Overview of the DES A block cipher encrypts

Overview of the DES • A block cipher: – encrypts blocks of 64 bits using a 64 bit key – outputs 64 bits of ciphertext • A product cipher – basic unit is the bit – performs both substitution and transposition (permutation) on the bits • Cipher consists of 16 rounds (iterations), each with a 48 -bit round key generated from the 64 -bit key

Generation of Round Keys • Round keys are 48 bits each 2

Encipherment 3

The f Function

• S-Box – There are eight S-Box, each maps 6 -bit input to 4 -bit output – Each S-Box is a look-up table – This is the only non-linear step in DES and contributes the most to its safety • P-Box – A permutation

Controversy • Considered too weak – Diffie, Hellman said “in a few years technology would allow DES to be broken in days” • DES Challenge organized by RSA • In 1997, solved in 96 days; 41 days in early 1998; 56 hours in late 1998; 22 hours in Jan 1999 • http: //w 2. eff. org/Privacy/Crypto_misc/DESC racker/HTML/19990119_deschallenge 3. html – Design decisions not public • S-boxes may have backdoors

Undesirable Properties • 4 weak keys – They are their own inverses • 12 semi-weak keys – Each has another semi-weak key as inverse • Complementation property – DESk(m) = c DESk (m ) = c • S-boxes exhibit irregular properties – Distribution of odd, even numbers non-random – Outputs of fourth box depends on input to third box

• Number of rounds – After 5 rounds, every cipher bit is impacted by every plaintext bit and key bit – After 8 rounds, cipher text is already a random function – When the number of rounds is 16 or more, brute force attack will be the most efficient attack for known plaintext attack – So NSA knows a lot when it fixes the DES

Differential Cryptanalysis • A chosen ciphertext attack – Requires 247 (plaintext, ciphertext) pairs • Revealed several properties – Small changes in S-boxes reduce the number of (plaintext, ciphertext) pairs needed – Making every bit of the round keys independent does not impede attack • Linear cryptanalysis improves result – Requires 243 (plaintext, ciphertext) pairs

• Multiple encryption of DES – Before we study multiple DES, a question must be answered. Is DES a group? EK 2( EK 1(P)) = EK 3(P) – It is proven that DES is not a group in 1993

• Double encryption – Encrypt the plaintext twice with different keys C = EK 2(EK 1(P)), P = DK 1(DK 2(C)) – If DES uses 56 bit key, can we get 112 bit key security? – Meet-in-the-middle attack makes the safety to 57 bits instead of 112 bit – Tradeoff storage and search for computation – Double encryption will not achieve your goal
DES Modes • Electronic Code Book Mode (ECB) – Encipher each block independently • Cipher Block Chaining Mode (CBC) – Xor each plaintext block with previous ciphertext block – Requires an initialization vector for the first one – The initialization vector can be made public
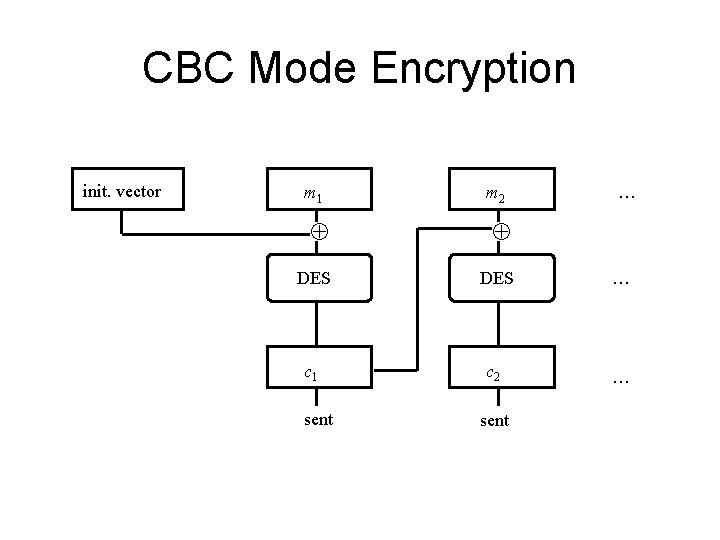
CBC Mode Encryption init. vector m 1 m 2 … DES … c 1 c 2 … sent
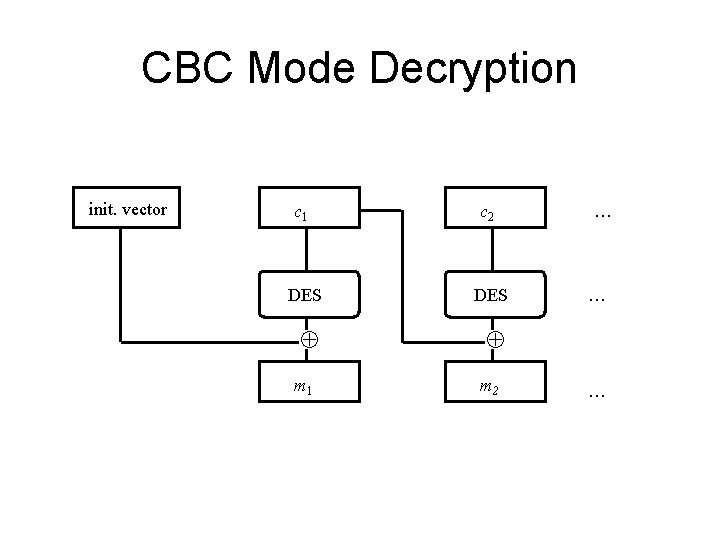
CBC Mode Decryption init. vector c 1 c 2 DES m 1 m 2 … … …

Self-Healing Property • What will happen if a bit gets lost during transmission? – All blocks will not be aligned • When one bit in a block flipped, only the next two blocks will be impacted. – Plaintext “heals” after 2 blocks

Current Status of DES • Design for computer system, associated software that could break any DES-enciphered message in a few days published in 1998 • Several challenges to break DES messages solved using distributed computing • NIST selected Rijndael as Advanced Encryption Standard, successor to DES – Designed to withstand attacks that were successful on DES
- Slides: 16