Overview q Modern symmetrickey cryptosystems o Data Encryption
























- Slides: 54

Overview q Modern symmetric-key cryptosystems o Data Encryption Standard (DES) § Adopted in 1976 § Block size = 64 bits § Key length = 56 bits o Advanced Encryption Standard (AES) § Adopted in 2000 § Block sizes = 128, 192, or 256 bits § Key lengths = 128, 192, or 256 bits Chapter 3 Symmetric Key Cryptosystems 1

DES - History q 1973: NBS (now NIST) solicits proposals for crypto algorithm which: o Provides a high level of security o Completely specified and easy to understand o Is available royalty-free o Is efficient Chapter 3 Symmetric Key Cryptosystems 2

DES – History (cont) q 1974 o IBM submits variant of Lucifer algorithm o NBS asks NSA for comments on the algorithm o NSA likes the algorithm with modifications § Key size reduced from 128 to 56 bits § Minor changes in details of the algorithm q 1976 o DES approved (unclassified communications) o To be reviewed every five years Chapter 3 Symmetric Key Cryptosystems 3

DES – History (cont) q 1983: NBS recertifies DES q 1987: NBS recertifies DES q 1988: NBS becomes NIST q 1993: NIST recertifies DES q 1998: NIST begins AES competition Chapter 3 Symmetric Key Cryptosystems 4

DES - Overview q Adopted as U. S. government standard in 1976 q Block cipher, symmetric key o 64 -bit block size, 56 -bit key o Simple algorithm Chapter 3 Symmetric Key Cryptosystems 5

DES - Keys q Any 56 -bit string can be a DES key q There are 256 keys o 72, 057, 594, 037, 927, 936 DES keys q Test one trillion keys per second o 2 hours to find the key q. A very small number of “weak keys” Chapter 3 Symmetric Key Cryptosystems 6

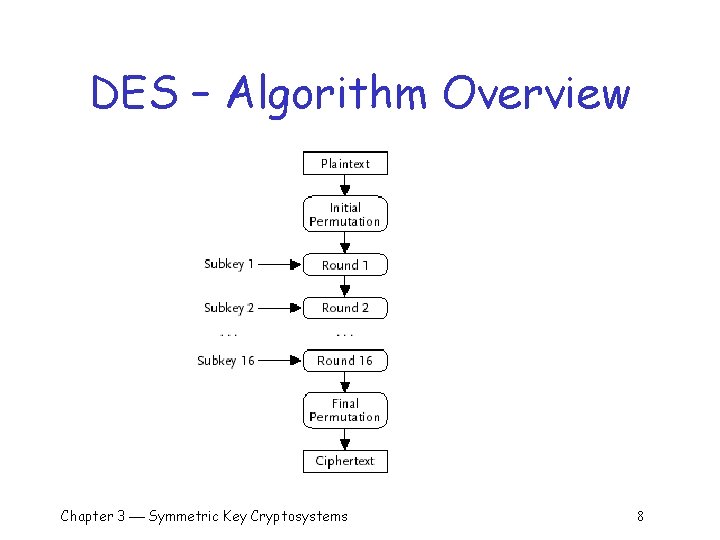
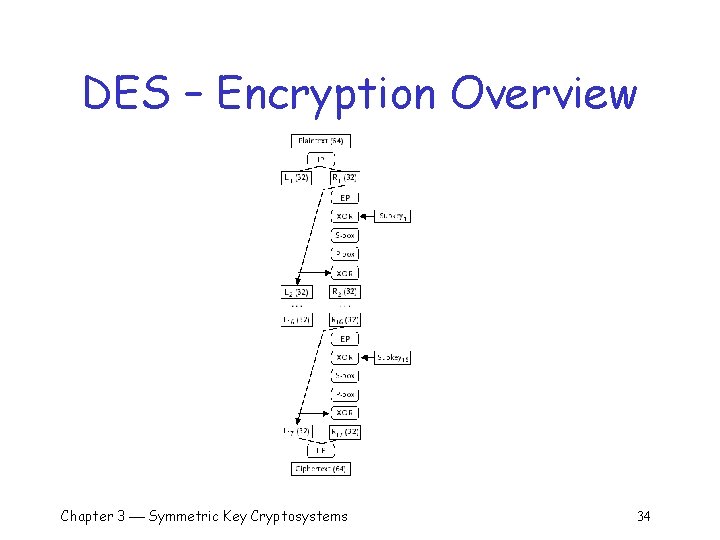
DES – The Algorithm q To encrypt a 64 -bit plaintext block q An initial permutation o o 16 rounds of substitution, transposition 48 -bit subkey added to each round, Subkeys derived from 56 -bit DES key Final permutation Chapter 3 Symmetric Key Cryptosystems 7

DES – Algorithm Overview Chapter 3 Symmetric Key Cryptosystems 8

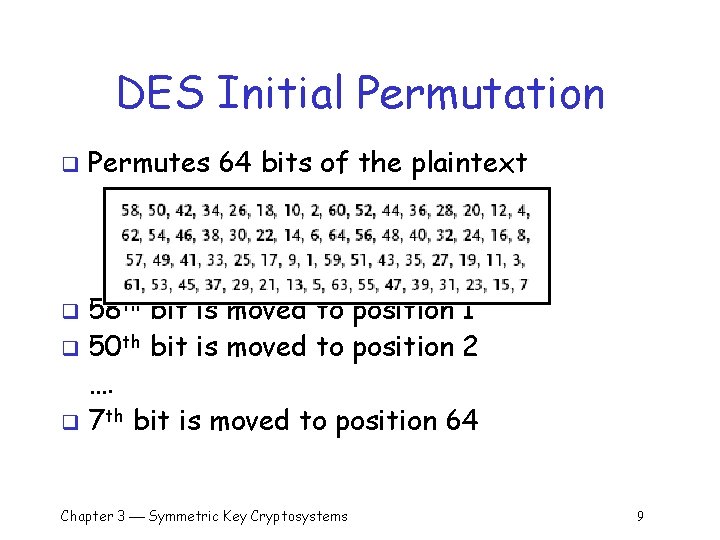
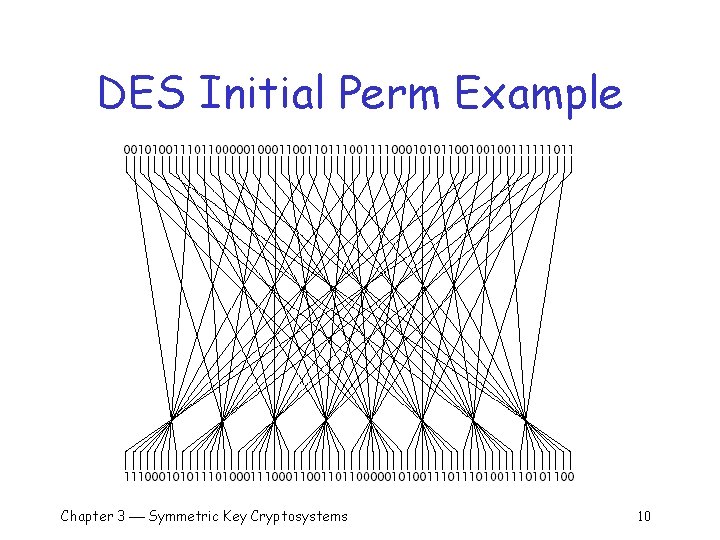
DES Initial Permutation q Permutes 64 bits of the plaintext 58 th bit is moved to position 1 q 50 th bit is moved to position 2 …. q 7 th bit is moved to position 64 q Chapter 3 Symmetric Key Cryptosystems 9

DES Initial Perm Example Chapter 3 Symmetric Key Cryptosystems 10

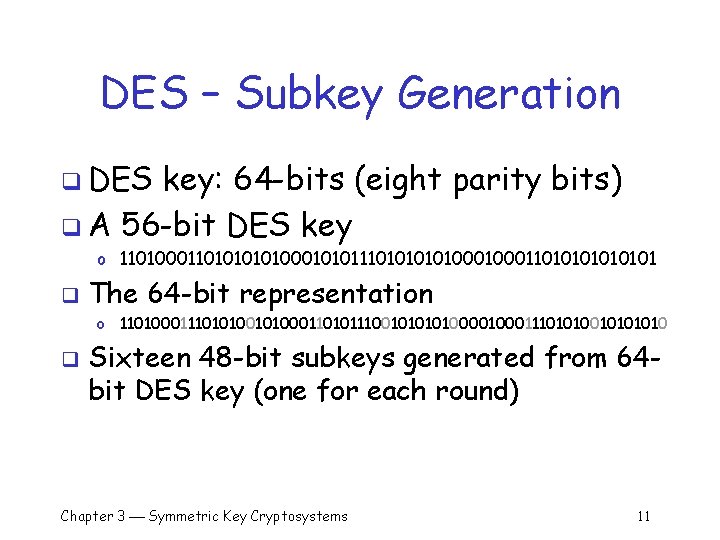
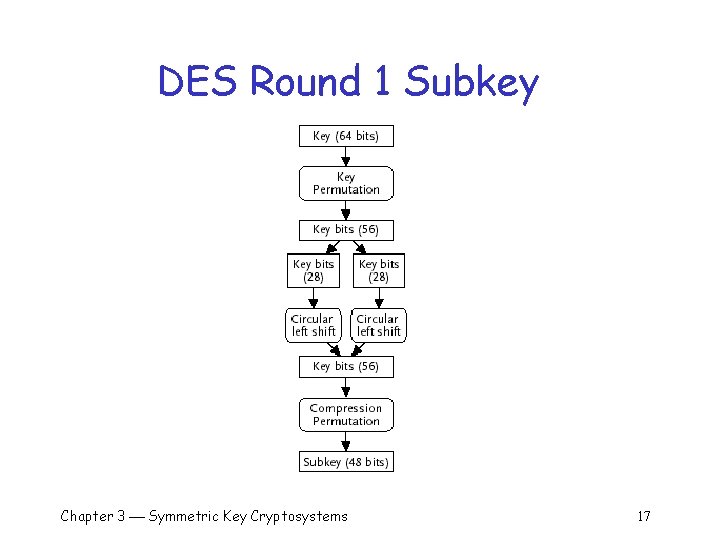
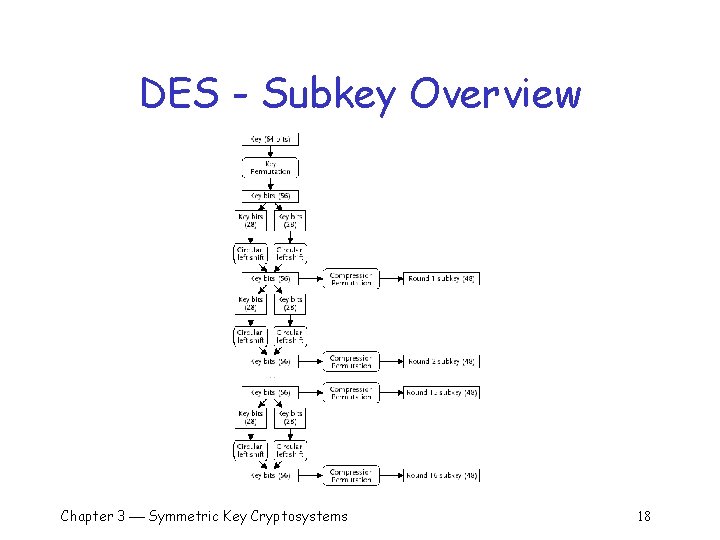
DES – Subkey Generation q DES key: 64 -bits (eight parity bits) q A 56 -bit DES key o 11010001101010001010111010100011010101 q The 64 -bit representation o 1101000111010100011010111001010000111010101010 q Sixteen 48 -bit subkeys generated from 64 bit DES key (one for each round) Chapter 3 Symmetric Key Cryptosystems 11

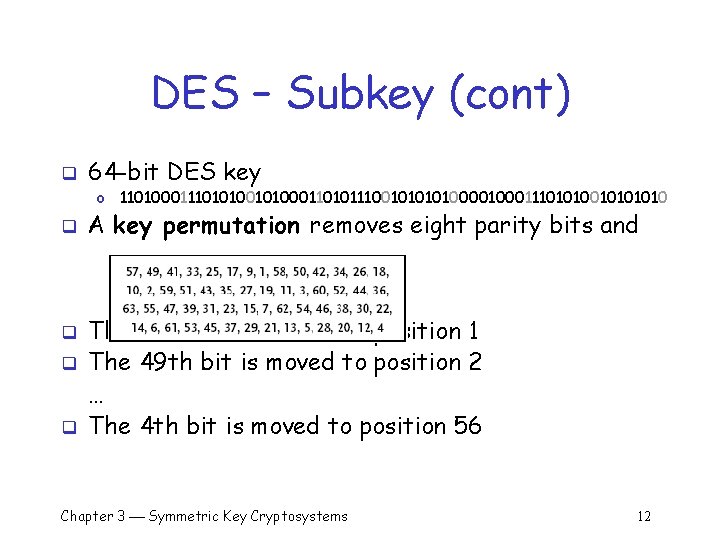
DES – Subkey (cont) q 64 -bit DES key o 1101000111010100011010111001010000111010101010 q q A key permutation removes eight parity bits and The 57 th bit is moved to position 1 The 49 th bit is moved to position 2 … The 4 th bit is moved to position 56 Chapter 3 Symmetric Key Cryptosystems 12

DES Key Perm Example q 64 -bit “key” to 56 -bit DES key Chapter 3 Symmetric Key Cryptosystems 13

DES – Subkey Gen (cont) 56 key bits (after permutation) divided into two 28 -bit halves q Each half circularly shifted left by one bit (rounds 1, 2, 9 and 16) or 2 bits (all other rounds) q Halves recombined into 56 bit string q Chapter 3 Symmetric Key Cryptosystems 14

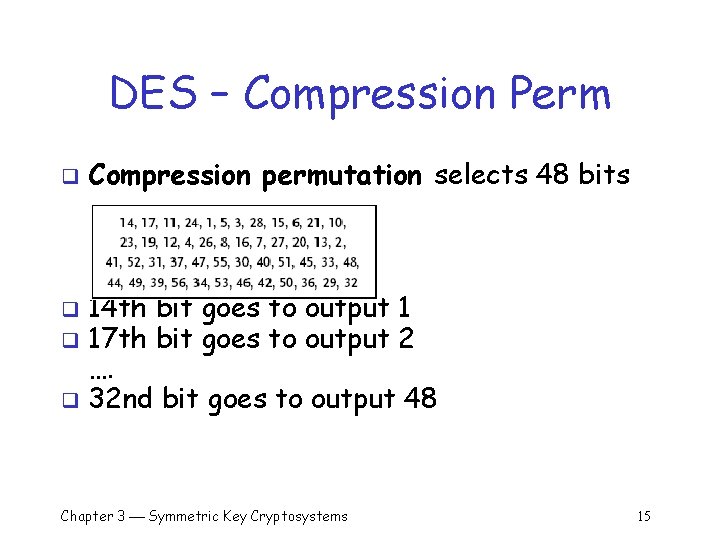
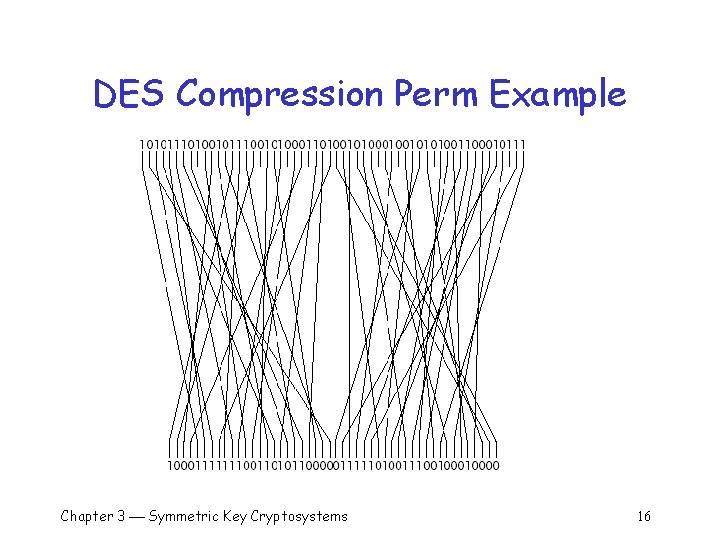
DES – Compression Perm q Compression permutation selects 48 bits 14 th bit goes to output 1 17 th bit goes to output 2 …. q 32 nd bit goes to output 48 q q Chapter 3 Symmetric Key Cryptosystems 15

DES Compression Perm Example Chapter 3 Symmetric Key Cryptosystems 16

DES Round 1 Subkey Chapter 3 Symmetric Key Cryptosystems 17

DES - Subkey Overview Chapter 3 Symmetric Key Cryptosystems 18

DES – Rounds Each of 16 rounds takes 64 -bit block of input to 64 -bit block of output q The output from initial perm is input to round one q Round one output is input to round two q Round two output is input to round three q Round 16 output is ciphertext q Chapter 3 Symmetric Key Cryptosystems 19

DES – Round 1 Input block (64) L 1 (32) R 1 (32) EP XOR Subkey 1 S-box P-box XOR L 2 (32) R 2 (32) Output block (64) Chapter 3 Symmetric Key Cryptosystems 20

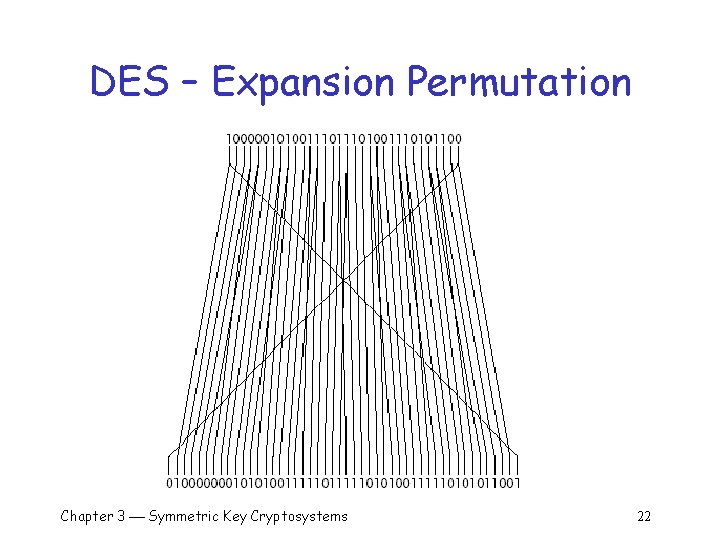
DES Rounds 64 -bit input divided into two 32 -bit halves q Right half sent through expansion perm which produces 48 bits by q o Rearranging the input bits o Repeating some input bits more than once Chapter 3 Symmetric Key Cryptosystems 21

DES – Expansion Permutation Chapter 3 Symmetric Key Cryptosystems 22

DES – XOR Operation q XOR is applied to the 48 -bit output of expansion perm and subkey q The resulting 48 -bits go to S-boxes Chapter 3 Symmetric Key Cryptosystems 23

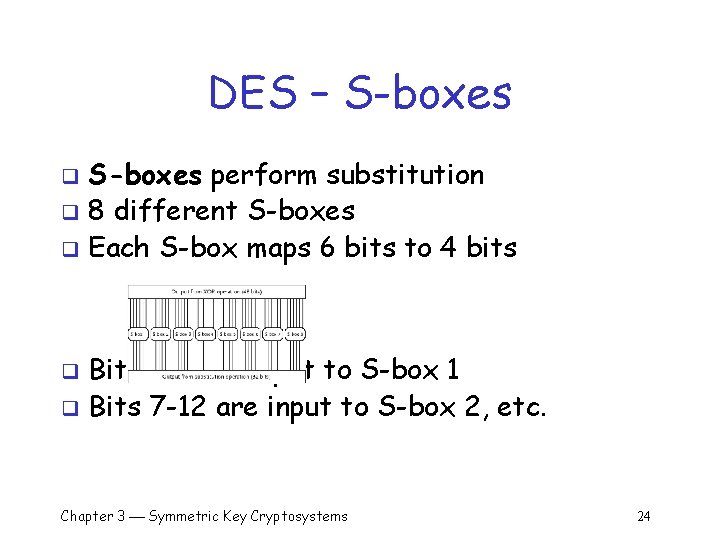
DES – S-boxes perform substitution q 8 different S-boxes q Each S-box maps 6 bits to 4 bits q Bits 1 -6 are input to S-box 1 q Bits 7 -12 are input to S-box 2, etc. q Chapter 3 Symmetric Key Cryptosystems 24

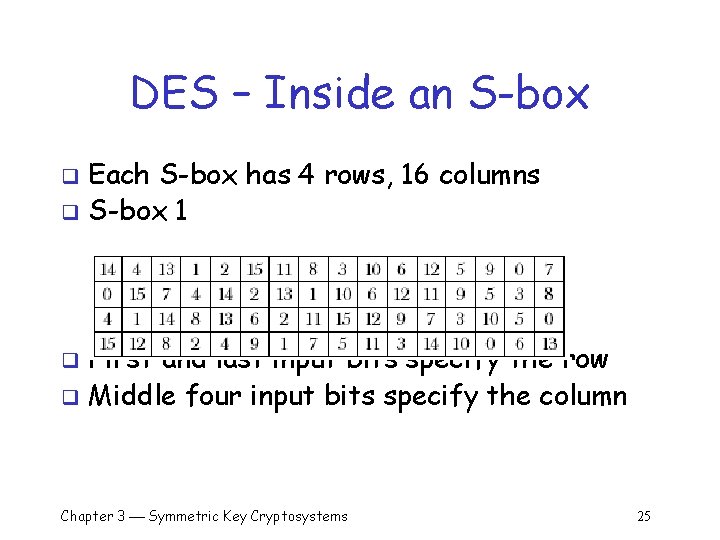
DES – Inside an S-box Each S-box has 4 rows, 16 columns q S-box 1 q First and last input bits specify the row q Middle four input bits specify the column q Chapter 3 Symmetric Key Cryptosystems 25

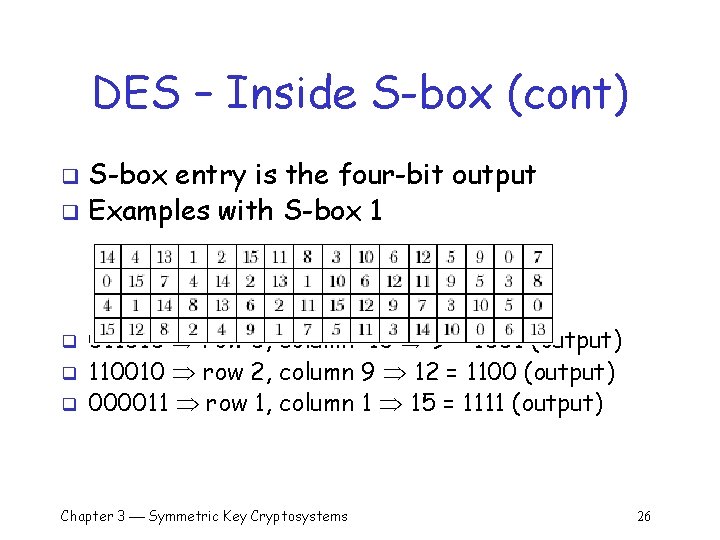
DES – Inside S-box (cont) S-box entry is the four-bit output q Examples with S-box 1 q q 011010 row 0, column 13 9 = 1001 (output) 110010 row 2, column 9 12 = 1100 (output) 000011 row 1, column 1 15 = 1111 (output) Chapter 3 Symmetric Key Cryptosystems 26

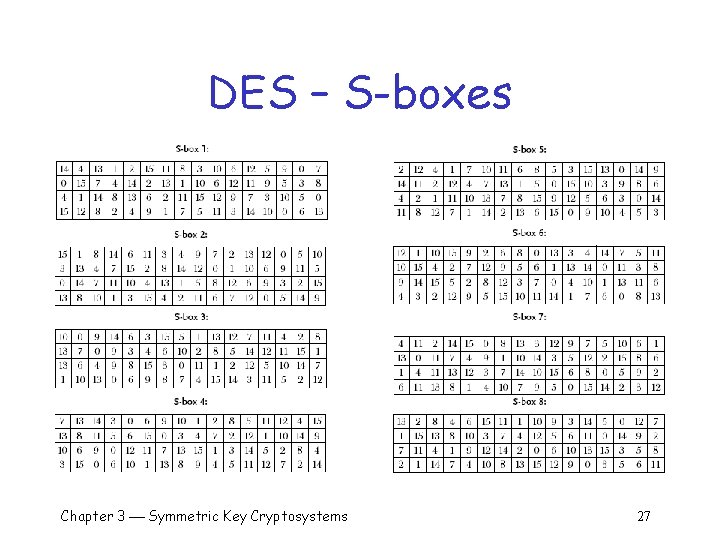
DES – S-boxes Chapter 3 Symmetric Key Cryptosystems 27

DES – S-boxes Example Chapter 3 Symmetric Key Cryptosystems 28

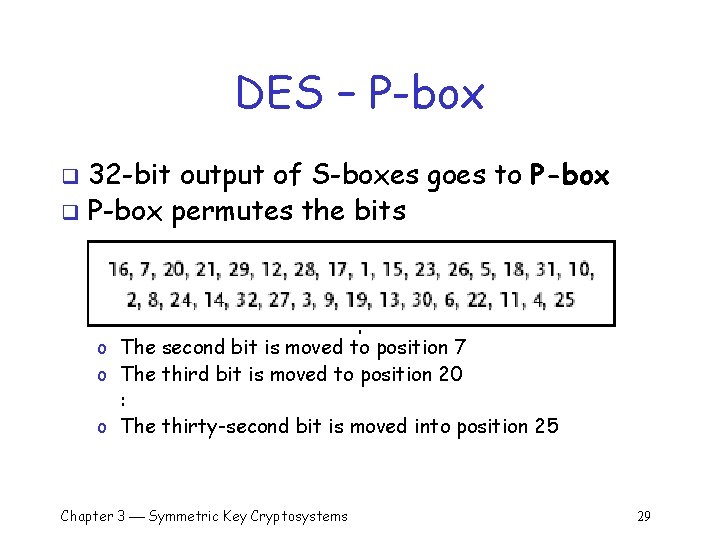
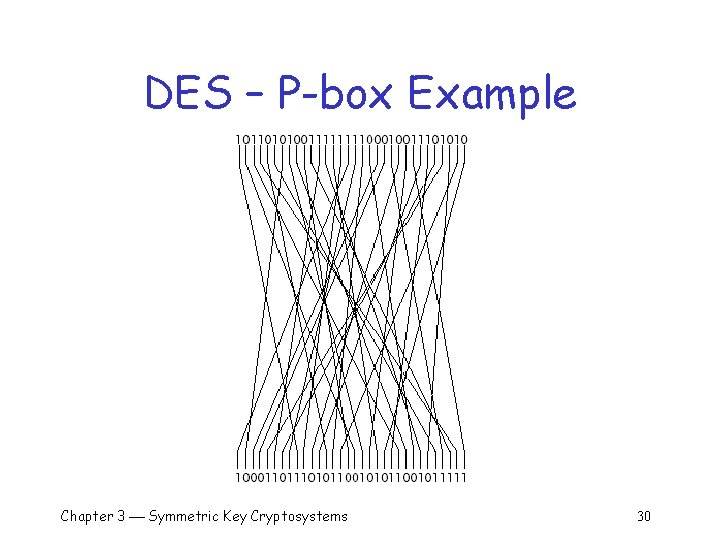
DES – P-box 32 -bit output of S-boxes goes to P-box q P-box permutes the bits q o The first bit is moved to position 16 o The second bit is moved to position 7 o The third bit is moved to position 20 : o The thirty-second bit is moved into position 25 Chapter 3 Symmetric Key Cryptosystems 29

DES – P-box Example Chapter 3 Symmetric Key Cryptosystems 30

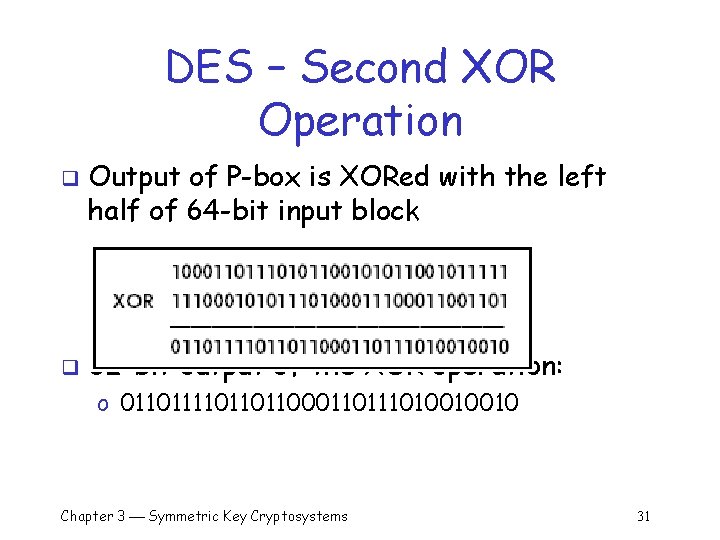
DES – Second XOR Operation q q Output of P-box is XORed with the left half of 64 -bit input block 32 -bit output of the XOR operation: o 01101101100011010010010 Chapter 3 Symmetric Key Cryptosystems 31

DES – Rounds q 64 -bit output from round 1 is input for round 2 q Output from round 2 is input for round 3 : q Output from round 16 is passed through a final permutation Chapter 3 Symmetric Key Cryptosystems 32

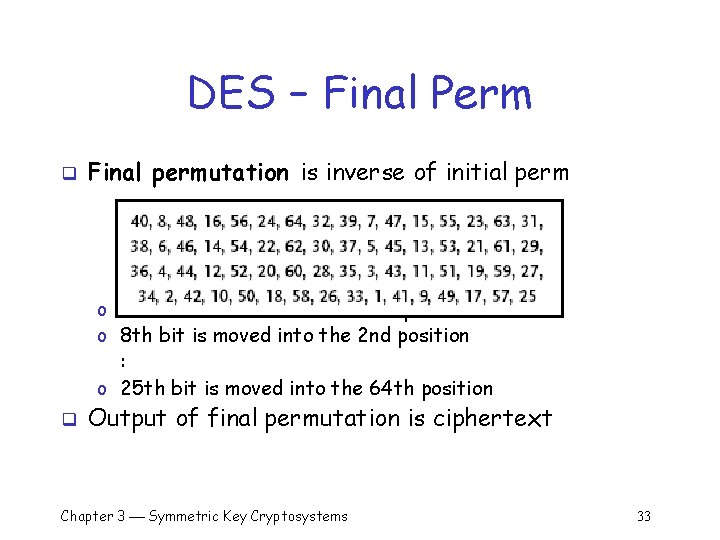
DES – Final Perm q Final permutation is inverse of initial perm o 40 th bit is moved into the 1 st position o 8 th bit is moved into the 2 nd position : o 25 th bit is moved into the 64 th position q Output of final permutation is ciphertext Chapter 3 Symmetric Key Cryptosystems 33

DES – Encryption Overview Chapter 3 Symmetric Key Cryptosystems 34

DES - Decryption q Same algorithm and key as encryption q Subkeys are applied in opposite order o Subkey 16 used in first round o Subkey 15 used in second round : o Subkey 1 used in 16 th round Chapter 3 Symmetric Key Cryptosystems 35

DES - Summary DES still widely used q 56 -bit key q o 1998, EFF built $220, 000 DES cracker, requires about 4 days/key DES also important historically q Late 90’s AES competition produced several strong crypto algorithms q Chapter 3 Symmetric Key Cryptosystems 36

AES - History q q 1997: NIST requests proposals for a new Advanced Encryption Standard (AES) to replace DES NIST required that the algorithm be: o o o q A symmetric-key cryptosystem A block cipher Capable of supporting a block size of 128 bits Capable of supporting key lengths of 128, 192, and 256 bits Available on a worldwide, non-exclusive, royalty-free basis Evaluation criteria: o Security - soundness of the mathematical basis and the results of analysis by the research community o Computational efficiency, memory requirements, flexibility, and simplicity Chapter 3 Symmetric Key Cryptosystems 37

AES – Round 1 of the Competition q NIST selects 15 submissions for evaluation: o o o o CAST-256 (Entrust Technologies, Inc. ) Crypton (Future Systems, Inc. ) DEAL (Richard Outerbridge, Lars Knudsen) DFC (Centre National pour la Recherche Scientifique—Ecole Normale Superieure) E 2 (Nippon Telegraph and Telephone Corporation) Frog (Tec. Apro Internacional S. A. ) HPC (Rich Schroeppel) Loki 97 (Lawrie Brown, Josef Pieprzyk, Jennifer Seberry) Magenta (Deutsche Telekom AG) MARS (IBM) RC 6 (RSA Laboratories) Rijndael (Joan Daemen, Vincent Rijmen) SAFER+ (Cylink Corporation) Serpent (Ross Anderson, Eli Biham, Lars Knudsen) Twofish (Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson) Chapter 3 Symmetric Key Cryptosystems 38

AES – Round 1 Results q After eight months of analysis and public comment, NIST: o Eliminated DEAL, Frog, HPC, Loki 97, and Magenta § Had what NIST considered major security flaws § Were among the slowest algorithms submitted o Eliminated Crypton, DFC, E 2, and SAFER+ § Had what NIST considered minor security flaws § Had unimpressive characteristics on the other evaluation criteria o Eliminated CAST-256 § Had mediocre speed and large ROM requirements q Five candidates, MARS, RC 6, Rijndael, Serpent, and Twofish, advanced to the second round Chapter 3 Symmetric Key Cryptosystems 39

AES – Results q q Analysis and public comment on the five finalists October 2000: NIST: o Eliminates MARS § High security margin o Eliminates RC 6 § Adequate security margin, fast encryption and decryption on 32 -bit platforms o Eliminates Serpent § High security margin o Eliminates Twofish § High security margin o Selects Rijndael § Adequate security margin, fast encryption, decryption, and key setup speeds, low RAM and ROM requirements Chapter 3 Symmetric Key Cryptosystems 40

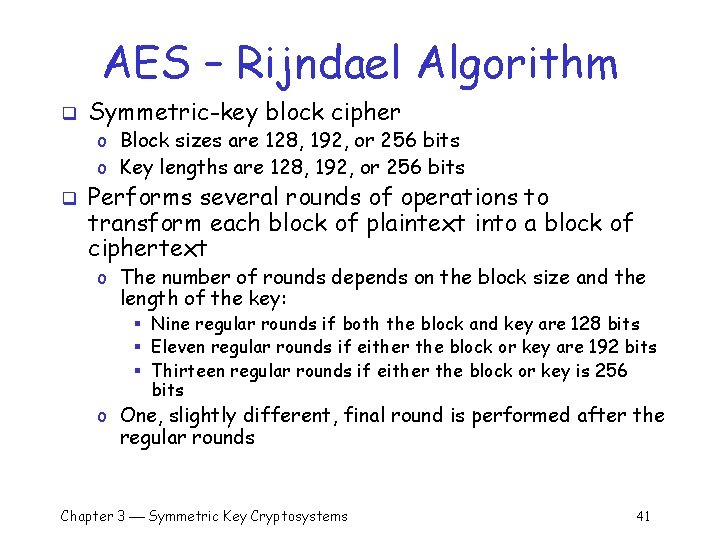
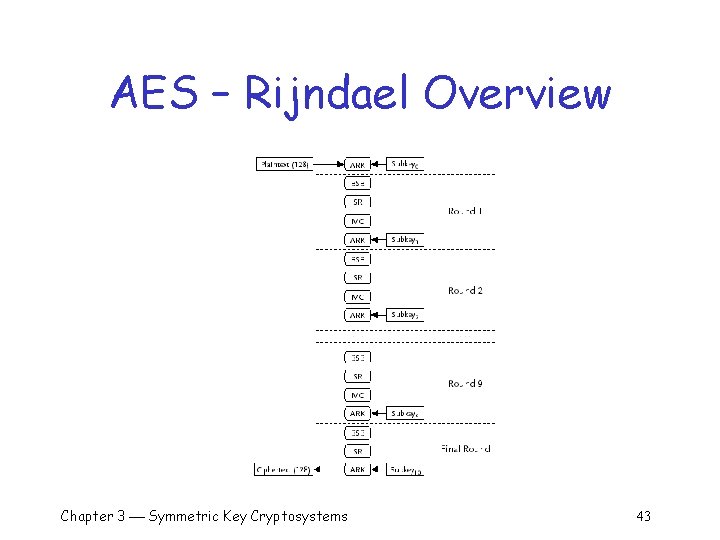
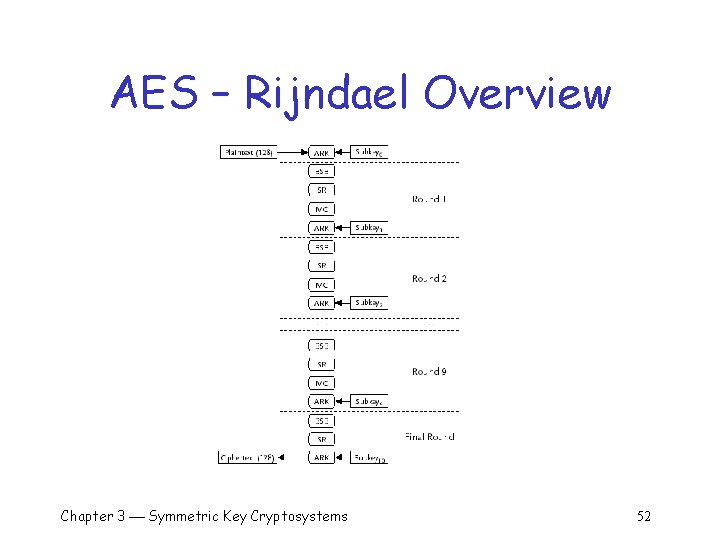
AES – Rijndael Algorithm q Symmetric-key block cipher o Block sizes are 128, 192, or 256 bits o Key lengths are 128, 192, or 256 bits q Performs several rounds of operations to transform each block of plaintext into a block of ciphertext o The number of rounds depends on the block size and the length of the key: § Nine regular rounds if both the block and key are 128 bits § Eleven regular rounds if either the block or key are 192 bits § Thirteen regular rounds if either the block or key is 256 bits o One, slightly different, final round is performed after the regular rounds Chapter 3 Symmetric Key Cryptosystems 41

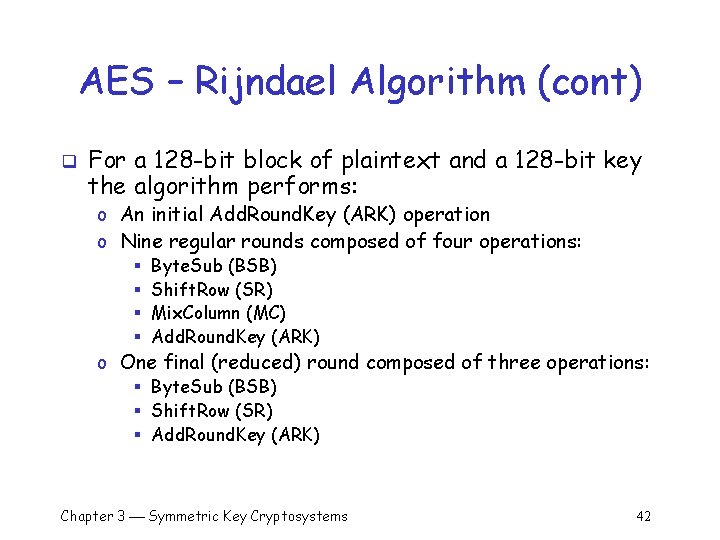
AES – Rijndael Algorithm (cont) q For a 128 -bit block of plaintext and a 128 -bit key the algorithm performs: o An initial Add. Round. Key (ARK) operation o Nine regular rounds composed of four operations: § § Byte. Sub (BSB) Shift. Row (SR) Mix. Column (MC) Add. Round. Key (ARK) o One final (reduced) round composed of three operations: § Byte. Sub (BSB) § Shift. Row (SR) § Add. Round. Key (ARK) Chapter 3 Symmetric Key Cryptosystems 42

AES – Rijndael Overview Chapter 3 Symmetric Key Cryptosystems 43

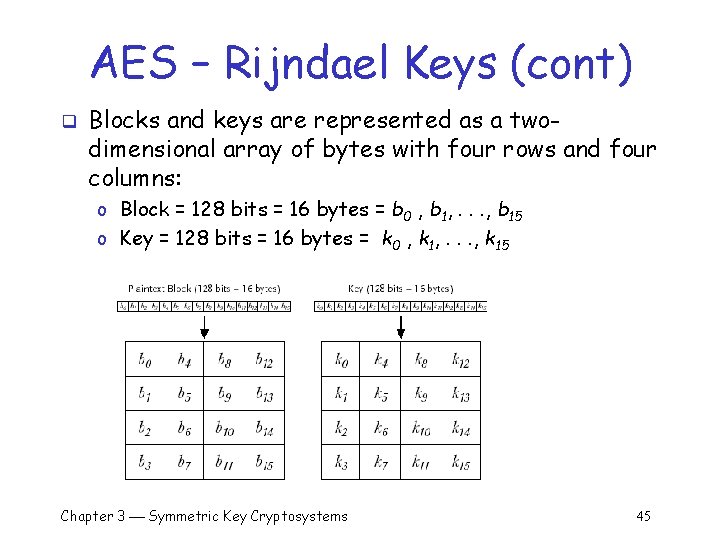
AES – Rijndael Keys q q Keys are expressed as 128 -bit (or bigger) quantities Keyspace contains at least 2128 elements: o 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 4 56 q Exhaustive search at one trillion keys per second takes: o 1 x 1019 years (the universe is thought to be about 1 x 1010 years old) Chapter 3 Symmetric Key Cryptosystems 44

AES – Rijndael Keys (cont) q Blocks and keys are represented as a twodimensional array of bytes with four rows and four columns: o Block = 128 bits = 16 bytes = b 0 , b 1, . . . , b 15 o Key = 128 bits = 16 bytes = k 0 , k 1, . . . , k 15 Chapter 3 Symmetric Key Cryptosystems 45

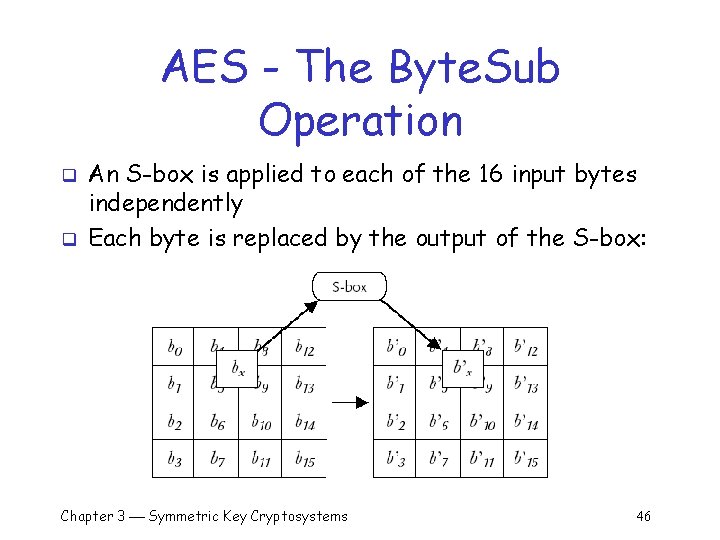
AES - The Byte. Sub Operation q q An S-box is applied to each of the 16 input bytes independently Each byte is replaced by the output of the S-box: Chapter 3 Symmetric Key Cryptosystems 46

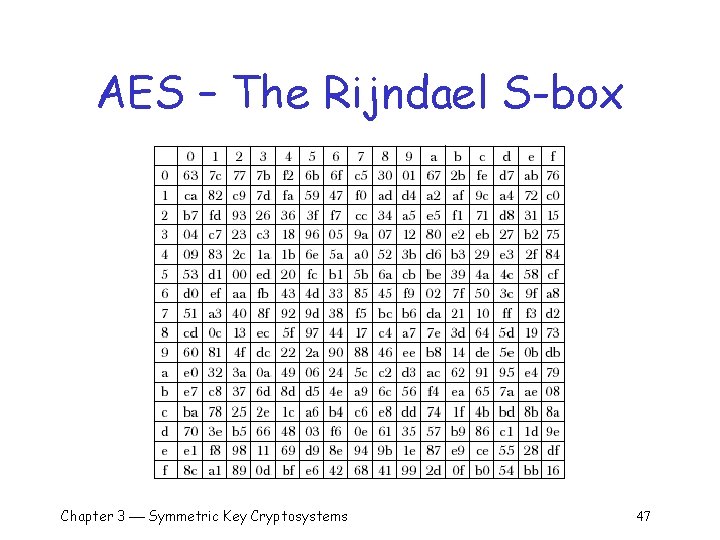
AES – The Rijndael S-box Chapter 3 Symmetric Key Cryptosystems 47

AES – The Rijndael S-box (cont) q q The input to the S-box is one byte: Example 1: o b 0 = 01101011 (binary) = 6 b (hex) o b’ 0 = row 6, column b = 7 f (hex) = 01111111 (binary) q Example 2: o b 1 = 00001000 (binary) = 08 (hex) o b’ 1 = row 0, column 8 = 30 (hex) = 00110000 (binary) q Example 3: o b 2 = 11111001 (binary) = f 9 (hex) o b’ 2 = row f, column 9 = 99 (hex) = 1001 (binary) Chapter 3 Symmetric Key Cryptosystems 48

AES - Shift. Row Operation q Each row of the input is circularly left shifted: o o First row by zero places Second row by one place Third row by two places Fourth row by three places Chapter 3 Symmetric Key Cryptosystems 49

AES - The Mix. Column Operation q The four bytes in each input column are replaced with four new bytes: Chapter 3 Symmetric Key Cryptosystems 50

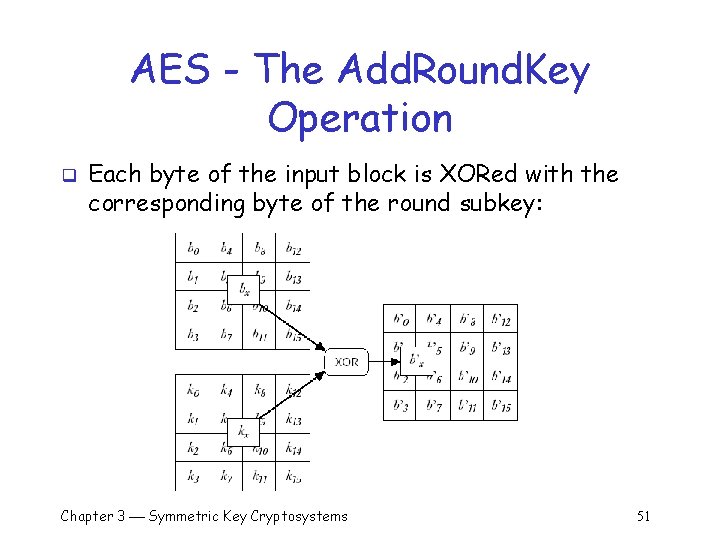
AES - The Add. Round. Key Operation q Each byte of the input block is XORed with the corresponding byte of the round subkey: Chapter 3 Symmetric Key Cryptosystems 51

AES – Rijndael Overview Chapter 3 Symmetric Key Cryptosystems 52

AES Summary q q The research community participated very actively and expertly in the design and evaluation of the candidate algorithms The AES selection process served to raise public awareness of cryptography and its importance The AES algorithm is starting to be widely used The AES should offer useful cryptographic protection for at least the next few decades Chapter 3 Symmetric Key Cryptosystems 53

Summary q DES (56 -bit keys): Each 64 -bit block of plaintext goes through: o Initial permutation o Sixteen rounds of substitution and transposition operations o Final permutation q AES (128 -bit keys): Each 128 -bit block of plaintext goes through: o An initial Add. Round. Key (ARK) operation o Nine rounds of operations (BSB, SR, MC, ARK) o One final (reduced) round Chapter 3 Symmetric Key Cryptosystems 54