Overview of Computer Security C Edward Chow CS





















- Slides: 23

Overview of Computer Security C. Edward Chow CS 691 – Chapter 1 of Matt Bishop cs 691 1 chow

Outline of the Talk cs 691 n Definitions n Three Basic Security Services n Threats n Policy and Mechanism n Assumptions and Trust n Assurance n Operational Issues n Human Issues 2 chow

Computer Security: 1. a feeling secure; freedom from fear, doubt, etc. 2. protection; safeguard 3. something given as a pledge of repayment, etc. 4. [pl. ] bonds, stocks, etc. n Secure 1. [Firm] fastened, bound, adjusted 2. [Safe] guarded, unharmed, defended 3. [Self-confident] assured, stable, determined 1. Above from Webster’s New World Dictionary 2. Computer Security: issues, theories, techniques, and tools that deals with the protection and safeguard of computer systems. n cs 691 3 chow

Three Basic Security Services Confidentiality: the concealment of information or resources. n Integrity: the trustworthiness of data and resources n Availability: the ability to use the information or resources desired. n cs 691 4 chow

Confidentiality The need for keeping information secret arises from: l Enforcing the “need to know” principle in military and civilian government agencies. l Protecting proprietary designs from competitors l Protecting a company’s personnel records l Protecting personal financial/ID info against ID theft. n Apply to existence of data or traffic pattern n Apply to resource hiding l System configuration data l Systems/Equipment/Service Provider used. n cs 691 5 chow

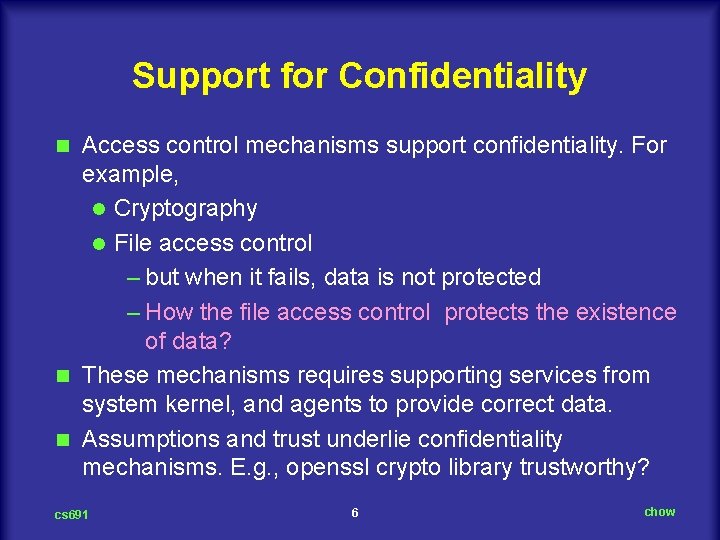
Support for Confidentiality Access control mechanisms support confidentiality. For example, l Cryptography l File access control – but when it fails, data is not protected – How the file access control protects the existence of data? n These mechanisms requires supporting services from system kernel, and agents to provide correct data. n Assumptions and trust underlie confidentiality mechanisms. E. g. , openssl crypto library trustworthy? n cs 691 6 chow

Integrity Preventing improper or unauthorized change. n Two types of integrity: l Data integrity (content of information) l Origin integrity (source of the data, related to authentication) significant bearing on the credibility and trust of the people who creates the info. n Example: newspaper print info from a leak at White House but attribute it to the wrong source. What integrity got violated? n cs 691 7 chow

Integrity Mechanisms Prevention mechanisms: They seek to maintain the integrity of the data by blocking l any unauthorized attempts to change the data, or – e. g. , intrusion – Protect with adequate authentication and access controls l Any attempts to change the data in unauthorized ways, e. g. , embezzlement such Enron? – Protect with (independent) Auditing, persons with integrity (those three persons of the year in Time n Detection mechanisms: report the data integrity is compromised, by analyzing system events or data itself. n cs 691 8 chow

Integrity vs. Confidentiality Which one is harder? n Confidentiality work finds whether data is compromised. n Integrity work includes checking the correctness and trustworthiness of the data. l This includes the history of the data – Integrity of the origin of data – How it is arrived (transport channel integrity) – How well it is protected after it arrived. n cs 691 9 chow

Availability n n n n Related to the reliability and system design Some may deliberately arrange to deny access to data or service by making it unavailable. The Attempts to block availability is called Denial of Service attacks. System designs usually assume a statistical model to analyze expected patterns of use. Those access patterns that follow the statistical model are allowed to use the services. How simple threshold-based related to this? How anomaly-based intrusion detection system (IDS) related to this? Deliberate attempt can “train” the IDS to treat attacks as atypical events. cs 691 10 chow

Threats n n n n Threat: Potential violation of security Violation need not actually occur for there to be a threat. Actions that could cause violation to occur must be guarded against, or prepared for. These actions are called attacks. Those who execute such actions, or cause them to be executed, are called attacker. Shirey [916] divided threats into four broad classes: l Disclosure --- unauthorized access to information l Deception – acceptance of false data l Disruption – interruption or prevention of correct operation l Usurpation – unauthorized control of some part of a system usurp – to take power by force [L usus a use rapere to seize] http: //www. ietf. org/ cs 691 11 chow

Examples of Threats Snooping: unauthorized interception of information, listen to communications, browse files/system info l disclosure type, l passive l Confidentiality services counter this threat. l Wiretapping or passive wiretapping: a form of snooping. n Modification or alteration: unauthorized change of info. l Deception, could lead to disruption or usurpation classes of threats if modified data control system operation. l Active wiretapping: a form of modification, – e. g. , Man-in-the-middle attack: intruder intercepts/modifies/relays the msg between sender/receiver. l Integrity services counter this threat. n cs 691 12 chow

Examples of Threats Masquerading or spoofing: an impersonation of one entity by another. l Deception and usurpation l Pretend to be a site or deliver different file. l integrity service (authentication services) counter this threat. l Masquerading vs. delegation. What is the difference? n Repudiation of origin: a false denial that an entity sent or created something. l Deception l Send order letter, then later deny the sending. l integrity mechanisms cope with this threat. n Denial of receipt: a false denial that an entity received some info or msg. l Deception l Deny receive payment or shipment. l integrity and availability guard against such attacks. n cs 691 13 chow

Examples of Threats Delay: a temporary inhibit of a service. l Usurpation (can play supporting role of deception). l Attacker force the delivery to take more time. l Availability mechanisms can thwart this threat. n Denial of Service: a long term inhibition of service l Usurpation l Attacker prevent server from providing a service. l The denial may occur at the source, destination, or along intermediate path. l Availability mechanisms counter this threat. l It can come from non-security related problems. n cs 691 14 chow

Policy and Mechanism Security policy is a statement of what is, and what is not, allowed. n Security mechanism is a method, tool, or procedure for enforcing a security policy. n cs 691 15 chow

Goals of Security Given a security policy’s spec of “ secure” and “nonsecure” actions. The security mechanisms can n Prevent the attack. l Implement mechanisms that attacker can not alter. l Password protection; ingress filtering n Detect the attack. l Determine if attack is underway, has occurred, and report it. l Monitor the attack activity, nature, severity and results. l Log/report high # of incorrect password. n Recover from the attack. 1. Stop attack, Assess and repair damages. (backup and recovery, identification and fixing the vulnerabilities, retaliation) 2. Continue to function while being attacked (fault tolerant design) n cs 691 16 chow

Assumptions and Trust n cs 691 A policy consists of a set of Axioms that policy makers believe can be enforced. Designer of policies always make two asumptions: 1. The policy correctly and unambigously partitions the set of system states into “secure” and “nonsecure” 2. The security mechanisms prevent the system from entering a “nonsecure” state. 17 chow

Secure, Precise, Broad Let P be the set of all possible states. n Let Q be the set of secure states as specified by the security policy. n Let the security mechanisms restrict the system to some set of states, R (thus R P) n A security mechanism is secure if R Q; It is precise if R = Q; and it is broad if there is a state r such that r R and r Q. n cs 691 18 chow

Assumptions for trusting security mechanism works Each mechanism is designed to implement one or more parts of the security policy n The union of the mechanisms implements all aspects of the security policy. n The mechanisms are implemented correctly. n The mechanisms are installed and administered correctly. n cs 691 19 chow

Assurance n n 1. cs 691 System specification, design and implementation can provide a basis for determining “how much” to trust a system. This aspect of trust is called Assurance. It is an attempt to provide a basis for bolstering how much one can trust a system. Assurance steps: 1. Detailed spec of desired or undesired behavior 2. An analysis of the design of hw, sw, other componets to show the system will not violate the spec 3. Arguments or proofs that implementation, operating procedures, and maintenance procedures will produce the desired behavior. Definition: A system is said to satisfy a specification if the specification correctly states how the system will function. 20 chow

Operational Issues Cost-Benefit Analysis n Risk Analysis n Laws and Customs n cs 691 21 chow

Human Issues Organizational Problems l No clear chains of responsibility and power l Lack of trained computer security people. l Knowledgeable people are overloaded. l Treat security as secondary task. l Lack of resource (time, money, computing resources, and training) n People Problems l Outsider: l Insider: l Untrained personnel. l Social Engineering attack: Disguise VP to change password over phone. l Misconfiguration problem with complexity of security related configuration files. n cs 691 22 chow

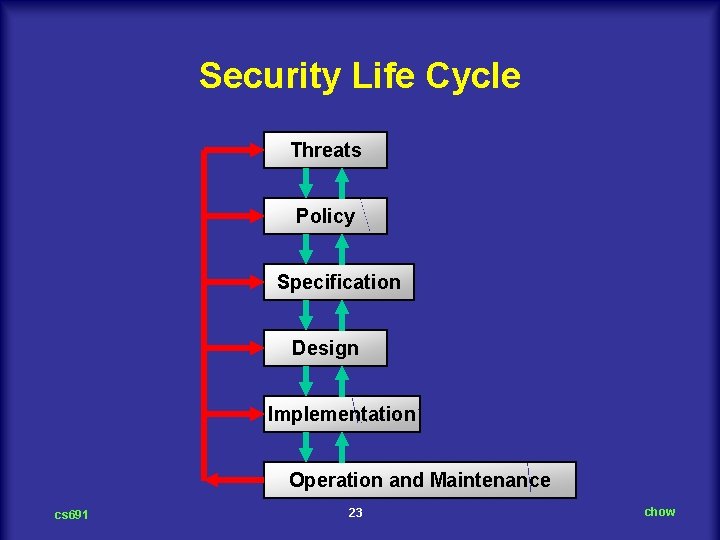
Security Life Cycle Threats Policy Specification Design Implementation Operation and Maintenance cs 691 23 chow