Part II Access Control Authorization Part 2 Access











- Slides: 49

Part II: Access Control Authorization Part 2 Access Control 1

Chapter 8: Authorization It is easier to exclude harmful passions than to rule them, and to deny them admittance than to control them after they have been admitted. Seneca You can always trust the information given to you by people who are crazy; they have an access to truth not available through regular channels. Sheila Ballantyne Part 2 Access Control 2

Authentication vs. Authorization q Authentication Are you who you say you are? o Restrictions on who (or what) can access system q Authorization Are you allowed to do that? o Restrictions on actions of authenticated users q Authorization is a form of access control q Classic view of authorization… o Access Control Lists (ACLs) o Capabilities (C-lists) Part 2 Access Control 3

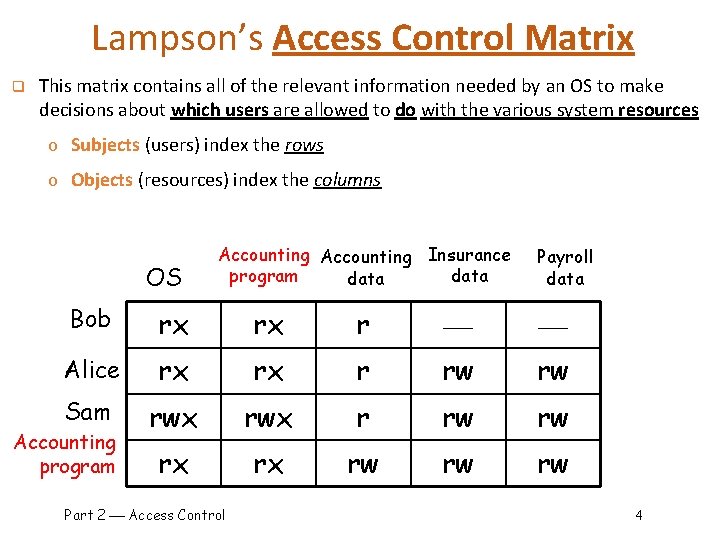
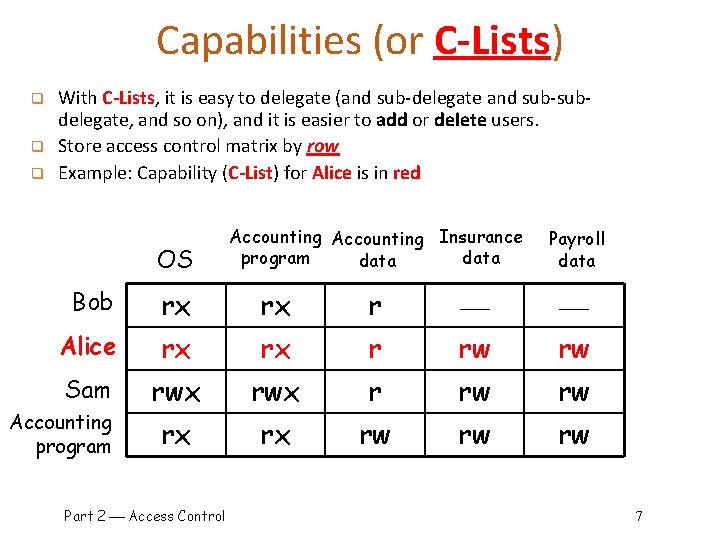
Lampson’s Access Control Matrix q This matrix contains all of the relevant information needed by an OS to make decisions about which users are allowed to do with the various system resources o Subjects (users) index the rows o Objects (resources) index the columns OS Accounting Insurance program data Payroll data Bob rx rx r Alice rx rx r rw rw Sam rwx r rw rw rx rx rw rw rw Accounting program Part 2 Access Control 4

Are You Allowed to Do That? q q Access control matrix has all relevant info Since all subjects and all objects appear in the access control matrix, o it contains all of the relevant information on which authorization decisions can be based. q q Could be 100’s of users, 10, 000’s of resources o Then, the matrix has 1, 000’s of entries How to manage such a large matrix? Note: We need to check this matrix before access to any resource by any user How to make this more efficient/practical? o ACLs and C-lists are derived from Lampson's access control matrix, which has a row for every subject and a column for every object Part 2 Access Control 5

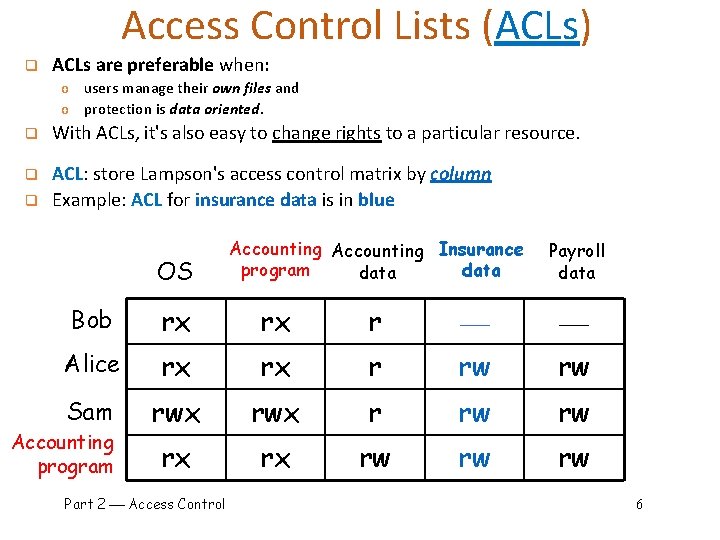
Access Control Lists (ACLs) q ACLs are preferable when: o users manage their own files and o protection is data oriented. q With ACLs, it's also easy to change rights to a particular resource. q ACL: store Lampson's access control matrix by column Example: ACL for insurance data is in blue q OS Accounting Insurance program data Payroll data Bob rx rx r Alice rx rx r rw rw Sam rwx r rw rw rx rx rw rw rw Accounting program Part 2 Access Control 6

Capabilities (or C-Lists) q q q With C-Lists, it is easy to delegate (and sub-delegate and sub-subdelegate, and so on), and it is easier to add or delete users. Store access control matrix by row Example: Capability (C-List) for Alice is in red OS Accounting Insurance program data Payroll data Bob rx rx r Alice rx rx r rw rw Sam rwx r rw rw rx rx rw rw rw Accounting program Part 2 Access Control 7

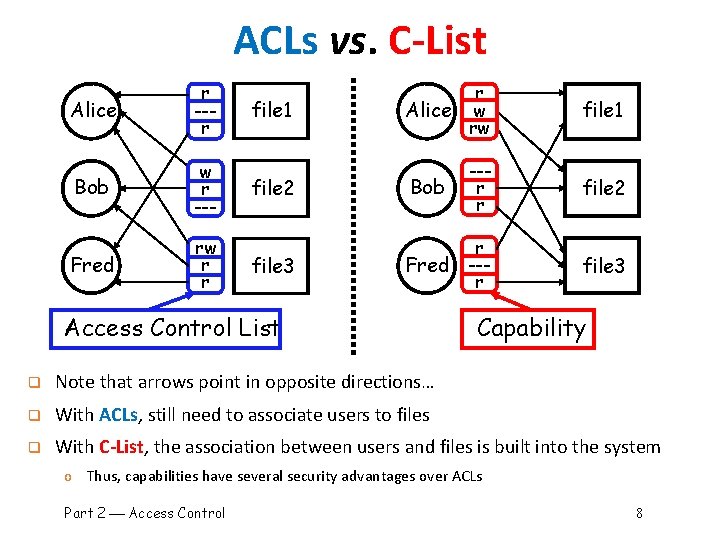
ACLs vs. C-List Alice r --r Bob w r --- Fred rw r r file 1 r Alice w rw file 1 file 2 Bob --r r file 2 Fred r --r file 3 Access Control List Capability q Note that arrows point in opposite directions… q With ACLs, still need to associate users to files q With C-List, the association between users and files is built into the system o Thus, capabilities have several security advantages over ACLs Part 2 Access Control 8

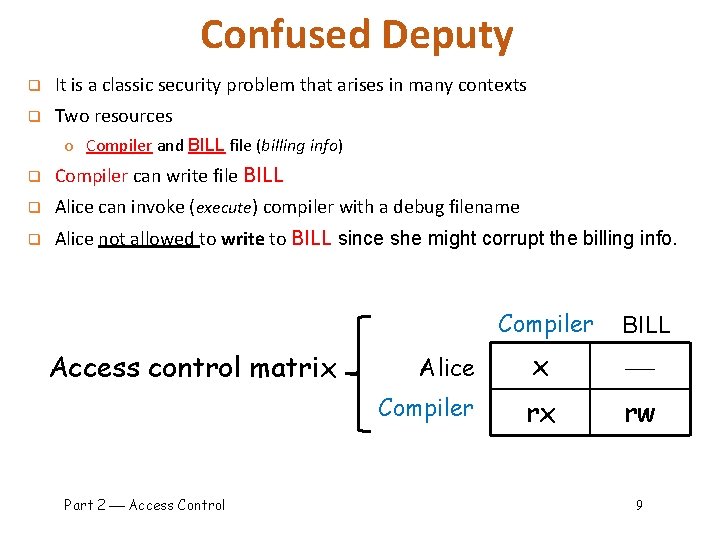
Confused Deputy q It is a classic security problem that arises in many contexts q Two resources o Compiler and BILL file (billing info) q Compiler can write file BILL q Alice can invoke (execute) compiler with a debug filename q Alice not allowed to write to BILL since she might corrupt the billing info. Access control matrix Part 2 Access Control Compiler BILL Alice x Compiler rx rw 9

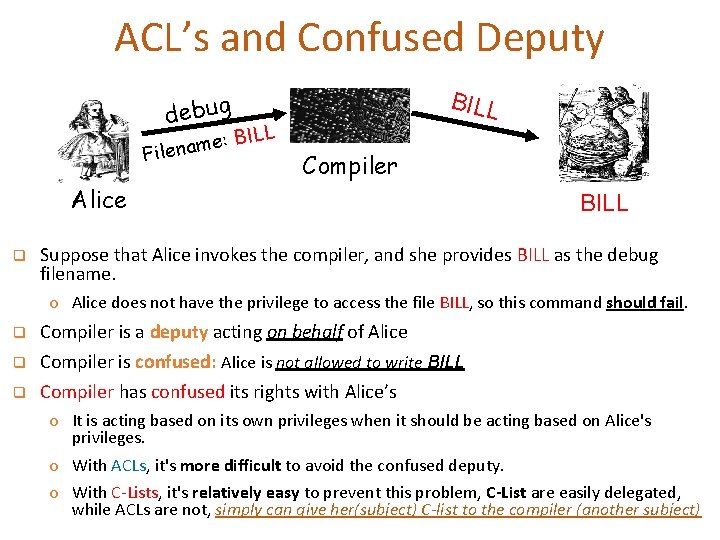
ACL’s and Confused Deputy BILL debug LL I B : e Filenam Compiler Alice q BILL Suppose that Alice invokes the compiler, and she provides BILL as the debug filename. o Alice does not have the privilege to access the file BILL, so this command should fail. q q q Compiler is a deputy acting on behalf of Alice Compiler is confused: Alice is not allowed to write BILL Compiler has confused its rights with Alice’s o It is acting based on its own privileges when it should be acting based on Alice's privileges. o With ACLs, it's more difficult to avoid the confused deputy. o With C-Lists, it's relatively easy to prevent this problem, C-List are easily delegated, while ACLs are not, simply can give her(subject) C-list to the compiler (another subject)

ACLs vs. C-List q ACLs o Good when users manage their own files o Protection is data-oriented o Easy to change rights to a resource q C-List o Easy to delegate § Due to the ability to delegate, it's easy to avoid the confused deputy when using capabilities, avoid the confused deputy o Easy to add/delete users o More difficult to implement q Capabilities loved by academics o Capability Myths Demolished Part 2 Access Control 11

Multilevel Security (MLS) Models Part 2 Access Control 12

Classifications vs. Clearances • MLS is needed when subjects/objects at different levels, different subjects access the same system • MLS is a form of Access Control Classifications apply to objects q Clearances apply to subjects q E. g. US Department of Defense (Do. D) uses 4 levels: q TOP SECRET CONFIDENTIAL UNCLASSIFIED Part 2 Access Control 13

Clearances and Classification q To obtain a SECRET clearance requires a o routine background check q A TOP SECRET clearance requires o extensive background check q Practical classification problems o Proper classification not always clear o Level of granularity to apply classifications o Aggregation flipside of granularity q For Do. D levels, we have TOP SECRET > CONFIDENTIAL > UNCLASSIFIED Part 2 Access Control 14

CAPTCHA Part 2 Access Control 15

q CAPTCHA o Completely Automated Public Turing test: to tell Computers and Humans Apart q Completely Automated: o test is generated and scored by computers q Public: o program and data are public q Turing test to tell: o humans can pass the test, but machines cannot o Also known as HIP == Human Interactive Proof q Like an inverse Turing test (sort of…) Part 2 Access Control 16

CAPTCHA Paradox? q Paradox: “…CAPTCHA is a program that can generate and grade tests that it itself cannot pass…” q CAPTCHA purpose? o Only humans get access (not bots / not computers) q So, CAPTCHA is for access control q Why CAPTCHA? o Free email services spammers like to use bots to sign up for 1000 s of email accounts § CAPTCHA employed so only humans get accounts o Sites that do not want to be automatically indexed by search engines § CAPTCHA would force human intervention Part 2 Access Control 17

CAPTCHA: Rules of the Game q Easy for most humans to pass q Difficult or impossible for machines to pass o Even with access to CAPTCHA software q From Trudy’s perspective, the only unknown is a random numbers/words/text o Similar to Kerckhoffs’ Principle q Good to have different CAPTCHAs in case someone cannot pass one type o E. g. , blind person could not pass visual CAPTCHA q q q Test: Find 2 words in the following Easy for most humans A (difficult? ) OCR problem for computer o OCR Optical Character Recognition Part 2 Access Control 18

CAPTCHAs q Current types of CAPTCHAs o Visual like previous example o Audio distorted words or music q No text-based CAPTCHAs o Maybe this is impossible…or even possible to pass by a machine q CAPTCHA’s and AI o OCR is a challenging AI problem § Hardest part is the segmentation problem § Humans good at solving this problem o Distorted sound makes good CAPTCHA § Humans also good at solving this o Hackers who break CAPTCHA have solved a hard AI problem (such as OCR) § So, putting hacker’s effort to good use! o Other ways to defeat CAPTCHAs? ? ? Part 2 Access Control 19

Firewalls Part 2 Access Control 20

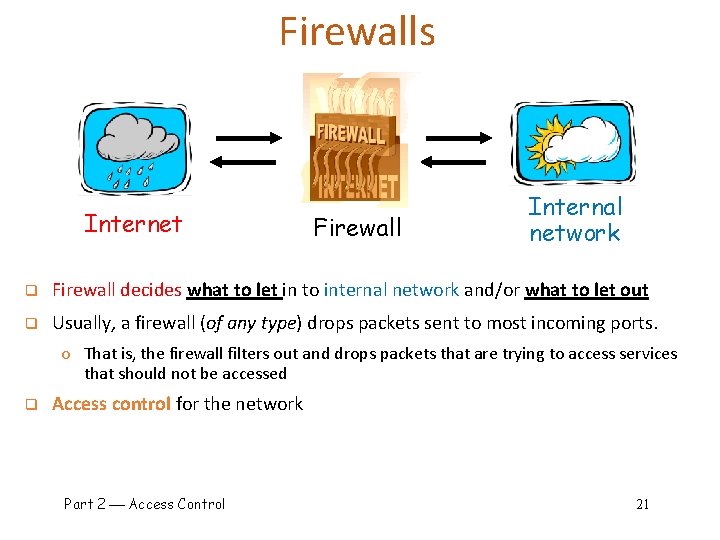
Firewalls Internet Firewall Internal network q Firewall decides what to let in to internal network and/or what to let out q Usually, a firewall (of any type) drops packets sent to most incoming ports. o That is, the firewall filters out and drops packets that are trying to access services that should not be accessed q Access control for the network Part 2 Access Control 21

Firewall q A firewall is like a secretary q To meet with an executive o First contact the secretary, then Secretary decides if meeting is important. So, secretary filters out many requests q You want to meet chair of CS department? o Secretary does some filtering q You want to meet President? o Secretary does lots of filtering q Types of firewalls o Packet filter § works at network layer o Stateful packet filter § works at transport layer o Application proxy § works at application layer

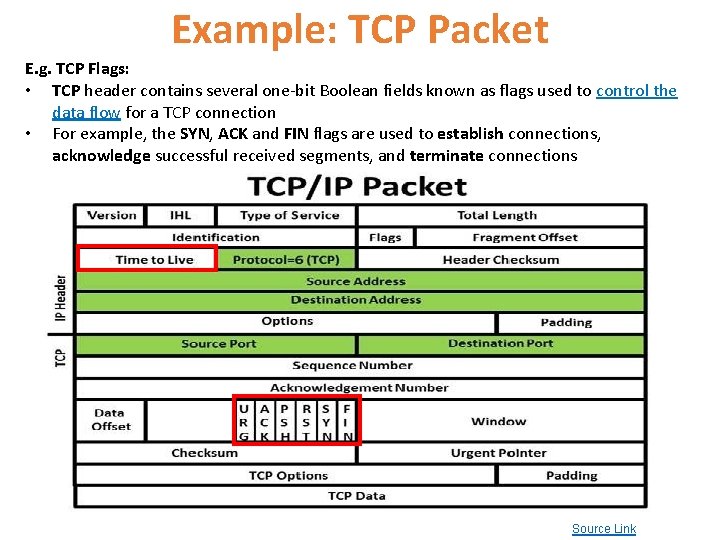
Example: TCP Packet E. g. TCP Flags: • TCP header contains several one-bit Boolean fields known as flags used to control the data flow for a TCP connection • For example, the SYN, ACK and FIN flags are used to establish connections, acknowledge successful received segments, and terminate connections Source Link

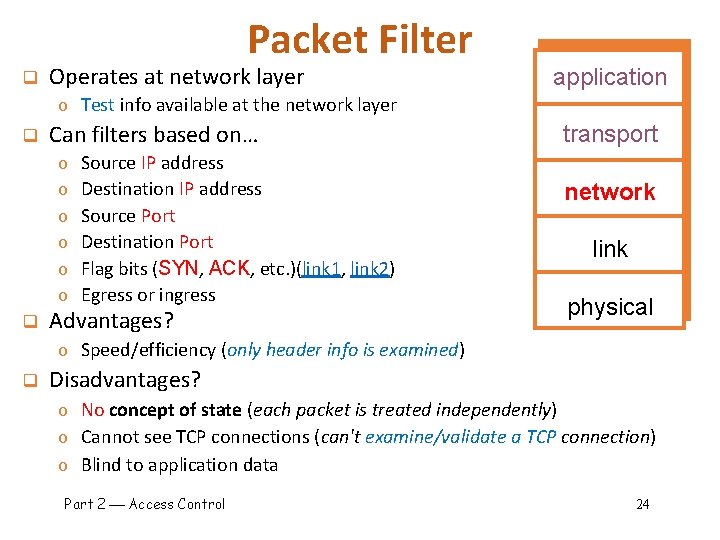
Packet Filter q Operates at network layer application o Test info available at the network layer q Can filters based on… o o o q Source IP address Destination IP address Source Port Destination Port Flag bits (SYN, ACK, etc. )(link 1, link 2) Egress or ingress Advantages? transport network link physical o Speed/efficiency (only header info is examined) q Disadvantages? o No concept of state (each packet is treated independently) o Cannot see TCP connections (can't examine/validate a TCP connection) o Blind to application data Part 2 Access Control 24

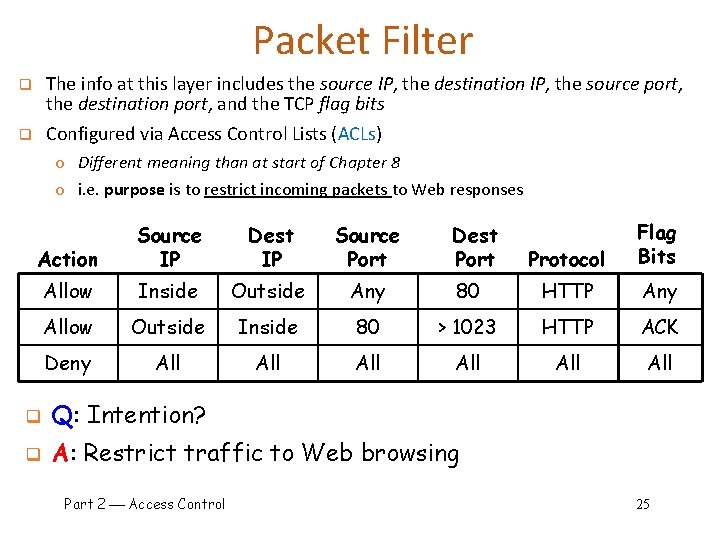
Packet Filter The info at this layer includes the source IP, the destination IP, the source port, the destination port, and the TCP flag bits Configured via Access Control Lists (ACLs) q q o Different meaning than at start of Chapter 8 o i. e. purpose is to restrict incoming packets to Web responses Protocol Flag Bits 80 HTTP Any 80 > 1023 HTTP ACK All All Action Source IP Dest IP Source Port Allow Inside Outside Any Allow Outside Inside Deny All Dest Port q Q: Intention? q A: Restrict traffic to Web browsing Part 2 Access Control 25

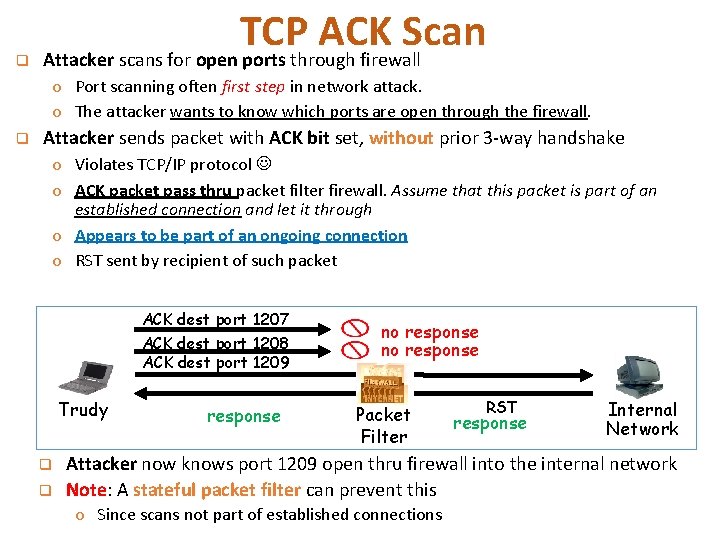
q TCP ACK Scan Attacker scans for open ports through firewall o Port scanning often first step in network attack. o The attacker wants to know which ports are open through the firewall. q Attacker sends packet with ACK bit set, without prior 3 -way handshake o Violates TCP/IP protocol o ACK packet pass thru packet filter firewall. Assume that this packet is part of an established connection and let it through o Appears to be part of an ongoing connection o RST sent by recipient of such packet ACK dest port 1207 ACK dest port 1208 ACK dest port 1209 Trudy q q response no response Packet Filter RST response Internal Network Attacker now knows port 1209 open thru firewall into the internal network Note: A stateful packet filter can prevent this o Since scans not part of established connections

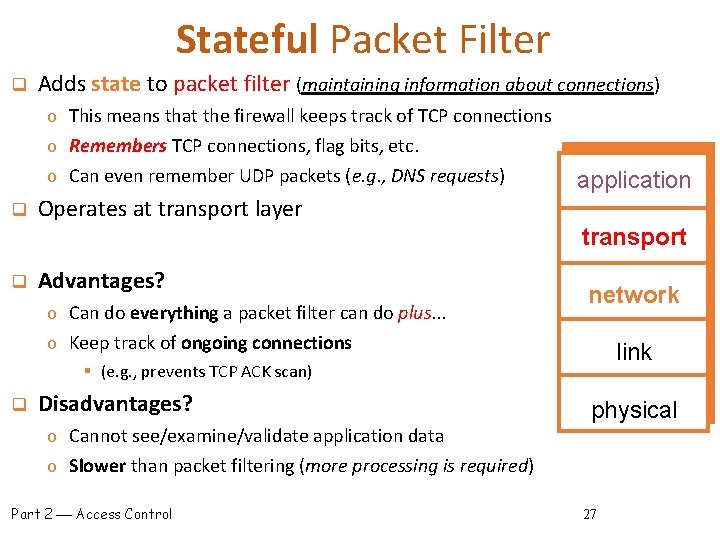
Stateful Packet Filter q Adds state to packet filter (maintaining information about connections) o This means that the firewall keeps track of TCP connections o Remembers TCP connections, flag bits, etc. o Can even remember UDP packets (e. g. , DNS requests) q application Operates at transport layer transport q Advantages? o Can do everything a packet filter can do plus. . . network o Keep track of ongoing connections link § (e. g. , prevents TCP ACK scan) q Disadvantages? o Cannot see/examine/validate application data physical o Slower than packet filtering (more processing is required) Part 2 Access Control 27

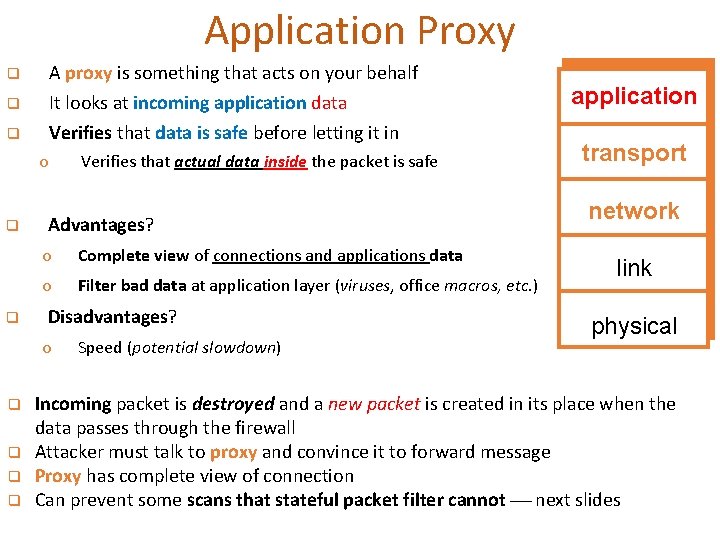
Application Proxy q A proxy is something that acts on your behalf q It looks at incoming application data Verifies that data is safe before letting it in q o q q Advantages? o Complete view of connections and applications data o Filter bad data at application layer (viruses, office macros, etc. ) Disadvantages? o q q Verifies that actual data inside the packet is safe Speed (potential slowdown) application transport network link physical Incoming packet is destroyed and a new packet is created in its place when the data passes through the firewall Attacker must talk to proxy and convince it to forward message Proxy has complete view of connection Can prevent some scans that stateful packet filter cannot next slides

q Firewalk For an information security attack, an attacker follow certain steps/phases o (1): information gathering, to gain enough information about the target systems to enable an actual attack. o (2): launch the actual exploitation of a target system. o (3): hiding the traces of the initial exploit and then installing tools to allow continued access as well as gathering more information for expanding the attack. q Firewalk is designed to scan for open ports through a firewall, (scanning tools) q If the attacker knows: o IP address of firewall and o IP address of one system inside firewall q Then, create a packet and set its time to live (TTL) to 1 more than number of hops to firewall, and set destination port to N q If firewall allows data on port N thru firewall, get time exceeded error message o When a packet is terminated due to the TTL field, an ICMP "time exceeded" error message is sent back to the source, it is from the first router inside the firewall that receives the attacker’s packet. o Otherwise, no response

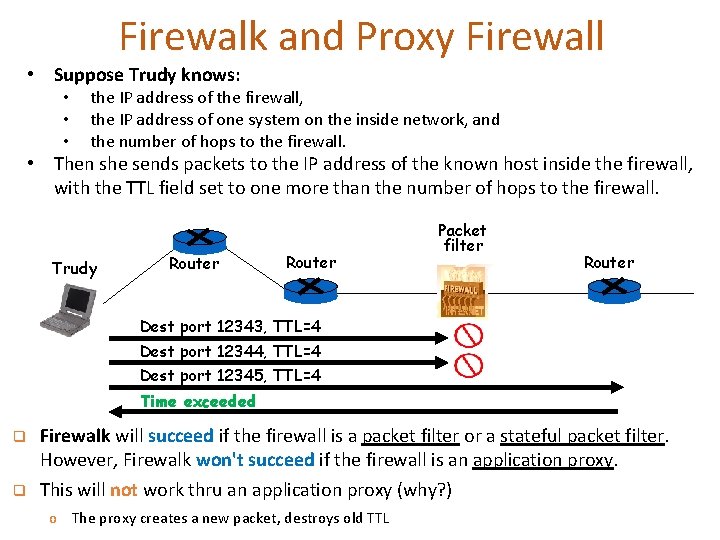
Firewalk and Proxy Firewall • Suppose Trudy knows: • • • the IP address of the firewall, the IP address of one system on the inside network, and the number of hops to the firewall. • Then she sends packets to the IP address of the known host inside the firewall, with the TTL field set to one more than the number of hops to the firewall. Trudy Router Packet filter Router Dest port 12343, TTL=4 Dest port 12344, TTL=4 Dest port 12345, TTL=4 Time exceeded q q Firewalk will succeed if the firewall is a packet filter or a stateful packet filter. However, Firewalk won't succeed if the firewall is an application proxy. This will not work thru an application proxy (why? ) o The proxy creates a new packet, destroys old TTL

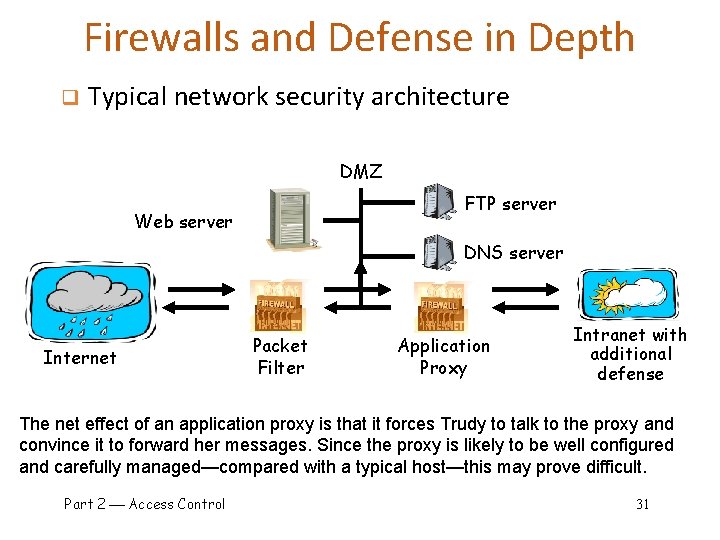
Firewalls and Defense in Depth q Typical network security architecture DMZ FTP server Web server DNS server Internet Packet Filter Application Proxy Intranet with additional defense The net effect of an application proxy is that it forces Trudy to talk to the proxy and convince it to forward her messages. Since the proxy is likely to be well configured and carefully managed—compared with a typical host—this may prove difficult. Part 2 Access Control 31

Intrusion Detection Systems (IDS) Part 2 Access Control 32

Intrusion Detection Systems (IDS) The primary focus of computer security tends to be intrusion prevention, where the goal is to keep the Trudys of the world out of your system or network. For examples: • • • Authentication can be viewed as a means to prevent intrusions, Firewalls are certainly a form of intrusion prevention, most types of virus protection (anti-viruses ) are to prevent intrusions. Occasionally, bad guys will be successful and an intrusion will occur. The purpose of IDS is to detect attacks: • before, • during, and • after they occur.

Intrusion Prevention q q Want to keep bad guys out Intrusion prevention is a traditional focus of computer security o o q q Authentication is to prevent intrusions Firewalls a form of intrusion prevention Virus defenses aimed at intrusion prevention Like locking the door on your car In spite of intrusion prevention, bad guys will sometime get in Intrusion Detection Systems (IDS) o Detect attacks in progress (or soon after) o Look for unusual or suspicious activity q q IDS evolved from log file analysis, currently a hot research topic How to respond when an intrusion is detected? o For example, we might detect a password guessing attack aimed at a specific account, in which case we could respond by locking the account. ? ! o However, often determining the proper response is not easy

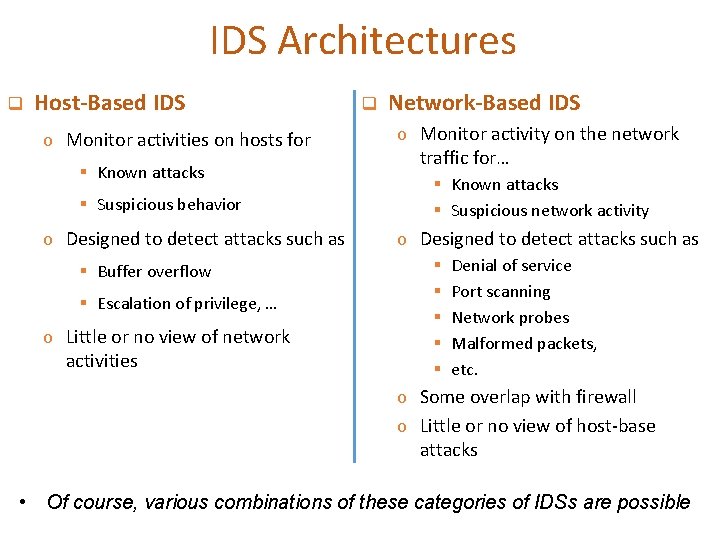
Intrusion Detection Systems q Who is likely an intruder? q o May be outsider who got thru the firewall o May be evil insider q What do intruders do? o Signature-based IDS o Anomaly-based IDS q o Use the breached system “Borrow resources” to launch an attacks on other systems o Use compromised system to attack others. o etc. Intrusion detection architectures o Host-based IDS o Launch well-known attacks, or variations on well-known attacks o Launch new/little-known attacks Intrusion detection approaches o Network-based IDS q Any IDS can be classified as above o In spite of marketing claims to the contrary!

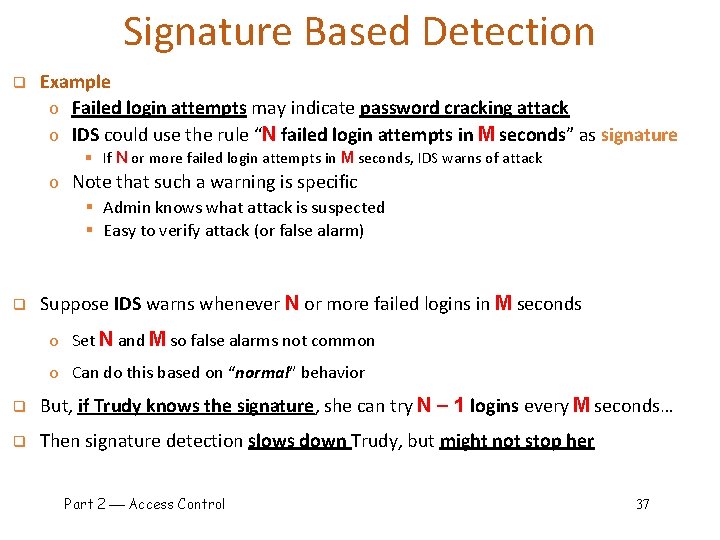
IDS Architectures q Host-Based IDS o Monitor activities on hosts for § Known attacks § Suspicious behavior o Designed to detect attacks such as § Buffer overflow § Escalation of privilege, … o Little or no view of network activities q Network-Based IDS o Monitor activity on the network traffic for… § Known attacks § Suspicious network activity o Designed to detect attacks such as § § § Denial of service Port scanning Network probes Malformed packets, etc. o Some overlap with firewall o Little or no view of host-base attacks • Of course, various combinations of these categories of IDSs are possible

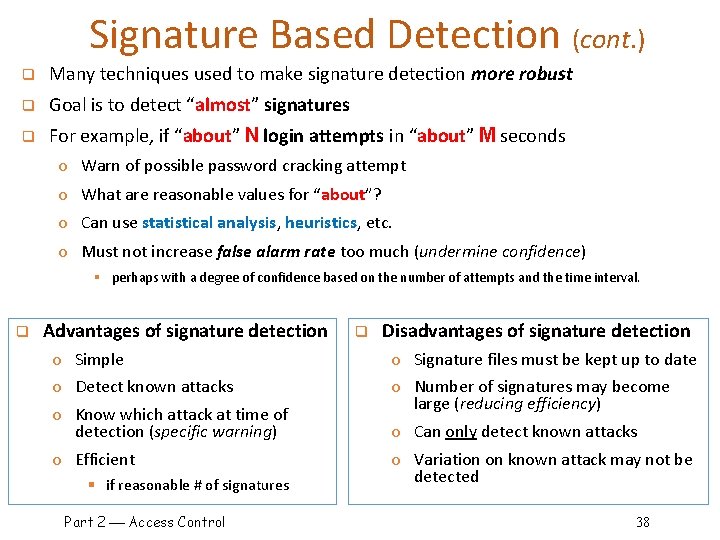
Signature Based Detection q Example o Failed login attempts may indicate password cracking attack o IDS could use the rule “N failed login attempts in M seconds” as signature § If N or more failed login attempts in M seconds, IDS warns of attack o Note that such a warning is specific § Admin knows what attack is suspected § Easy to verify attack (or false alarm) q Suppose IDS warns whenever N or more failed logins in M seconds o Set N and M so false alarms not common o Can do this based on “normal” behavior q But, if Trudy knows the signature, she can try N 1 logins every M seconds… q Then signature detection slows down Trudy, but might not stop her Part 2 Access Control 37

Signature Based Detection (cont. ) q Many techniques used to make signature detection more robust q Goal is to detect “almost” signatures q For example, if “about” N login attempts in “about” M seconds o Warn of possible password cracking attempt o What are reasonable values for “about”? o Can use statistical analysis, heuristics, etc. o Must not increase false alarm rate too much (undermine confidence) § perhaps with a degree of confidence based on the number of attempts and the time interval. q Advantages of signature detection q Disadvantages of signature detection o Simple o Signature files must be kept up to date o Detect known attacks o Number of signatures may become large (reducing efficiency) o Know which attack at time of detection (specific warning) o Efficient § if reasonable # of signatures Part 2 Access Control o Can only detect known attacks o Variation on known attack may not be detected 38

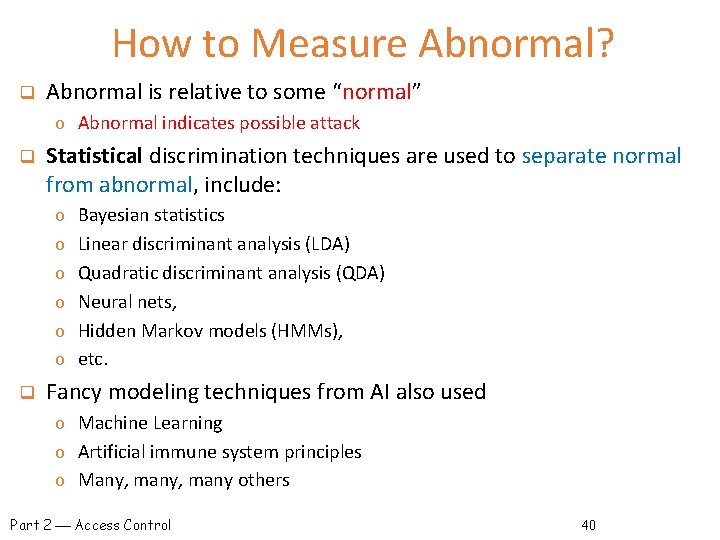
Anomaly Based Detection q Anomaly detection systems look for unusual or abnormal behavior (challenging) q There are (at least) two challenges o What is normal for this system? o How “far” from normal is abnormal? q No avoiding statistics here! (difficult statistical thresholding issues) o mean defines normal o variance gives distance from normal to abnormal q How to measure normal? o Must measure during times of “representative” behavior o Must not measure during an attack … or else attack will seem normal! o i. e. abnormal must be measured relative to some specific value of normal o Normal is statistical mean o Must also compute variance to have any reasonable idea of abnormal Part 2 Access Control 39

How to Measure Abnormal? q Abnormal is relative to some “normal” o Abnormal indicates possible attack q Statistical discrimination techniques are used to separate normal from abnormal, include: o o o q Bayesian statistics Linear discriminant analysis (LDA) Quadratic discriminant analysis (QDA) Neural nets, Hidden Markov models (HMMs), etc. Fancy modeling techniques from AI also used o Machine Learning o Artificial immune system principles o Many, many others Part 2 Access Control 40

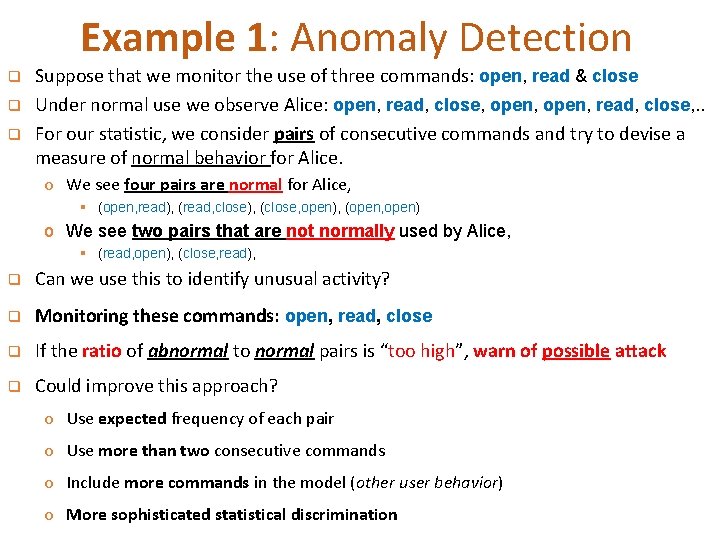
Example 1: Anomaly Detection q q q Suppose that we monitor the use of three commands: open, read & close Under normal use we observe Alice: open, read, close, . . For our statistic, we consider pairs of consecutive commands and try to devise a measure of normal behavior for Alice. o We see four pairs are normal for Alice, § (open, read), (read, close), (close, open), (open, open) o We see two pairs that are not normally used by Alice, § (read, open), (close, read), q Can we use this to identify unusual activity? q Monitoring these commands: open, read, close q If the ratio of abnormal to normal pairs is “too high”, warn of possible attack q Could improve this approach? o Use expected frequency of each pair o Use more than two consecutive commands o Include more commands in the model (other user behavior) o More sophisticated statistical discrimination

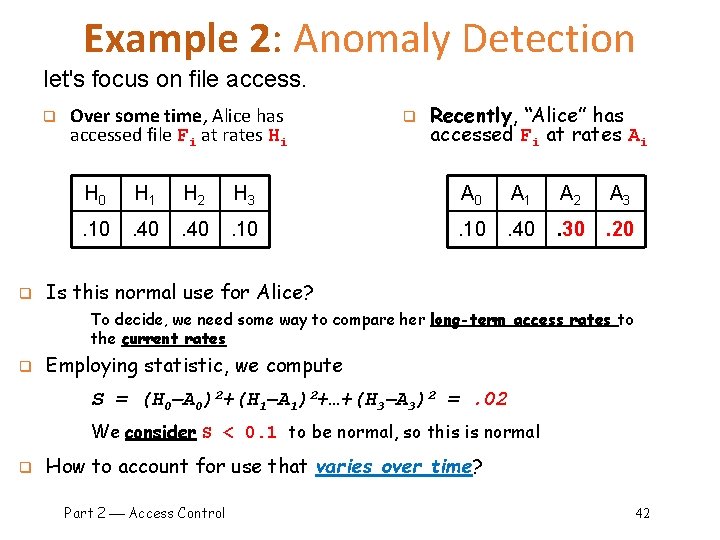
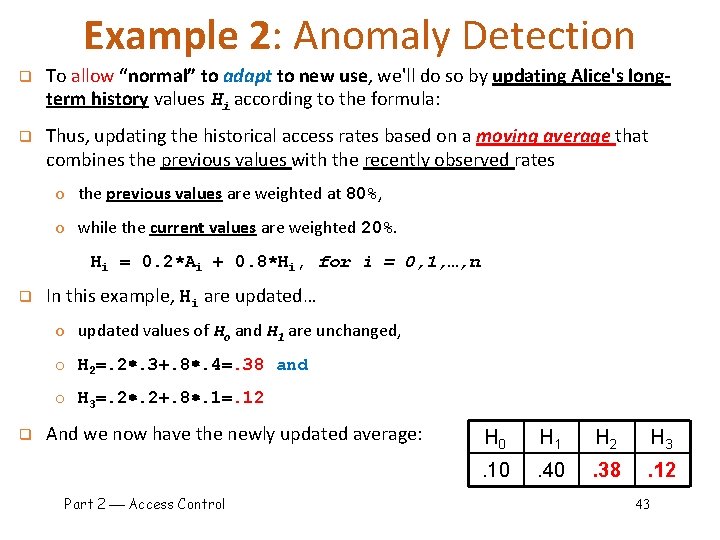
Example 2: Anomaly Detection let's focus on file access. q q Over some time, Alice has accessed file Fi at rates Hi q Recently, “Alice” has accessed Fi at rates Ai H 0 H 1 H 2 H 3 A 0 A 1 A 2 A 3 . 10 . 40 . 30 . 20 Is this normal use for Alice? To decide, we need some way to compare her long-term access rates to the current rates q Employing statistic, we compute S = (H 0 A 0)2+(H 1 A 1)2+…+(H 3 A 3)2 =. 02 We consider S < 0. 1 to be normal, so this is normal q How to account for use that varies over time? Part 2 Access Control 42

Example 2: Anomaly Detection q To allow “normal” to adapt to new use, we'll do so by updating Alice's longterm history values Hi according to the formula: q Thus, updating the historical access rates based on a moving average that combines the previous values with the recently observed rates o the previous values are weighted at 80%, o while the current values are weighted 20%. Hi = 0. 2*Ai + 0. 8*Hi, for i = 0, 1, …, n q In this example, Hi are updated… o updated values of Ho and H 1 are unchanged, o H 2=. 2. 3+. 8. 4=. 38 and o H 3=. 2. 2+. 8. 1=. 12 q And we now have the newly updated average: Part 2 Access Control H 0 H 1 H 2 H 3 . 10 . 40 . 38 . 12 43

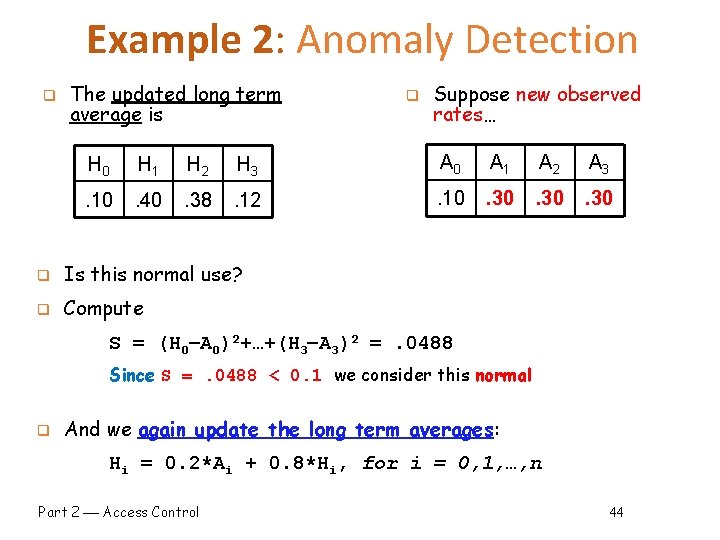
Example 2: Anomaly Detection q The updated long term average is q Suppose new observed rates… H 0 H 1 H 2 H 3 A 0 A 1 A 2 A 3 . 10 . 40 . 38 . 12 . 10 . 30 q Is this normal use? q Compute S = (H 0 A 0)2+…+(H 3 A 3)2 =. 0488 Since S =. 0488 < 0. 1 we consider this normal q And we again update the long term averages: Hi = 0. 2*Ai + 0. 8*Hi, for i = 0, 1, …, n Part 2 Access Control 44

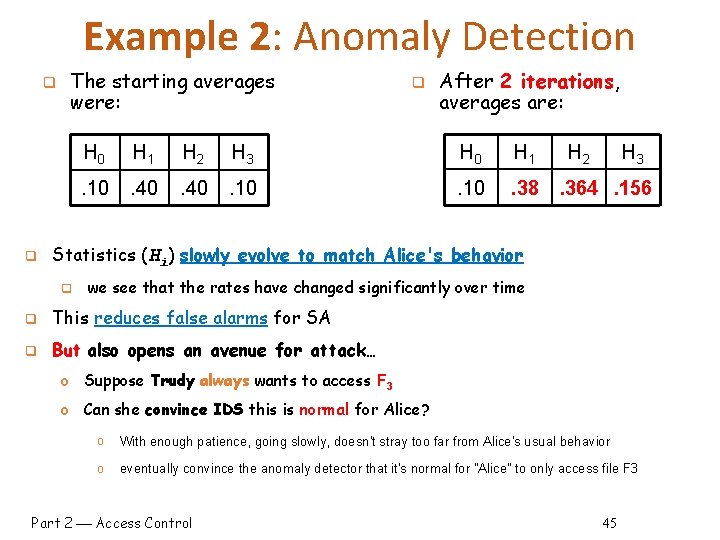
Example 2: Anomaly Detection q q The starting averages were: q After 2 iterations, averages are: H 0 H 1 H 2 H 3 H 0 H 1 . 10 . 40 . 10 . 38 H 2 H 3 . 364. 156 Statistics (Hi) slowly evolve to match Alice's behavior q we see that the rates have changed significantly over time q This reduces false alarms for SA q But also opens an avenue for attack… o Suppose Trudy always wants to access F 3 o Can she convince IDS this is normal for Alice? o With enough patience, going slowly, doesn't stray too far from Alice's usual behavior o eventually convince the anomaly detector that it's normal for "Alice" to only access file F 3 Part 2 Access Control 45

Anomaly Detection (2) q To make this approach more robust, o Certainly need to measure more than one statistic o If we measured N different statistics, S 1, S 2, …, SN o i. e. must incorporate the variance q Can also combine N stats Si as, say, T = (S 1 + S 2 + S 3 + … + SN) / N o to obtain a more complete/comprehensive view of “normal” o make the determination of normal or abnormal based on T q Example: similar (but more sophisticated) approach is used in an IDS known as NIDES o NIDES combines anomaly & signature IDS Part 2 Access Control 46

q Advantages? Anomaly Detection o Chance of detecting unknown attacks o Anomaly detection more efficient than signature detection, if signature file is large q Disadvantages? o Cannot use anomaly detection alone…must be used with signature detection o Reliability is unclear o May be subject to attack o Anomaly detection indicates “something unusual”, but lacks specific info on attack q Anomaly Detection: The Bottom Line o o Anomaly-based IDS is active research topic Many security experts have high hopes for its ultimate success Often cited as key future security technology Hackers are not convinced! § Title of a talk at Defcon: “Why Anomaly-based IDS is an Attacker’s Best Friend” o Anomaly detection is difficult and tricky o As hard as AI?

Summary: Anomaly Detection Issues q Systems constantly evolve and so must IDS o Static system would place huge burden on admin o But evolving IDS makes it possible for attacker to (slowly) convince IDS that an attack is normal o Attacker may win simply by “going slow” q What does “abnormal” really mean? o Indicates there may be an attack o Might not be any specific info about “attack” o How to respond to such vague information? o In contrast, signature detection is very specific Part 2 Access Control 48

Summary: Access Control q Authentication and authorization o Authentication who goes there? § Passwords something you know § Biometrics something you are (you are your key) § Something you have q Coming Attractions… o Security protocols § Generic authentication protocols § SSH, SSL, IPSec, Kerberos, WEP, GSM o We’ll see lots of crypto applications in the protocol chapters Part 2 Access Control 49