Panorama Capturing Systemwide Information Flow for Malware Detection









- Slides: 19

Panorama: Capturing System-wide Information Flow for Malware Detection and Analysis Authors: Heng Yin, Dawn Song, Manuel Egele, Christoper Kruegel, and Engin Kirda Publication: Presenter: ACM Conference on Computer and Communications Security, 2007 Brad Mundt for CAP 6133 Spring ‘ 08

Motivation n Malicious software sneaks onto computers ¨ Collects users’ private information ¨ Causes havoc on Internet n n Slows performance Costs to remove ¨ Reputable n n vendors violate users’ privacy Google Desktop Sony Media Player

Traditional Malware detection n Signature-based ¨ Cannot n detect new malware or variants Heuristics ¨ High false positives ¨ High false negatives

The Panorama way n Input ¨ Suspicious behavior n n Process ¨ Whole-system, fine-grained taint tracking n ¨ Marking data Operating-system-aware taint analysis n n Inappropriate data access, stealthfully What touches the tainted data and how Output ¨ Taint Graphs n Tracked tainted data

Taint Graph n Information flow that shows the process that accessed the tainted data n Make policies based on Taint Graph n Compare unknown samples against Taint Graph ¨ Automatic ¨ Numerous categories

Taint Graph example

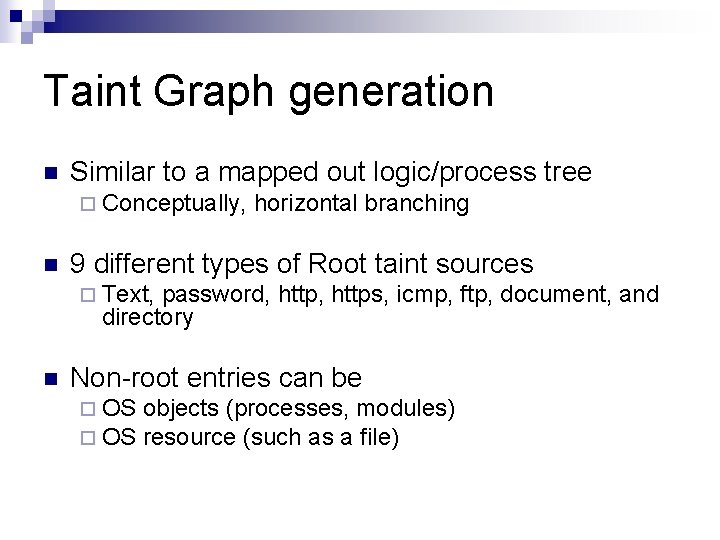
Taint Graph generation n Similar to a mapped out logic/process tree ¨ Conceptually, n horizontal branching 9 different types of Root taint sources ¨ Text, password, https, icmp, ftp, document, and directory n Non-root entries can be ¨ OS objects (processes, modules) resource (such as a file)

System Overview

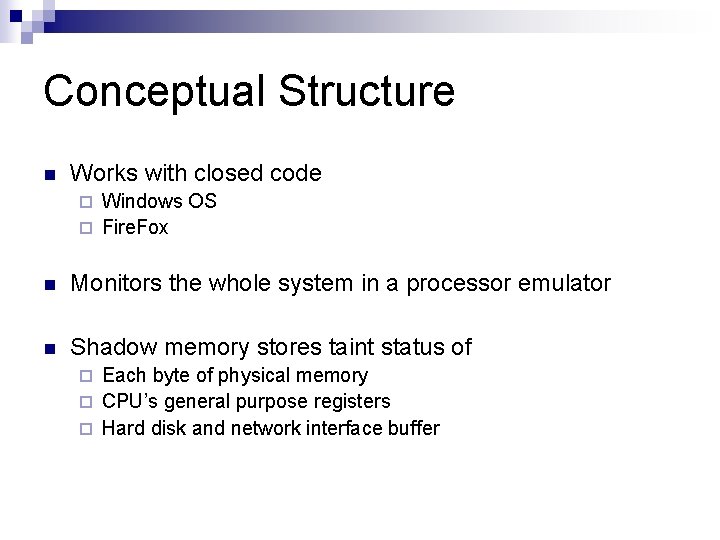
Conceptual Structure n Works with closed code Windows OS ¨ Fire. Fox ¨ n Monitors the whole system in a processor emulator n Shadow memory stores taint status of Each byte of physical memory ¨ CPU’s general purpose registers ¨ Hard disk and network interface buffer ¨

Taint Sources n Test information is inputted and marked as taint source n Inputted from hardware such as Keyboard ¨ Network interface ¨ Hard disk ¨ n Tainting at hardware level ¨ Malware could hook before input reaches the software

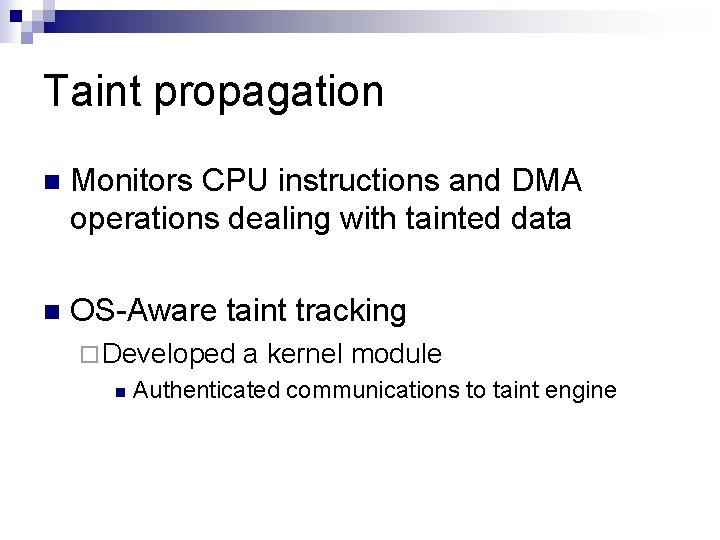
Taint propagation n Monitors CPU instructions and DMA operations dealing with tainted data n OS-Aware taint tracking ¨ Developed n a kernel module Authenticated communications to taint engine

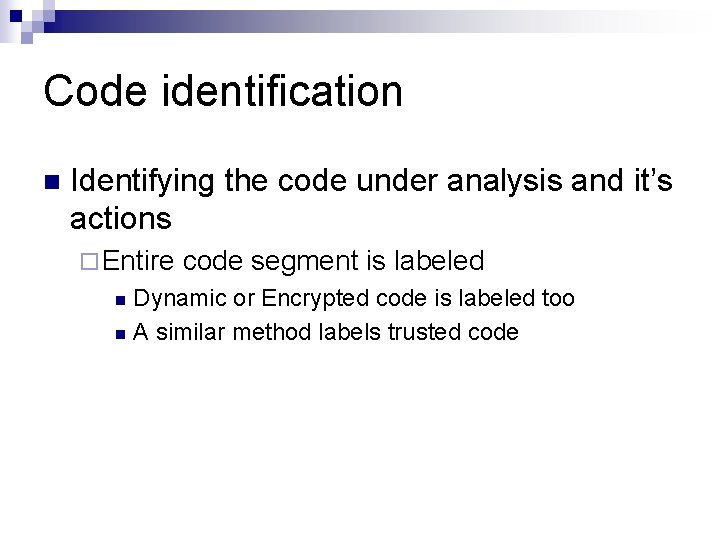
Code identification n Identifying the code under analysis and it’s actions ¨ Entire code segment is labeled Dynamic or Encrypted code is labeled too n A similar method labels trusted code n

Three categorized behaviors n Anomalous information access ¨ MS n Paint accessing passwords Anomalous information leakage ¨ BHO n reporting home about surfed websites Excessive information access ¨ Repeatedly accessed directory to hide rootkit

Malware detections 42 real-world malware samples n 56 benign applications were tested n Only 3 false positives, no false negatives n ¨ 2 from a personal firewall ¨ 1 from a browser accelerator

Summary n A new system to detect malware ¨ System-Wide n Taint tracking ¨ ¨ Taint n Information Flow Data access and process tracking graphs Policies

Contributions Unified approach to detect and analyze diverse malware n Designed and developed a functional prototype n Detected all malware samples n ¨ Keystroke loggers, password sniffers, packet sniffers, stealth backdoors, rootkits, and spyware

Weaknesses n Performance Overhead ¨ Using Cygwin utilities ¨ Prototype is not optimized ¨ Slowdown average is 20 times ¨ Intended as a offline tool n Evasive malware ¨ Time bombs ¨ Selective keystroke loggers ¨ Virtual environment detection

How to Improve n Optimize the code n Automate taint graph analysis and policy implementation n Virtual environment shielding ¨ n Or switch out of emulated environment Implementioned improvements ¨ Unicode conversion- switch case issue

The End Thank you…