Packet Leashes A Defense against Wormhole Attacks in
































- Slides: 62

Packet Leashes: A Defense against Wormhole Attacks in Wireless Networks Yih-Chun Carnegie Mellon University yihchun@cs. cmu. edu Hu. Adrian Perrig Carnegie Mellon University perrig@cs. cmu. edu David B. Johnson Rice University dbj@cs. rice. edu packet presented by Luba Yelovich-Sakharuk 1 of 62

Outline z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Introduction What is a wormhole attack? Attacker records a packet at one location in the network, tunnels the packet to another location, and replays it there. What is a leash? Any information added to a packet designed to restrict the packet’s maximum allowed transmission distance What is a packet leash? A general mechanism to detect a wormhole attack. What are geographic and temporal leashes? Two types of leashes presented in this paper. What is TIK ? An efficient authentication protocol designed for use with temporal leashes

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Problem Statement The wormhole attack is particularly dangerous against: • ad hoc network routing protocols in which the nodes that hear a packet transmission directly from some node consider themselves to be a neighbor of that node DSR, AODV DSDV, OLSR, TBRPF - use Route Request for route discovery - rely on the reception of broadcast packets for neighbor detection OLSR and TBRPF use HELLO packets to detect neighbors • any wireless access control system - an attacker could relay the authentication exchanges to gain unauthorized access

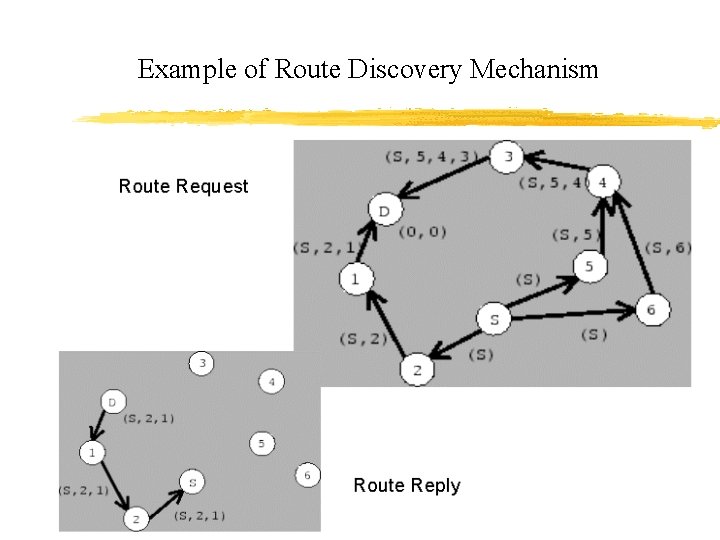
Example of Route Discovery Mechanism

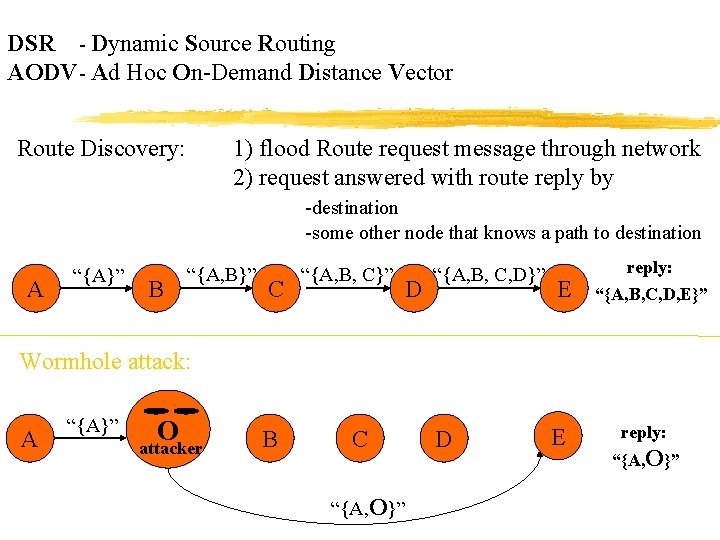
DSR - Dynamic Source Routing AODV - Ad Hoc On-Demand Distance Vector Route Discovery: 1) flood Route request message through network 2) request answered with route reply by -destination -some other node that knows a path to destination A “{A}” B “{A, B}” C “{A, B, C}” D “{A, B, C, D}” E reply: “{A, B, C, D, E}” Wormhole attack: A “{A}” O attacker B C “{A, O}” D E reply: “{A, O}”

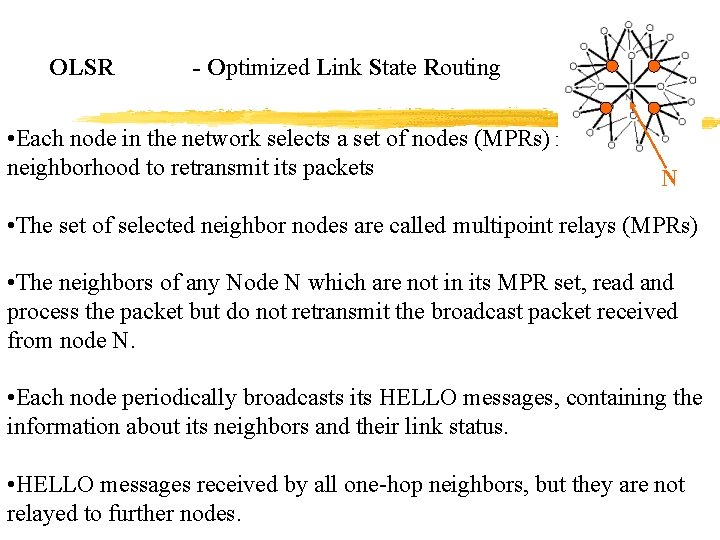
OLSR - Optimized Link State Routing • Each node in the network selects a set of nodes (MPRs) in its neighborhood to retransmit its packets N • The set of selected neighbor nodes are called multipoint relays (MPRs) • The neighbors of any Node N which are not in its MPR set, read and process the packet but do not retransmit the broadcast packet received from node N. • Each node periodically broadcasts its HELLO messages, containing the information about its neighbors and their link status. • HELLO messages received by all one-hop neighbors, but they are not relayed to further nodes.

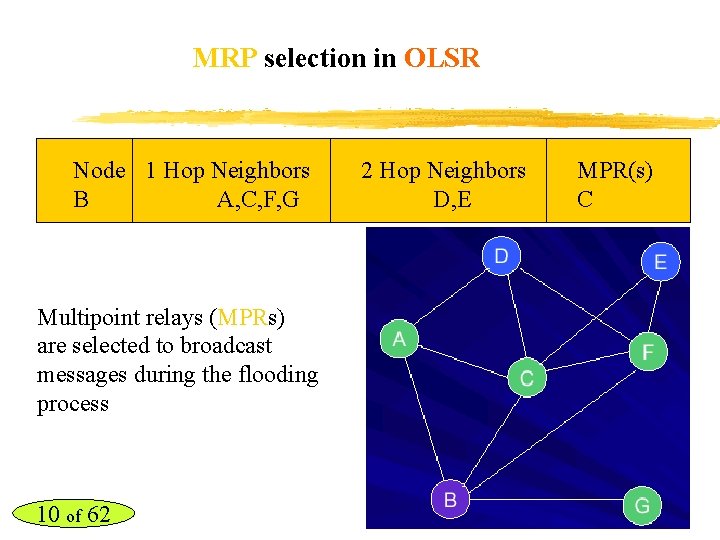
MRP selection in OLSR Node 1 Hop Neighbors B A, C, F, G Multipoint relays (MPRs) are selected to broadcast messages during the flooding process 10 of 62 2 Hop Neighbors D, E MPR(s) C

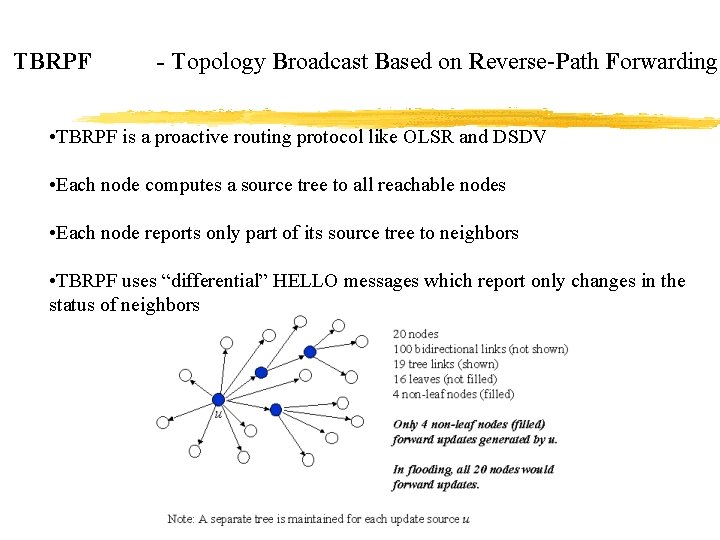
TBRPF - Topology Broadcast Based on Reverse-Path Forwarding • TBRPF is a proactive routing protocol like OLSR and DSDV • Each node computes a source tree to all reachable nodes • Each node reports only part of its source tree to neighbors • TBRPF uses “differential” HELLO messages which report only changes in the status of neighbors

OLSR and TBRPF use HELLO packets to detect neighbors HELLO A HELLO O attacker O LL HE LO L HE A and B will believe they are neighbors, which will cause the routing protocol to fail to find routes. O attacker HELLO B

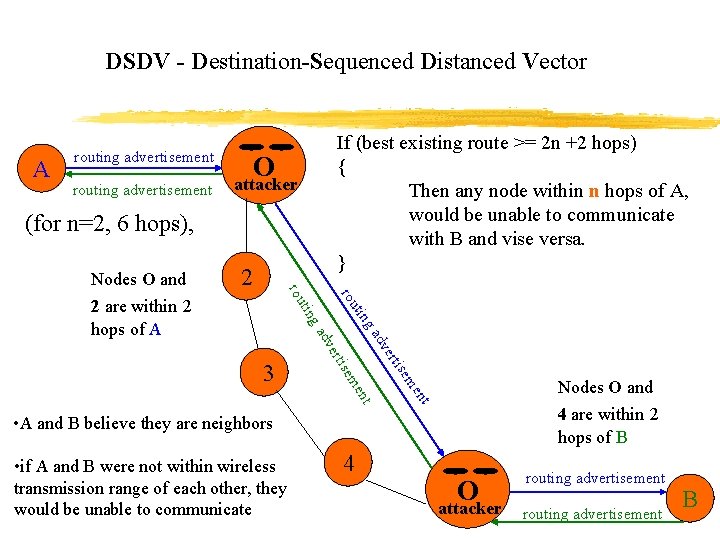
DSDV - Destination-Sequenced Distanced Vector A routing advertisement If (best existing route >= 2 n +2 hops) { Then any node within n hops of A, would be unable to communicate with B and vise versa. } O attacker (for n=2, 6 hops), 2 ise Nodes O and me nt nt me ise ert dv 3 ga tin 2 are within 2 hops of A rou Nodes O and 4 are within 2 hops of B • A and B believe they are neighbors • if A and B were not within wireless transmission range of each other, they would be unable to communicate 4 O attacker routing advertisement B

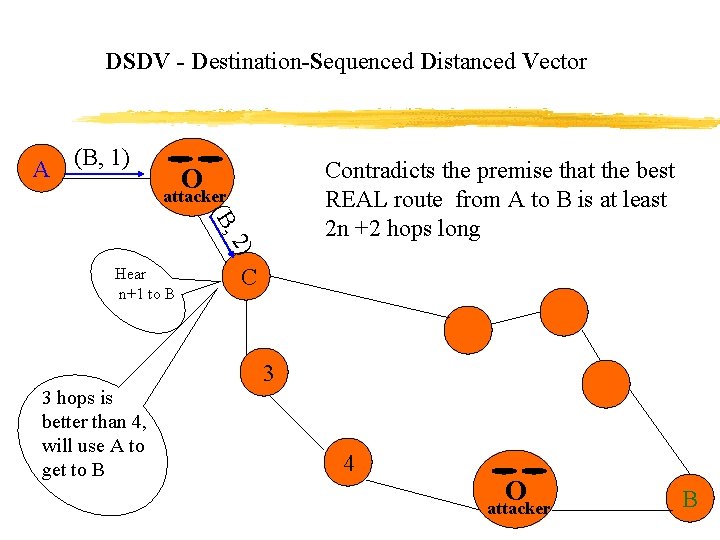
DSDV - Destination-Sequenced Distanced Vector A (B, 1) Contradicts the premise that the best REAL route from A to B is at least 2 n +2 hops long O attacker ) , 2 (B Hear n+1 to B C 3 3 hops is better than 4, will use A to get to B 4 O attacker B

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Assumption and Notation • Beyond the scope of this paper: • Security attacks on the wireless network’s physical layer • Denial-of-Service attacks against MAC layer protocols • Assumptions • The wireless network may drop, corrupt, duplicate, or reorder packets • MAC layer contains level of redundancy to detect randomly corrupted packets • Nodes in the network may be resource constrained • Node can obtain an authenticated key for the other node • TIK - TESLA with Instant Key Disclosure • Uses only efficient symmetric cryptography (block ciphers and hash functions) • Like public keys in systems using asymmetric cryptography (digital signatures), these keys in TIK are public values(once disclosed).

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Detecting Wormhole Attacks • Packet leash is general mechanism to detect a wormhole attack. • Leash is any information added to a packet designed to restrict the packet’s maximum allowed transmission distance • Geographical leash insures that the recipient of the packet is within a certain distance from the sender. • Temporal leash ensures that the packet has an upper bound of its lifetime (restricts the maximum travel distance). Not allowed further BUSTED packet

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Geographical Leashes Sender Ps ts -------dsr Ps tr Receiver ts Pr ||Ps - Pr|| + 2 v*(tr - ts + ) + Ps - location of the Sender Pr - location of the Receiver ts - time at which Sender sent the packet tr - time at which Receiver received the packet v - velocity of any node - maximum relative error in location information -error in the clocks synchronization Note: Any authentication technique can be used to allow a receiver to authenticate the location and timestamp in the received packets 20 of 62

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

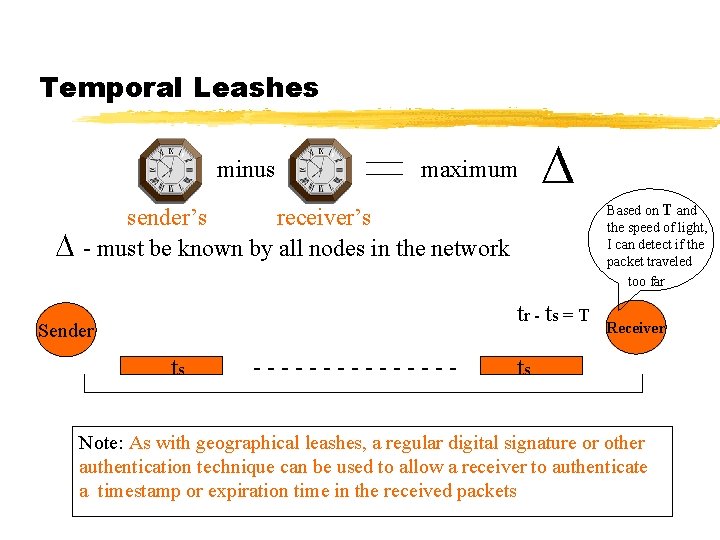
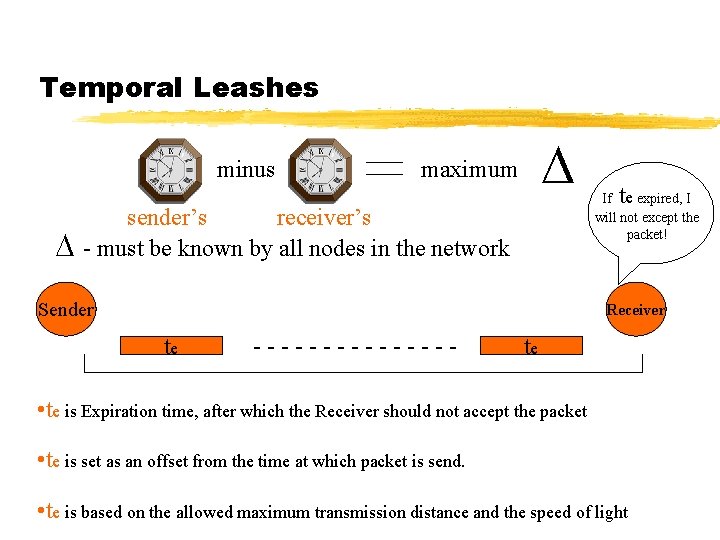
Temporal Leashes minus maximum Based on T and the speed of light, I can detect if the packet traveled too far sender’s receiver’s - must be known by all nodes in the network tr - ts = T Sender ts -------- Receiver ts Note: As with geographical leashes, a regular digital signature or other authentication technique can be used to allow a receiver to authenticate a timestamp or expiration time in the received packets

Temporal Leashes minus maximum sender’s receiver’s - must be known by all nodes in the network Sender t If e expired, I will not except the packet! Receiver te -------- te • te is Expiration time, after which the Receiver should not accept the packet • te is set as an offset from the time at which packet is send. • te is based on the allowed maximum transmission distance and the speed of light

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Discussion An advantage of geographical leashes over temporal leashes: • time synchronization can be much looser • attacker can be caught if it pretends to reside at multiple locations A potential problem with leashes using a timestamp in a packet, the sender may not know the precise time at which it will transmit the packet The sender will know the time one slot (20 s) prior to transmission Generating a digital signature, could take 10 ms (RSA with 1024 -bit key) Two approaches to hide the signature generation latency: • increase minimum transmission unit to allow computation to overlap with transmission • use more efficient signature scheme such as Schnorr’s signature

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Temporal Leashes and the TIK Protocol TIK te or ts Discussion of temporal leashes in more detail Design and operation of TIK protocol that implements temporal leashes

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Temporal Leash Construction Details Sender te = ts + L/ c - te -------- tr < te? If so, I will process the packet. If not, I will drop it! Receiver te c - propagation speed of our wireless signal L - temporal leash prevents the packet from travelling further than distance L, L > Lmin = ts - time at which Sender sent the packet tr - time at which Receiver received the packet te - expiration timer -error in the clocks synchronization Receiver needs to authenticate the expiration time: • Sender S and Receiver R must share a secret key K • To send a message M to a receiver R, S sends: S R: M, HMACK (M) , where HMACK (M) represents the message authentication code computed over message M with key K *c

Two major drawbacks in using message authentication codes in the standard: 30 of 62 1 • Key setup is an expensive operation • n(n-1)/2 keys in network with n nodes 2 • This approach can not efficiently authenticate broadcast packets • To secure a broadcast packet, add to the packet separate message authentication code - makes packet extremely large • Separate HMAC can be avoided by multiple receivers sharing the same key, BUT it might allow colluding receivers to impersonate the sender

SOLUTION to the two major drawbacks: • Attach a digital signature to each packet • Each node needs to have only one public-private key pair • Each node needs to know only the public key for every other node • Only n public keys need to be distributed in a network with n nodes • A digital signature provides non-repudiation and authentication for broadcast packet the same way as for unicast packets

Several drawbacks in using digital signatures: • Usually digital signature are based on computationally expensive asymmetric cryptography • Computationally expensive for the verifier (receiver) • Overwhelmingly expensive for the signer (sender) $$$$$$$ Solution: Designed TIK protocol, based on a new protocol for efficient broadcast authentication that simultaneously provides the functionality of a temporal leash

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

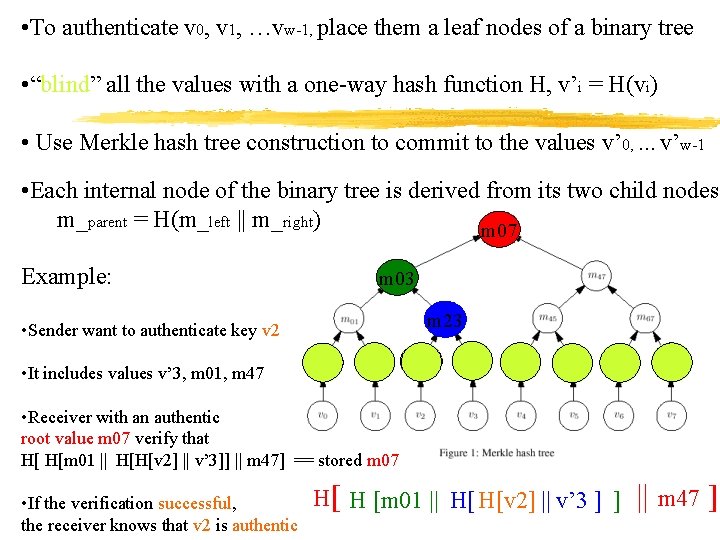
Tree-Authenticated Values • TIK requires an efficient mechanism for authenticating keys • Values from a one-way hash chain are very efficient to verify, but only if values in sequence • For the TIK, values used very sparsely • One-way hash function is efficient to compute, but computation requires overhead • Tree structure is used for more efficient authentication of values

• To authenticate v 0, v 1, …vw-1, place them a leaf nodes of a binary tree • “blind” all the values with a one-way hash function H, v’i = H(vi) • Use Merkle hash tree construction to commit to the values v’ 0, . . . v’w-1 • Each internal node of the binary tree is derived from its two child nodes m_parent = H(m_left || m_right) m 07 Example: m 03 m 23 • Sender want to authenticate key v 2 v'2 • It includes values v’ 3, m 01, m 47 • Receiver with an authentic root value m 07 verify that H[ H[m 01 || H[H[v 2] || v’ 3]] || m 47] == stored m 07 • If the verification successful, the receiver knows that v 2 is authentic H[ H [m 01 || H[ H[v 2] || v’ 3 ] ] || m 47 ]

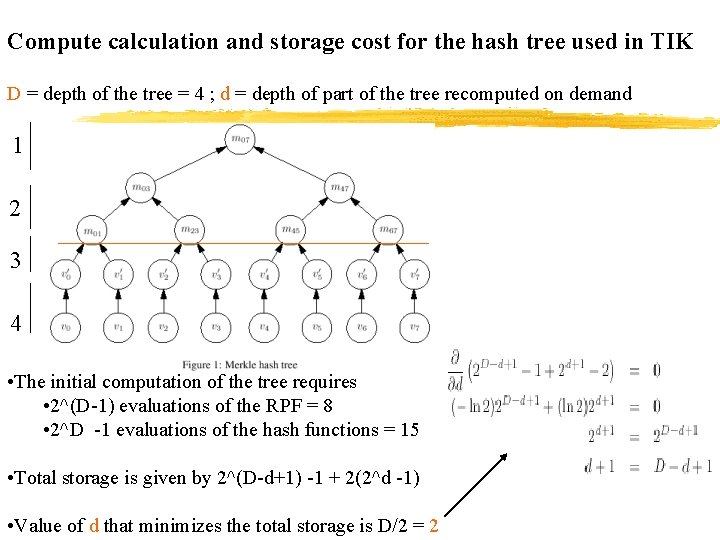
Hash Tree Optimization • In TIK, the depth of the hash tree can be large • Storing the entire tree is impractical • Store only the upper layers of the tree, recompute lower layer on demand • Node keeps two trees of depth d, • one fully computed and being used • one being filled in

Compute calculation and storage cost for the hash tree used in TIK D = depth of the tree = 4 ; d = depth of part of the tree recomputed on demand 1 2 3 4 • The initial computation of the tree requires • 2^(D-1) evaluations of the RPF = 8 • 2^D -1 evaluations of the hash functions = 15 • Total storage is given by 2^(D-d+1) -1 + 2(2^d -1) • Value of d that minimizes the total storage is D/2 = 2

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

TIK Protocol Description TIK - TESLA with Instant Key Disclosure (extension of the TESLA broadcast authentication protocol ) • TIK implements a temporal leash and enables the receiver to detect a wormhole attack • TIK is based on efficient symmetric cryptographic primitives • TIK requires accurate time synchronization between all communicating parties • TIK requires each communicating node to know just one public value for each sender • FOUR stages in TIK protocol: • Sender setup • Receiver bootstrapping • Sending and Verifying Authenticated packets

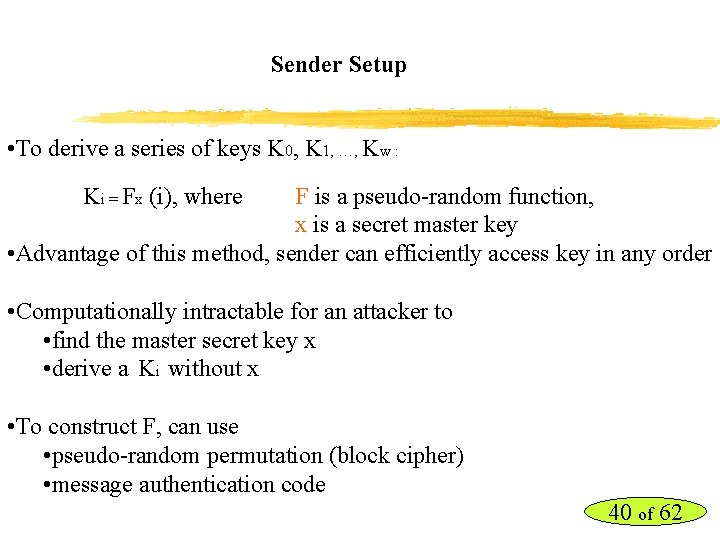
Sender Setup • To derive a series of keys K 0, K 1, …, Kw : Ki = Fx (i), where F is a pseudo-random function, x is a secret master key • Advantage of this method, sender can efficiently access key in any order • Computationally intractable for an attacker to • find the master secret key x • derive a Ki without x • To construct F, can use • pseudo-random permutation (block cipher) • message authentication code 40 of 62

More on Sender Setup • Sender selects a key expiration interval I • Determines a schedule for each of it’s keys to expire K 0 expires at T 0, K 1 expires at T 1 = T 0 + I, Ki expires at Ti = Ti-1 + I= T 0 + i*I • Sender constructs the Merkle hash tree to commit K 0, K 1, …, Kw-1 • The root of the resulting hash tree is m 0, w-1, or simply m • The value m commits to all keys and is used to authenticate any leaf key efficiently!

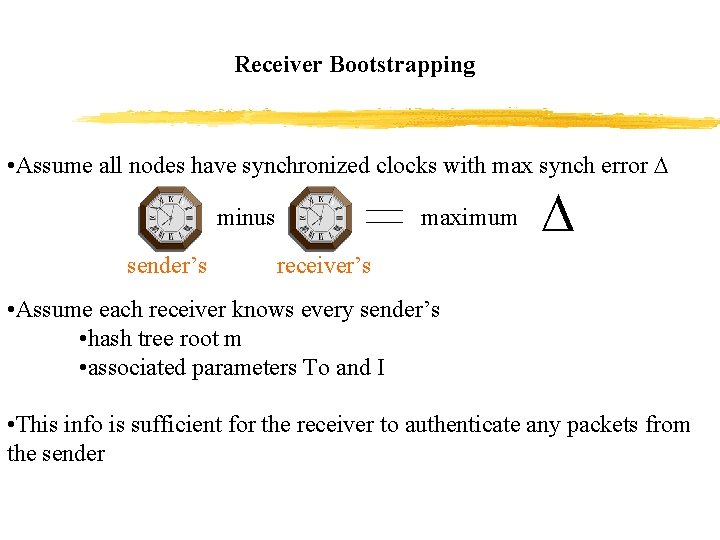
Receiver Bootstrapping • Assume all nodes have synchronized clocks with max synch error minus sender’s maximum receiver’s • Assume each receiver knows every sender’s • hash tree root m • associated parameters To and I • This info is sufficient for the receiver to authenticate any packets from the sender

Sending and Verifying Authentication Packets • Sender sends a Packet P • Estimates upper bound tr on the arrival time of the HMAC at the receiver • Based on tr, sender picks a key Ki, Ti > tr + Sender Ki , v’ 3, m 01, m 47 - -key expired - - HMAC ------- Receiver • Sender discloses the key only after it expires • No attacker can know Ki • Once the receiver gets the authentic key Ki, it can authenticate all packets that carry a message authentication code computed with Ki

Drawback • Message authentication is delayed • Receiver must wait for the key before it can authenticate the packet • If nodes are tightly time synchronized, possible to remove authentication delay • Sender can disclose the key in the same packet that carries the corresponding message authentication code

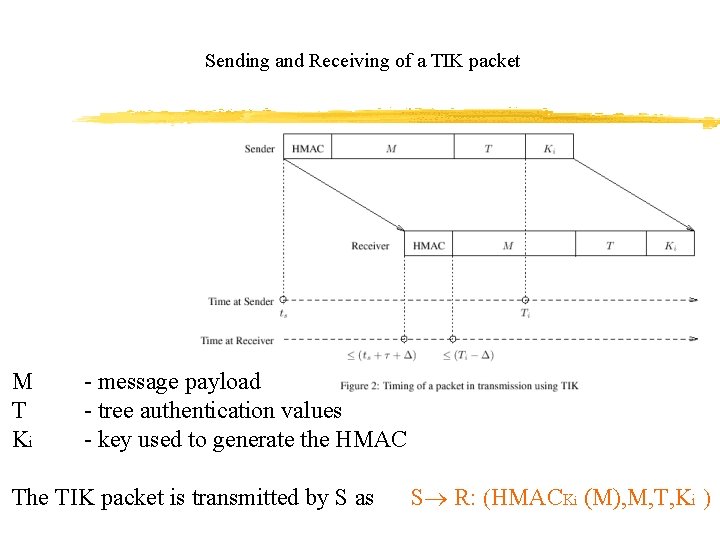
Sending and Receiving of a TIK packet M T Ki - message payload - tree authentication values - key used to generate the HMAC The TIK packet is transmitted by S as S R: HMACKi (M), M, T, Ki

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

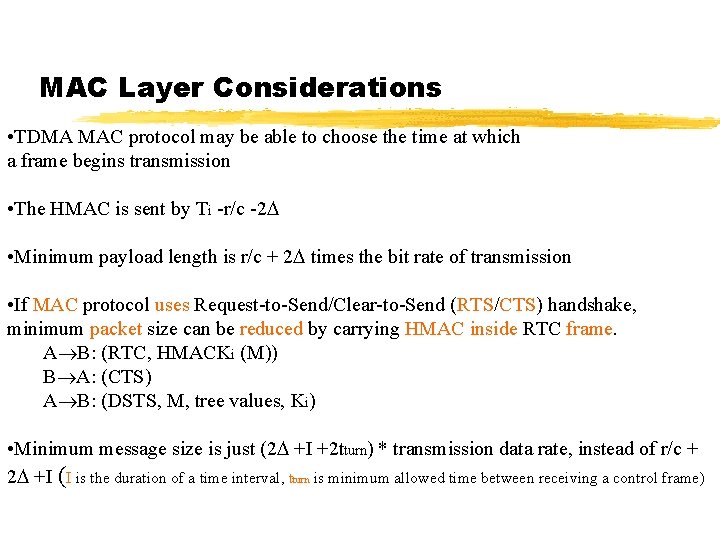
MAC Layer Considerations • TDMA MAC protocol may be able to choose the time at which a frame begins transmission • The HMAC is sent by Ti -r/c -2 • Minimum payload length is r/c + 2 times the bit rate of transmission • If MAC protocol uses Request-to-Send/Clear-to-Send (RTS/CTS) handshake, minimum packet size can be reduced by carrying HMAC inside RTC frame. A B: (RTC, HMACKi (M)) B A: (CTS) A B: (DSTS, M, tree values, Ki) • Minimum message size is just (2 +I +2 tturn) * transmission data rate, instead of r/c + 2 +I (I is the duration of a time interval, tturn is minimum allowed time between receiving a control frame)

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Evaluation Is TIK good?

50 of 62 z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

TIK Performance • Measured computational power and memory currently available in mobile devices • Optimized MD 5 hash code from ISI to achieve maximum performance for hashing hashes/second Pentium III Compaq i. Paq 3870 Pocket. PC 1 GHz Linux 1. 3 million 222, 000 • Can also be efficiently implemented in hardware 20 k gate ASIC (1/3 complexity of Bluetooth, <1/3 IEEE 802. 11 Xilinx FPGA using 1650 LUTs 1. 9 million 1. 0 million • In terms of memory consumption i. Paq 3870 32 MB Flash, 64 MB of RAM Modern notebooks 100 s of Mbytes of RAM

• IEEE 802. 11 a card: • transmission data rate of 108 Mbps • range of 250 m • To authenticate a received packet, a node needs to perform 33 hashes • To keep up wit link speed, a node needs to verify pack at most 25. 9 s • Requiring 1, 273, 000 hashes per second • For a total computational requirement of 1, 516, 000 hashes per second Can be achieved today in hardware by: • placing two MD 5 units on a singe FPGA board • with an ASIC Many laptops today are equipped with at least 1. 2 GHz Pentium III CPU’s which should be able to perform 1. 5 million hash operation per second

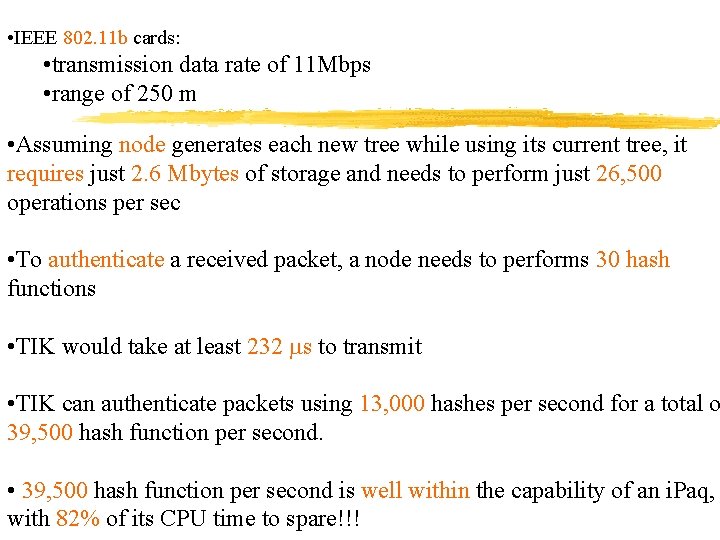
• IEEE 802. 11 b cards: • transmission data rate of 11 Mbps • range of 250 m • Assuming node generates each new tree while using its current tree, it requires just 2. 6 Mbytes of storage and needs to perform just 26, 500 operations per sec • To authenticate a received packet, a node needs to performs 30 hash functions • TIK would take at least 232 s to transmit • TIK can authenticate packets using 13, 000 hashes per second for a total o 39, 500 hash function per second. • 39, 500 hash function per second is well within the capability of an i. Paq, with 82% of its CPU time to spare!!!

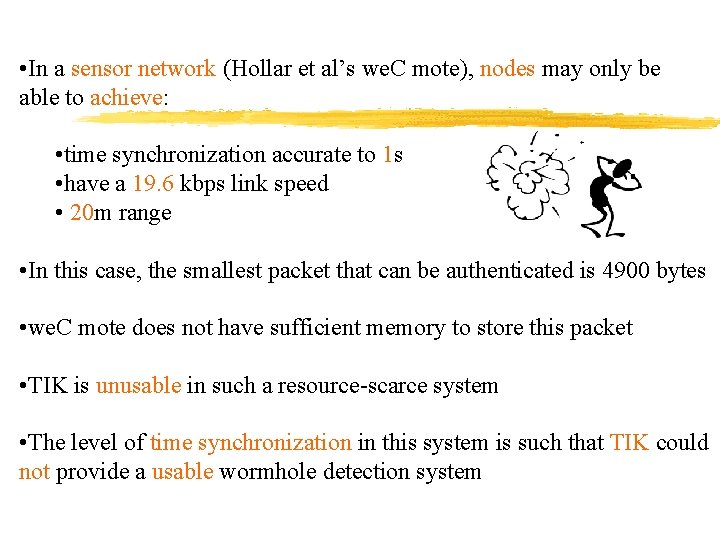
• In a sensor network (Hollar et al’s we. C mote), nodes may only be able to achieve: • time synchronization accurate to 1 s • have a 19. 6 kbps link speed • 20 m range • In this case, the smallest packet that can be authenticated is 4900 bytes • we. C mote does not have sufficient memory to store this packet • TIK is unusable in such a resource-scarce system • The level of time synchronization in this system is such that TIK could not provide a usable wormhole detection system

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

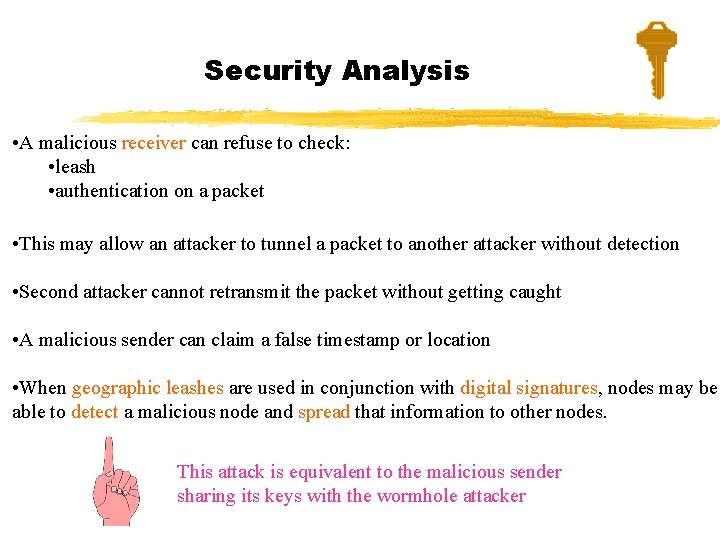
Security Analysis • A malicious receiver can refuse to check: • leash • authentication on a packet • This may allow an attacker to tunnel a packet to another attacker without detection • Second attacker cannot retransmit the packet without getting caught • A malicious sender can claim a false timestamp or location • When geographic leashes are used in conjunction with digital signatures, nodes may be able to detect a malicious node and spread that information to other nodes. This attack is equivalent to the malicious sender sharing its keys with the wormhole attacker

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

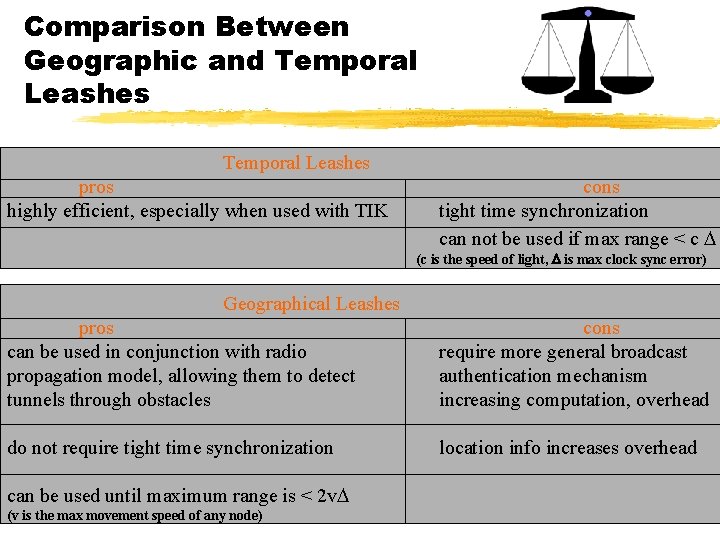
Comparison Between Geographic and Temporal Leashes pros highly efficient, especially when used with TIK cons tight time synchronization can not be used if max range < c (c is the speed of light, is max clock sync error) Geographical Leashes pros can be used in conjunction with radio propagation model, allowing them to detect tunnels through obstacles cons require more general broadcast authentication mechanism increasing computation, overhead do not require tight time synchronization location info increases overhead can be used until maximum range is < 2 v (v is the max movement speed of any node)

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

60 of 62 Related Work • Radio Frequency (RF) water marking (difficult to assess its security) • No work has been published regarding possibility of using intrusion detection to detect wormhole attacks • TIK provides advantage over hop-by-hop authentication with TESLA (latency and packet overhead, but byte overhead suffers) • IEEE 802. 11 i Task Group is designing modifications to IEEE 802. 11 to improve security (proposals don’t address wormhole attack) • Other Medium Access Control protocols specify privacy and authenticity mechanisms (none protect against wormhole attacks)

z z z z Introduction Problem Statement Assumption and Notation Detecting Wormhole Attacks y Geographical Leashes y Temporal Leashes y Discussion Temporal Leashes and the TIK Protocol y Temporal Leash Construction Details y Tree-Authenticated Values y TIK Protocol Description y MAC Layer Considerations Evaluation y TIK Performance y Security Analysis y Comparison Between Geographic and Temporal Leashes Related Work Conclusions

Conclusions • Wormhole attack • Packet leashes • Geographic and Temporal leashes • TIK 62