Password Hashing Dan Johnson What is a hashing
















- Slides: 19

Password Hashing Dan Johnson

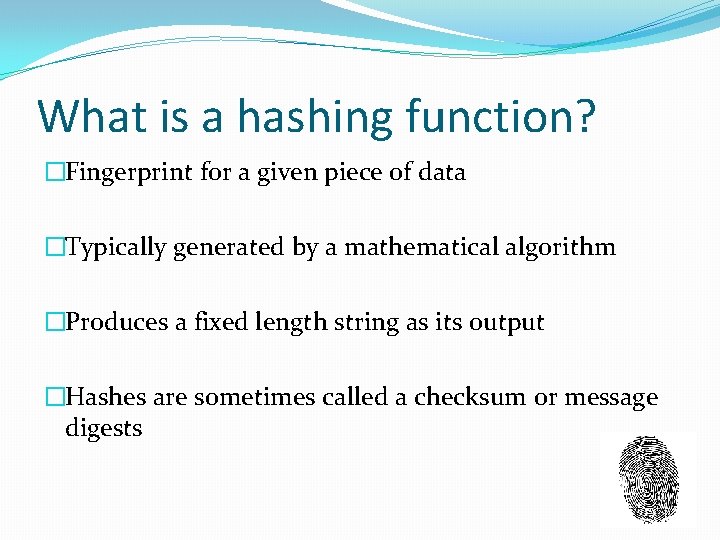
What is a hashing function? �Fingerprint for a given piece of data �Typically generated by a mathematical algorithm �Produces a fixed length string as its output �Hashes are sometimes called a checksum or message digests

Cryptographic hashing functions �Have four major properties: �It is impossible for any given output to determine the original input. � This does not mean we can’t use inference to find input that is likely correct �It is easy to compute the hash of any given input. � Easy means that it does not require a lot of system resources or time to compute the hash of a given input.

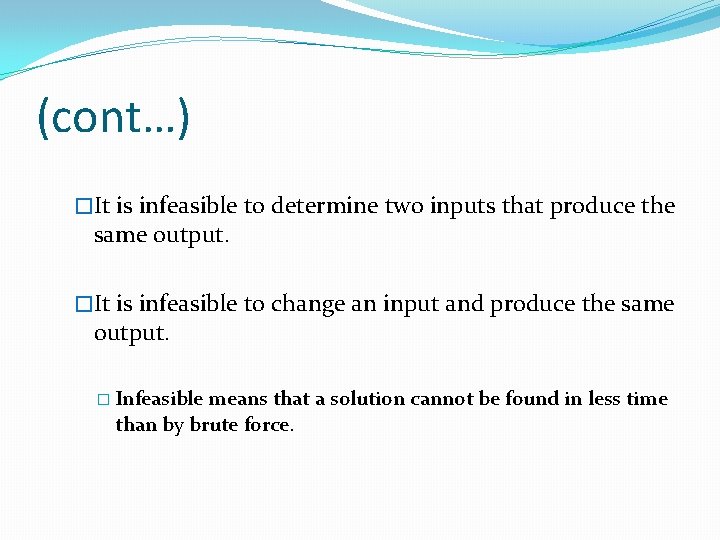
(cont…) �It is infeasible to determine two inputs that produce the same output. �It is infeasible to change an input and produce the same output. � Infeasible means that a solution cannot be found in less time than by brute force.

Cryptographic Strength �Determined by output length and ability to resist cryptanalytic attack �Output length expressed in number of bits �Attacks attempt to break one of the cryptographic properties.

Preimage Attacks �Two types, “first-preimage” and “second-preimage” �Both attempt to break the one way property of the hashing function �Both are similar in nature �If a hashing function is vulnerable to one form of preimage attack, it is likely vulnerable to the other form of attack �Successful attack executes in less that brute force time

Collision Attack �A collision occurs when two pieces of input produce the same output. �Collision attacks take advantage of a property of probability theory called the birthday paradox or birthday problem. �Collision attacks attempt to find a collision in less than O(2 n/2)

MD 5 �Published by Ronald Rivest in 1994. �Produces 128 -bit output, represented by 32 bit hexadecimal number. �Vulnerable to collision attacks. �Now mostly used for creating checksums of large files.

SHA-1 �Created by the National Security Agency �Creates a 160 -bit message digest represented by a 20 character string �More secure than MD 5 �Widely popular and used in many applications �In 2005, a group of Chinese researches discovered mathematical errors that could lead to a preimage attack in less than brute force time. �No known attacks based on these findings have surfaced.

SHA-256 �Also created by NSA as a part of the SHA 2 family which includes SHA 224, SHA 256 and SHA 512. �Creates a 256 bit output, hence its name. �Considered to be more secure than SHA 1 because of increased bit size. �Mathematical problems found in SHA 1 are not present in SHA 256. �Less popular than SHA 1.

Hash Based Authentication �Works the same way as password authentication �Store hashed value of password in database instead of password itself �When a user attempts to authenticate, hashes input value and compares it with value stored in database �“password” => [�aäɹ? ? ツ%lø 3~æマØ

Example implementation �Consider the following PHP code snippet. �From this we can clearly see that adding hash based authentication does not add a much code.

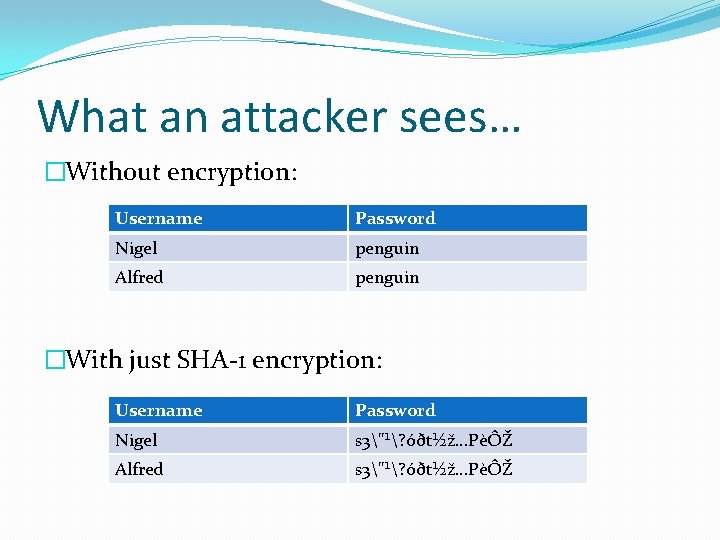
What an attacker sees… �Without encryption: Username Password Nigel penguin Alfred penguin �With just SHA-1 encryption: Username Password Nigel s 3"¹? óðt½ž…PèÔŽ Alfred s 3"¹? óðt½ž…PèÔŽ

Cont… �Can this be improved? �Better solution: sha 1( username + password) Username Password Nigel äQÞË‚HBŽ{<7 r‚¿i}_H Alfred 4ŠT@Œ‚ ›e. V€J×ÜÇ �Even better solution: �sha 1(username) + sha 1(password) ) Username Password Nigel äQÞË‚HBŽ{<7 r‚¿i}_H Alfred 4ŠT@Œ‚ ›e. V€J×ÜÇ

Microsoft Store India �Earlier this year, the Microsoft Store web site for India was breached. �Attackers stole hundreds of thousands of usernames and passwords. �All passwords were stored in plaintext. �Credit Card information was also not encrypted in any from. �Many users had their identity compromised and fraudulent purchases charged to their credit card.

Sony �Playstation Network and Sony Pictures customer databases were both breached in 2011. �Credit card information was encrypted, but several reports indicate that encryption may have been compromised. �User data was not encrypted in any way. �Class action lawsuit filed over negligence.

Other protection methods �Hashing not good for everything. �Credit card information could be stored using symmetric key encryption. �This allows for the input to be determined at a later date. �BE SUPER CAREFUL!

Questions?

References � Agarwal, A. (2012, February 27). Not just email addresses, credit card numbers also stolen from microsoft india store. Retrieved from http: //www. labnol. org/india/microsoft-indiastore-hacked/20891/ � Gallagher, S. (2012, February 14). Microsoft's store site in india defaced; hackers find plain text passwords. Retrieved from http: //arstechnica. com/business/news/2012/02/microsofts-store-site-in-india-defacedhackers-find-plain-text-passwords. ars � Mc. Glinn, J. (2005, March 20). Password hashing. Retrieved from http: //phpsec. org/articles/2005/password-hashing. html � Silva, J. (2003). An overview of cryptographic hash functions and their uses. Retrieved from http: //www. sans. org/reading_room/whitepapers/vpns/overview-cryptographichash-functions_879 � Schneier, B. , & Hoffman, P. (2005). attacks on cryptographic hashes in internet protocols. Retrieved from http: //www. ietf. org/rfc 4270. txt � Schwartz, M. (2011, June 3). Sony hacked again, 1 million passwords exposed. Retrieved from http: //www. informationweek. com/news/security/attacks/229900111 � Stallings, W. , Brown, L. , & Howard, M. (2008). Computer security, principles and practice. Upper Sadddle River, NJ: Pearson Education. � Ullrich, J. (2011, June 28). Hashing passwords. Retrieved from http: //www. dshield. org/diary. html? storyid=11110