Palo Alto Networks security solution protection against new














- Slides: 52

Palo Alto Networks security solution - protection against new cyber-criminal threats focused on client-side vulnerabilities Mariusz Stawowski, Ph. D. , CISSP Director of Professional Services, CLICO email: mstawow@clico. pl

AGENDA • Introduction • New client-side vulnerabilities used by cybercriminals • Next-Generation Firewall – en effective protection against attacks focused on end users • A live demo of Palo Alto Networks security solution unique features in practice • Summary ISO 9001: 2001

INTRODUCTION 90 ties • Hackers were showing to the World their knowledge and achievements Nowadays • Cyber-criminals’ activities are performed in an invisible way ISO 9001: 2001

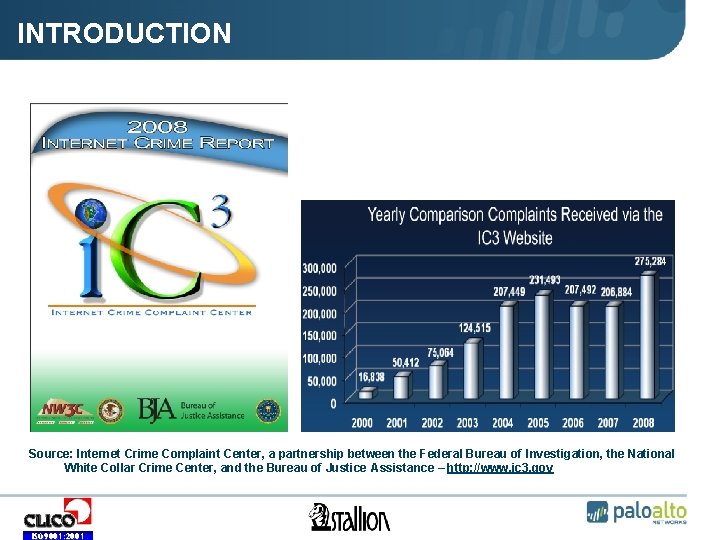
INTRODUCTION Source: Internet Crime Complaint Center, a partnership between the Federal Bureau of Investigation, the National White Collar Crime Center, and the Bureau of Justice Assistance – http: //www. ic 3. gov ISO 9001: 2001

INTRODUCTION SANS The Top Cyber Security Risks 2009 Executive Summary Priority One: Client-side software that remains unpatched. Priority Two: Internet-facing web sites that are vulnerable. … Source: SANS Institute - http: //www. sans. org/top-cyber-security-risks/ ISO 9001: 2001

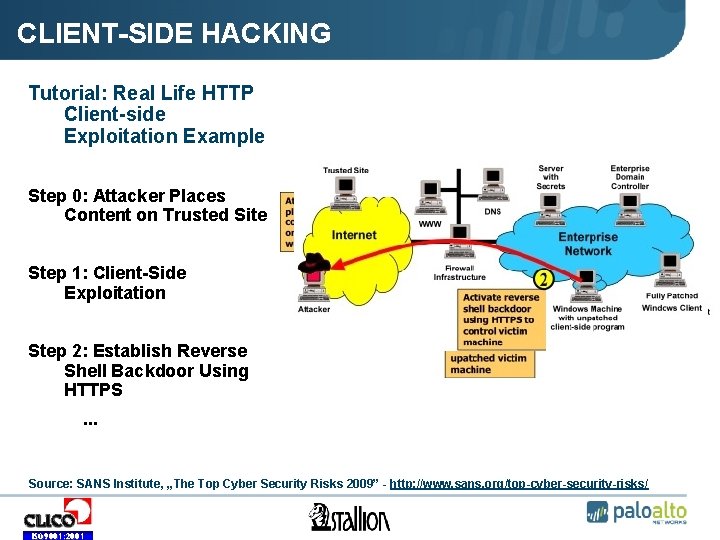
CLIENT-SIDE HACKING Tutorial: Real Life HTTP Client-side Exploitation Example Step 0: Attacker Places Content on Trusted Site Step 1: Client-Side Exploitation Step 2: Establish Reverse Shell Backdoor Using HTTPS. . . Source: SANS Institute, „The Top Cyber Security Risks 2009” - http: //www. sans. org/top-cyber-security-risks/ ISO 9001: 2001

CLIENT-SIDE HACKING Are we vulnerable? Every company can easily conduct the test to verify if their safeguards are able to protect IT systems against common client-side threats. ISO 9001: 2001

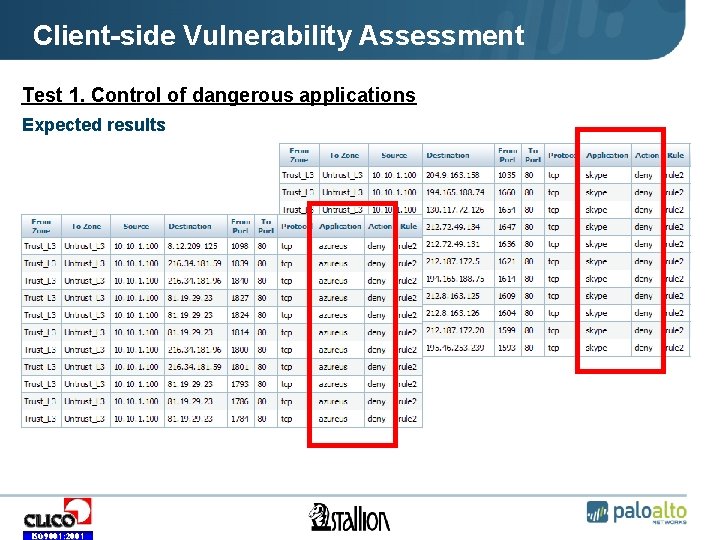
Client-side Vulnerability Assessment Test 1. Control of dangerous applications The test objective is to verify if the Company’s safeguards properly detect and block dangerous applications, i. e. : • P 2 P (file sharing), • Tor (free access to Internet services, publishing network services), • Web conferencing (desktop sharing). Security assessment should be conducted using real applications, i. e. Skype, smart P 2 P (e. g. Azureus) and Web session covered by Tor. ISO 9001: 2001

Client-side Vulnerability Assessment Test 1. Control of dangerous applications Expected results ISO 9001: 2001

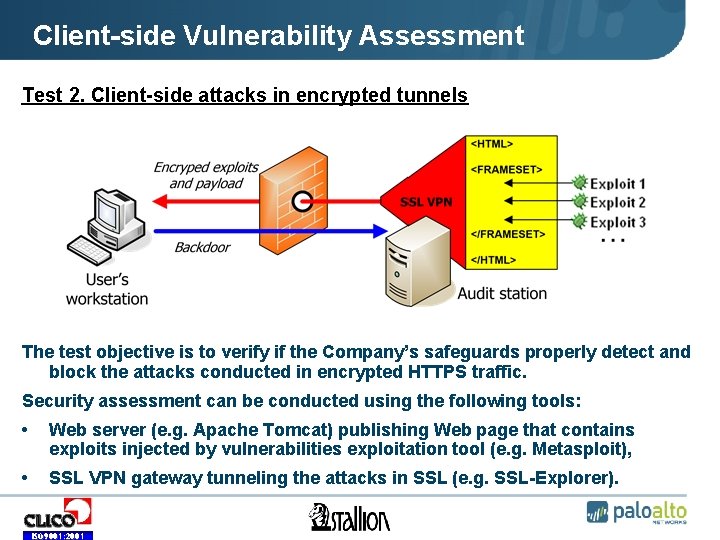
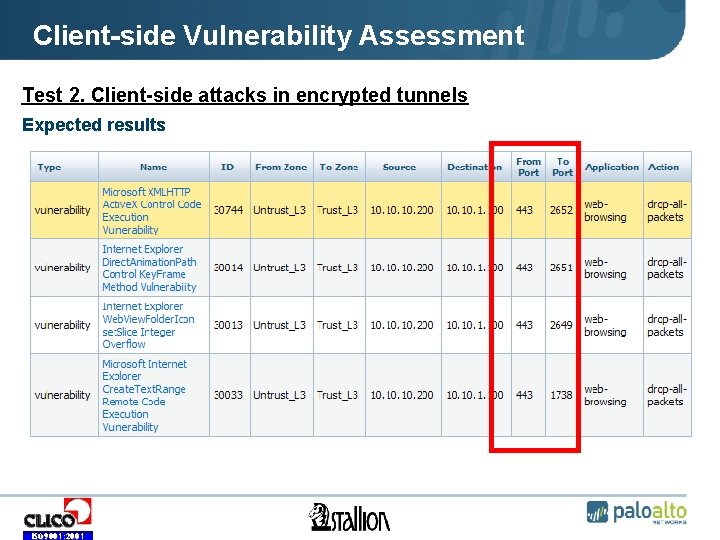
Client-side Vulnerability Assessment Test 2. Client-side attacks in encrypted tunnels The test objective is to verify if the Company’s safeguards properly detect and block the attacks conducted in encrypted HTTPS traffic. Security assessment can be conducted using the following tools: • Web server (e. g. Apache Tomcat) publishing Web page that contains exploits injected by vulnerabilities exploitation tool (e. g. Metasploit), • SSL VPN gateway tunneling the attacks in SSL (e. g. SSL-Explorer). ISO 9001: 2001

Client-side Vulnerability Assessment Test 2. Client-side attacks in encrypted tunnels Expected results ISO 9001: 2001

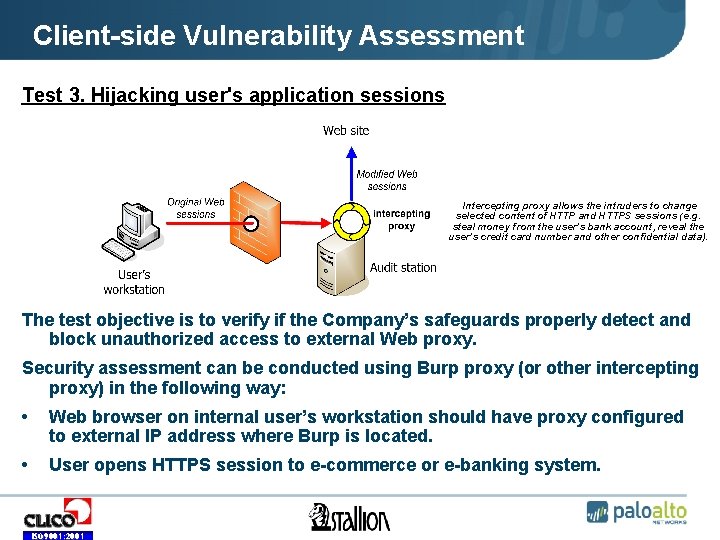
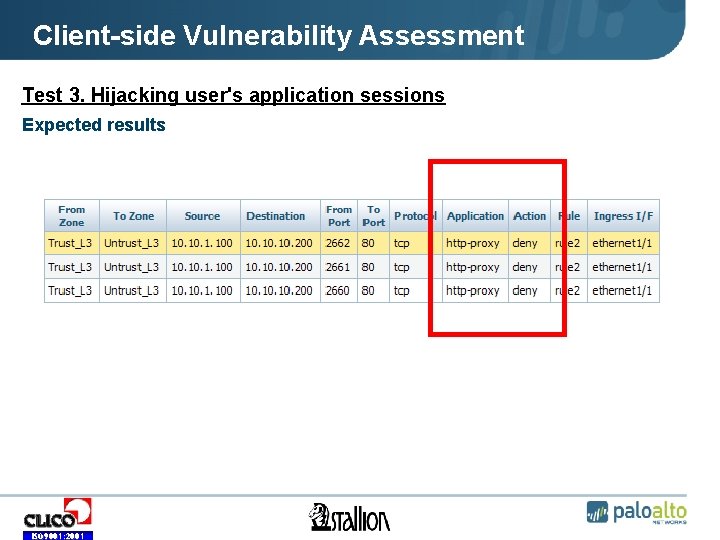
Client-side Vulnerability Assessment Test 3. Hijacking user's application sessions • Intercepting proxy allows the intruders to change selected content of HTTP and HTTPS sessions (e. g. steal money from the user’s bank account, reveal the user’s credit card number and other confidential data). The test objective is to verify if the Company’s safeguards properly detect and block unauthorized access to external Web proxy. Security assessment can be conducted using Burp proxy (or other intercepting proxy) in the following way: • Web browser on internal user’s workstation should have proxy configured to external IP address where Burp is located. • User opens HTTPS session to e-commerce or e-banking system. ISO 9001: 2001

Client-side Vulnerability Assessment Test 3. Hijacking user's application sessions Expected results ISO 9001: 2001

Client-side Vulnerability Assessment Detailed guidelines in ISSA Journal, November 2009 https: //issa. org/Members/Journals-Archive/2009. html#November ISO 9001: 2001

Next Generation Firewall ISO 9001: 2001

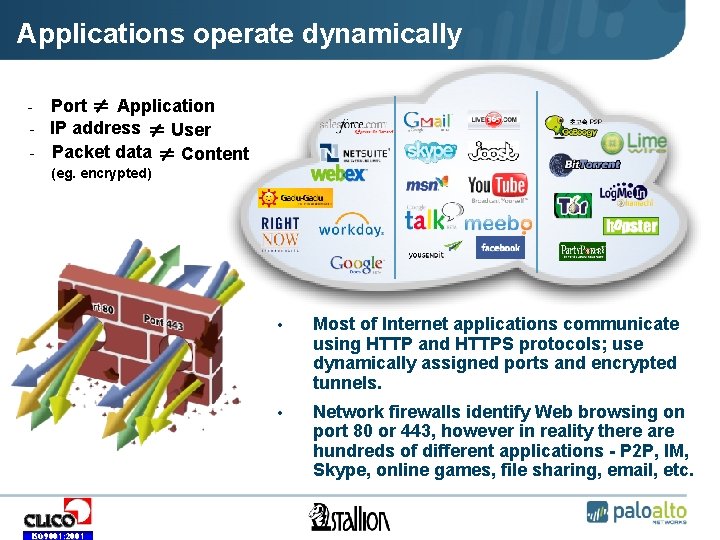
Applications operate dynamically • • • - • Port • ≠ • Application • IP address • ≠ • User • Packet data • ≠ • Content • (eg. encrypted) ISO 9001: 2001 • Most of Internet applications communicate using HTTP and HTTPS protocols; use dynamically assigned ports and encrypted tunnels. • Network firewalls identify Web browsing on port 80 or 443, however in reality there are hundreds of different applications - P 2 P, IM, Skype, online games, file sharing, email, etc.

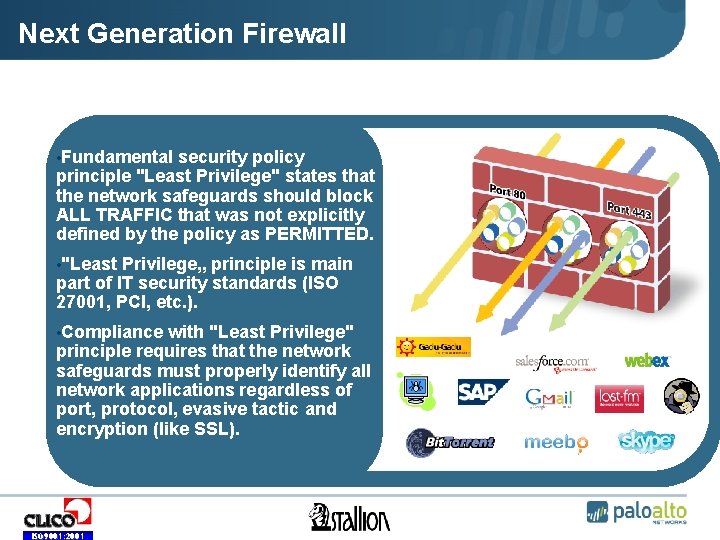
Next Generation Firewall • Fundamental security policy principle "Least Privilege" states that the network safeguards should block ALL TRAFFIC that was not explicitly defined by the policy as PERMITTED. • "Least Privilege„ principle is main part of IT security standards (ISO 27001, PCI, etc. ). • Compliance with "Least Privilege" principle requires that the network safeguards must properly identify all network applications regardless of port, protocol, evasive tactic and encryption (like SSL). ISO 9001: 2001

Next Generation Firewall ISO 9001: 2001

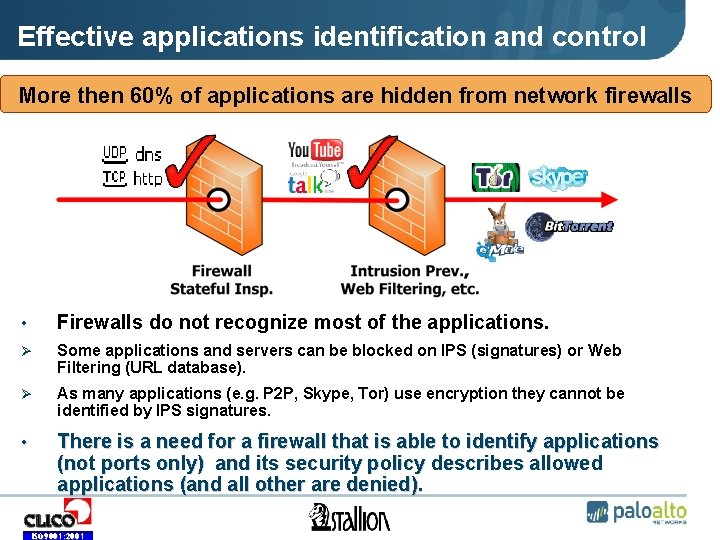
Effective applications identification and control More then 60% of applications are hidden from network firewalls • Firewalls do not recognize most of the applications. Ø Some applications and servers can be blocked on IPS (signatures) or Web Filtering (URL database). Ø As many applications (e. g. P 2 P, Skype, Tor) use encryption they cannot be identified by IPS signatures. • There is a need for a firewall that is able to identify applications (not ports only) and its security policy describes allowed applications (and all other are denied). ISO 9001: 2001

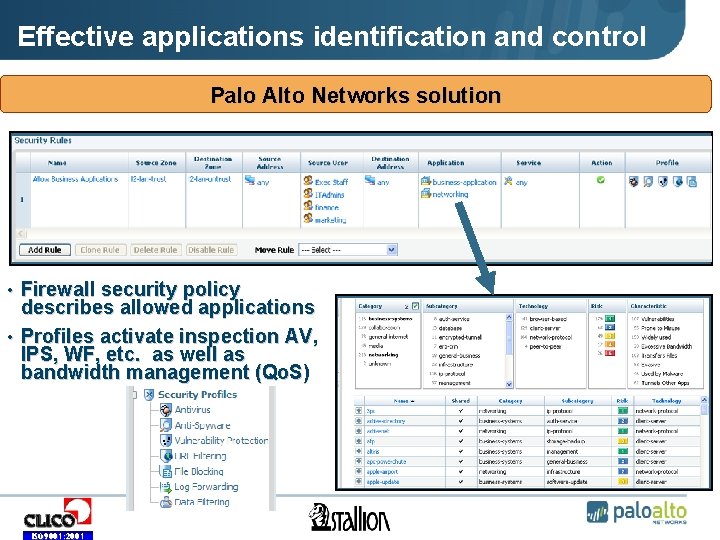
Effective applications identification and control Palo Alto Networks solution • Firewall security policy describes allowed applications • Profiles activate inspection AV, IPS, WF, etc. as well as bandwidth management (Qo. S) ISO 9001: 2001

Effective applications identification and control • Security Profiles identify malicious use of allowed applications. • Firewall protects against network attacks and malicious code as well as with multigigabit throughput detects and filters illegal data transferred by applications (e. g. credit card numbers, specified documents). üData Filtering - stops sensitive information (e. g. SSN, CC#) from traversing trusted boundaries. üData objects defined as regular expressions (regex). üFile Filtering - identification and filtering of specified files sent by applications. üIdentification based on MIME type and file header (not extension). ISO 9001: 2001

Effective users identification and control • Firewall policy accurately defines users’ access to the network services and it's enforced even when the users change location and IP address. • Firewall transparently verifies user’s identity (Active Directory, Citrix and TS integration). ISO 9001: 2001

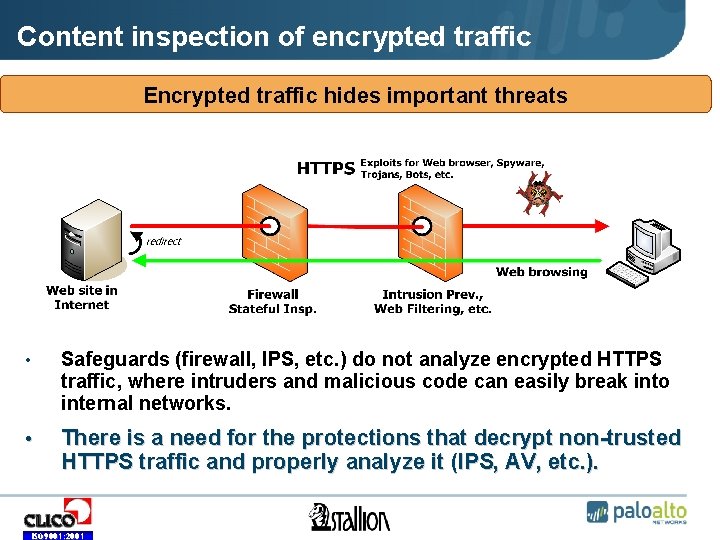
Content inspection of encrypted traffic Encrypted traffic hides important threats • Safeguards (firewall, IPS, etc. ) do not analyze encrypted HTTPS traffic, where intruders and malicious code can easily break into internal networks. • There is a need for the protections that decrypt non-trusted HTTPS traffic and properly analyze it (IPS, AV, etc. ). ISO 9001: 2001

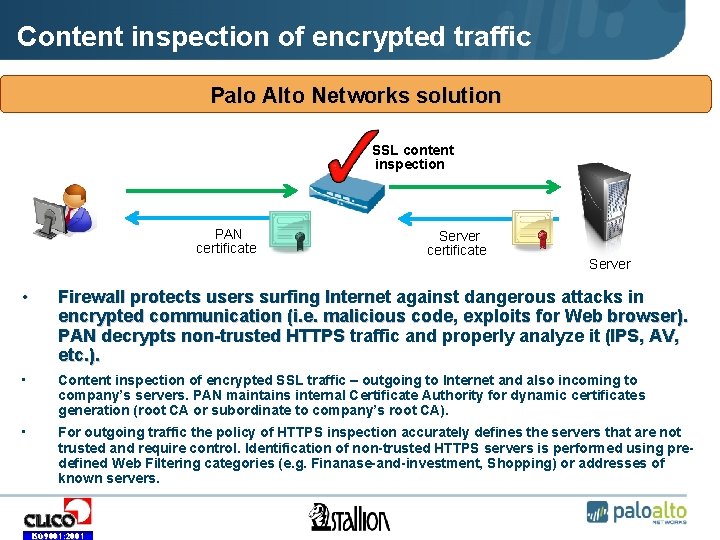
Content inspection of encrypted traffic Palo Alto Networks solution • SSL content inspection • PAN certificate • Server • Firewall protects users surfing Internet against dangerous attacks in encrypted communication (i. e. malicious code, exploits for Web browser). PAN decrypts non-trusted HTTPS traffic and properly analyze it (IPS, AV, etc. ). • Content inspection of encrypted SSL traffic – outgoing to Internet and also incoming to company’s servers. PAN maintains internal Certificate Authority for dynamic certificates generation (root CA or subordinate to company’s root CA). • For outgoing traffic the policy of HTTPS inspection accurately defines the servers that are not trusted and require control. Identification of non-trusted HTTPS servers is performed using predefined Web Filtering categories (e. g. Finanase-and-investment, Shopping) or addresses of known servers. ISO 9001: 2001

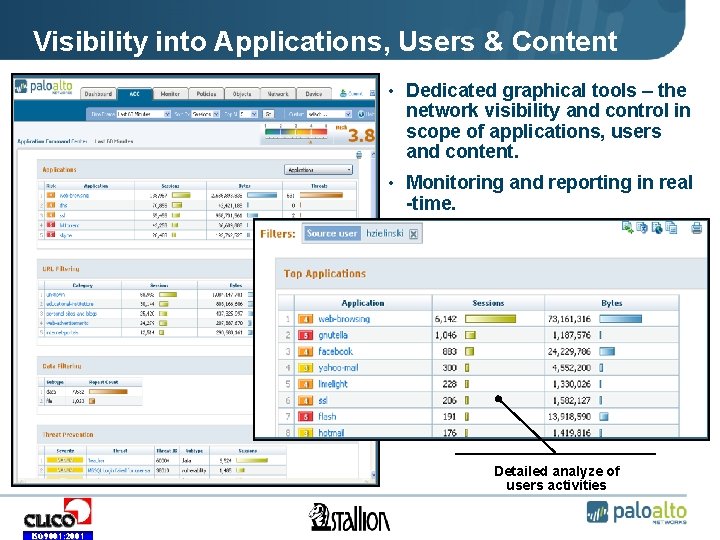
Visibility into Applications, Users & Content • Dedicated graphical tools – the network visibility and control in scope of applications, users and content. • Monitoring and reporting in real -time. Detailed analyze of users activities ISO 9001: 2001

NEXT GENERATION FIREWALL A live demo ISO 9001: 2001

Palo Alto Networks - technical features ISO 9001: 2001

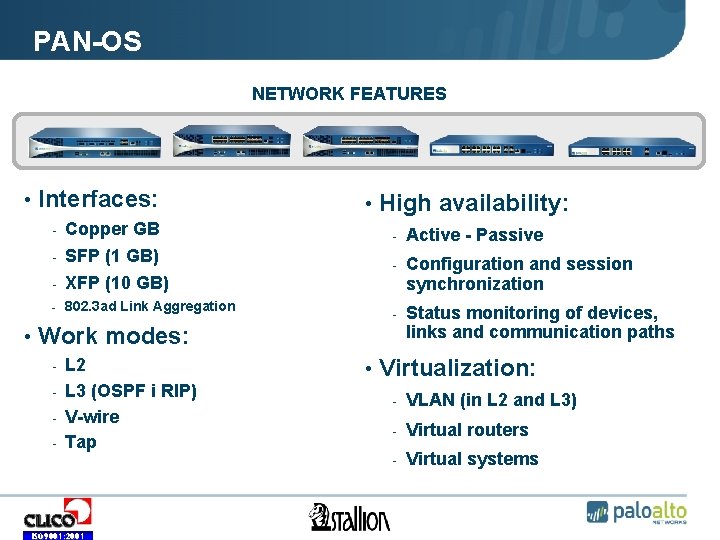
PAN-OS NETWORK FEATURES • Interfaces: - Copper GB - SFP (1 GB) - XFP (10 GB) - 802. 3 ad Link Aggregation • Work modes: L 2 - L 3 (OSPF i RIP) - V-wire - Tap - ISO 9001: 2001 • High availability: - Active - Passive - Configuration and session synchronization - Status monitoring of devices, links and communication paths • Virtualization: - VLAN (in L 2 and L 3) - Virtual routers - Virtual systems

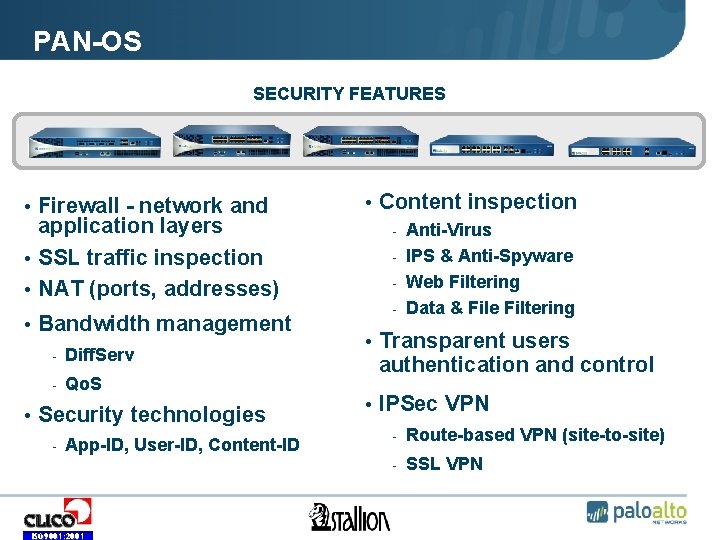
PAN-OS SECURITY FEATURES • Firewall - network and application layers • SSL traffic inspection • NAT (ports, addresses) • Bandwidth management - Diff. Serv - Qo. S • Security technologies - App-ID, User-ID, Content-ID ISO 9001: 2001 • Content inspection Anti-Virus - IPS & Anti-Spyware - Web Filtering - Data & File Filtering - • Transparent users authentication and control • IPSec VPN - Route-based VPN (site-to-site) - SSL VPN

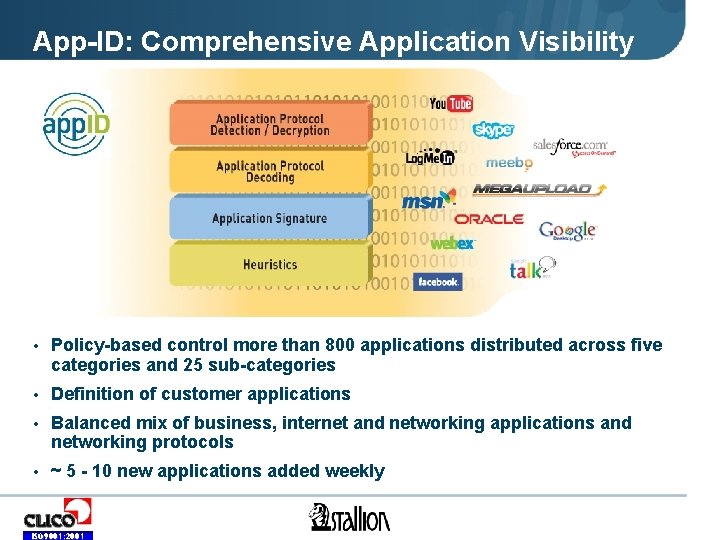
App-ID: Comprehensive Application Visibility • Policy-based control more than 800 applications distributed across five categories and 25 sub-categories • Definition of customer applications • Balanced mix of business, internet and networking applications and networking protocols • ~ 5 - 10 new applications added weekly ISO 9001: 2001

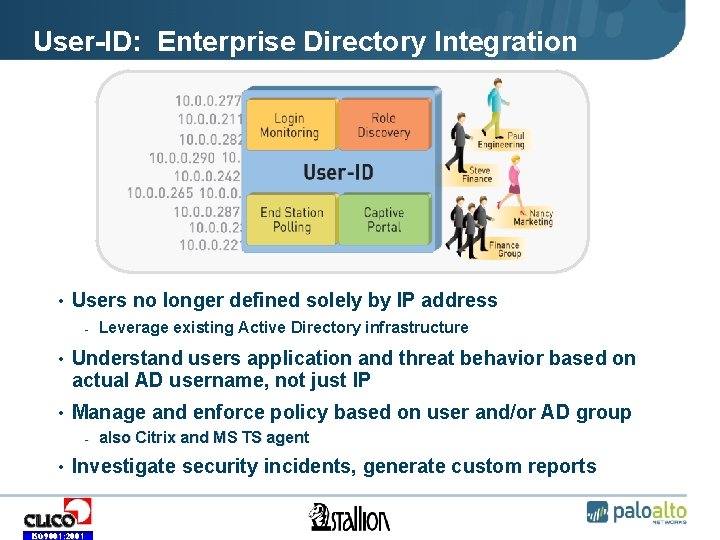
User-ID: Enterprise Directory Integration • Users no longer defined solely by IP address - Leverage existing Active Directory infrastructure • Understand users application and threat behavior based on actual AD username, not just IP • Manage and enforce policy based on user and/or AD group - also Citrix and MS TS agent • Investigate security incidents, generate custom reports ISO 9001: 2001

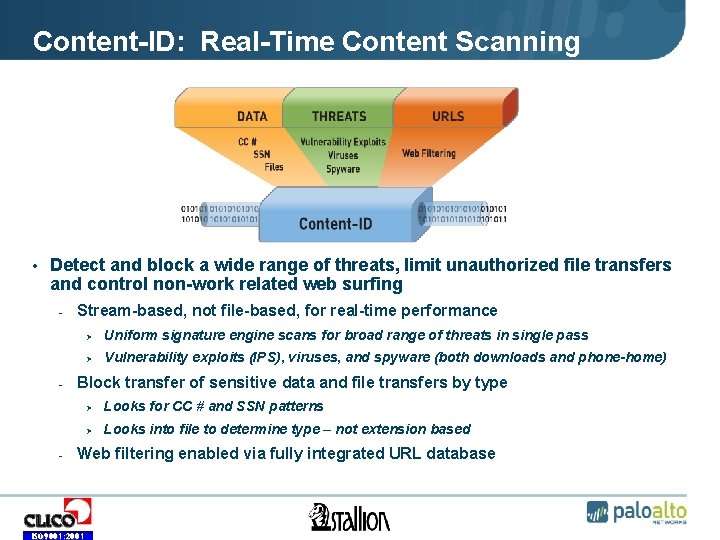
Content-ID: Real-Time Content Scanning • Detect and block a wide range of threats, limit unauthorized file transfers and control non-work related web surfing - - - Stream-based, not file-based, for real-time performance Ø Uniform signature engine scans for broad range of threats in single pass Ø Vulnerability exploits (IPS), viruses, and spyware (both downloads and phone-home) Block transfer of sensitive data and file transfers by type Ø Looks for CC # and SSN patterns Ø Looks into file to determine type – not extension based Web filtering enabled via fully integrated URL database ISO 9001: 2001

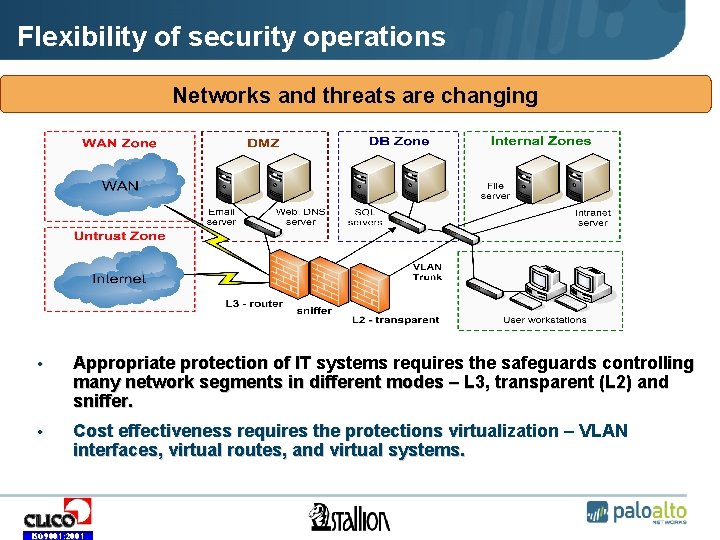
Flexibility of security operations Networks and threats are changing • Appropriate protection of IT systems requires the safeguards controlling many network segments in different modes – L 3, transparent (L 2) and sniffer. • Cost effectiveness requires the protections virtualization – VLAN interfaces, virtual routes, and virtual systems. ISO 9001: 2001

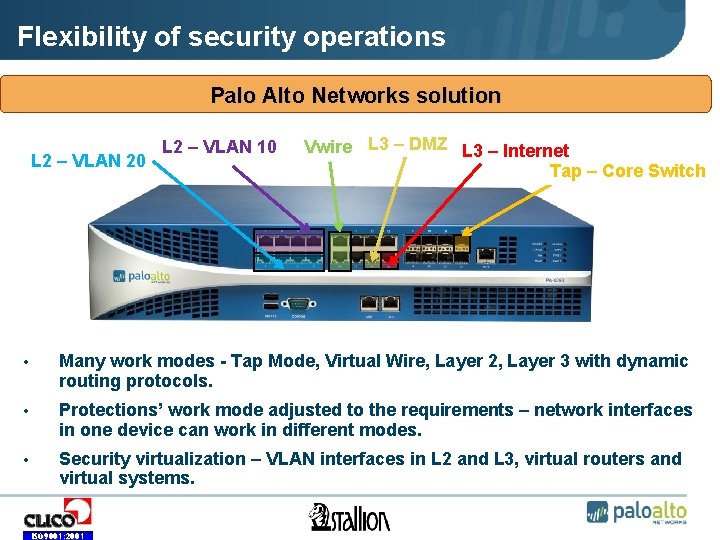
Flexibility of security operations Palo Alto Networks solution • L 2 – VLAN 20 • L 2 – VLAN 10 • Vwire • L 3 – DMZ • L 3 – Internet • Tap – Core Switch • Many work modes - Tap Mode, Virtual Wire, Layer 2, Layer 3 with dynamic routing protocols. • Protections’ work mode adjusted to the requirements – network interfaces in one device can work in different modes. • Security virtualization – VLAN interfaces in L 2 and L 3, virtual routers and virtual systems. ISO 9001: 2001

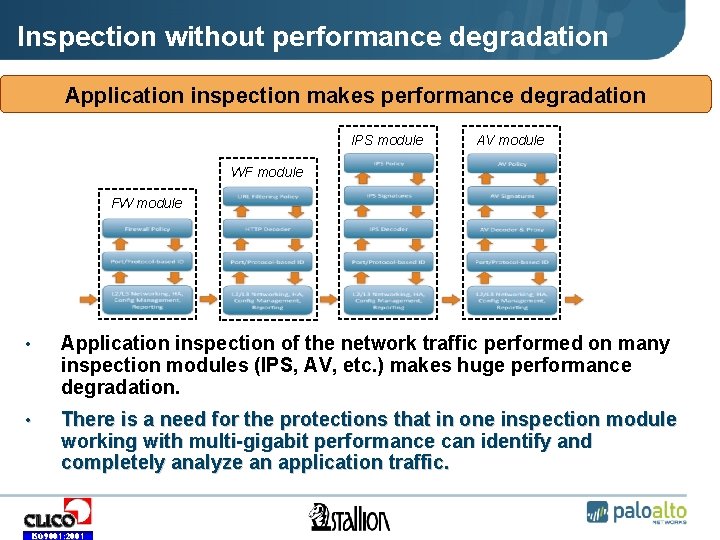
Inspection without performance degradation Application inspection makes performance degradation • IPS module • AV module • WF module • FW module • Application inspection of the network traffic performed on many inspection modules (IPS, AV, etc. ) makes huge performance degradation. • There is a need for the protections that in one inspection module working with multi-gigabit performance can identify and completely analyze an application traffic. ISO 9001: 2001

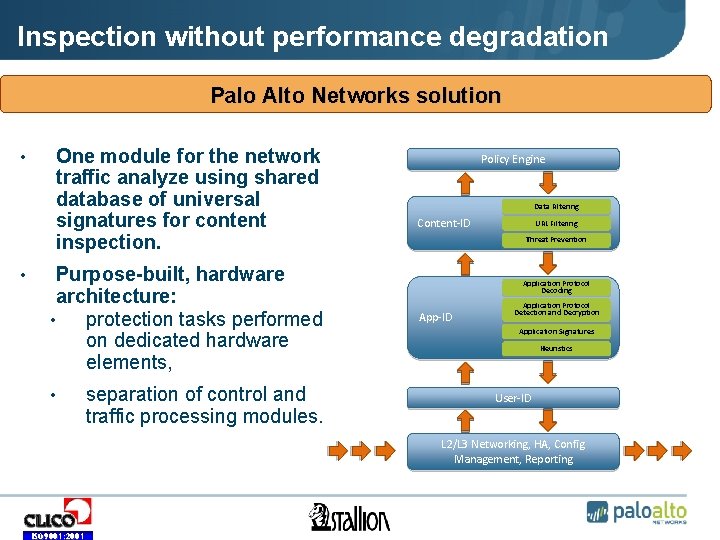
Inspection without performance degradation Palo Alto Networks solution • • One module for the network traffic analyze using shared database of universal signatures for content inspection. Purpose-built, hardware architecture: • protection tasks performed on dedicated hardware elements, • separation of control and traffic processing modules. Policy Engine Data Filtering Content-ID URL Filtering Threat Prevention Application Protocol Decoding App-ID Application Protocol Detection and Decryption Application Signatures Heuristics User-ID L 2/L 3 Networking, HA, Config Management, Reporting ISO 9001: 2001

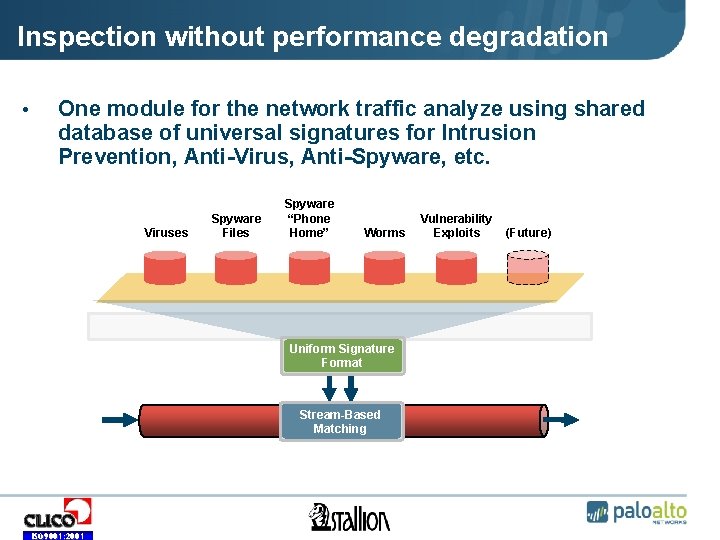
Inspection without performance degradation • One module for the network traffic analyze using shared database of universal signatures for Intrusion Prevention, Anti-Virus, Anti-Spyware, etc. Viruses Spyware Files Spyware “Phone Home” Worms Uniform Signature Format Stream-Based Matching ISO 9001: 2001 Vulnerability Exploits (Future)

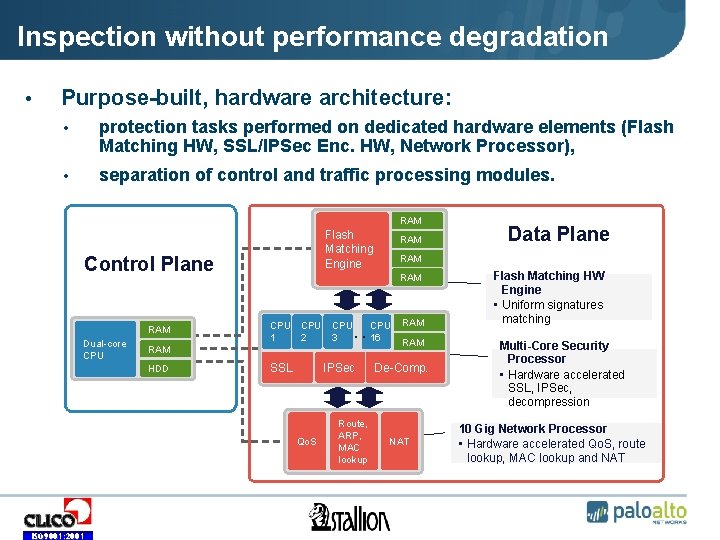
Inspection without performance degradation • Purpose-built, hardware architecture: • protection tasks performed on dedicated hardware elements (Flash Matching HW, SSL/IPSec Enc. HW, Network Processor), • separation of control and traffic processing modules. RAM Flash Matching Engine Control Plane RAM Dual-core CPU RAM HDD CPU 1 2 SSL CPU. 3 . IPSec Route, ARP, MAC lookup Data Plane RAM Qo. S ISO 9001: 2001 RAM CPU 16 RAM De-Comp. NAT Flash Matching HW Engine • Uniform signatures matching Multi-Core Security Processor • Hardware accelerated SSL, IPSec, decompression 10 Gig Network Processor • Hardware accelerated Qo. S, route lookup, MAC lookup and NAT

Security management • CLI and graphical Web console • Central management system - Panorama • Role-based administration enables delegation of tasks to appropriate person • Local user database and RADIUS • Admin audit • Syslog, SNMP and Email reporting • XML-based API ISO 9001: 2001

Security management • >commit • Active and candidate configurations • Rollback, quick comparison of different configurations ISO 9001: 2001

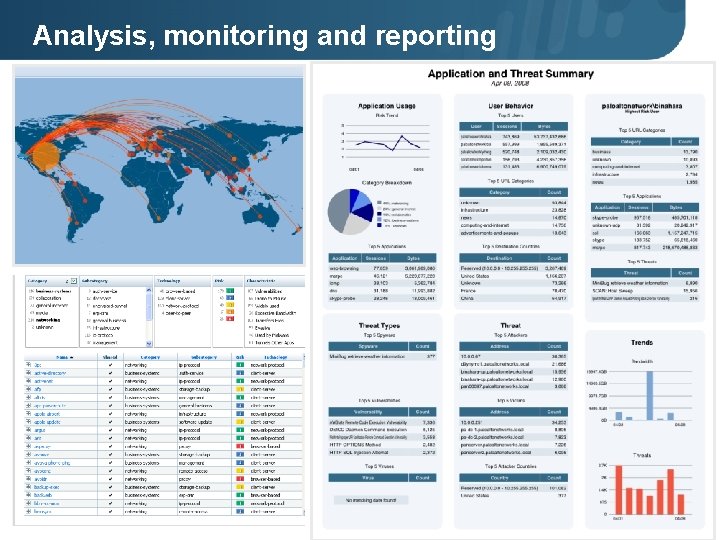
Analysis, monitoring and reporting Page 41 | ISO 9001: 2001 © 2008 Palo Alto Networks. Proprietary and Confidential.

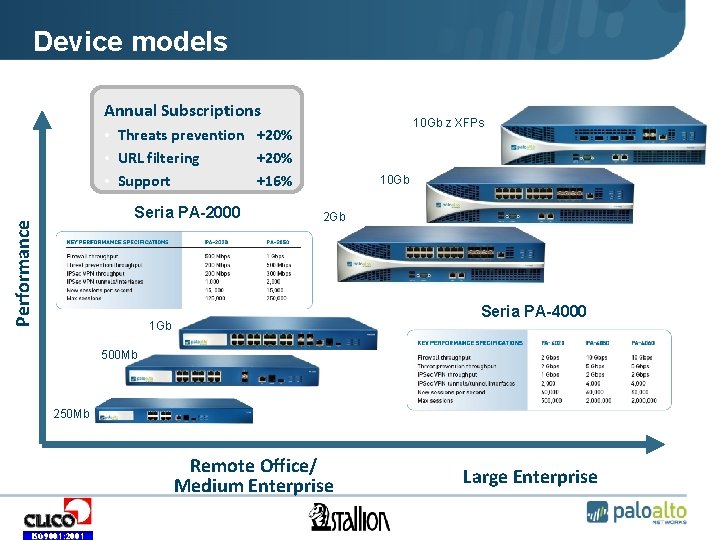
Device models Annual Subscriptions 10 Gb z XFPs • Threats prevention +20% • URL filtering +20% • Support +16% Performance • Seria PA-2000 10 Gb 2 Gb • Seria PA-4000 • 1 Gb • 500 Mb • 250 Mb Remote Office/ Medium Enterprise ISO 9001: 2001 Large Enterprise

PA-500 - 250 Mbps firewall throughput - 100 Mbps threat prevention throughput - 50 Mbps IPSec VPN throughput - 250 IPSec VPN tunnels and tunnel interfaces - 7, 500 new sessions per second - 64, 000 max sessions - (8) 10/1000 - (1) 10/1000 out of band management interface - (1) 1 RJ-45 console interface ISO 9001: 2001

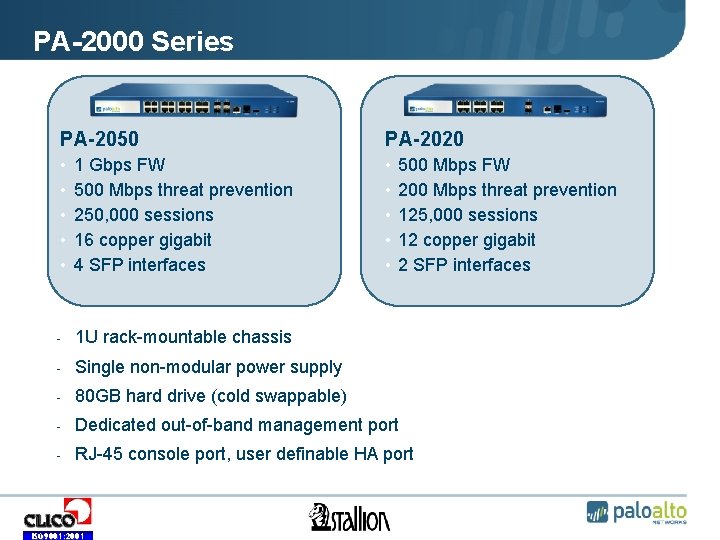
PA-2000 Series PA-2050 PA-2020 • • • 1 Gbps FW 500 Mbps threat prevention 250, 000 sessions 16 copper gigabit 4 SFP interfaces • • • - 1 U rack-mountable chassis - Single non-modular power supply - 80 GB hard drive (cold swappable) - Dedicated out-of-band management port - RJ-45 console port, user definable HA port ISO 9001: 2001 500 Mbps FW 200 Mbps threat prevention 125, 000 sessions 12 copper gigabit 2 SFP interfaces

PA-4000 Series PA-4060 PA-4050 PA-4020 • 10 Gbps FW • 5 Gbps threat prevention • 2, 000 sessions • 4 XFP (10 Gig) I/O • 4 SFP (1 Gig) I/O • 10 Gbps FW • 5 Gbps threat prevention • 2, 000 sessions • 16 copper gigabit • 8 SFP interfaces • 2 Gbps FW • 2 Gbps threat prevention • 500, 000 sessions • 16 copper gigabit • 8 SFP interfaces - 2 U, 19” rack-mountable chassis - Dual hot swappable AC power supplies - Dedicated out-of-band management port - 2 dedicated HA ports - DB 9 console port ISO 9001: 2001

Summery ISO 9001: 2001

Palo Alto Networks – unique features 1. Identifies applications regardless of port numbers, tunneling and encryption protocols (including P 2 P and IM). Firewall policy rules explicitly define what applications are permitted. More then 60% of applications are hidden from network firewalls. • Control of applications is an essential requirement of IT security standards (ISO 27001, PCI, etc. ) - The Principle of Least Privilege. • Common firewall, IPS and UTM are not able to fulfill this requirement. ISO 9001: 2001 ISO 27001, A. 11. 4. 1. Policy on use of network services. The users should only be provided with access to the services that they have been specifically a u t h o r i z e d t o u s e.

Palo Alto Networks – unique features 2. Protects the users surfing Internet against dangerous attacks in encrypted communication (e. g. malicious code, exploits for Web browsers). Non-trusted HTTPS traffic is decrypted and properly inspected (IPS, AV, etc. ). Common safeguards (network firewall, IPS, etc. ) do not analyze encrypted SSL traffic, where intruders and malicious code can easily break into internal networks. ISO 9001: 2001

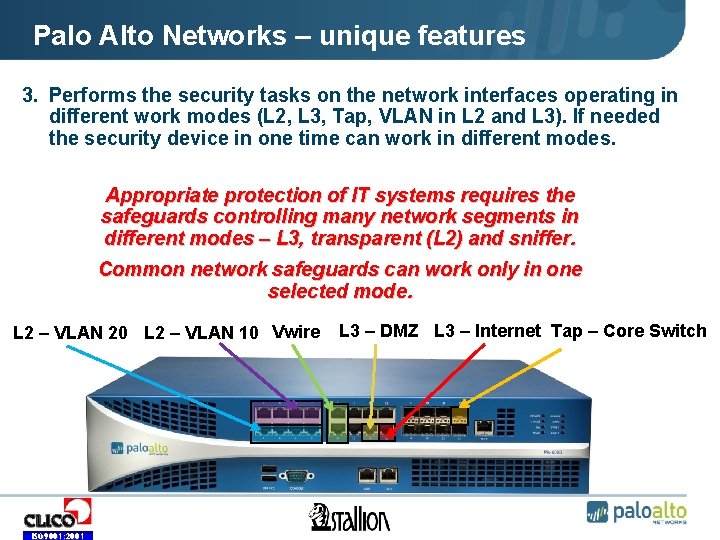
Palo Alto Networks – unique features 3. Performs the security tasks on the network interfaces operating in different work modes (L 2, L 3, Tap, VLAN in L 2 and L 3). If needed the security device in one time can work in different modes. Appropriate protection of IT systems requires the safeguards controlling many network segments in different modes – L 3, transparent (L 2) and sniffer. Common network safeguards can work only in one selected mode. • L 2 – VLAN 20 • L 2 – VLAN 10 • Vwire • L 3 – DMZ • L 3 – Internet • Tap – Core Switch ISO 9001: 2001

Palo Alto Networks – unique features Policy Engine 4. Performs accurate application inspection (IPS, AV, etc. ) without performance degradation (one inspection path - shared database of universal signatures, purposebuilt hardware architecture). Content-ID Data Filtering URL Filtering Threat Prevention App-ID Application Protocol Application Decoding Protocol Detection and Application Decryption Signatures Heuristics User-ID L 2/L 3 Networking, HA, Config Management, Reporting Application inspection in common UTM is performed on many inspection modules (IPS, AV, WF, etc. ) based on products from different vendors. • It makes huge performance degradation. • IPS module • WF module • FW module ISO 9001: 2001 • AV module

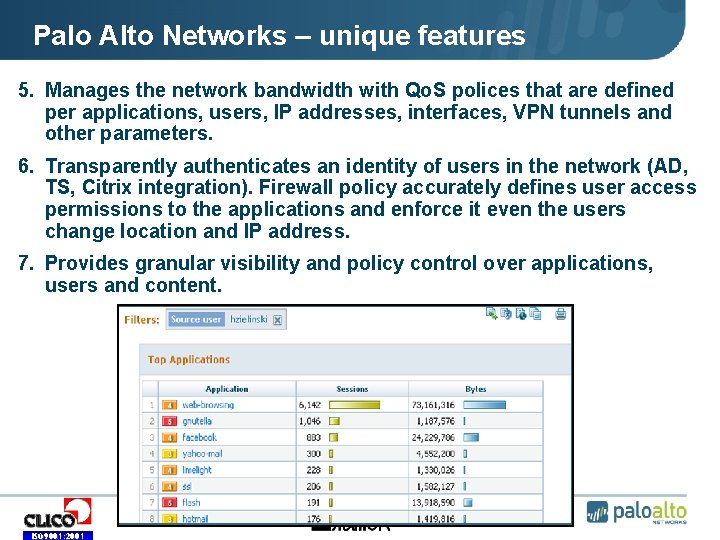
Palo Alto Networks – unique features 5. Manages the network bandwidth with Qo. S polices that are defined per applications, users, IP addresses, interfaces, VPN tunnels and other parameters. 6. Transparently authenticates an identity of users in the network (AD, TS, Citrix integration). Firewall policy accurately defines user access permissions to the applications and enforce it even the users change location and IP address. 7. Provides granular visibility and policy control over applications, users and content. ISO 9001: 2001

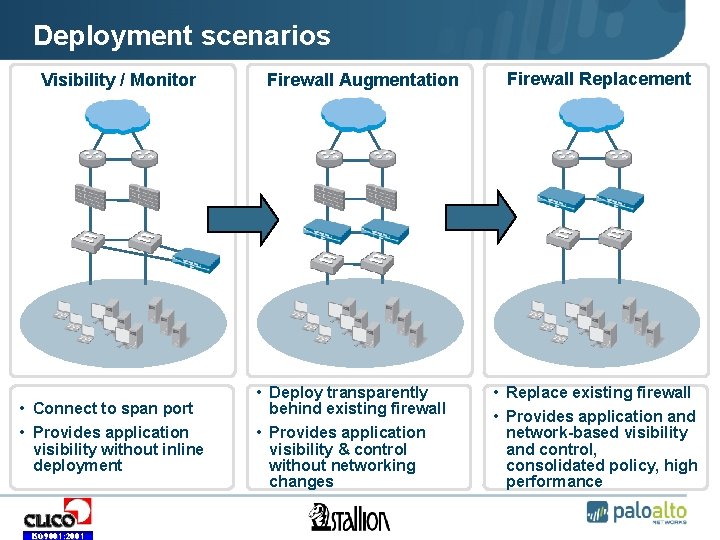
Deployment scenarios Visibility / Monitor • Connect to span port • Provides application visibility without inline deployment ISO 9001: 2001 Firewall Augmentation • Deploy transparently behind existing firewall • Provides application visibility & control without networking changes Firewall Replacement • Replace existing firewall • Provides application and network-based visibility and control, consolidated policy, high performance