OWASP INTERNET OF THINGS Penetration Testing Methodology OWASP




- Slides: 18

OWASP INTERNET OF THINGS Penetration Testing Methodology OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

WHO AM I? • Ethical Hacker aka IT Security Consultant • IT Security Researcher • Forensic Investigator (Computer hacking) • Chapter Leader for OWASP Macedonia Chapter • Certified EC-Council Instructor • Microsoft Certified Trainer OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

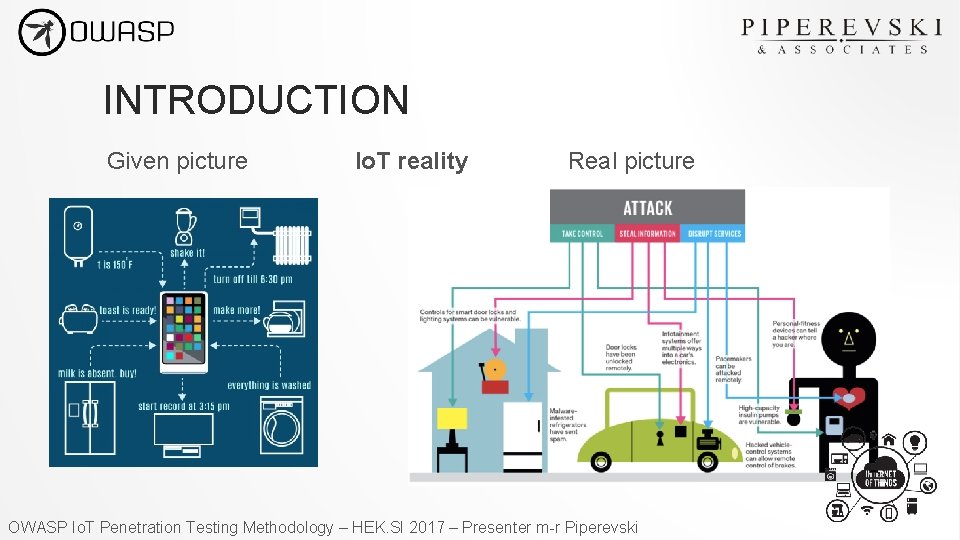
INTRODUCTION Given picture Io. T reality Real picture OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

WE NEED TO PROTECT Devices Humans and Cyborgs Processes OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

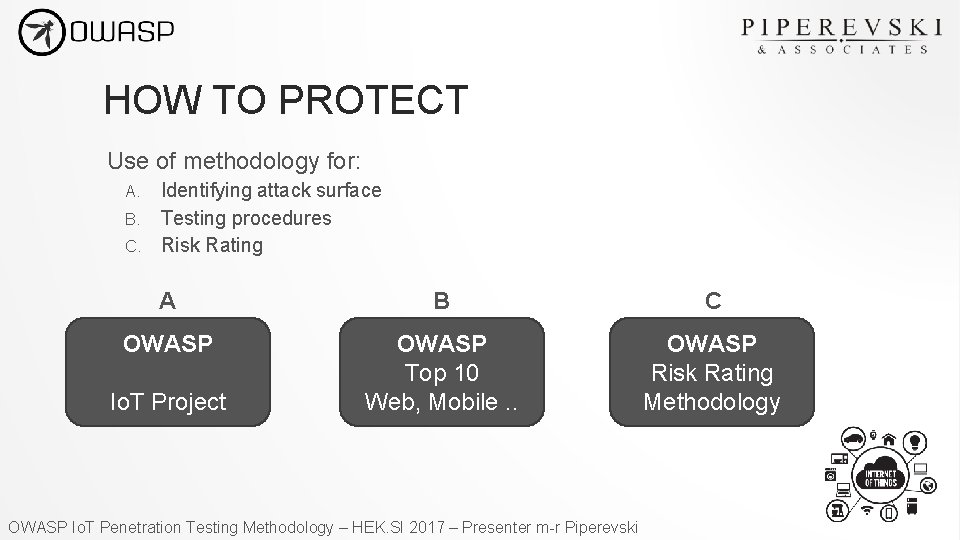
HOW TO PROTECT Use of methodology for: Identifying attack surface B. Testing procedures C. Risk Rating A. A B C OWASP Top 10 Web, Mobile. . OWASP Risk Rating Methodology Io. T Project OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

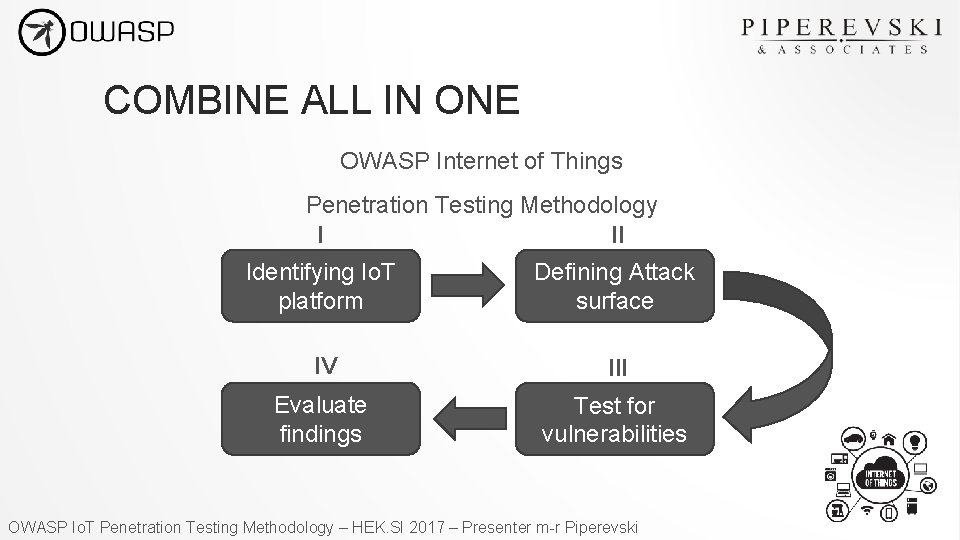
COMBINE ALL IN ONE OWASP Internet of Things Penetration Testing Methodology I II Identifying Io. T platform Defining Attack surface IV III Evaluate findings Test for vulnerabilities OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

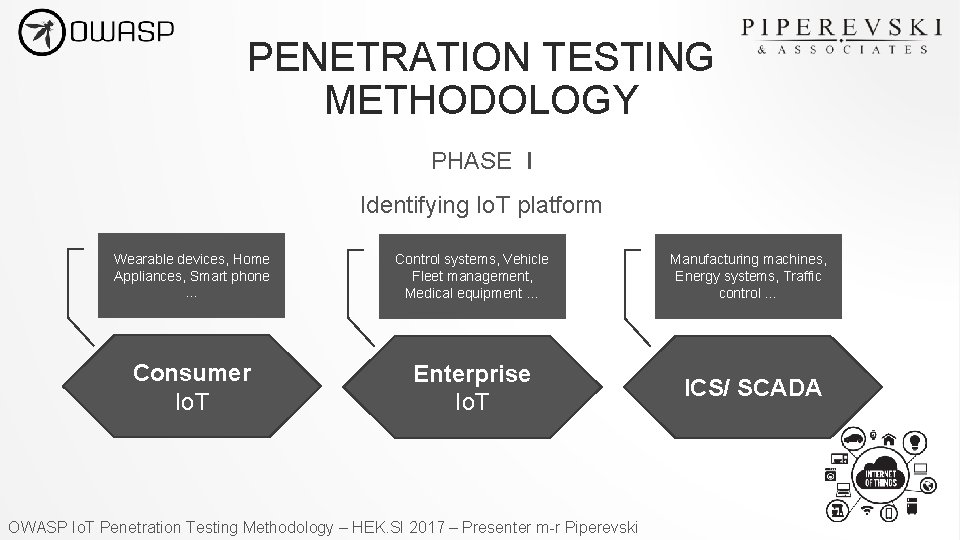
PENETRATION TESTING METHODOLOGY PHASE I Identifying Io. T platform Wearable devices, Home Appliances, Smart phone … Control systems, Vehicle Fleet management, Medical equipment … Consumer Io. T Enterprise Io. T OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski Manufacturing machines, Energy systems, Traffic control … ICS/ SCADA

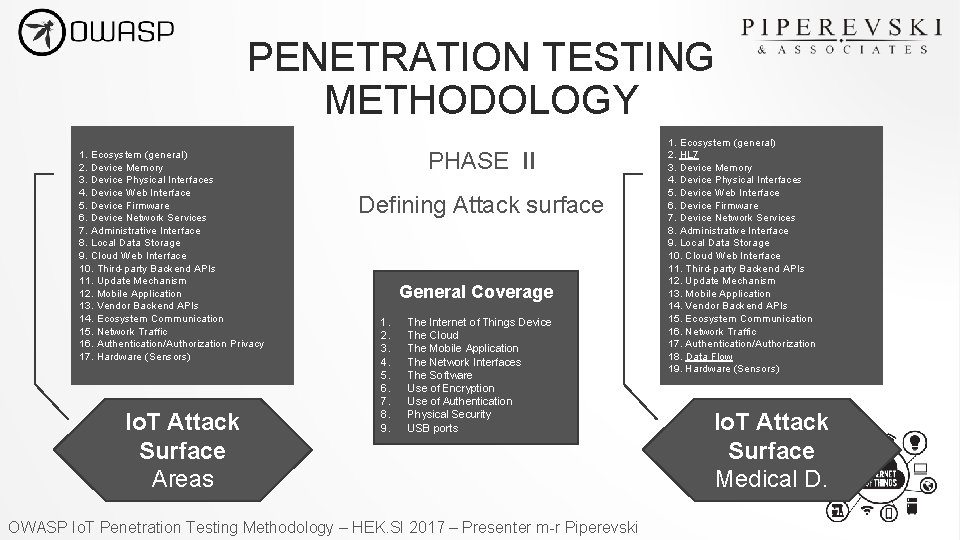
PENETRATION TESTING METHODOLOGY 1. Ecosystem (general) 2. Device Memory 3. Device Physical Interfaces 4. Device Web Interface 5. Device Firmware 6. Device Network Services 7. Administrative Interface 8. Local Data Storage 9. Cloud Web Interface 10. Third-party Backend APIs 11. Update Mechanism 12. Mobile Application 13. Vendor Backend APIs 14. Ecosystem Communication 15. Network Traffic 16. Authentication/Authorization Privacy 17. Hardware (Sensors) Io. T Attack Surface Areas PHASE II Defining Attack surface General Coverage 1. 2. 3. 4. 5. 6. 7. 8. 9. The Internet of Things Device The Cloud The Mobile Application The Network Interfaces The Software Use of Encryption Use of Authentication Physical Security USB ports OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski 1. Ecosystem (general) 2. HL 7 3. Device Memory 4. Device Physical Interfaces 5. Device Web Interface 6. Device Firmware 7. Device Network Services 8. Administrative Interface 9. Local Data Storage 10. Cloud Web Interface 11. Third-party Backend APIs 12. Update Mechanism 13. Mobile Application 14. Vendor Backend APIs 15. Ecosystem Communication 16. Network Traffic 17. Authentication/Authorization 18. Data Flow 19. Hardware (Sensors) Io. T Attack Surface Medical D.

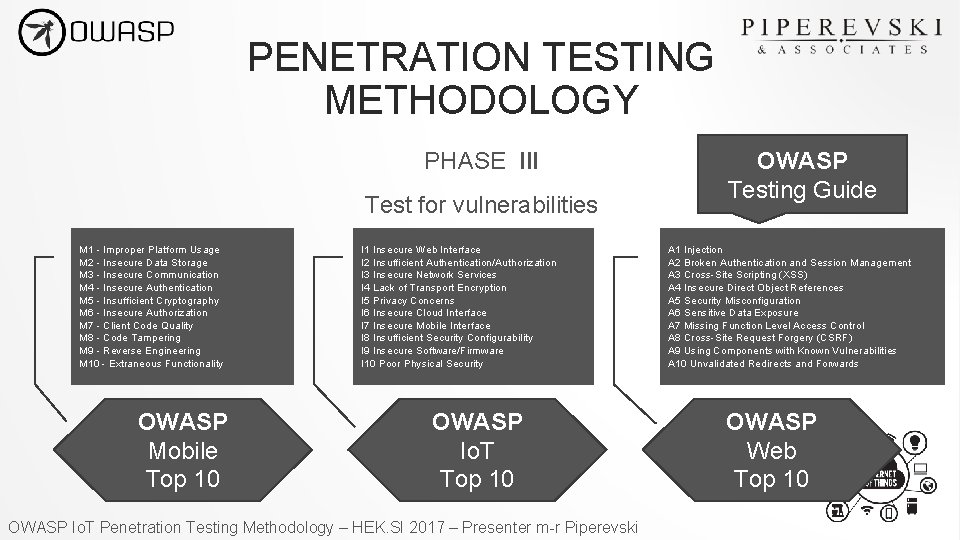
PENETRATION TESTING METHODOLOGY PHASE III Test for vulnerabilities M 1 - Improper Platform Usage M 2 - Insecure Data Storage M 3 - Insecure Communication M 4 - Insecure Authentication M 5 - Insufficient Cryptography M 6 - Insecure Authorization M 7 - Client Code Quality M 8 - Code Tampering M 9 - Reverse Engineering M 10 - Extraneous Functionality OWASP Mobile Top 10 I 1 Insecure Web Interface I 2 Insufficient Authentication/Authorization I 3 Insecure Network Services I 4 Lack of Transport Encryption I 5 Privacy Concerns I 6 Insecure Cloud Interface I 7 Insecure Mobile Interface I 8 Insufficient Security Configurability I 9 Insecure Software/Firmware I 10 Poor Physical Security OWASP Io. T Top 10 OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski OWASP Testing Guide A 1 Injection A 2 Broken Authentication and Session Management A 3 Cross-Site Scripting (XSS) A 4 Insecure Direct Object References A 5 Security Misconfiguration A 6 Sensitive Data Exposure A 7 Missing Function Level Access Control A 8 Cross-Site Request Forgery (CSRF) A 9 Using Components with Known Vulnerabilities A 10 Unvalidated Redirects and Forwards OWASP Web Top 10

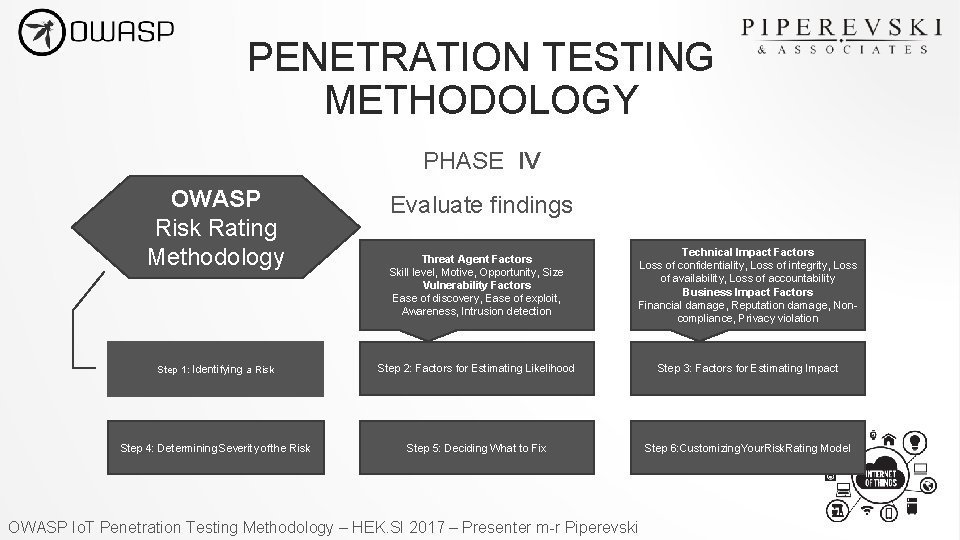
PENETRATION TESTING METHODOLOGY PHASE IV OWASP Risk Rating Methodology Evaluate findings Threat Agent Factors Skill level, Motive, Opportunity, Size Vulnerability Factors Ease of discovery, Ease of exploit, Awareness, Intrusion detection Technical Impact Factors Loss of confidentiality, Loss of integrity, Loss of availability, Loss of accountability Business Impact Factors Financial damage, Reputation damage, Noncompliance, Privacy violation Step 1: Identifying a Risk Step 2: Factors for Estimating Likelihood Step 3: Factors for Estimating Impact Step 4: Determining Severity of the Risk Step 5: Deciding What to Fix Step 6: Customizing Your. Risk Rating Model OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

PENETRATION TESTING METHODOLOGY Practical Example Testing Subject – Smart Lamp OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

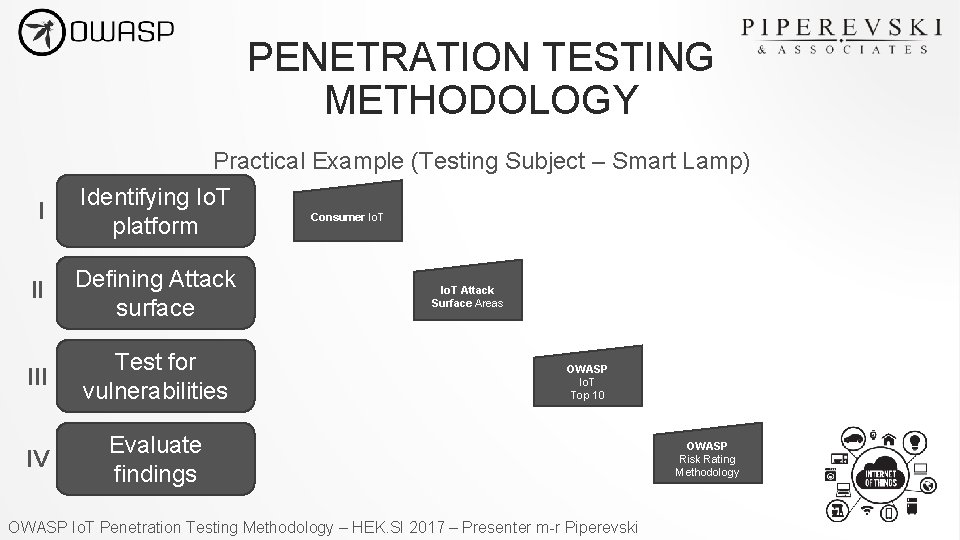
PENETRATION TESTING METHODOLOGY Practical Example (Testing Subject – Smart Lamp) I Identifying Io. T platform II Defining Attack surface III Test for vulnerabilities IV Evaluate findings Consumer Io. T Attack Surface Areas OWASP Io. T Top 10 OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski OWASP Risk Rating Methodology

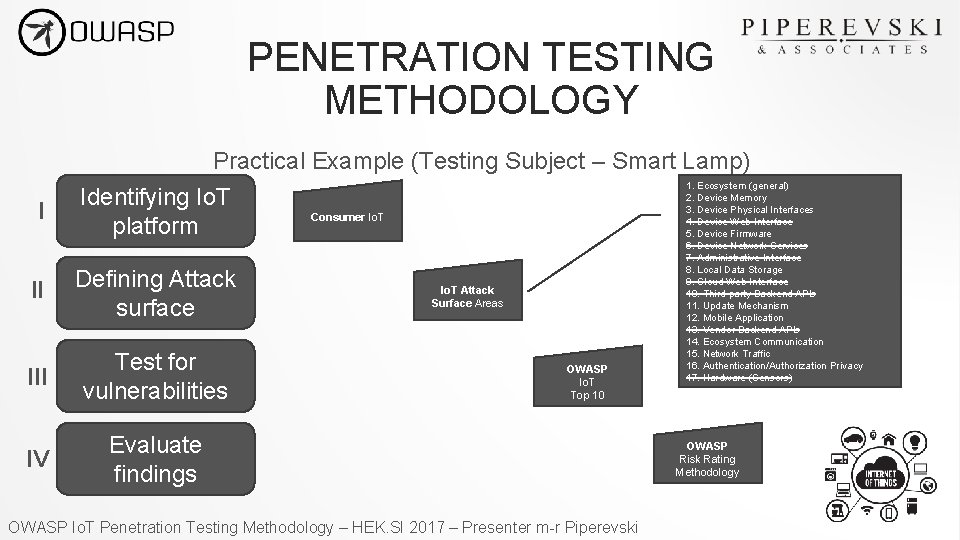
PENETRATION TESTING METHODOLOGY Practical Example (Testing Subject – Smart Lamp) I Identifying Io. T platform II Defining Attack surface III Test for vulnerabilities IV Evaluate findings Consumer Io. T Attack Surface Areas OWASP Io. T Top 10 OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski 1. Ecosystem (general) 2. Device Memory 3. Device Physical Interfaces 4. Device Web Interface 5. Device Firmware 6. Device Network Services 7. Administrative Interface 8. Local Data Storage 9. Cloud Web Interface 10. Third-party Backend APIs 11. Update Mechanism 12. Mobile Application 13. Vendor Backend APIs 14. Ecosystem Communication 15. Network Traffic 16. Authentication/Authorization Privacy 17. Hardware (Sensors) OWASP Risk Rating Methodology

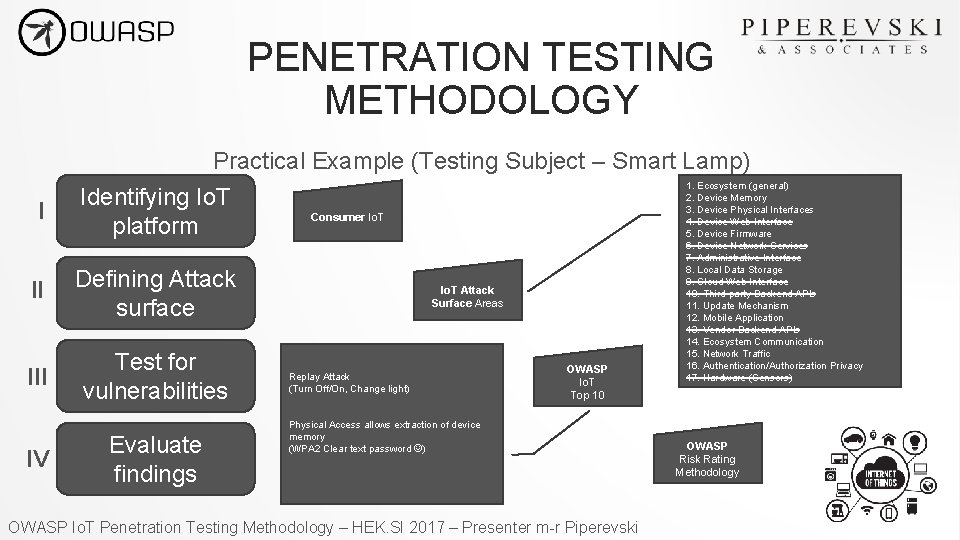
PENETRATION TESTING METHODOLOGY Practical Example (Testing Subject – Smart Lamp) I Identifying Io. T platform II Defining Attack surface III Test for vulnerabilities IV Evaluate findings Consumer Io. T Attack Surface Areas Replay Attack (Turn Off/On, Change light) OWASP Io. T Top 10 Physical Access allows extraction of device memory (WPA 2 Clear text password ) OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski 1. Ecosystem (general) 2. Device Memory 3. Device Physical Interfaces 4. Device Web Interface 5. Device Firmware 6. Device Network Services 7. Administrative Interface 8. Local Data Storage 9. Cloud Web Interface 10. Third-party Backend APIs 11. Update Mechanism 12. Mobile Application 13. Vendor Backend APIs 14. Ecosystem Communication 15. Network Traffic 16. Authentication/Authorization Privacy 17. Hardware (Sensors) OWASP Risk Rating Methodology

PENETRATION TESTING METHODOLOGY Replay Attack Physical Access allows extraction of device memory Skill level network and programming skills Security penetration skills Motive possible reward Opportunity Some access or resources required special access or resources required Size Anonymous Internet users Authenticated users Ease of discovery easy difficult Ease of exploit easy difficult Awareness Unknown Intrusion detection not logged Loss of confidentiality Minimal non-sensitive data disclosed minimal critical data disclosed Loss of integrity extensive seriously corrupt data Loss of availability all services completely lost Loss of accountability completely anonymous Financial damage minor effect on annual profit Reputation damage Minimal damage Non-compliance Minor violation Privacy violation One individual Threat Agent Factors Vulnerability Factors Technical Impact Factors Business Impact Factors OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski Practical Example (Testing Subject – Smart Lamp)

PENETRATION TESTING METHODOLOGY Practical Example (Testing Subject – Smart Lamp) At the END. . only this information is important for the Client Risk Replay Attack Physical Access allows extraction of device memory Low OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

QUESTIONS … IDEAS … QUESTIONS AGAIN !!! OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski

OWASP Io. T Penetration Testing Methodology – HEK. SI 2017 – Presenter m-r Piperevski