 6/14/2021 1

Motivation and Background n n n Wireless networks are being used in almost every organization today Latest trend in wireless networks is pervasive and ubiquitous computing – catering to both nomadic and fixed users anytime and anywhere 802. 11 or Wi-fi standards for Wireless Local Area Networks ( 802. 11 a, 802. 11 b, 802. 11 g, 802. 11 i) is most commonly used in enterprises today Distributed wireless networks are deployed over a wide geographic area and consist of mobile clients and base stations Two factors of prime importance in these networks – Performance and Security Achieving an optimal balance between these two factors in such networks is an ongoing research problem 6/14/2021 2
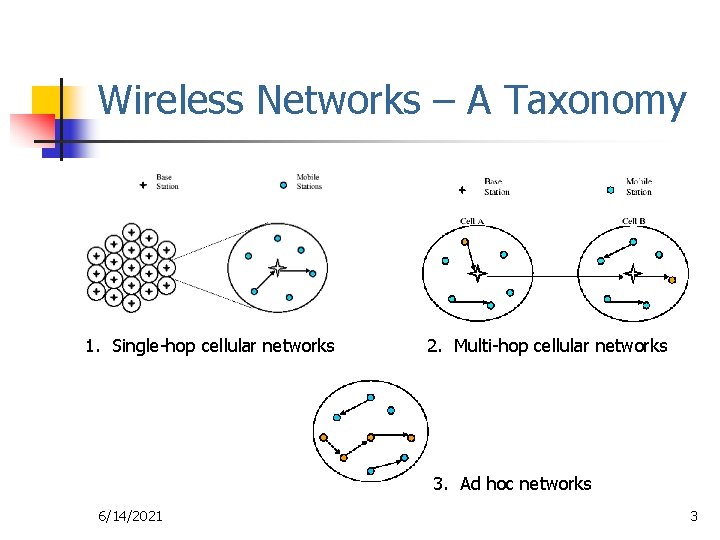
Wireless Networks – A Taxonomy 1. Single-hop cellular networks 2. Multi-hop cellular networks 3. Ad hoc networks 6/14/2021 3

Wireless Local Area Networks (WLANs) n n n A Wireless Local Area Network consists of a set of mobile clients communicating via an access point (AP). IEEE 802. 11 - adopted international standard for wireless LANs Transmission speeds ranging from 1 Mbps to 54 Mbps in either the 2. 4 GHz or 5 GHz frequency bands Various standards for IEEE 802. 11 – 802. 11 a, 802. 11 b, 802. 11 g, 802. 11 i 802. 11 protocol has been found to be vulnerable to several types of attacks such as Do. S, WEP key vulnerability, rogue APs 6/14/2021 4
Ultra Wide. Band (UWB) Networks n n n Latest standard for high speed wireless networks (200 -400 Mbps range) It works on impulse radio (short pulses of picoseconds duration) rather than carrier based radio US FCC has allocated a spectrum between 3. 1 and 10. 6 GHz Initially it was used in radar communications Current research aims at the development of Physical and higher layer protocols for its use in WPANs and WMANs (IEEE 802. 15 group for WPANs for PHY layer) 6/14/2021 5
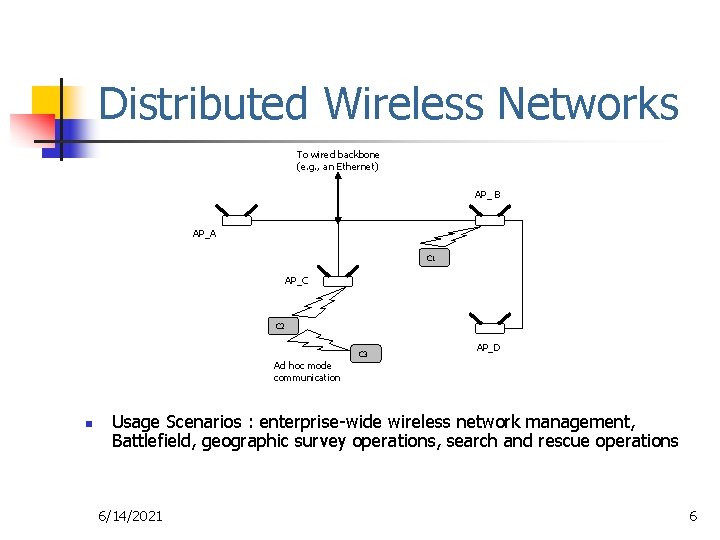
Distributed Wireless Networks To wired backbone (e. g. , an Ethernet) AP_ B AP_A C 1 AP_C C 2 Ad hoc mode communication n C 3 AP_D Usage Scenarios : enterprise-wide wireless network management, Battlefield, geographic survey operations, search and rescue operations 6/14/2021 6
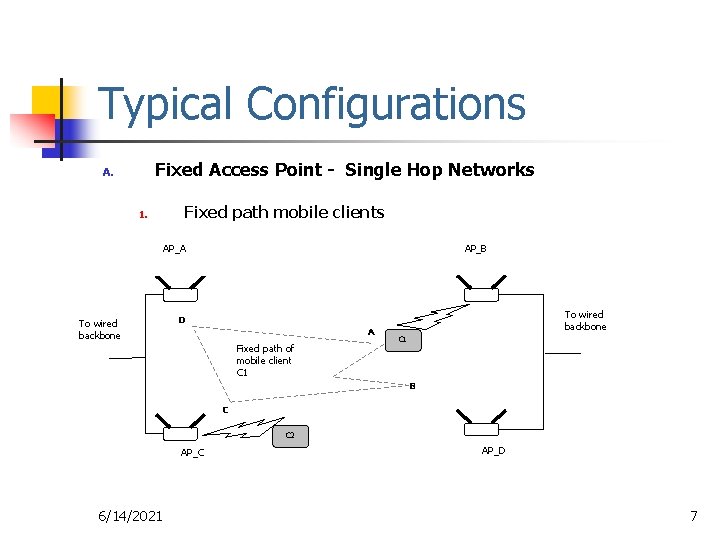
Typical Configurations Fixed Access Point - Single Hop Networks A. 1. Fixed path mobile clients AP_A To wired backbone AP_B To wired backbone D A Fixed path of mobile client C 1 B C C 2 AP_C 6/14/2021 AP_D 7
Typical Configurations (contd. ) Fixed Access Point - Single Hop Networks A. 2. Variable path (roaming) mobile clients AP_A AP_B To wired backbone B C 1 Variable path of mobile client C 1 AP_ C A AP_ D C 2 6/14/2021 C 2 out of range of all access points 8
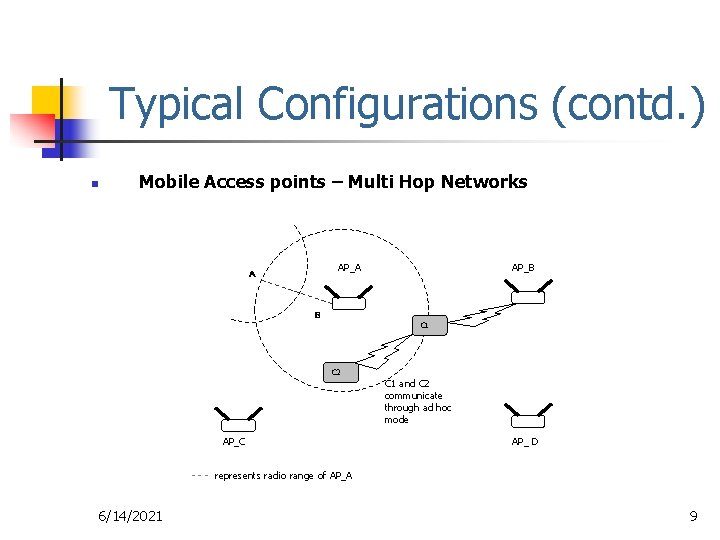
Typical Configurations (contd. ) n Mobile Access points – Multi Hop Networks AP_A A AP_B B C 1 C 2 AP_C C 1 and C 2 communicate through ad hoc mode AP_ D - - - represents radio range of AP_A 6/14/2021 9
Performance Factors The following are factors which affect performance of wireless networks in general: n n 6/14/2021 Number of nodes : Since bandwidth is shared equally among all nodes, the performance and throughput decreases as more nodes enter the network The underlying protocol : Each layer of the TCP/IP protocol suite adds its own header, which tends to affect the performance considerably. The topology: In case of a dynamically changing topology (for example, in ad hoc networks), the nodes have to maintain routing tables, which have to be recalculated every time a node leaves a current network and enters a new network 10
Performance Factors (contd. ) Fixed Access Point - Single Hop Networks n In addition to the factors listed above, the following factors are specific to these type of networks: n 1. 2. 6/14/2021 In the case of fixed path clients, the distance of the clients from the access point plays an important role in determining the performance In the case of roaming mobile clients , re-authentication is needed whenever a client moves away from the range of one access point to enter the range of another access point (known as ‘handoff’) 11
Performance Factors (contd. ) n n Performance in Mobile Access Point - Multi Hop Networks The following factors have been found to affect the performance of multi hop wireless networks. Routing protocols: Most of the routing protocols used for ad hoc networks demand considerable bandwidth and power Node speed : With increase in node mobility, the routing overhead and the bit error rate increases Traffic sources: In multi hop networks, the source of traffic keeps varying constantly. At a particular instant of time, if we measure the bandwidth for a particular traffic source, it may not remain constant over a period of time as the topology changes. 6/14/2021 12
Performance Metrics n Measurement of performance in a wireless network involves many interdependent factors. We consider the packet-level metrics only for sake of simplicity n End-to-End Throughput - Measure of the number of packets successfully transmitted to their final destination per unit time. . n End-to-End Delay - Average time a packet takes to reach its destination n Link Utilization - Long term proportion of time or probability that there is transmission on the link. n Packet Loss - Ratio of transmitted packets that may have been discarded or lost in the network. 6/14/2021 13

Security issues n n In a distributed wireless network composed of both wired and wireless segments, the threat to the network is doubled. Some of the threats are common to both wireless and wired networks such asn invasion and resource stealing n traffic redirection. n Denial of Service (Do. S) Others are specific to wireless networks such as – Rogue APs, WEP key vulnerability, MAC address spoofing, etc. Ad hoc networks introduce more security issues in routing since there are no inherent security mechanisms. 6/14/2021 14

Security issues (contd. ) n Authentication is one of the most important security issues for distributed wireless networks. The following are types of authentication methods used: n Mutual authentication – Both the authenticator and the user must be able to mutually authenticate each other, in order to prevent threats such as rogue access points. . n Self-protecting – A wireless node must protect itself from eavesdropping and impersonation n Immune to dictionary attacks n Secure session keys - Session keys provide message authentication, confidentiality and integrity for the user session. n n 6/14/2021 User-level authentication Fast re-authentication – important in the case of roaming clients 15

Security issues (contd. ) n n Classification of Authentication methods: Certificate based methods – Such methods use public key infrastructure (PKI) to authenticate users. E. g PEAP and EAP n Disadvantage: n . n n Password based methods – They are based on password authentication mechanism. E. g Cisco’s LEAP n Disadvantage : i. 6/14/2021 cost of administration provides device authentication rather than userlevel authentication more prone to attacks such as the Man-in-the. Middle (MITM) 16
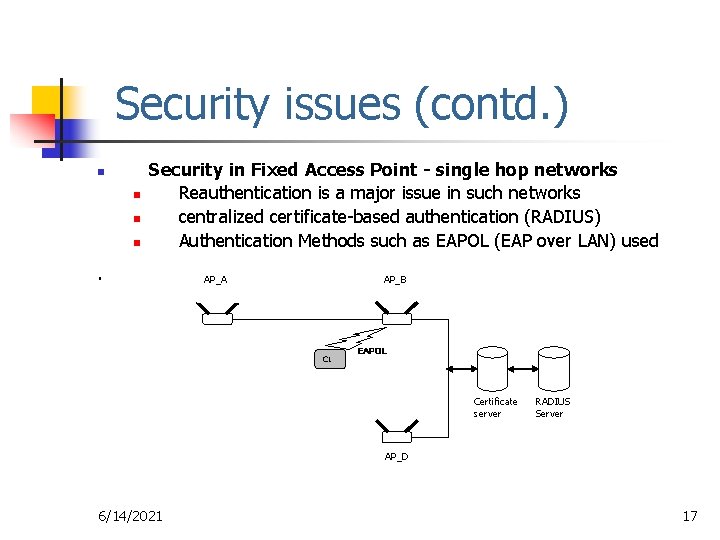
Security issues (contd. ) n n Security in Fixed Access Point - single hop networks Reauthentication is a major issue in such networks centralized certificate-based authentication (RADIUS) Authentication Methods such as EAPOL (EAP over LAN) used . AP_A AP_B C 1 EAPOL Certificate server RADIUS Server AP_D 6/14/2021 17
Security issues (contd. ) n n n Security in Mobile Access point – Multi Hop Networks Inter-Access Point authentication required in this case. Inter Access Point Protocol is used for this purpose Security in routing between mobile hostsn No centrally administered secure routers n No strict security policies n Highly dynamic nature of MANETs n Current ad hoc protocols trust all participating nodes. 6/14/2021 18

Research Plan n n The study of performance will mostly be simulation-based A comparison of various factors affecting the performance will be done and most important ones will be derived Test cases will be drawn for these factors The major security issues in distributed networks will be studied and the impact of them on the performance will be analyzed The results of the security and performance analysis from these cases will be aggregated and compared to determine the tradeoffs between these two factors, so that an optimal solution may be achieved. 6/14/2021 19
Methods and instrumentation § n Hardware n Pentium IV or higher machine with 512 MB RAM and wireless network adapter n Cisco Wireless Access Point Software n Operating Systems: Windows 2 K/ XP, Linux n Network simulators n Ns-2 n OPNET n Programming platform: Java SDK 1. 4. 2 n 6/14/2021 Cisco Aironet client utility (ACU) 20

Acknowledgements My sincere thanks to Dr. Andrew Yang for his support and guidance and the NSF for funding my position 6/14/2021 21

Thank you! Any Questions? 6/14/2021 22
- Slides: 22