PEER TO PEER COMPUTING PAPER 4 3 COMPUTER






- Slides: 9

PEER TO PEER COMPUTING PAPER: 4. 3 COMPUTER APPLICATIONS IN BUSINESS THEORY for B. COM(HONS) SEM: IV SEC: D SHRUTI GULATI

�Peer-to-peer (P 2 P) computing or networking is created when two or more PCs are connected and share resources without going through a separate server computer. Peers are both suppliers and consumers of resources, in contrast to the traditional client-server model in which the consumption and supply of resources is divided. �

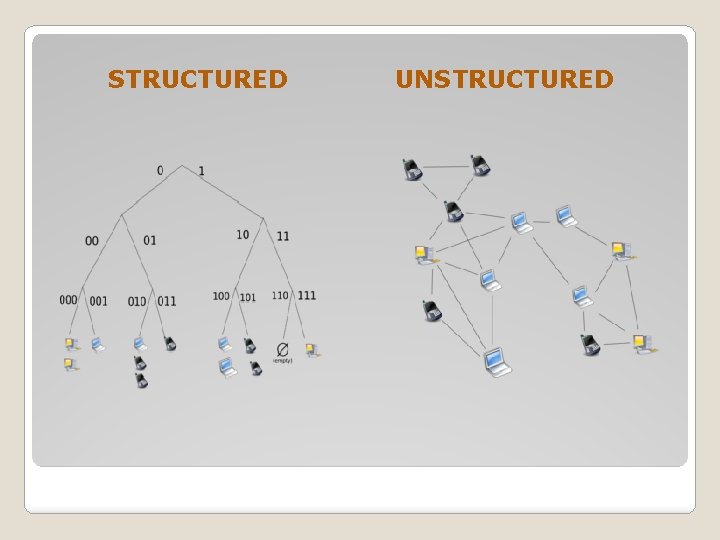
TYPES OF P 2 P NETWORKS�UNSTRUCTURED NETWORKSUnstructured peer-to-peer networks do not impose a particular structure on the overlay network by design. Because there is no structure globally imposed upon them, unstructured networks are easy to build and allow for localized optimizations to different regions of the overlay.

�STRUCTURED NETWORKSIn structured peer-to -peer networks the overlay is organized into a specific topology, and the protocol ensures that any node can efficiently search the network for a file/resource, even if the resource is extremely rare.

STRUCTURED UNSTRUCTURED

APPLICATIONS�CONTENT DELIVERYIn P 2 P networks, clients both provide and use resources. �COPYRIGHT INFRINGEMENTSCompanies developing P 2 P applications have been involved in numerous legal cases , over conflicts with copyright law.

�ADVANTAGES �It OF P 2 P- is easier to set up �In peer-to-peer networks all nodes are act as server as well as client therefore no need of dedicated server. �Less expensive. �Easier to set up and use

�DISADVANTAGES �A OF P 2 P- computer can be accessed anytime. �Network security has to be applied to each computer separately. �Backup has to be performed on each computer separately. �No centralized server is available to manage and control the access of data.

�EXAMPLES �SKYPE �BITCOIN �SPOTIFY �TRADEPAL OF P 2 P-