PACKET HIDING METHODS FOR PREVENTING SELECTIVE JAMMING ATTACKS













- Slides: 24

PACKET HIDING METHODS FOR PREVENTING SELECTIVE JAMMING ATTACKS ‘- Naina Nigam (50208030) Surabhi Singh (50208675) 1

WIRELESS NETWORKS • One of the most transformative technology trends of the past decade is the availability and growing expectation of ubiquitous connectivity. • Without a doubt, the future is about connectivity where access to the Internet is omnipresent. ‘ • Wireless networks are at the epicenter of this trend. At its broadest, a wireless network refers to any network not connected by cables, which is what enables the desired convenience and mobility for the user. • There are several advantages and disadvantages of wireless networks that the users should be aware of. 2

ADVANTAGES • Wi-Fi Hotspots : It has become a necessity for many people to remain connected to the internet whenever they are awake. Wireless network is a boon to such people. ‘ • Better Mobility : Mobility is a great advantage offered by wireless networks especially for businesses. It enables you to access the server from anywhere in the office. • Cost effective : Compared to wired network, wireless network are cost effective because it requires no cables and other accessories to connect. • Scalability : Expansion with wireless is pretty easy. A new user can be added by issuing a password and updating it in the server. 3

DISADVANTAGES • Lesser range : Normally, the range of a medium-range wireless network is up to around 100 meters. This may be suitable for a home or a small office, but insufficient for larger structures. ‘ • Security issues : Wireless networks involve the risk of modification and eavesdropping. So they make use of certain encryption techniques for security. • Reliability : Since wireless networks work with radio wave communication, the signal is affected by much interference. • Less speed : The maximum speed of 802. 11 n standard network is 600 Mbps. This is only almost half the speed of a wired network. 4

WIRELESS NETWORK SECURITY CONCERN • Wireless networks rely on the uninterrupted availability of the wireless medium to interconnect participating nodes. • However, the open nature of this medium leaves it vulnerable to ‘multiple security threats. • Anyone with a transceiver can eavesdrop on wireless transmissions, inject spurious messages, or jam legitimate ones. • While eaves- dropping and message injection can be prevented using cryptographic methods, jamming attacks are much harder to counter. 5

JAMMING • In the simplest form of jamming, the adversary interferes with the reception of messages by transmitting a continuous jamming signal, or several short jamming pulses. ‘ • In almost every case, jamming causes a denial of service type attack to either sender or receiver. • The easiest form of jamming a wireless network communication is to continually transmit useless data to the node where the server becomes overloaded. • Most people have no idea if a jamming signal is in use. It appears as if there is no service. 6

TYPES OF JAMMERS Jammers are categorized into four models: • Constant Jammer : In this model, jammer continuously emits RF signals and it transmits random bits of data to channel. It does not follow any MAC layer etiquette. Being constant to the transfer it ‘does not wait for channel to become an idle. • Deceptive Jammer : In this model, jammer constantly injects series packets to the channel without any gap between subsequent transmissions. It also broadcasts fabricated messages and reply old ones. • Random Jammer : In this model, jammer alternates between period of continuous jamming and inactivity. • Reactive Jammer : In this model, jammer will stay quite when the channel is idle. As soon as it senses activity on channel, it starts transmitting signal. 7

PROBLEM STATEMENT • The problem of jamming under an internal threat model is considered. • The adversary is aware of the network secrets and the implementation details of the network protocols at any layer in the ‘network stack. • The adversary exploits his internal knowledge for launching selective jamming attacks in which messages of high-importance are targeted. • To launch selective jamming attacks, the adversary must be capable of implementing classify-then-jam strategy. • This can be done either by classifying transmitted packets using protocol semantics or by decoding packets on the fly. 8

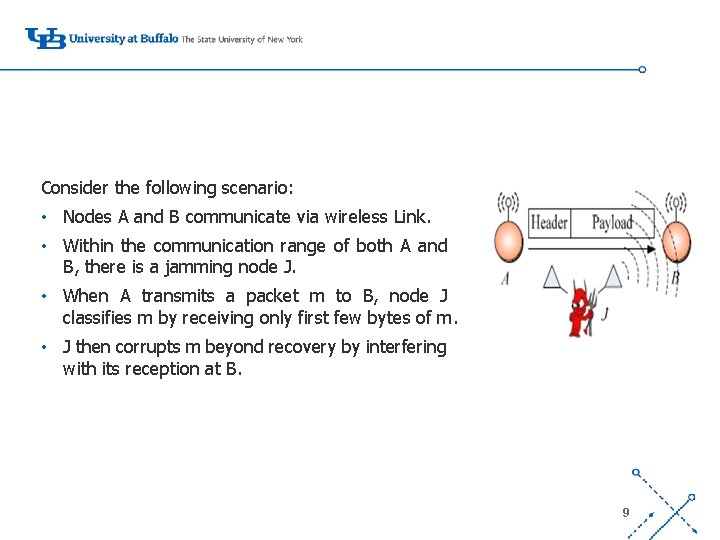
Consider the following scenario: • Nodes A and B communicate via wireless Link. • Within the communication range of both A and B, there is a jamming node J. ‘ • When A transmits a packet m to B, node J classifies m by receiving only first few bytes of m. • J then corrupts m beyond recovery by interfering with its reception at B. 9

PROPOSED METHODOLOGY • Preventing the jamming node from performing real-time packet classification, thus mitigating adversary’s ability to perform selective jamming. ‘ • Real-time packet classification is prevented by combining cryptographic primitives with physical-layer attributes. • The cryptographic primitives are : Strong Hiding Commitment scheme, Puzzle based Hiding scheme and All-or-Nothing based hiding scheme. 10

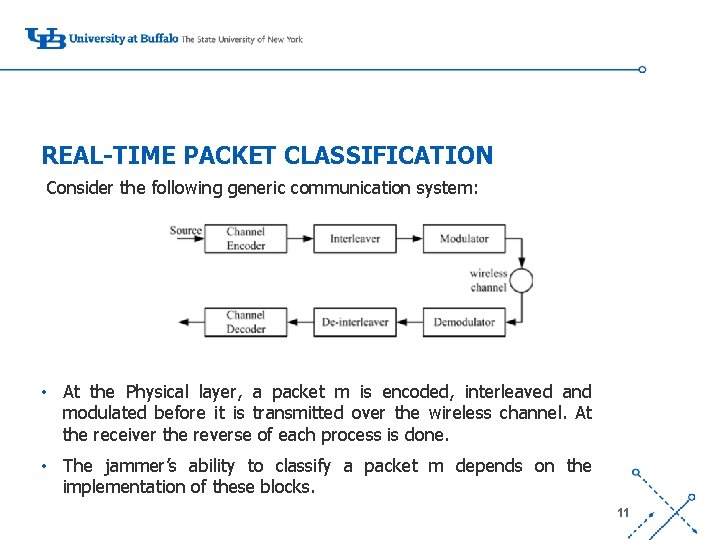
REAL-TIME PACKET CLASSIFICATION Consider the following generic communication system: ‘- • At the Physical layer, a packet m is encoded, interleaved and modulated before it is transmitted over the wireless channel. At the receiver the reverse of each process is done. • The jammer’s ability to classify a packet m depends on the implementation of these blocks. 11

AN EXAMPLE. . • Consider the transmission of a TCP-SYN packet used for establishing a TCP connection at the transport layer. • PHY Layer – 40 bit header + 6 bit tail appended to the MAC packet ‘carrying the TCP-SYN packet • Encoding – ½ rate Convolutional encoder maps the packet to a sequence of 1180 bits • Interleaving – The output of the encoder is split into 25 blocks of 48 bits each and interleaved on a per symbol basis • Modulation - Each of the block is modulated as an OFDM symbol for transmission 12

CONTD. . Information contained in each of the 25 OFDM symbols – • Symbols 1 -2 contain the PHY-layer header and the first byte of the MAC Header • Symbols 3 -10 contain the source and destination MAC addresses and the length of the IP packet header ‘ • Symbols 11 -17 contain the source and destination IP addresses, the size of the TCP datagram carried by the IP packet, and other IP layer information • Symbols 18 -23 contain the TCP destination port, sequence number, acknowledgment number, TCP flags, window size, and the header checksum • Symbols 24 -25 contain the MAC CRC code. • it is evident that intercepting the first few symbols of a packet is sufficient for obtaining relevant header information 13

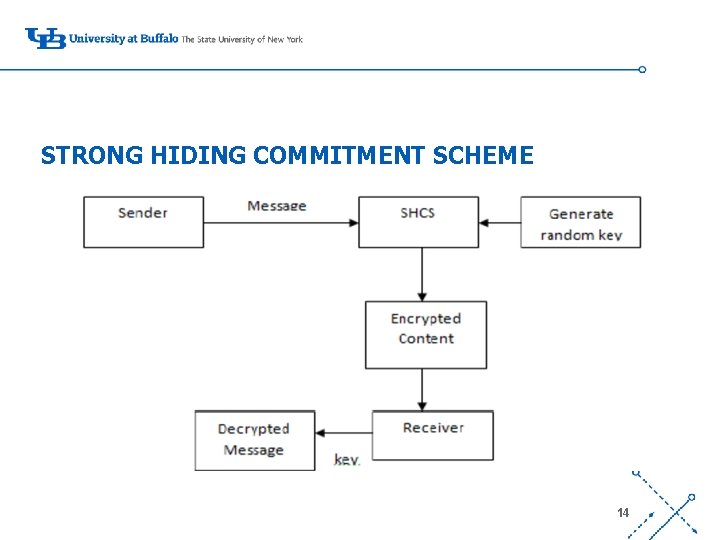
STRONG HIDING COMMITMENT SCHEME ‘- 14

• Strong Hiding Commitment Scheme is based on symmetric cryptography. • Firstly the key is selected randomly of length s. • Data is divided into packets and these packets are encrypted using ‘the newly generated key. • Some bits are added to the encrypted data as padding process to hide the identity of the data. • The data is then permuted and transferred to the destination node. • The cryptographic key is refreshed periodically to hide the key from the jammer node. 15

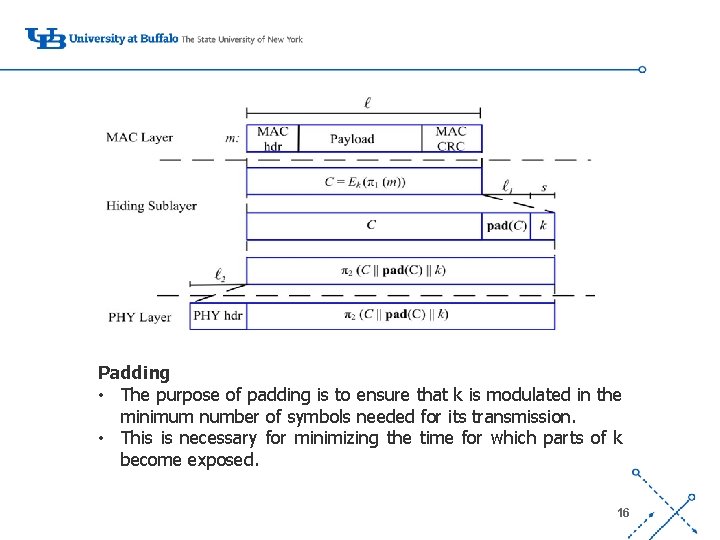
‘- Padding • The purpose of padding is to ensure that k is modulated in the minimum number of symbols needed for its transmission. • This is necessary for minimizing the time for which parts of k become exposed. 16

Permutation • Permutation 1 (P 1) is applied to m before it is encrypted. distributes critical frame fields which can be used for packet ‘classification across multiple plaintext blocks. Hence, to reconstruct these fields, all corresponding cipher text blocks must be received and decrypted. • Header information is pushed at the end of P 1(m). • Permutation 2 (P 2) is applied to reverse the effects of interleaving on the bits of k, so that k is contained at the packet trailer. 17

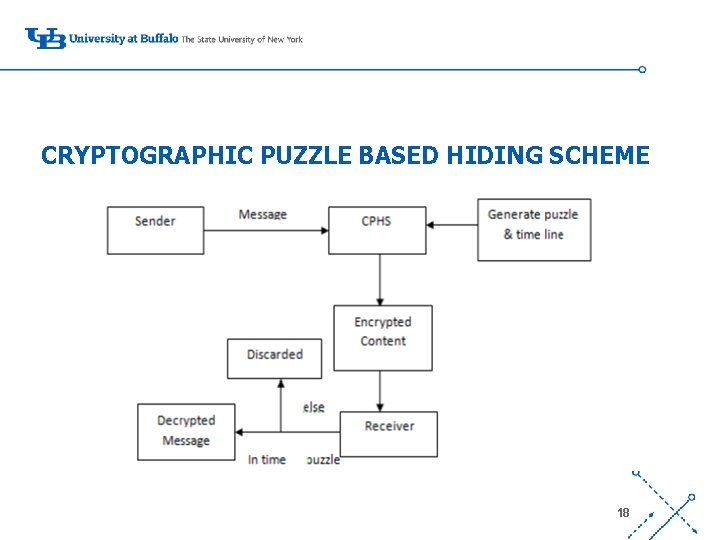
CRYPTOGRAPHIC PUZZLE BASED HIDING SCHEME ‘- 18

• The sender S selects a random key k of some desired length. • S generates a puzzle P= puzzle(k, t), where puzzle() denotes the puzzle generator function, and t denotes the time required for the solution of the puzzle. ‘ • t is directly dependent on the assumed computational capability of the adversary denoted by N • Receiver solves the received puzzle to recover the key k and then computes the decrypted packet • If the decrypted packet is meaningful then it is accepted, else discarded • Can be implemented in 2 ways – Time-lock puzzles and Puzzles based on Hashing 19

ALL-OR-NOTHING BASED HIDING SCHEME • An AONT serves as a publicly known and completely invertible preprocessing step to a plaintext before it is passed to an ordinary block encryption algorithm. • A transformation f, mapping message m={m 1, …, mx} to a sequence of pseudo messages m’={m 1’, …. , mx’} is an AONT if ‘ 1. f is a bijection 2. It is computationally infeasible to obtain any part of the original plaintext, if one of the pseudo messages is unknown. 3. f and it’s inverse are efficiently computable. • When a plaintext is preprocessed by an AONT before encryption, all cipher text blocks must be received to obtain any part of the plaintext. • Can be implemented using 2 AONTs: linear transformation and original packet transformation. 20


CONCLUSION • Addressed the problem of selective jamming in wireless networks under internal threat model. • Discussed 3 packet hiding techniques using cryptographic ‘primitives which helps to prevent selective jamming in the wireless networks. • Though these techniques are quite efficient, there is still scope of improving these schemes for better throughput. 22

REFERENCE • Alejandro Proano and Loukas Lazos, “Packet-Hiding Methods for ‘Preventing Selective Jamming Attacks”, IEEE Transactions on Dependable and Secure Computing, Vol. 9, No. 1, pp 101 -114, January/February 2012 23

THANK YOU!! ‘- 24